The specter of data breaches looms large over businesses of all sizes, in all sectors. One powerful tool emerging in the cybersecurity arsenal is dark web monitoring. Organizations that employ this proactive strategy can detect threats earlier, more effectively assess vulnerabilities, and better protect both their data and their reputation.
The dark web is an obscure domain where cybercriminals operate in the shadows, shielded by anonymity. This hidden realm has become a haven for threat actors and illicit trade alike. While it is naturally a source of concern for cybersecurity professionals, it is also an excellent source of intelligence that can mitigate the very threats cybercriminals hope to perpetuate.
In this post, we’ll explore the critical role of dark web monitoring services in defending businesses against data breaches.
What is the dark web?
The dark web is a hidden part of the internet – concealed from search engines and traditional web browsers. It is a network of encrypted connections, primarily accessed via special browsers or software like Tor, I2P, and Zeronet. The IP addresses of dark web users are hidden, making their activity anonymous. It is this anonymity that makes the dark web such a haven for cybercriminals and illicit content, as well as a breeding ground for illegal activities.
The dark web is a thriving marketplace for illicit content – especially stolen data like credit card details, social security numbers, and login credentials. This data is generally obtained through data breaches or hacking, then sold in underground marketplaces – fueling identity theft and cybercrime. The dark web is also a source for detecting illegal drugs, firearms, counterfeit currency, hacking services, and various forms of explicit or illegal media.
The dark web is highly relevant to business owing to the risks it poses, from data breaches to cyberattacks to reputational damage. It’s a marketplace for stolen business data and hacking tools. It hosts forums where cybercriminals exchange tactics for exploiting vulnerabilities, increasing the likelihood of cyberattacks on businesses. The dark web also provides a platform for leaked internal data, potentially leading to reputational damage and legal issues. All these make the dark web a strategic threat to businesses.
What is a data breach?
A data breach is an unauthorized access, disclosure, or acquisition of sensitive information from an organization’s systems. Breaches happen when cybercriminals or threat actors gain access to data they are not supposed to have through various means. Key causes of data breaches include:
- Human error – A whopping 88% of data breaches are caused by employee mistakes like sending sensitive information to the wrong recipient or misconfiguring security settings.
- Insider threats – Disgruntled employees or others with access to sensitive data can intentionally steal data or misuse it for personal gain or other malicious purposes.
- Cyberattacks – Cybercriminals use numerous tactics that include phishing, malware, ransomware, and hacking to gain unauthorized access to data or systems.
- Third-party vulnerabilities – Security weaknesses in partners, vendors, or other third parties can expose an organization’s data to breaches.
- Unpatched software – Out-of-date or unpatched software and systems are vulnerable to exploitation by cybercriminals who target known vulnerabilities.
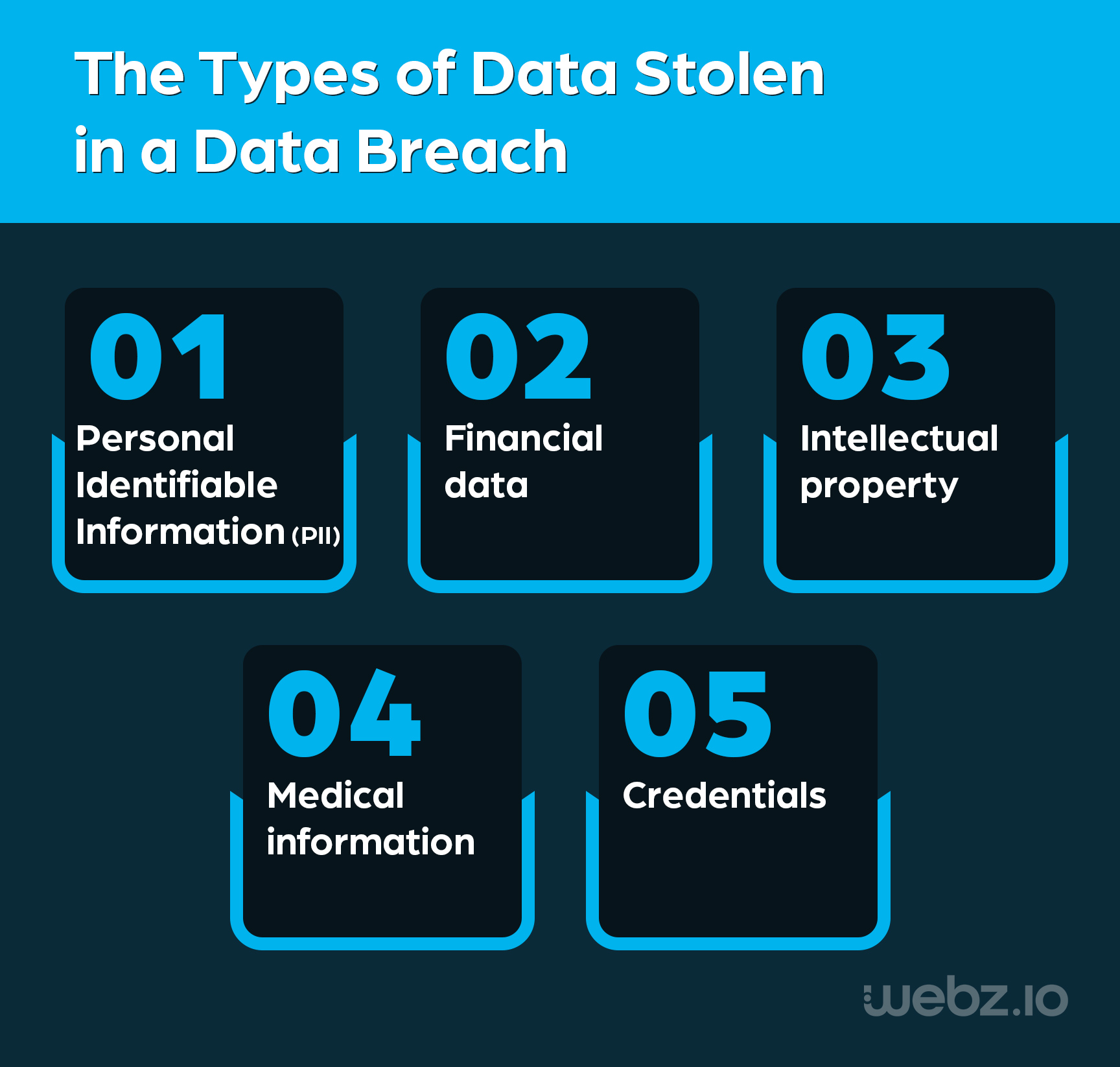
Various types of data can be stolen in a data breach, including:
- Personal Identifiable Information (PII) – Names, addresses, Social Security numbers, birthdates, etc.
