Microsoft Under the Microscope: Is a Patched Windows CVE Safe Now?

A critical security vulnerability in Microsoft’s services attracted a lot of attention recently. Assigned CVE-2023-36874, this flaw which could be used to gain admin-level access, was swiftly patched. However, we have been able to find discussions that have emerged since on the dark web to raise new concerns, ones that require an investigation.
In this article, we’ll embark on a journey into the depths of the dark web to explore suspicious posts related to CVE-2023-36874 by using Lunar, our new dark web monitoring tool.
Before we dive into this investigation, let’s first talk about CVE-2023-36874 and the broader context of CVE discussions on the dark web.
What is CVE-2023-36874?
CVE-2023-36874 exposes a critical security vulnerability within Microsoft’s Windows Error Reporting Service. While this service typically helps collect and report errors in the Windows operating system, a vulnerability in this system poses a significant risk. Threat actors can exploit this vulnerability to manipulate the Windows Error Reporting Service. This manipulation grants them elevated privileges, akin to administrator-level access. The implications can be major, encompassing unauthorized system control, data access, and the potential for disruptive actions that could affect anyone using Microsoft’s Windows Error Reporting Service (WER).
The danger of CVEs on the darknet
As we thoroughly covered in previous Dark Web Pulse articles, the dark web serves as a hub for cybercriminals to share knowledge, trade tools, and orchestrate attacks. However, it is also a prime space for tracking new vulnerabilities and CVEs.
CVE monitoring never stops as even after a CVE is identified and patched, cybercriminals persist in their attempts to leverage the vulnerability in various ways in order to compromise systems and steal sensitive data.
For this reason, we have decided to investigate CVE-2023-36874 further and see if we can find other newer threats, despite the fact that Microsoft has patched it. We will be using Lunar to discover dark web conversations related to this CVE and see if there are any signs that threat actors tend to abuse it again.
Let’s start our investigation.
Investigating CVE-2023-36874 with Lunar
Step #1: Discovery
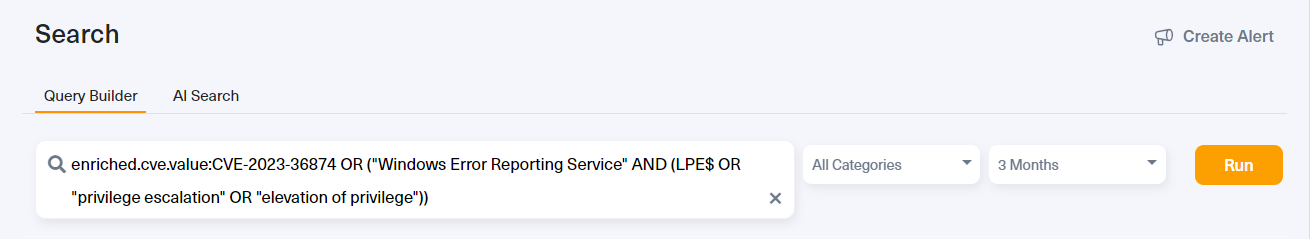
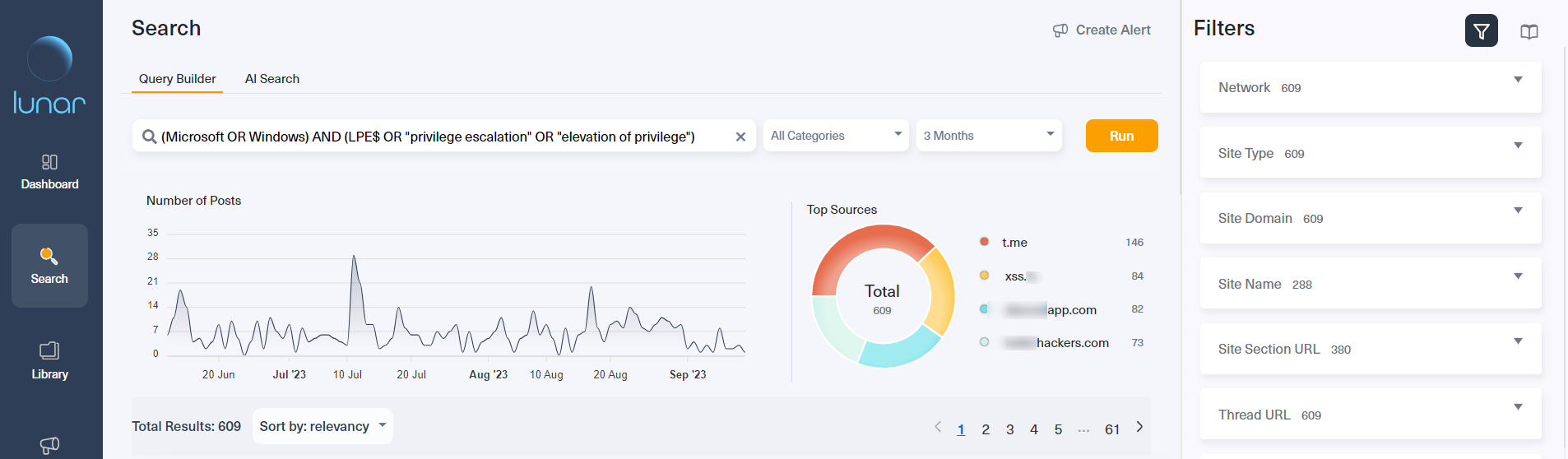
Our investigation begins with a simple query, searching for any discussions related to CVE-2023-36874. We also employed alternative search terms describing the CVE, all within the context of the last 3 months (see image below).
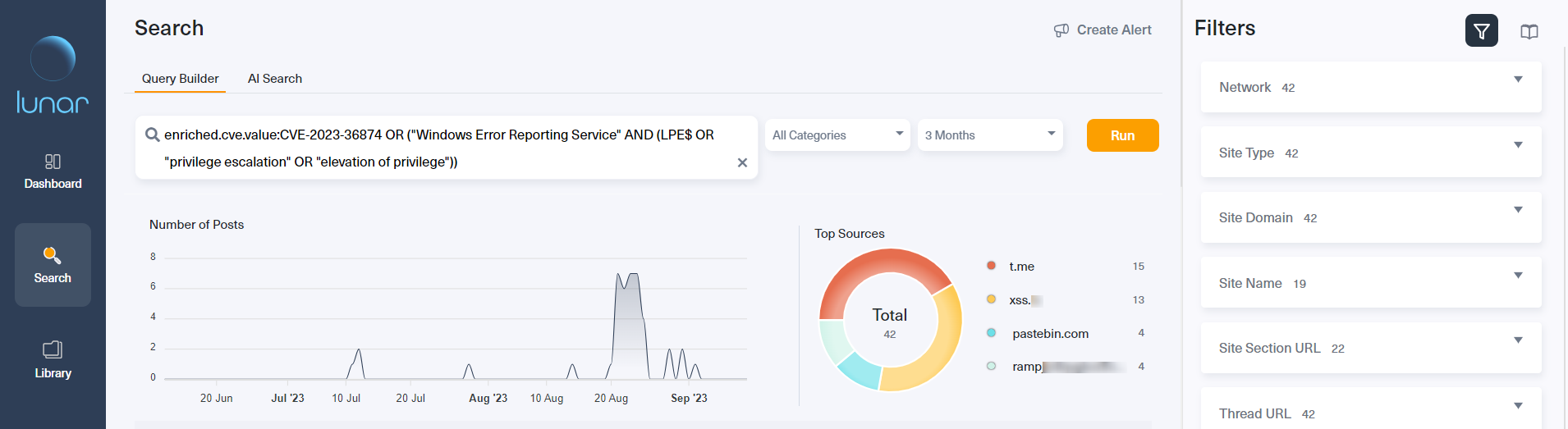
Once we ran this query, Lunar immediately returned a chart illustrating the distribution of dark web discussions around CVE-2023-36874 over the past 3 months, which shows an unusual uptick recently.
