How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

As 2023 draws to a close, it’s time to look back at all we have seen taking place on the web’s most enigmatic and dynamic spaces – the deep and dark web.
This year, we’ve witnessed significant shifts in the activities and strategies employed in the dark web, from the rise of hacktivism to the increased use of advanced technologies by cybercriminals. This report aims to shed light on these critical developments, offering insights into the tactics, tools, and trends that define the current state of the dark web.
Whether you’re a cybersecurity expert, threat intelligence analyst, or simply someone curious about the hidden layers of the internet, this report will provide an overview of the key changes and challenges we have witnessed in this shadowy digital realm.
Over the past year, we have seen a significant increase in the activities of hacktivist groups. These groups target organizations for political or social reasons, often driven by nationalist ideologies. This trend already started in 2022 with the Russia-Ukraine war, which saw pro-Russian and pro-Ukrainian hacktivists engaged in cyber warfare. Similar patterns emerged following the Israel-Hamas conflict, with various hacktivist groups targeting each other’s strategic assets.
This rise in hacktivism is a global phenomenon, which is continuously spreading as social crises evolve. Currently, most hacktivist attacks involve DDoS attacks and website defacements. However, we’re starting to see that more sophisticated groups are attempting server and system penetrations, intending to cause more significant damage through data breaches.
Hacktivist activities are present on the dark web, where groups often use platforms like Tor and Telegram to coordinate and execute real-time cyber attacks against their targets. These groups also turn to alternative social media platforms to spread their ideologies and publicize their attacks.
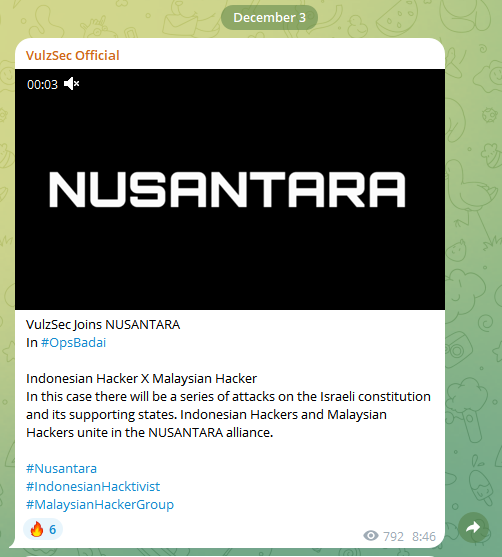
Some of the more renowned hacktivist groups include Killnet, Anonymous, VulzSec, and Lazarus Group.
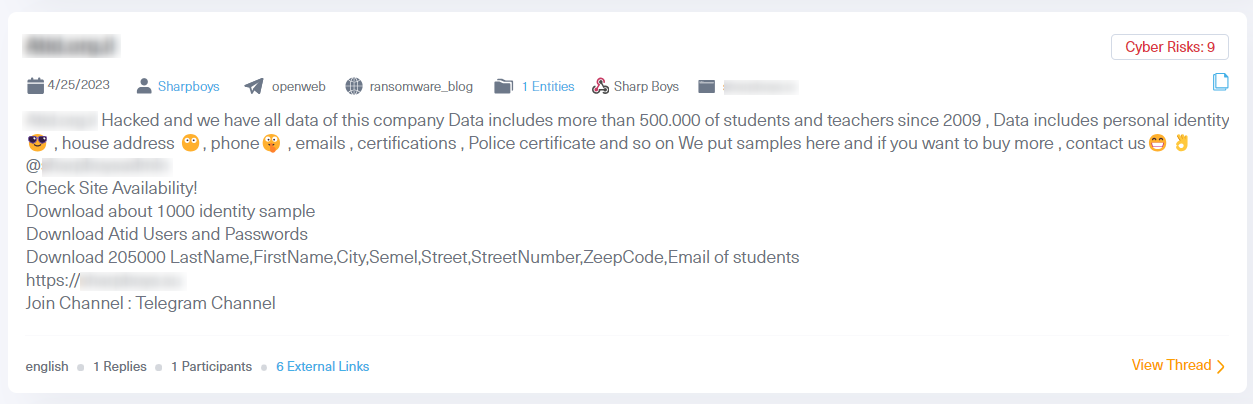
The dark web has always been known as a prime place to trade and spread compromised data. Over the past year, stealer logs have become the most popular form of compromised assets. These logs, which are obtained by infostealer malware, include information stored on a victim’s browser. This includes cookies, usernames, and passwords from visited websites, IP addresses, and various operating system details. Cybercriminals exploit this data to gain unauthorized access to accounts and platforms, including servers, posing a major risk to organizations. The breach of such assets escalates the risk of data security threats, account takeovers, identity theft, and possible security breaches.
