The Rising Threat of the CL0P Ransomware Group in 2023

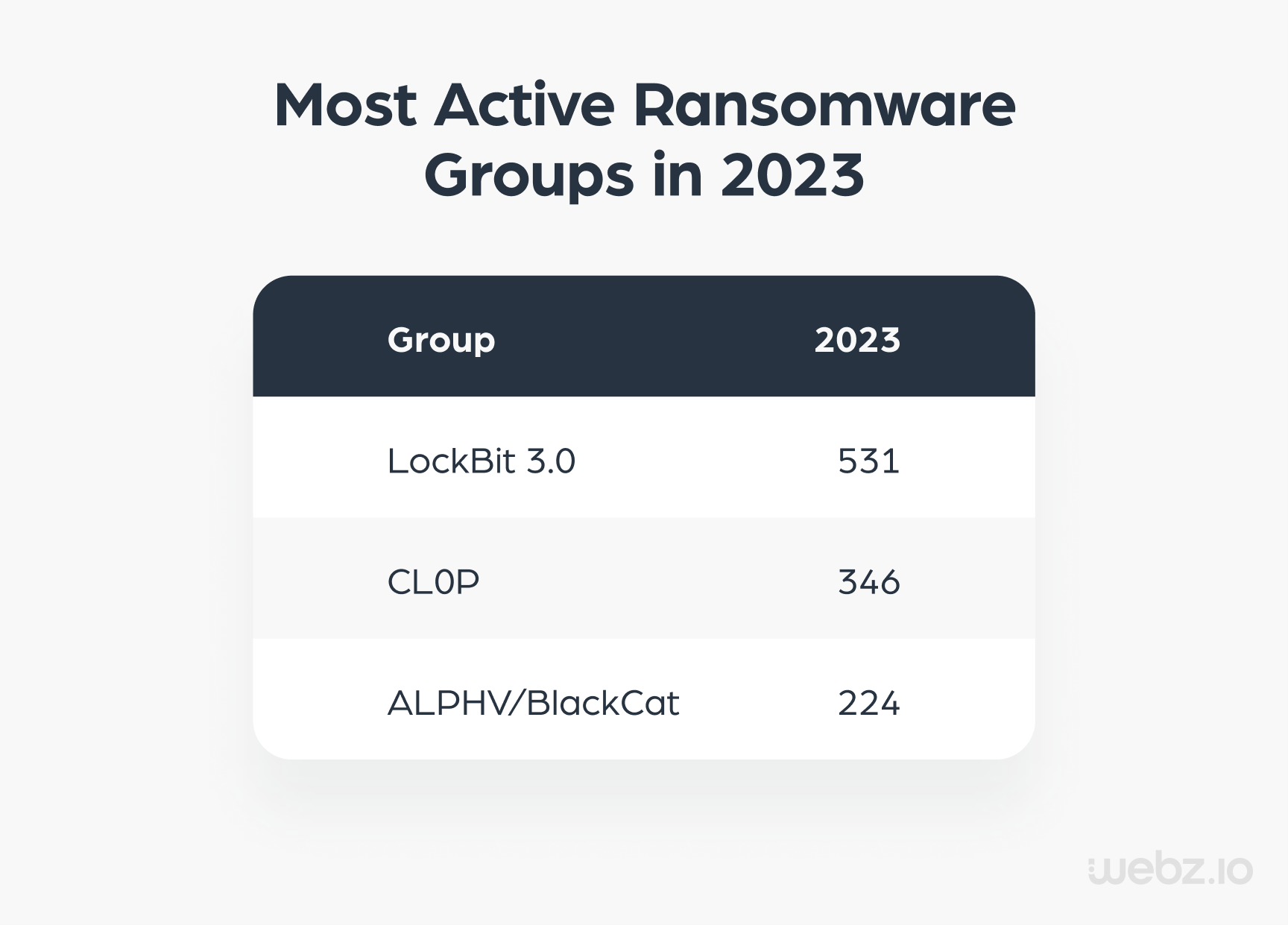
The year 2023 has marked a significant surge in the activities of the CL0P ransomware group, which first emerged in 2019. This past year, the group has claimed to have executed 346 attacks, surpassed only by Lockbit 3.0, which positions them at the forefront as one of the leading ransomware groups in recent months.
