Revealed: The Hidden Malware Threat Landscape in the Dark Web

Malware is a general term used for a malicious code or intrusive software developed by hackers or cybercriminals with the aim to steal data, damage or destroy servers, networks, infrastructure or digital facilities.
There are different types of malwares including ransomware, trojan horse, spyware, and worm. We regularly see them discussed and traded in the deep and dark web, often on chat apps like Telegram but also in hacking forums such as Cracked, Xss, Exploit and in the past, in the recently seized Raidforums.
In this post, we will dive deeper into the dark web landscape to discover the context in which malwares are mentioned and discussed.
We will also cover the following topics:
- High-risk malware in the dark web
- Top platforms that host malwares discussions and trade
- Emerging new malware
We have looked to first establish the sheer scope of the discussions and trade of malware in the deep and dark web.
We used our Cyber API to run a query on general mentions of the malware and its subtypes, since most threat actors specify the relevant malware types and subtypes to advertise the exploit they are trading. Some of the keywords we used in our search included malware, keylogger, malvertiser, scareware, skimmer, trickbot and trojan horse.
Over the past 4 month, we have seen a 47% increase in the daily average of malware mentions in the dark web. But what are the risks we could find?
High-risk malware in the dark web
We used our Cyber Segmentation API to get a different angle and analyze our queries per dimension.
First let’s aggregate the results using Webz.io’s cyber risk value, which automatically ranks the level of risk of each post from 1-10, with 10 being the highest. The risk is determined by the post’s context, entities and site on which it was published.
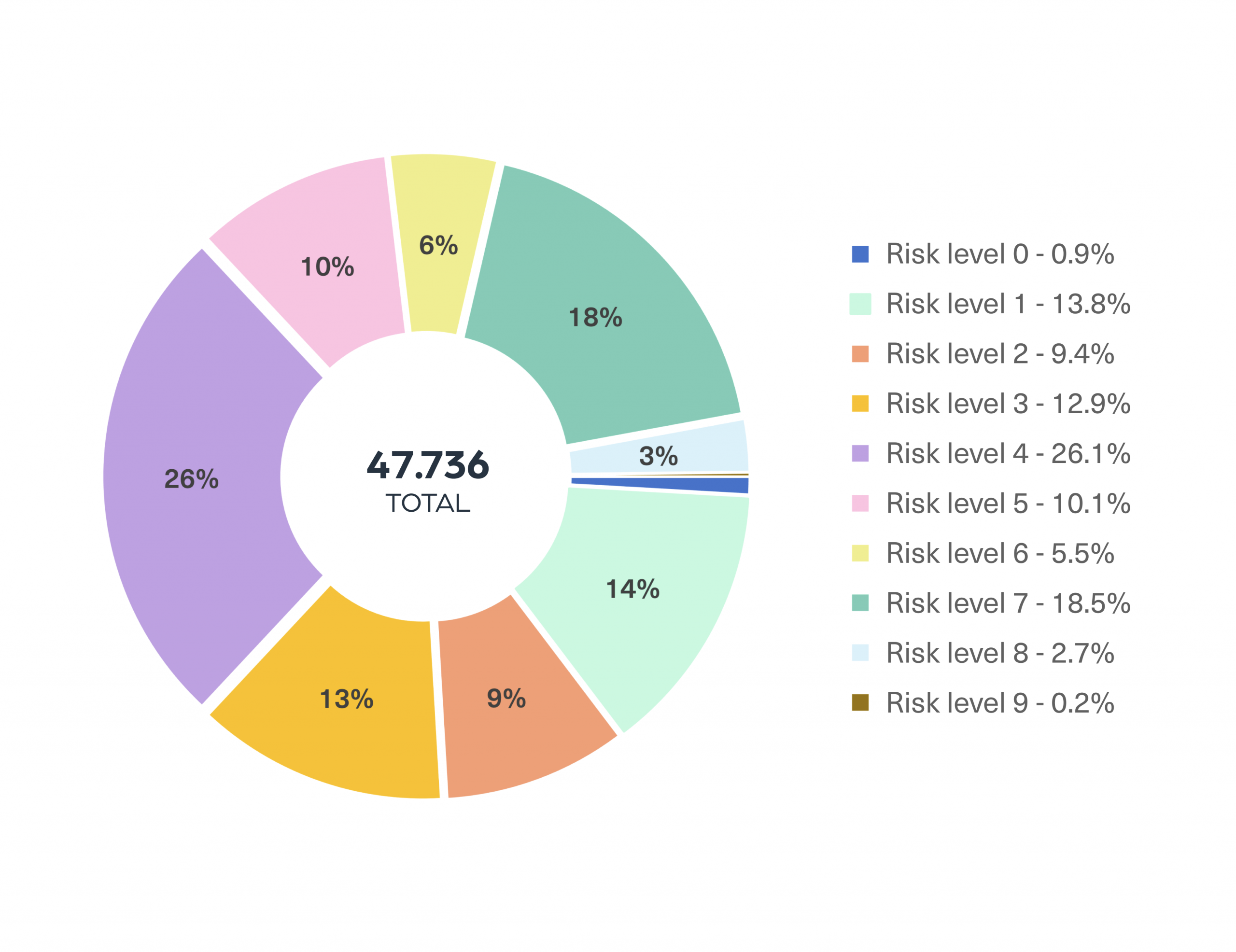
Looking at the results, we can clearly see that more than 60% of the content is rated as medium or high cyber risk (4-9).