We can see the top domains featuring the highest number of relevant posts in the pie chart on the right-hand side. Here we can see that the top domains are Telegram, PasteBin, the Russian hacking forum XSS, and the ransomware forum Ramp.
Once we take a look at the posts Lunar displays, we can see many discussions revolving around the exchange of PoC (proof-of-concept) exploit code. These PoC codes provide a step-by-step method for exploiting the vulnerability, which could potentially be misused if employed against systems that have not yet been fully patched or patched at all, without proper authorization.
You can see an example of such misuse in the next image:
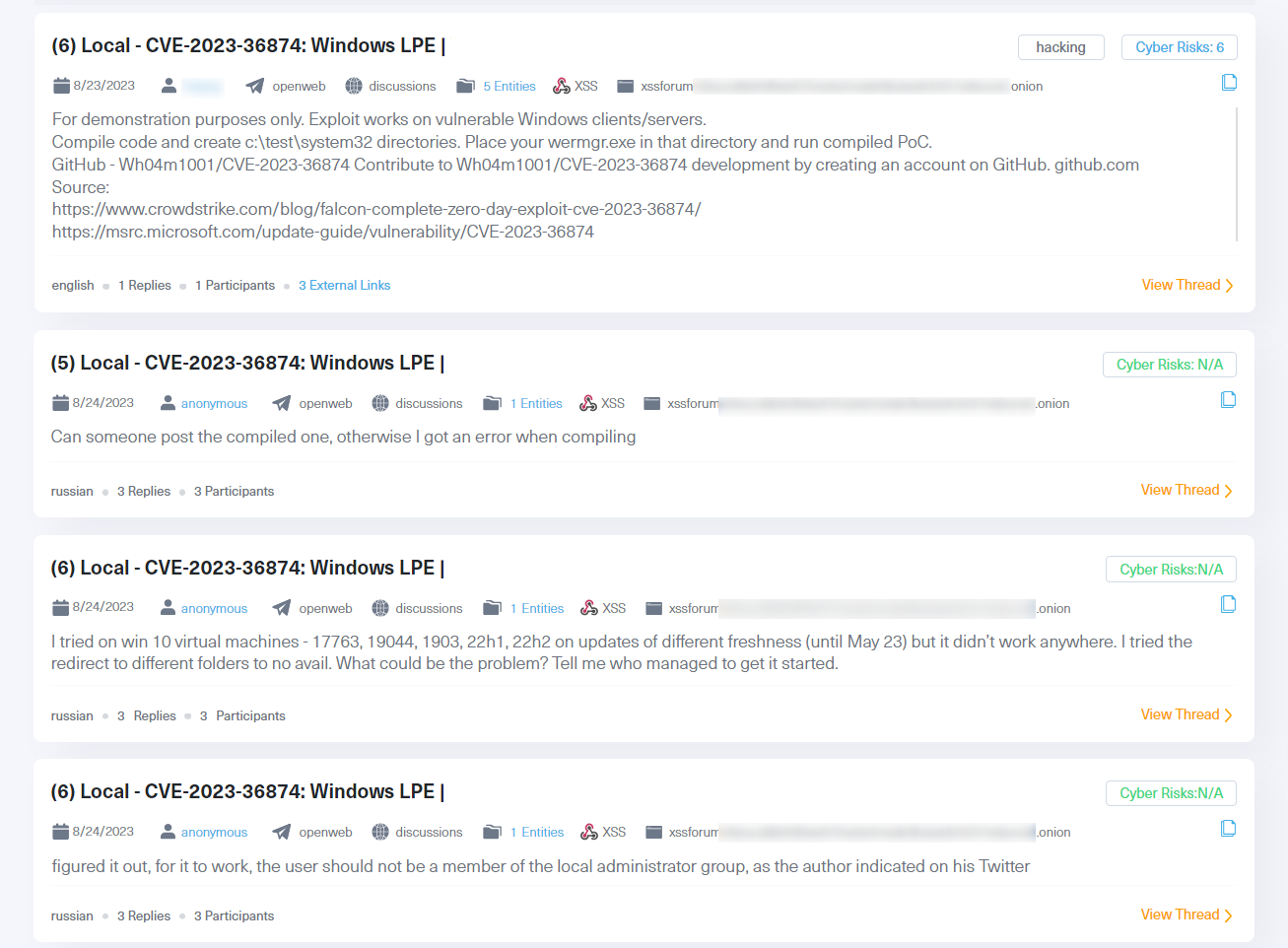
In this thread, a user states that the PoC they found works on vulnerable Windows systems, assuming he has already tested it. Other users respond and share their experiences and issues when attempting to run the exploit on various Microsoft Windows versions. Given that this discussion is taking place on a hacking forum, it is very likely that these individuals are not legitimate threat actors authorized to use these techniques.
