How to Monitor CVEs on the Dark Web

Discussions about Common Vulnerabilities and Exposures (more commonly known as CVEs), can be found across all corners of the dark web, in hacking forums, illicit marketplaces, and clandestine chat applications. These often hidden spaces offer cybercriminals a relatively safe and accessible environment to exchange insights, uncover vulnerabilities, and even trade methods for exploiting CVEs. These illicit activities lead to far-reaching implications, leading to unauthorized access to digital assets, data breaches, and cyberattacks.
How are cybercriminals using CVEs on the dark web?
Cybercriminals use CVEs on the dark web in various ways, including:
- The trade of weaponized CVEs – Selling or exchanging of step-by-step guides that illustrate how an attacker could exploit the vulnerability associated with the CVE within a system. These guides can be used to target systems that have not yet been fully patched or patched at all. You can find these activities on dark web hacking forums and dark marketplaces.
- The trade of exploit kits for existing CVEs – This includes the trade of exploit kits that include tools and methods that are used to exploit CVEs. These are usually offered for sale on hacker forums, dark web marketplaces, and paste sites.
- Sharing unpatched vulnerable assets – Sharing digital assets, servers, or unpatched systems vulnerable to existing CVEs. This exposure provides attackers with a direct pathway to exploit the identified vulnerabilities within these assets and systems. These discussions are typically found on paste sites and on closed Telegram groups in which hackers discuss their activity and recent findings.
- Zero-days trade – CVEs have become attractive targets for skilled threat actors who are looking for other potentially undetected vulnerabilities (also known as zero-days). These vulnerabilities stem from, for instance, a partially patched CVE, or as a result of pattern recognition leading to the discovery of similar vulnerabilities to those already identified. Such trading usually takes place in underground forums and dark web marketplaces.
CVEs on the dark web
Because the dark web serves as a rich environment for cybercriminals to learn, exchange, and trade guides and tools related to cyberattacks, it serves as a prime space for the continuous discovery of new vulnerabilities and CVEs. Many companies monitor the dark web to track any attempts of cybercriminals to leverage these vulnerabilities to compromise systems, steal sensitive data, and cause widespread harm to their business and employees.
We have noted a persistent surge in the volume of discussions about CVEs on the dark web when we looked for relevant values on our new dark web monitoring tool Lunar. You can see this trend in the chart below:
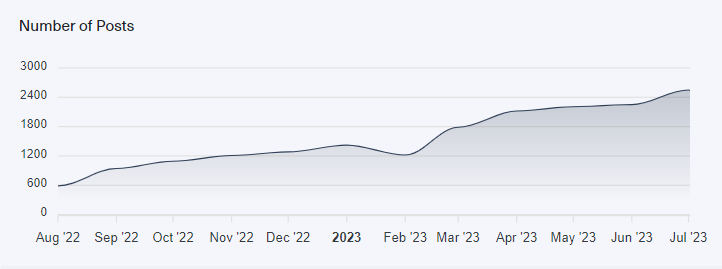
The reason behind this trend we believe can be attributed to two main factors. The first is the ongoing identification of security vulnerabilities across diverse software and systems, and the second is the increase in the number of available spaces hackers can easily turn to and securely share their knowledge on the dark web.
To combat this growing risk, cyber analysts need to constantly monitor the dark web to keep their organizations safe. We used the same workflow a cyber analyst would use to discover, investigate and monitor risks involving two CVEs by using our Lunar tool.
Case study: From discovering to monitoring CVEs on the dark web
We first ran a basic query on Lunar to search for CVEs mentioned on the dark web associated with vulnerabilities, exploits, and other hacking-related mentions that could indicate foul play.
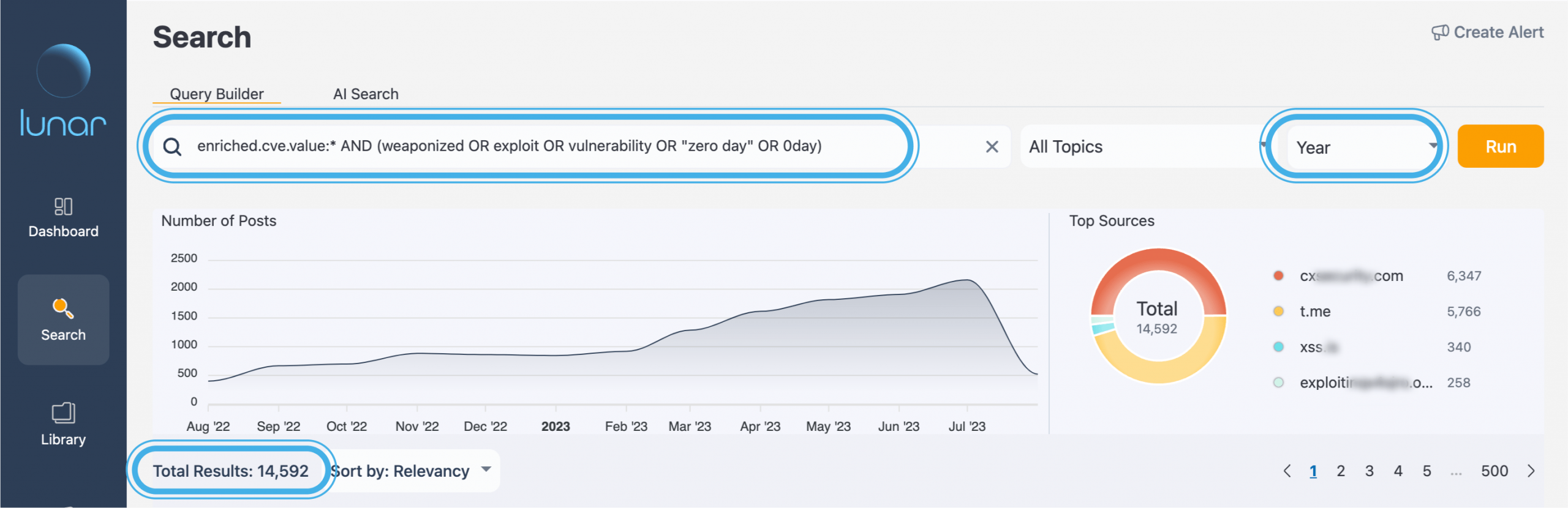
Running the discovery query a year back retrieved almost 15,000 posts.