Dark web marketplaces, often referred to as datastores, serve as a primary hub for trading stolen digital credentials, commonly known as stealer logs. The most popular datastore today is “Russian Market”, which is known for its affordability, where you can purchase one log for as little as 10 USD. However, we have seen a new trend where cybercriminals share dozens and even thousands of such log credentials at no cost at all in dark web hacking forums and more notably in Telegram groups.
With every introduction of a transformative technology comes the fear that they will be abused by cybercriminals. This was no different when the first announcement of LLM models and ChatGPT versions came out in December 2022. It was clear that this new disruptive technology could be exploited for malicious activities.
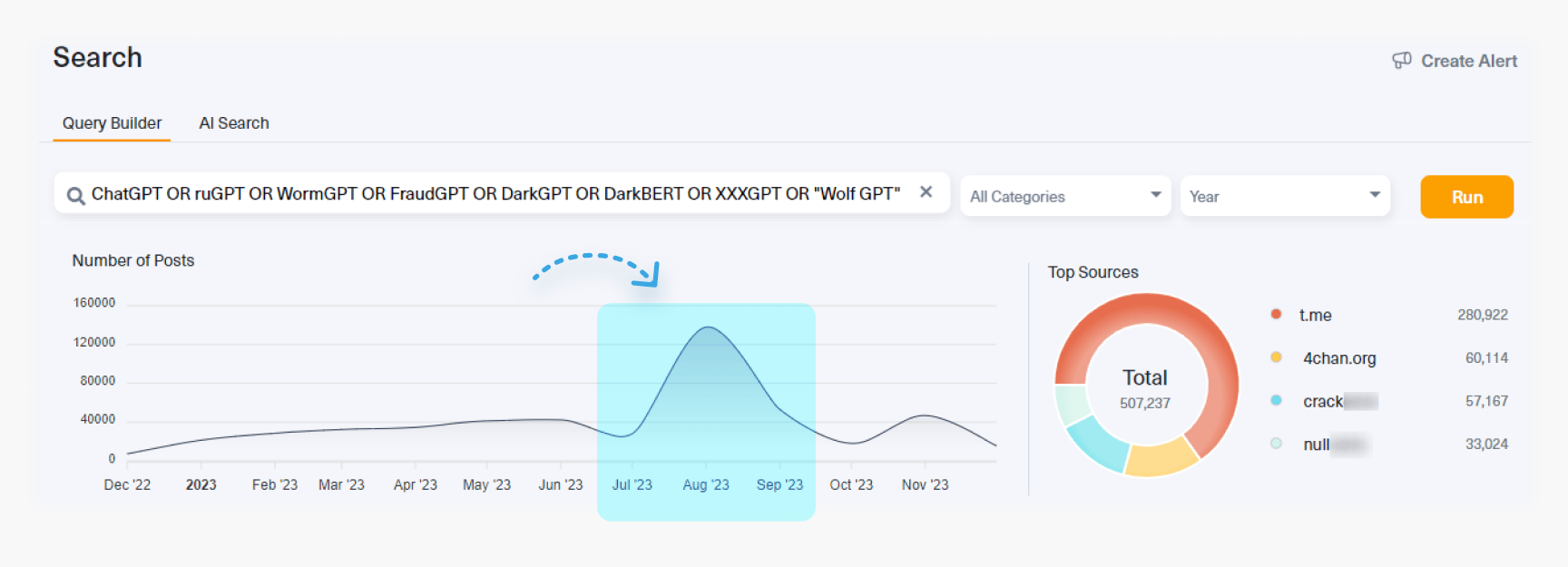
It didn’t take long before these fears materialized when new LLM models were created specifically for malicious purposes. Less than a year later, we have been able to track an increased use of these LLM models, like ruGPT or DarkLLaMa. These models have one thing in common – they operate without the ethical and regulatory constraints that govern models like ChatGPT or Bard.
