How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

The specter of data breaches looms large over businesses of all sizes, in all sectors. One powerful tool emerging in the cybersecurity arsenal is dark web monitoring. Organizations that employ this proactive strategy can detect threats earlier, more effectively assess vulnerabilities, and better protect both their data and their reputation.
The dark web is an obscure domain where cybercriminals operate in the shadows, shielded by anonymity. This hidden realm has become a haven for threat actors and illicit trade alike. While it is naturally a source of concern for cybersecurity professionals, it is also an excellent source of intelligence that can mitigate the very threats cybercriminals hope to perpetuate.
In this post, we’ll explore the critical role of dark web monitoring services in defending businesses against data breaches.
The dark web is a hidden part of the internet – concealed from search engines and traditional web browsers. It is a network of encrypted connections, primarily accessed via special browsers or software like Tor, I2P, and Zeronet. The IP addresses of dark web users are hidden, making their activity anonymous. It is this anonymity that makes the dark web such a haven for cybercriminals and illicit content, as well as a breeding ground for illegal activities.
The dark web is a thriving marketplace for illicit content – especially stolen data like credit card details, social security numbers, and login credentials. This data is generally obtained through data breaches or hacking, then sold in underground marketplaces – fueling identity theft and cybercrime. The dark web is also a source for detecting illegal drugs, firearms, counterfeit currency, hacking services, and various forms of explicit or illegal media.
The dark web is highly relevant to business owing to the risks it poses, from data breaches to cyberattacks to reputational damage. It’s a marketplace for stolen business data and hacking tools. It hosts forums where cybercriminals exchange tactics for exploiting vulnerabilities, increasing the likelihood of cyberattacks on businesses. The dark web also provides a platform for leaked internal data, potentially leading to reputational damage and legal issues. All these make the dark web a strategic threat to businesses.
A data breach is an unauthorized access, disclosure, or acquisition of sensitive information from an organization’s systems. Breaches happen when cybercriminals or threat actors gain access to data they are not supposed to have through various means. Key causes of data breaches include:
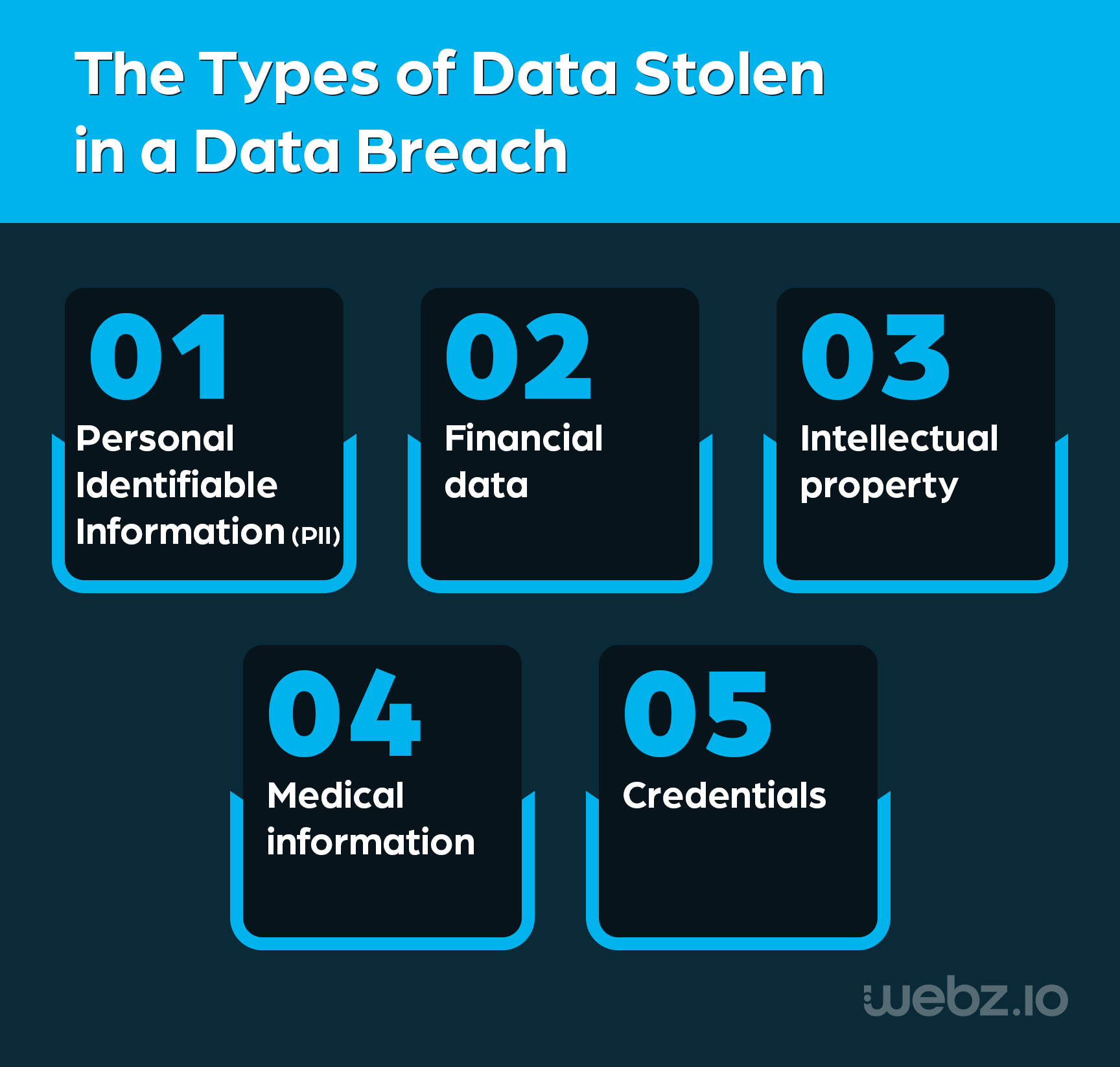
Various types of data can be stolen in a data breach, including:
The repercussions of a data breach for businesses can be severe. Legal ramifications can include fines from regulatory bodies for non-compliance with data protection laws (GDPR and HIPAA, for example). What’s more, businesses can suffer severe reputational damage and loss of customer trust, leading to customer attrition and lower revenues.
Dark web monitoring can be invaluable for businesses seeking to mitigate the threat of data breaches, notably by:
Armed with intelligence from the dark web, businesses can implement preventive measures, such as patching vulnerabilities and improving cybersecurity protocols. They can also leverage dark web monitoring to help meet regulatory requirements by demonstrating diligence in protecting customer data.
There are several key steps to implementing dark web monitoring in an organization, including:
Data breaches remain a constant threat to any business. Yet the implementation of dark web monitoring is a potent addition to the cybersecurity arsenal. Owing to its dangers, the dark web paradoxically holds the key to early threat detection and intelligence that can mitigate the risk of data breaches. In the battle to safeguard sensitive information, dark web monitoring offers organizations the chance to proactively protect their data and preserve their reputation in an evolving threat landscape.
Talk to the dark web experts at Webz.io to see how we can help with a dark web monitoring tool or dark web data to automate your own dark web monitoring solution.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.