How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Social engineering attacks pose a serious threat to organizations worldwide as they involve cybercriminals using psychological manipulation techniques to exploit human weaknesses to obtain sensitive information. Threat actors also use social engineering as the vector for executing malicious attacks. In fact, the global average cost for a data breach arising from social engineering techniques is more than $4.55 million per a recent IBM Security report.
With these serious consequences in mind, we used Lunar, our dark web monitoring and data breach detection tool, to search for trending discussions around social engineering tools and techniques. This article highlights the results of that search and threat actor tactics companies should focus on when updating their security strategies.
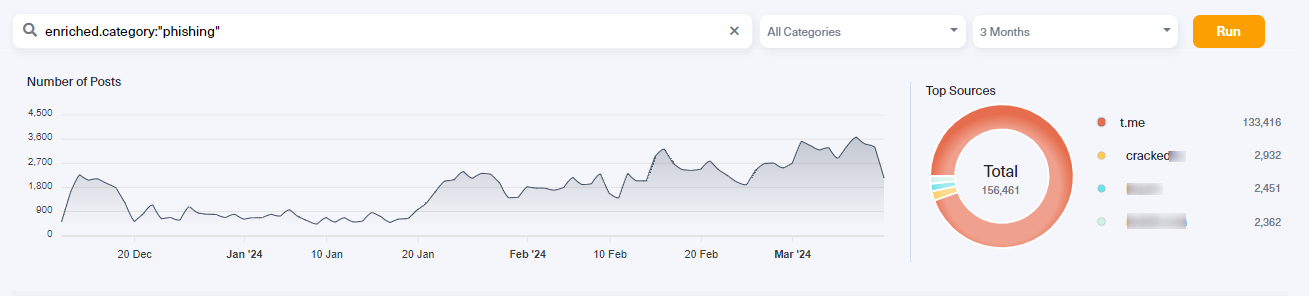
Cybercriminals talk about many different tactics for employing social engineering attacks. With Lunar, we discovered the most discussed social engineering tactics on the dark web at this time:
Phishing remains one of the most used social engineering tactics. Cybercriminals leverage various forms of communication — e.g., email, website, SMS, social media — to trick individuals into divulging sensitive information, such as login credentials or financial details. These communications typically include one or more malicious links where victims download infected files or enter sensitive information into a fake form. As the cyber world evolves, so do phishing methods, sprouting new tactics such as vishing, smishing, and crypto phishing.
A social engineering technique that often involves impersonation and fabricating realistic scenarios or pretexts to manipulate individuals into divulging sensitive information. For example, a threat actor might impersonate a member of law enforcement or a tax official, telling the victim if they don’t pay back due taxes immediately, they will go to jail. The criminal would scare the victim into divulging account numbers and financial details.
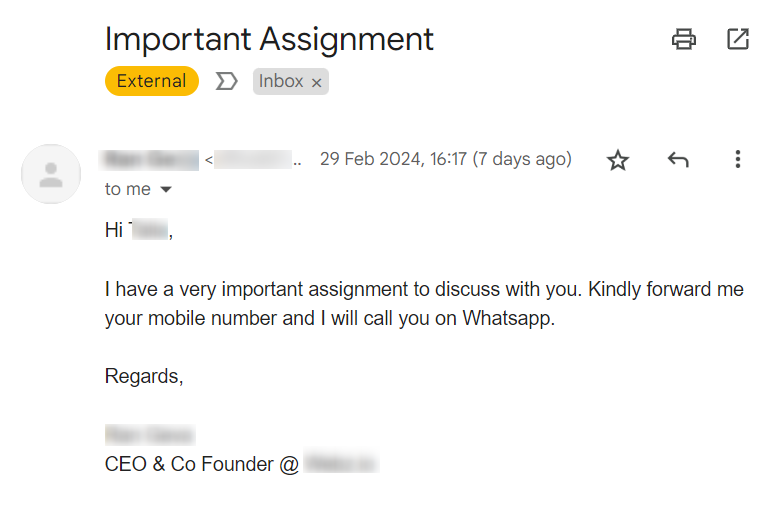
Business email compromise (BEC) is a targeted form of social engineering that relies heavily on pretexting. A threat actor creates a scenario involving a high-level executive or a company representative who has authority over the targeted victim. The criminal might ask the target via email to transfer funds to a fraudulent account, pay a fake invoice, or reveal sensitive information. The fraudster spoofs the email or hacks the executive’s account to make the email look genuine.
Baiting is a deceptive social engineering tactic where an attacker entices individuals with false promises to lure them into giving up sensitive information or infecting their system with malware. Baiting scams often include free downloads, like games, music, or movies. Some threat actors might entice the victim with offers for free phone upgrades or deceptive online ads. If successful, the threat actor can sell the stolen information on dark web marketplaces.
