Dark Web Data: A Comprehensive Guide
Learn all about dark web data in our full guide. We cover what dark web data is, how to access it, how to collect data from the dark web, and how to analyze it.
In a time when executives are increasingly vulnerable to targeted threats, Lunar's Executive Threat Protection platform offers a proactive solution to safeguard your leadership team.
Get the complete view of threats against key executives within your organization, measuring risk so you can prioritize the highest credibility threats before they turn real.
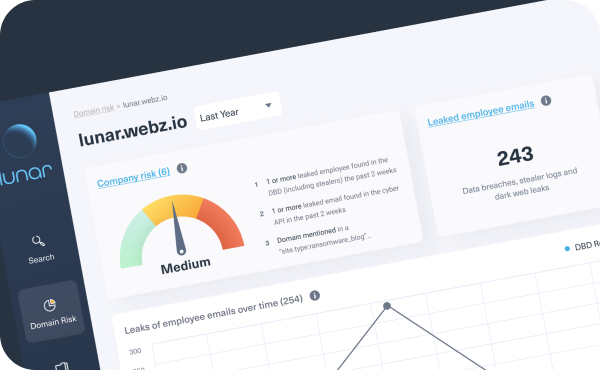
Instantly detect and analyze any malicious mentions of your executives and VIPs with Lunar to prevent the next attack.
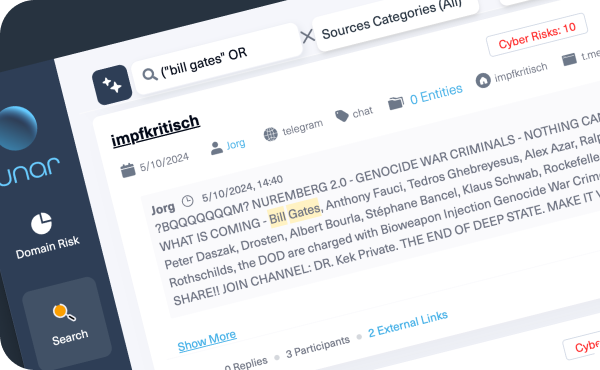
Monitor the alerts you have to see with Lunar’s advanced alert system, allowing you to prioritize high-risk alerts to mitigate imminent threats.
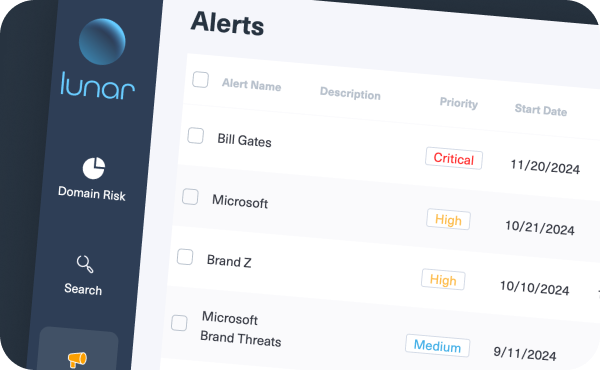
Get an overview of urgent breaches threatening your executives and company with Lunar’s automated reporting system. Now you can share an instant report and collaborate with your team to mitigate the next threat.


Guard your VIPs’ personally identifiable information (PII) from unauthorized access, preventing fraud, financial loss, operational disruptions, and legal liability. Quickly identify and eliminate risks to your company and VIPs.

Stay on top with instant notifications about any sensitive information or threats against your executives on the deep, dark, or open web. Proactively mitigate risks and potential damage to your organization's reputation, compliance, and bottom line.

Mitigate threats to your executives' safety and digital security by proactively addressing online threats and data breaches.
"Lunar has become an invaluable partner in our Dark Web and OSINT research. We can't rave enough about the user-friendly interface, the comprehensive data scope, and the accessibility of even the most elusive 'dark information.' These features have transformed our research process, eliminating tedious digging and freeing us to focus on in-depth analysis and maximizing the impact of our findings."

Learn all about dark web data in our full guide. We cover what dark web data is, how to access it, how to collect data from the dark web, and how to analyze it.

We reveal for the very first time the original post by the hacker behind T-Mobile's breach, which was published three days before the post the media and T-Mobile cited over the past weeks.

Could the latest mega cryptocurrency heist have been prevented? Let's review the role of early indications in averting the next hacking attack.