This kind of discussion highlights how exploit code can be used to gain unauthorized access, manipulation of compromised systems, and new breaches.
Step #2: Investigation
In our investigation of dark web discussions related to CVE-2023-36874, we didn’t stop at the surface level. We went beyond only finding mentions of this specific CVE to uncover broader indicators of malicious activities tied to known or possibly undiscovered vulnerabilities within Microsoft’s services that could enable privilege escalation, similar to CVE-2023-36874.
To cast a wider net, we ran a more comprehensive search using relevant keywords such as “Windows” and “privilege escalation.” The results provided us with a broader view of discussions related to privilege escalation in Microsoft products.
Among the wealth of information we found, one post stood out. Published shortly after the thread discussing CVE-2023-36874 we showed before, this post includes a “Fully Undetectable” (FUD) privilege escalation exploits specifically designed for Windows 10/11 which is up for sale.
In this post, the threat actor also shares a video in which he shows how effective the exploit is. In the video, they successfully exploited a vulnerability within the Windows operating system, providing evidence of the potential harm this exploit can cause:
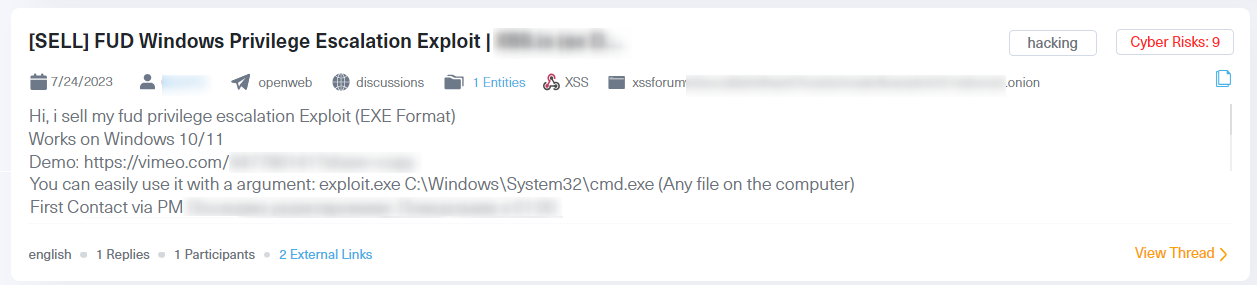
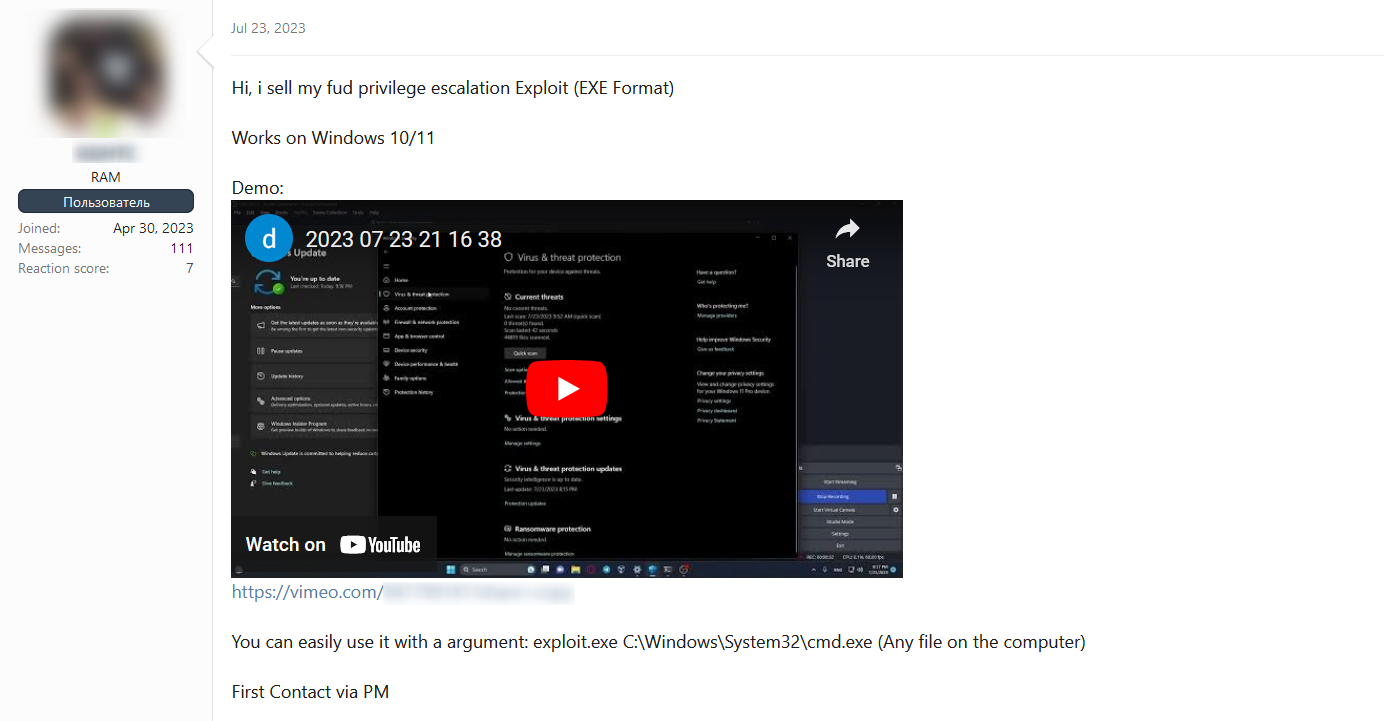