Using our Cyber API, we’ve been able to closely monitor the shifting patterns in the mentions of the CL0P ransomware group across the deep and dark web. An increase in mentions of specific ransomware groups on the dark web can serve as an alert, indicating emerging trends and a heightened level of risk associated with the group.
We looked at the number of mentions of CL0P on the deep and dark web from May 2022 to May 2023, which you can see in the chart.
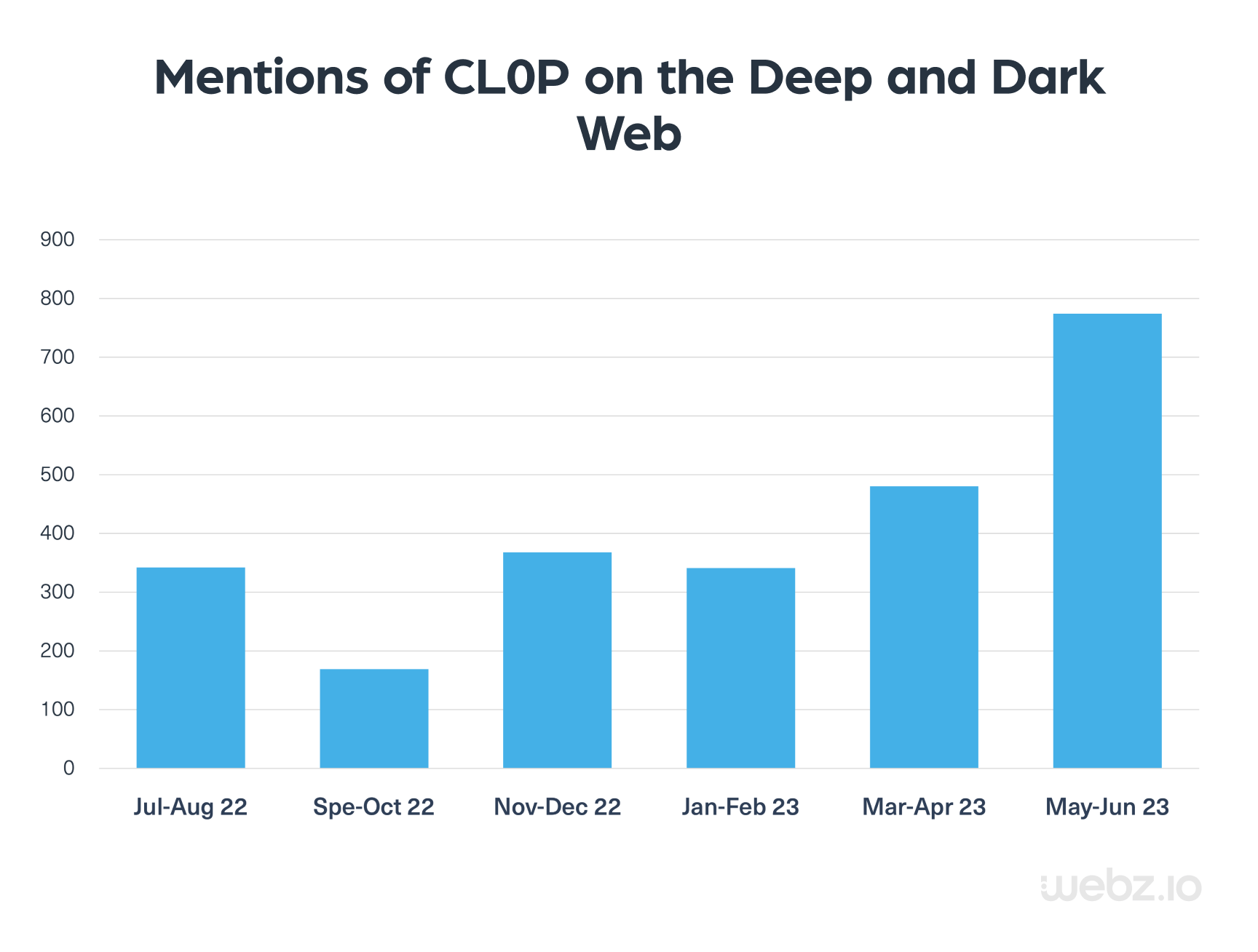
As you can see, there has been a steady increase in the number of mentions of the group over the past year.