- Financial data – Credit card numbers, bank account information, financial transaction data, and more
- Intellectual property – Proprietary information, trade secrets, patents and more
- Medical information – Medical records, health insurance details, and other sensitive health-related data
- Credentials – Usernames and passwords that offer access to accounts and systems
The repercussions of a data breach for businesses can be severe. Legal ramifications can include fines from regulatory bodies for non-compliance with data protection laws (GDPR and HIPAA, for example). What’s more, businesses can suffer severe reputational damage and loss of customer trust, leading to customer attrition and lower revenues.
How can dark web monitoring help businesses defend against data breaches?
Dark web monitoring can be invaluable for businesses seeking to mitigate the threat of data breaches, notably by:
- Acting as an early warning system by detecting mentions of a company name, employee names, customer data, or other parameters that might alert of potential threats before they escalate.
- Identifying stolen data through tracking sales and trades of certain data types and flagging data that could indicate that a company’s own data has been compromised.
- Assessing vulnerabilities to understand which (if any) specific vulnerabilities and security weaknesses in a company’s infrastructure are being discussed by threat actors as candidates for exploitation.
Armed with intelligence from the dark web, businesses can implement preventive measures, such as patching vulnerabilities and improving cybersecurity protocols. They can also leverage dark web monitoring to help meet regulatory requirements by demonstrating diligence in protecting customer data.
How to implement dark web monitoring
There are several key steps to implementing dark web monitoring in an organization, including:
- Select a dark web monitoring tool or service – Select a reputable and proven dark web monitoring tool or service provider that offers comprehensive coverage, real-time monitoring, and robust threat intelligence.
- Integrate with existing security infrastructure – Integrate your dark web monitoring service of choice into your existing cybersecurity infrastructure, making sure that it seamlessly syncs with your SIEM and other security tools.
- Train employees and raise awareness – Explain the purpose and significance of dark web monitoring to employees, and educate them to recognize and report potential threats, such as phishing emails or suspicious online activities.
- Continuously monitor and analyze – Regularly monitor and analyze data collected by your dark web monitoring service, remaining constantly vigilant for alerts and potential breaches.
- Adjust and improve – Continuously evaluate the effectiveness of your dark web monitoring strategy and make adjustments as needed.
Conclusion
Data breaches remain a constant threat to any business. Yet the implementation of dark web monitoring is a potent addition to the cybersecurity arsenal. Owing to its dangers, the dark web paradoxically holds the key to early threat detection and intelligence that can mitigate the risk of data breaches. In the battle to safeguard sensitive information, dark web monitoring offers organizations the chance to proactively protect their data and preserve their reputation in an evolving threat landscape.
Talk to the dark web experts at Webz.io to see how we can help with a dark web monitoring tool or dark web data to automate your own dark web monitoring solution.




