How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

The cryptocurrency revolution is in full swing, with the number of global owners skyrocketing to half a billion by 2024. But with this surge in popularity comes a hidden threat lurking in the shadows of the digital gold rush: cybercrime.
While the appeal of cryptocurrencies is undeniable, a staggering $24.2 billion worth of cryptocurrency was funneled through illegal channels in 2023 alone, according to a recent Chainalysis report. This begs the question: what type of illicit activities are taking place in the dark corners of the web, and what’s the role of crypto?
Join us as we uncover how cybercriminals are using cryptocurrencies for a variety of purposes, and explore the best practices to monitor illicit crypto activities.
2023 witnessed a surge in ransomware attacks, fueled by the anonymity and ease of transaction offered by cryptocurrency. Criminals use malicious software to encrypt a victim’s data, demanding a ransom in cryptocurrency for its release. Failure to pay often results not only in losing access to vital data, but also in the exposure and leaking of such files across the dark web.
Recently one of the most notorious RaaS ransomware groups, LockBit, was seized by a joint effort of multiple law enforcement agencies in February 2024. According to an Europol report, the authorities froze more than 200 crypto addresses linked to the group.
The group would often publish their wallet addresses in their ransom notes, see in the next image, demanding payment will be made there.
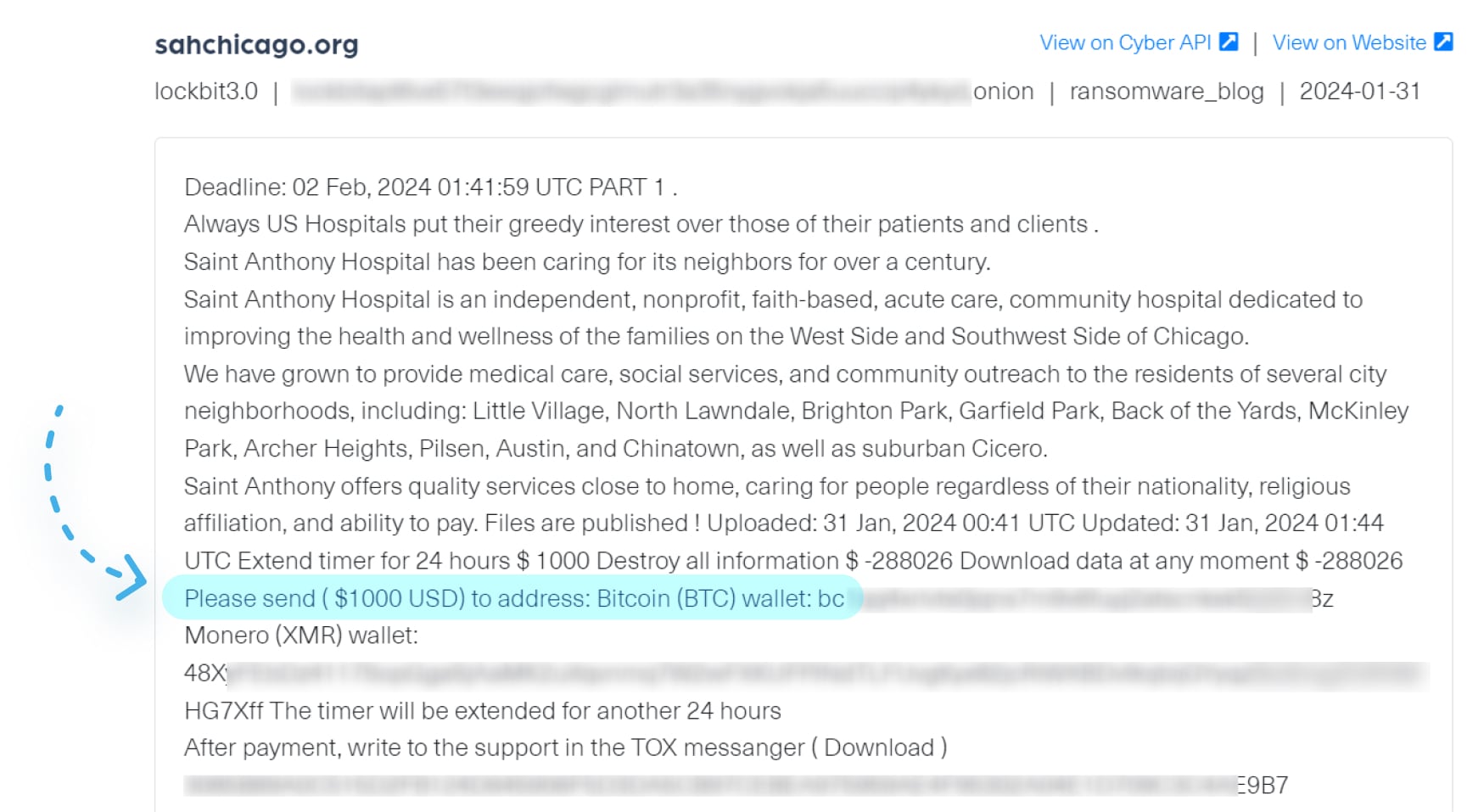
Darknet marketplaces are online platforms that operate on the dark web, facilitating the buying and selling of various illicit goods and services, including drugs, weapons, stolen data, hacking tools, counterfeit currency, fake passports, and more. Cryptocurrencies play a crucial role in enabling these illicit activities on dark web marketplaces and forums, as they are often used as the primary transaction currency for one main reason – anonymity.
But can we still keep track of who is posting wallet addresses and where? To answer that question, we used Lunar, Webz.io’s dark web monitoring tool, to monitor crypto addresses mentioned in dark web forums and marketplaces.
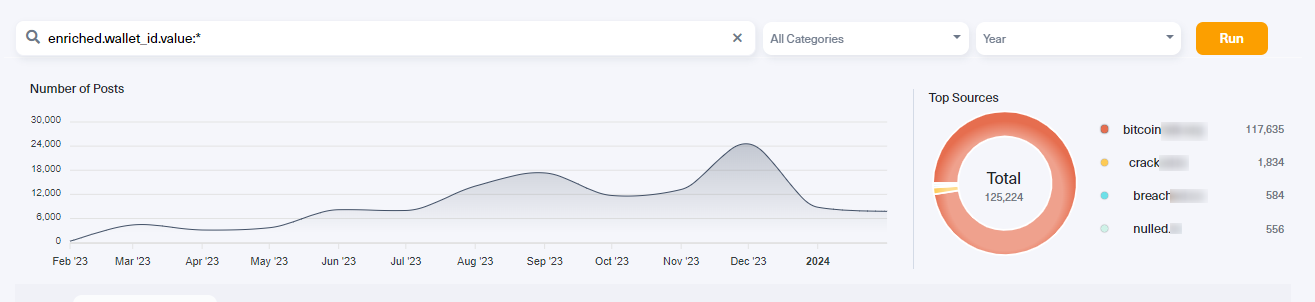