What do we know about CL0P?
The CL0P ransomware group has been active since 2019. While the identities of its members remain unknown, researchers believe the group is likely based in a country that’s part of the Commonwealth of Independent States (CIS), including Russia and former Soviet Union countries. One of the reasons for this assumption is the fact that CL0P’s ransomware contains metadata in Russian and their activities seem to halt during Russian holidays. Another possible indication is that their malware checks if infected computers use the Russian language character set or keyboard layouts for countries in the CIS. If they do, the ransomware deletes itself.
We used our data to analyze CL0P’s mentions on the dark web over the last year, and then we segmented the attacks based on the countries affected, which you can see in the pie chart below.
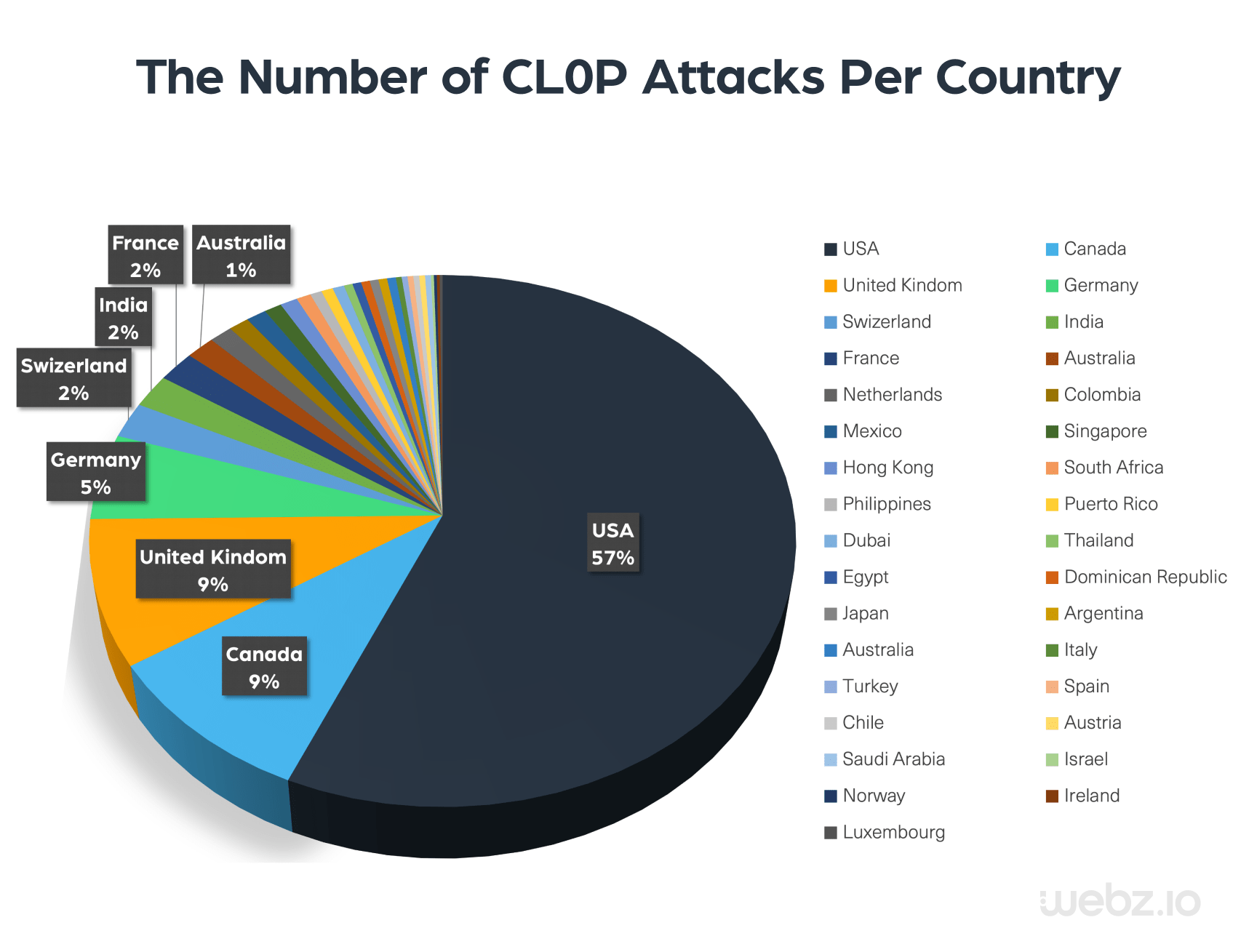
As you can see in the chart, the majority of the attacks were directed at US companies, followed by Canada and various European countries. It is worth noting that there were no reported incidents targeting companies based in Russia or in any other former Soviet Union countries. This is yet another sign that shows that the group members are likely from the CIS region, and their primary targets are American and European companies.
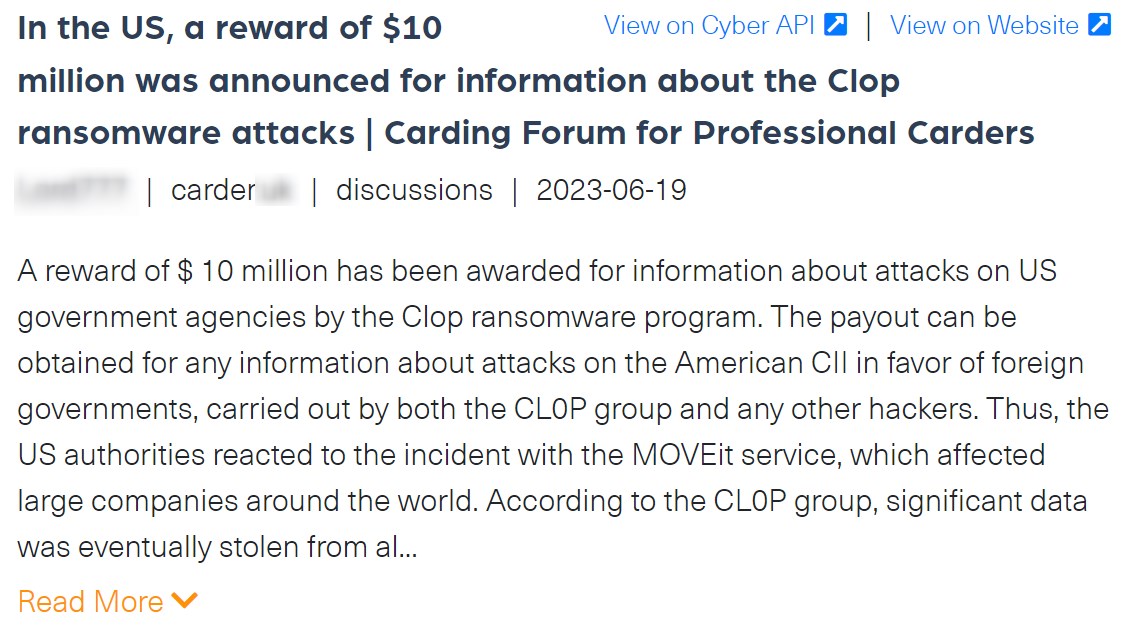
Due to the anonymity of the group members, US government agencies have recently issued a bounty of $10M for anyone who will provide information that will help identify members of the CL0P group. This move also indicates that CL0P is gaining in popularity and reinforces its status as one of the primary, must-watch ransomware groups.