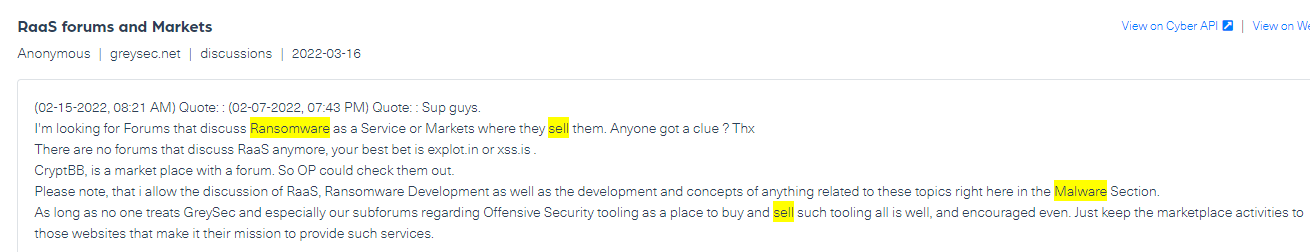
Below you can find an example of a post that stands at risk level 5. In it, threat actors are looking to buy RaaS (Ransomware as a service):
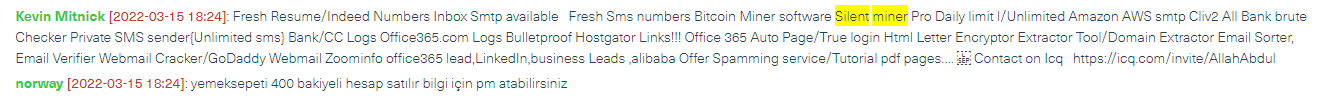
We also see new malwares published and traded every day in the deep and dark web. Below is an example of a post offering a new malware called Silent Miner which mines bitcoin on the victim’s computer.
The top platforms that host discussions and trade of malware on the dark web
We also looked for the top domains hosting discussions and trade of malware, where we can see threat actors exchanging ideas as well as buying and selling new malware codes.
In the chart below, we list the top 5 domains with the highest number of discussions relating to malwares, alongside the types of malwares that can be found on them:
| Platforms | Type of platform | Type of Malware |
|---|---|---|
| Telegram* | Chat application | Keyloggers, skimmers, trojan horse, spywares, and adware |
| Cracked.to | Forum | Keyloggers, exploit kits, ransomwares, and spywares |
| Eternia.to | Forum | Keyloggers |
| Cybercarder.su | Data store | Skimmers and adware |
| XSS | Forum | Ransomwares and exploits |
Emerging new malwares in the dark web
Monitoring these sites can help discover new malwares that need to be tracked.