Discovery of CVEs on the dark web
The first thing we got was an overview which we could easily narrow down according to our needs by using Lunar’s dynamic filters. In the following image, you can easily see the most mentioned CVEs (on the right) by using the CVE Entity filter.

By further zooming in on the most discussed CVEs, and then narrowing down our search to one of them, we can determine which CVEs are the main subject of conversations and how often they’re mentioned on the dark web. This enables us both to discover the top recent CVEs discussed on the dark web and to detect a renewed interest in older CVEs.
You can also find new lines of investigation when using other filters such as risk score, dark web sources, threat actors, and extracted entities found in the posts such as emails, domains, IPs, etc. Each of them allows you to unravel other potential risks and gain quicker insights.
Investigating CVEs on the dark web
After running this query, we want to enhance our investigation. We start by refining our results by using the sources filter. In this case, we narrowed down our search to posts from the popular Russian underground forum XSS.
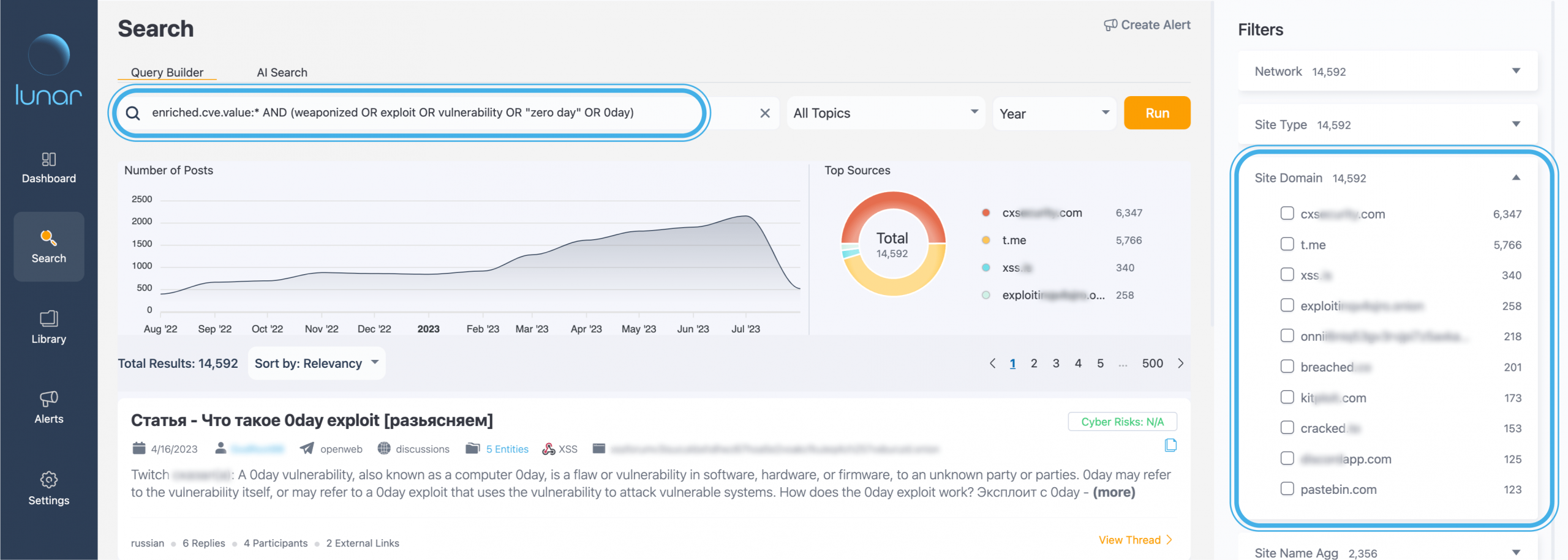
Once selecting XSS, the results shrank from 15,000 to a few hundred, streamlining our information intake to allow a more efficient and thorough investigation.