The malicious LLM models are used as tools to carry out various malicious activities, such as:
The potential risk is huge and requires vigilant attention through continuous threat intelligence monitoring and mitigation strategies.
In the image below, taken from our dark web monitoring tool Lunar, you can see greater use of dark web LLM models, which have been developed in underground laboratories.
One of the less-known trends that has emerged over the past year is the increased use of platforms that document cyberattacks by cybercriminals.
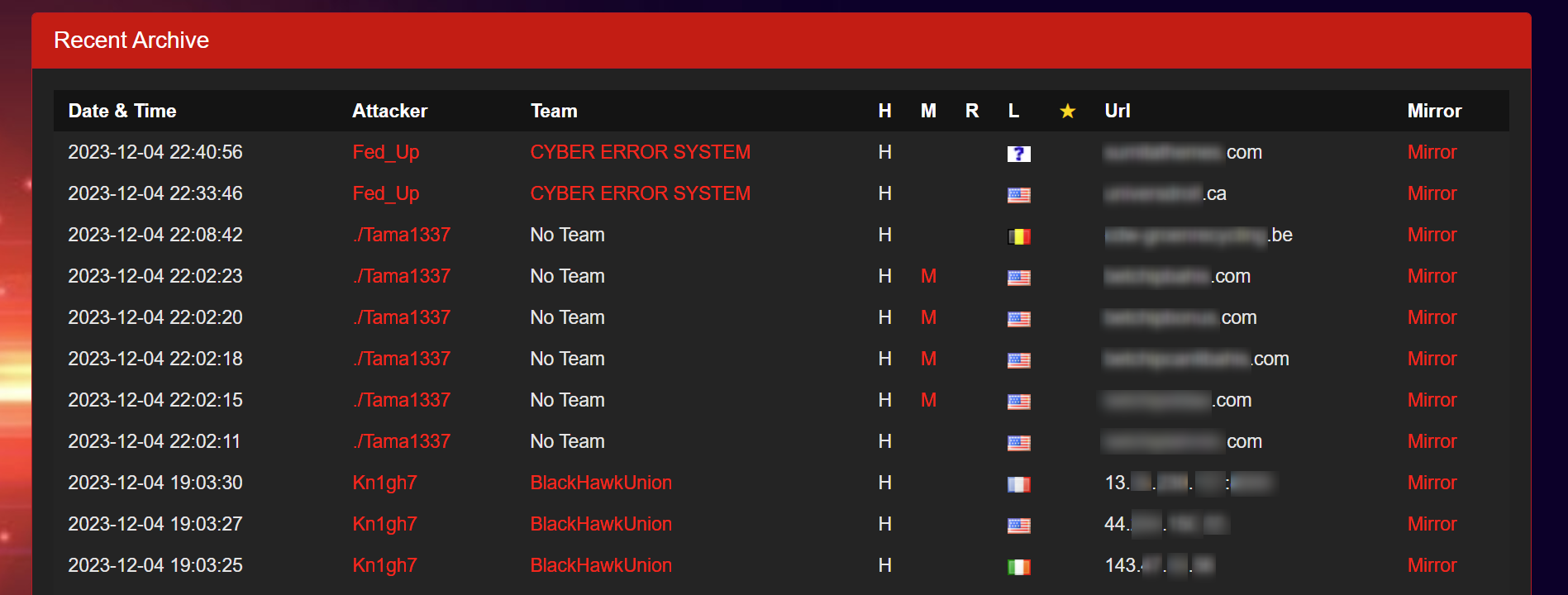
Currently, various platforms serve as databases of recorded cyberattacks on the open web. These platforms, which are known as “Global Cyber Vandalism Mirror Databases” or “Defacement Mirrors,” primarily feature records of website defacements and Distributed Denial of Service (DDoS) attacks. These records are comprehensive, detailing victim information such as URLs, IP addresses, server types, and occasionally, the identities of the attackers.