Hackers utilize designated sections within hacking forums on the dark web that focus on social engineering. They use information from these forums to mastermind social engineering attacks. These forums act as hubs for cybercriminals to exchange tactics and refine strategies, enhancing their ability to manipulate individuals. Some of the ways bad actors use the dark web for social engineering attacks include:
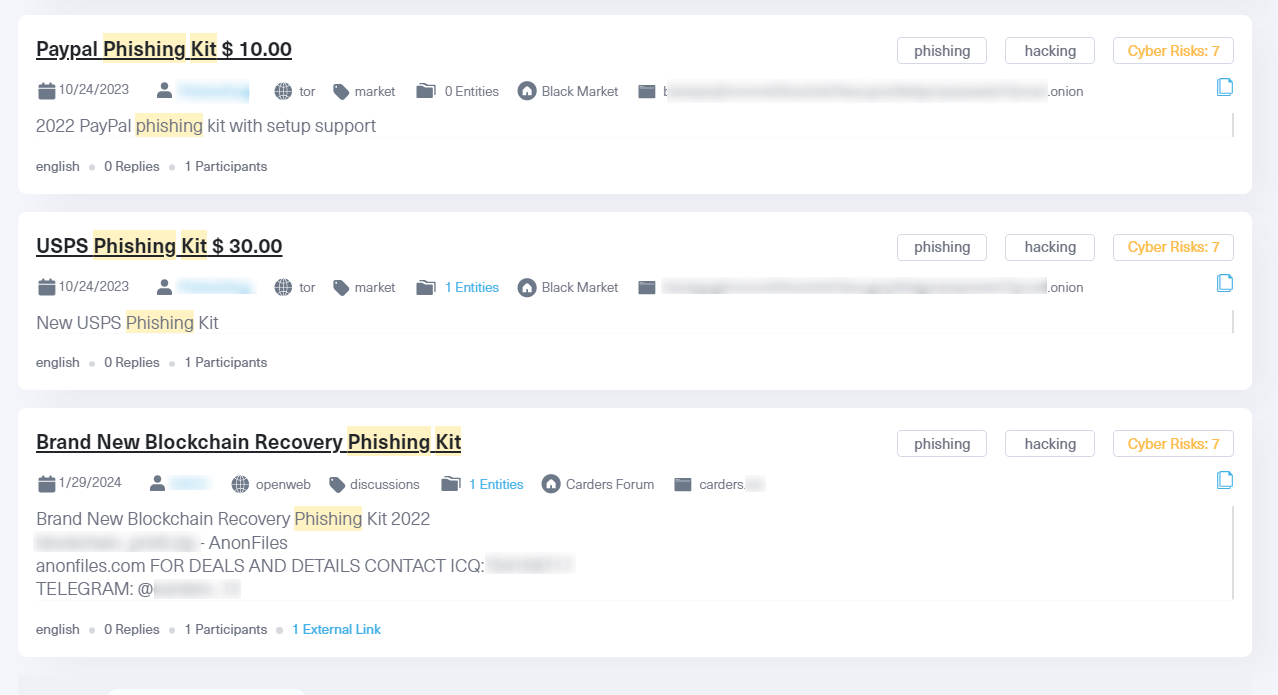
A phishing kit contains tools that allow bad actors to quickly create a large amount of fake web pages or emails that look authentic. Many cybercriminals sell ready-to-use phishing kits on dark web forums. These kits typically include code and scripts, email templates, and fake login pages.
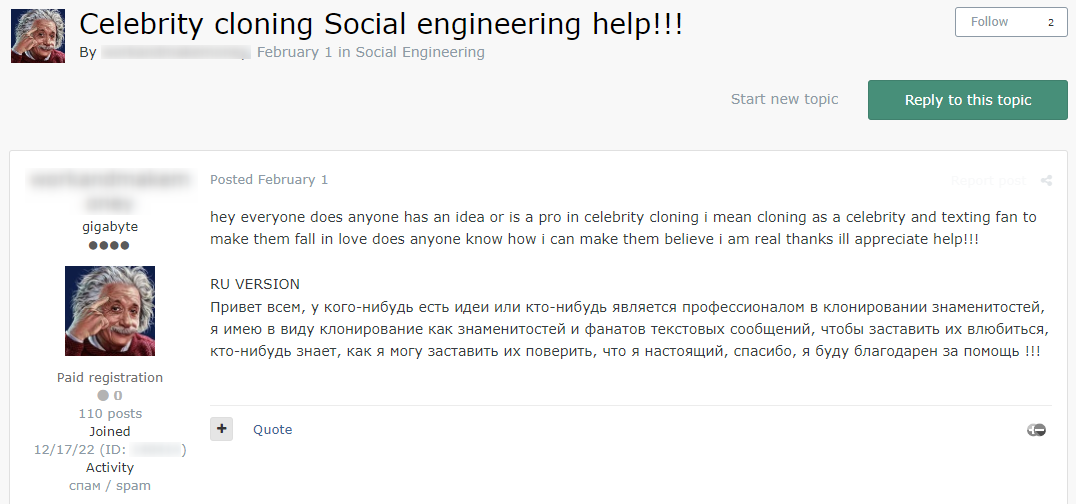
Less experienced cybercriminals turn to specialized services sold on dark web forums and marketplaces to help them conduct their attacks. These services range from developing malware and hacking tools to crafting persuasive phishing and pretexting campaigns.

Hacking communities on the dark web serve as a hub for threat actors to connect. Individuals with malicious intent can seek assistance from members of encrypted forums and underground communities, recruiting accomplices for their social engineering attacks.
Social engineering attacks are exceptionally dangerous for companies and organizations as they exploit human vulnerabilities, bypassing even the most advanced technical defenses. By regularly monitoring the tactics newly emerging within the shadows of the dark web, organizations can develop effective countermeasures and mitigate potential risks that lead to significant monetary losses. Webz.io’s dark web monitoring tool Lunar helps cyber analysts and security teams stay ahead of the game.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.