The following screenshot was taken from CARDER, a carding forum, where the news about the bounty on CL0P was shared:
How is CL0P different from other ransomware groups?
Unlike other ransomware groups such as Netwalker, REvil, and CONTI, CL0P doesn’t run an affiliate program, meaning they don’t share their malware with other cybercriminals for money.
Instead, CL0P runs the entire hacking operation from start to finish, which, although reducing the size of their earnings, increases their control over the operation.
What are the top Cl0P attacks in 2023?
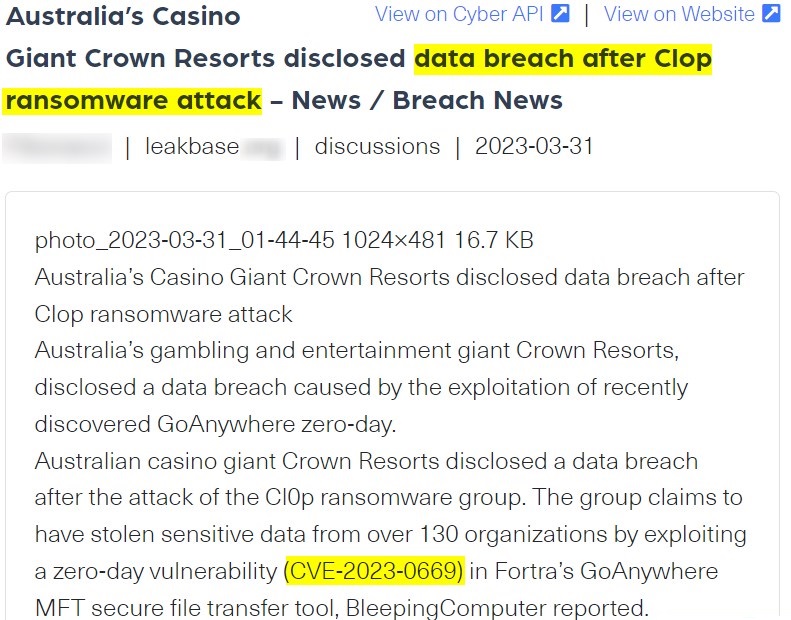
The first attack was launched in late January 2023, when the group exploited a zero-day vulnerability, recorded as CVE-2023-0669, targeting the GoAnywhere Managed File Transfer (MFT) platform. The group claimed to have exfiltrated data from this platform that impacted approximately 130 victims over 10 days. By searching for the IoC CVE-2023-0669, we identified evidence of a data breach affecting one of the victims targeted by this particular attack.
The second attack took place in May 2023, exploiting a previously unknown SQL injection vulnerability (CVE-2023-34362) in Progress Software’s MOVEit Transfer MFT solution. The vulnerability was exploited to infect internet-facing MOVEit Transfer web applications with a web shell named LEMURLOOT, which was then used to steal data from underlying MOVEit Transfer databases.
What does the future hold for CL0P?
The surge in the activities of the CL0P ransomware group in 2023 has raised concerns and attracted attention from cybersecurity researchers and law enforcement agencies. As the group continues its illegal operations, experts believe that it’s only a matter of time before the group makes a mistake that would lead to its identification. Some speculate that CL0P may attempt to rebrand, as other ransomware groups have done to avoid attention, but it’s difficult to know what the future holds for this group.
How can we protect against ransomware attacks?
CL0P serves as just one example of a ransomware group that should be monitored due to its rising threat. While you were reading this post, it is likely that a new ransomware group has emerged, or that an existing ransomware group has targeted a new company. With ransomware attacks becoming more frequent, the need for dark web monitoring tools, like Lunar, becomes increasingly crucial to track real-time leaks and provide information that can be used to protect against ransomware-led breaches.