Let’s take a look at some emerging malwares we have recently found:
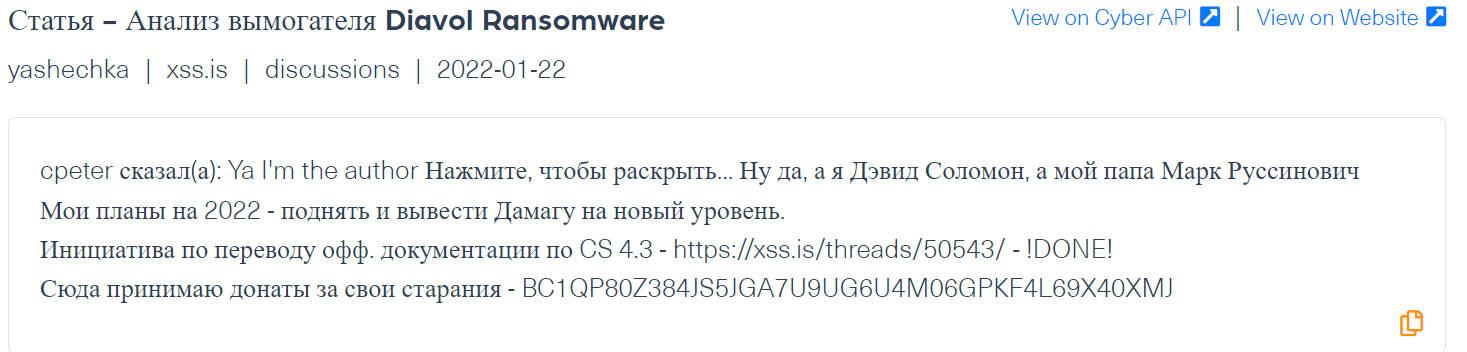
Diavol and Mermaid
These are two types of ransomwares which have been mainly mentioned in Russian forums such as XSS. Such ransomwares encrypt data on systems and employ a strong RSA encryption. This type of ransomwares is used to attack enterprise level organizations.
Below is a post from a popular hacking forum, XSS, which is part of a thread analyzing and explaining how the malware works for malicious use:
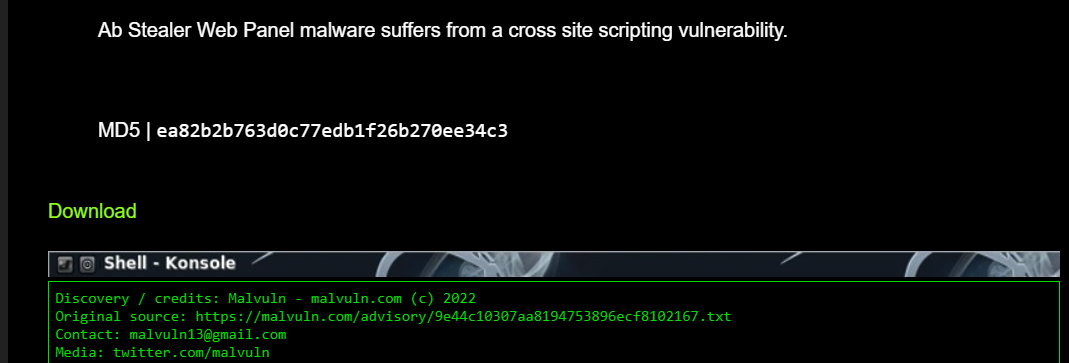
AB Stealer
The AB Stealer is a keylogger that works through the browser and enables the collection of user passwords. We have seen it mentioned on the Cracked.to forum, where it was recommended by cybercriminals for personal use.
This malware was also advertised on an exploits site, in a post featuring a tutorial and a download link.
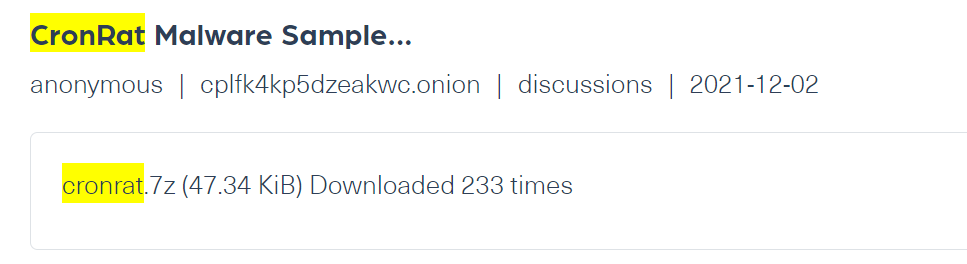
CronRat
This malware attacks through the Linux calendar. It enables threat actors to steal credit card information by installing online payment skimmers. It was mentioned in carding shops and forums on the Tor network.
In the example below, crawled from a carding forum about 4 months ago, you can see that a threat actor posted a CronRat malware sample ready for download.
When defending against malwares, the deep and dark web play an important role in monitoring the activities of threat actors and cybercriminals. Some of them use the darknets as a safe space to trade, advertise and discuss malwares. either exchanged or as a service.
Leading cyber threat intelligence companies use our Cyber API and Cyber Segmentation API, to analyze and identify specific exploits or cyber threats that can pose a risk to organizations. Monitoring these data feeds helps understanding the context and plans around malwares, the technology in use and mentions of companies ahead of attacks.