While the post did not explicitly mention CVE-2023-36874, it could potentially be linked to the same or a similar vulnerability. However, whether directly associated with CVE-2023-36874 or not, the presence of such exploits on the dark web is a cause for concern. Privilege escalation exploits, as already mentioned earlier, can lead to various malicious activities, including taking control of the system, stealing sensitive data, or delivering and executing malware. The very use of the term “FUD” implies that the exploit is designed to evade detection by security software, making it even more potent in the hands of cybercriminals.
Step #3: Monitoring
When monitoring for threats on the dark web, our goal is to maintain unwavering vigilance against not only established threats but also emerging ones. In order to do that, we would usually set a system of alerts to stay on top of any new mentions, based on predefined queries.
For the purpose of ongoing monitoring of any discussions around privilege escalation threats to Windows systems, we’d use the query we set before to set a new alert. We will then set the name, priority, frequency, and more to get relevant notifications in time to stay on top of any developments in the deep and dark web.
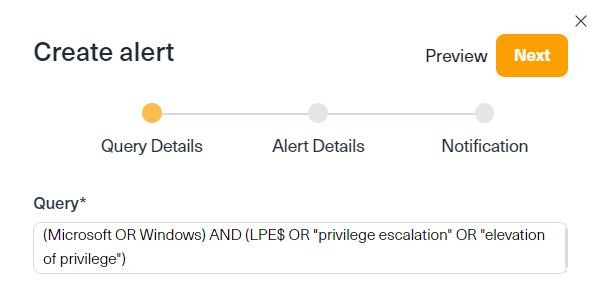
This is the only way to ensure ongoing and proactive dark web monitoring to protect companies and systems from emerging CVE threats like Microsoft’s CVE-2023-36874. By taking all of these steps, and creating the right alert, you can stay ahead of potential threats that may be lurking in the internet’s underbelly, and safeguard your digital environment.