While these databases are invaluable tools for cybersecurity experts, aiding in research and threat analysis, they are also used by cybercriminals to boost their activities and “brand”.
Cybercriminals frequently use these databases to publicize their illegal activities. They often share links to these databases on the deep and dark web, showcasing their successful attacks. This practice not only glorifies cybercrime but also starkly highlights the ongoing vulnerabilities in cyberspace that organizations and individuals face.
Some notable platforms in this domain include Zone-Xsec, HaxOrID, Defacer Net.
Obtaining data from dark web sites that have implemented advanced security measures, such as CloudFlare protection and sophisticated CAPTCHA systems, has become a notable challenge. Popular platforms such as XSS, WWH-Club, and Hackforums have stepped up their security measures. Take for example XSS, this website has introduced a more advanced CAPTCHA system in the past year. Some dark web sites, especially those with restricted access or specialized content, have changed their user policies and pricing structures. An example of that is Russian Market, which has introduced a 100 USD minimum fee for premium services, and implemented charges for specific data access. In response to these evolving challenges, our team at Webz.io is dedicated to the ongoing development of innovative strategies. These strategies are designed to navigate these security measures effectively, ensuring that our data collection processes remain stable and robust.
Law enforcement agencies across the U.S. and Europe have intensified their efforts to crack down on illicit activities on the dark web. These campaigns involved the arrest of nearly 300 individuals, most of whom are involved in the operation of dark web drug marketplaces.
Some of the popular marketplaces that have closed this year include Genesis, Monopoly Market, ASAP, Alphabay, and Tor2Door. These growing law enforcement efforts reflect a growing commitment to combating cybercrime, especially in the realms of drug trafficking, cyberattacks, and other illicit transactions conducted on the dark web. Such actions send a strong message that law enforcement agencies are actively working together to track down and bring to justice those who operate in the hidden corners of the internet for criminal purposes.
Another trend we’ve seen this year is that cybercriminals are now using chat applications, such as Telegram, more than other dark web platforms. One possible explanation for this shift is possibly linked to the action law enforcement agencies have taken against dark web platforms, such as marketplaces.
Among the popular chat applications used by cybercriminals is Telegram, due to its robust end-to-end encryption, which offers a secure channel that allows them to operate illegal activities of almost all kinds in relative anonymity. These activities range from discussions about hacking, the sale of counterfeit goods, and the dissemination of leaked data to radical conversations. We believe this trend is expected to continue and even intensify as law enforcement agencies step up their efforts to combat dark web operations. Regardless, it’s become very clear that encrypted chat applications have become indispensable for cybercriminals, influencing the dynamics of online criminal activities.
Reflecting on the key dark web trends of 2023, it’s clear that the cybercriminal ecosystem on the deep and dark web is not just surviving but thriving, adapting rapidly to new technologies and global events.
From the rise of hacktivism fueled by geopolitical conflicts to the innovative use of generative AI for malicious purposes, these trends highlight the ever-changing nature of cybercrime and the dark web.
As the dark web continues to evolve, so must our cyber strategies to combat its illicit activities. This report serves as a crucial reminder of the persistent and ever-evolving threats that lurk in the depths of the internet, urging us to stay informed by monitoring the dark web and taking action in the face of these challenges. As the battle against cybercrime continues into 2024, so is the need to understand these trends and take proactive measures to safeguard our organizations and people in the digital world.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.