Once a filter is applied, we get an additional layer of insights that help open new directions of investigations.
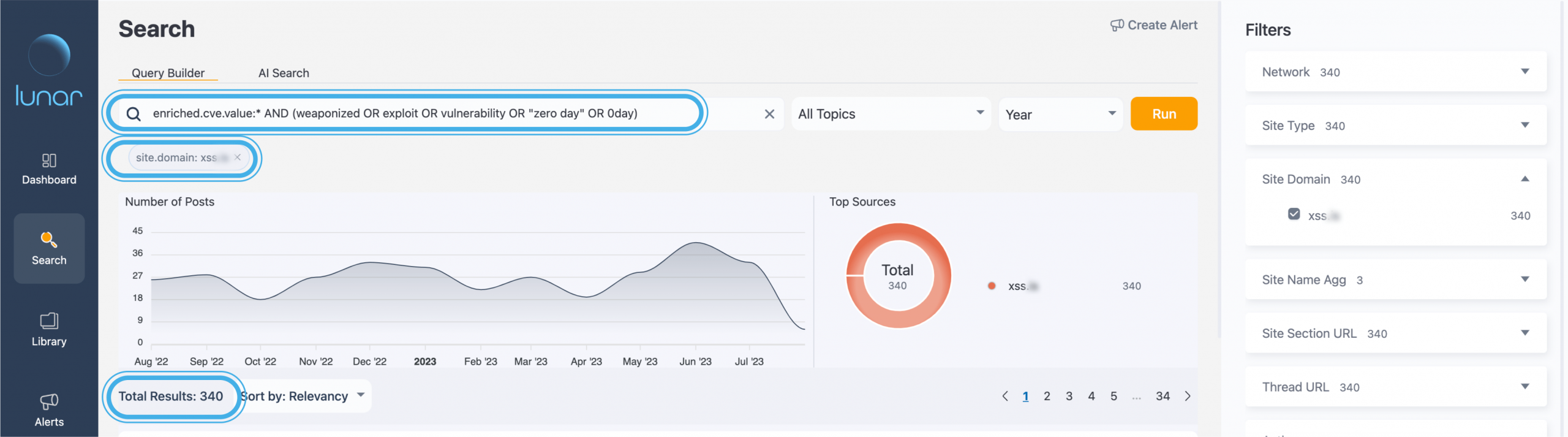
Monitoring specific CVEs on the dark web
Once we filtered the results, we found a post (see the image below) in which a threat actor sells exploits and exploit configurations service for 2 different CVEs; The first is CVE-2022-28672, which allows remote attackers to execute arbitrary code on affected installations of Foxit PDF Reader. The second is CVE-2023-21608, a security flaw in Adobe Acrobat Reader versions 22.003.20282, 22.003.20281, and 20.005.30418.
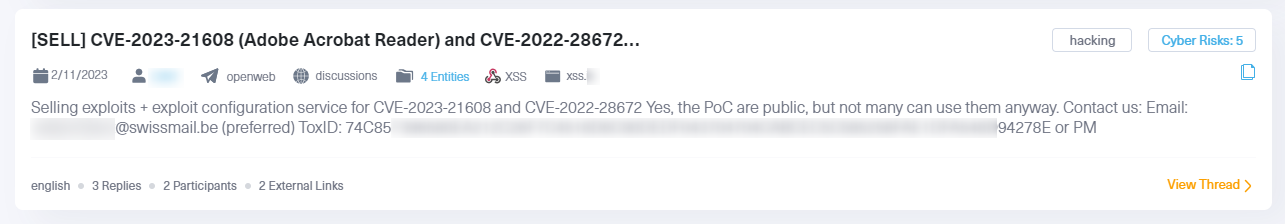
Using exploit configurations, additional components, or guidance that complement an exploit, a hacker can take advantage of vulnerabilities in CVEs, potentially gaining unauthorized access or control over systems, leading to data breaches, system compromise, and broader security risks.
Monitoring the dark web for CVEs and threats against brands and operating systems
It’s crucial for security teams, from CTI (Cyber Threat Intelligence) Analysts, SOCs (Security Operation Centers), to threat hunters to monitor the dark web for discussions related to CVEs since they can provide early insights into emerging vulnerabilities and potential exploits. By staying informed about the latest CVE-related trends and illicit activities, teams can proactively defend against cyber threats, assess their organization’s risk exposure, and take timely measures to secure their systems before they become targets for malicious actors. This proactive approach helps prevent data breaches, system compromises, and potential financial losses.
CVEs are only one example of many different entities that can be tracked on the dark web to monitor for emerging threats and hacking trends that pose risks to brands, and individuals.
Dark web monitoring tools, like Lunar, help analysts easily search through the largest database of darknet data to discover, investigate, and continuously monitor the dark web for quick insights. In this blog post, we showed how you can efficiently identify and discover recently disclosed CVEs on the dark web, find which system they belong to, on which dark web source they were mentioned, and investigate who posted them and where else those threat actors operate on a daily basis. You can also set up alerts to receive notifications about pre-set searches that you’d like to continuously monitor to gain critical insights and take proactive measures to protect your business.