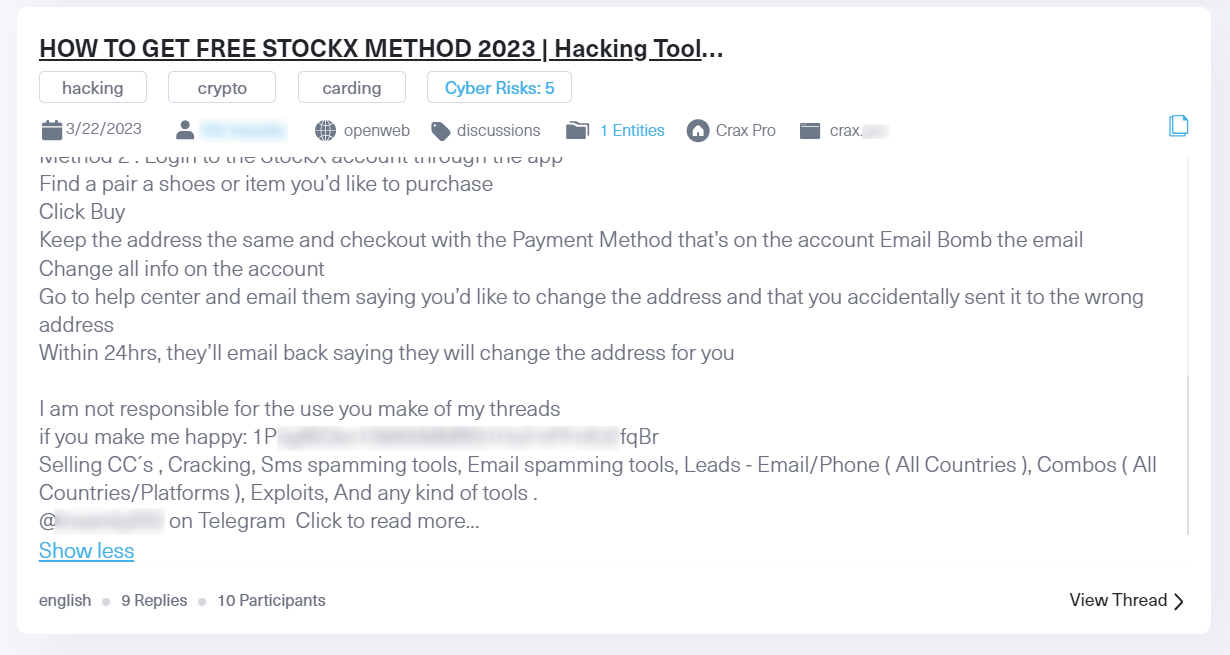
The results allowed us to discover a threat actor on the dark web advertising the sale of stolen credit cards and various kinds of hacking tools. By running the wallet address the threat actor provided, we found many more different accounts using the same address. We have even traced the threat actor’s Telegram account, which can be used for actor profiling.
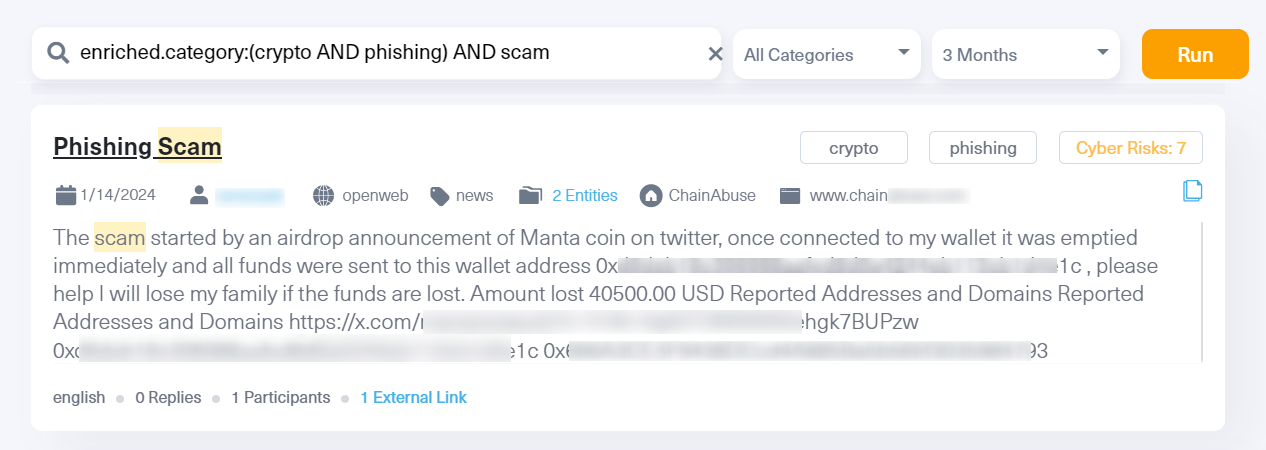
The world wide web is a breeding ground for various scam activities, including fraud, phishing, extortion. A lot of it is taking place on the dark web and is largely carried out with cryptocurrnecies.
Some popular cryptocurrency scams on the the dark web include:
The key difference between a regular scam and a cryptocurrency scam is the difficulty in tracing the culprits due to the use of untraceable crypto wallet addresses. This makes it crucial to stay vigilant and keep an eye on new scams online, as they can have a much greater financial impact that is nearly impossible to remedy.
We use Lunar’s “Crypto” and “Phishing” tags to keep track of phishing scams on the open and dark web as they emerge.
As more radical groups turn to Telegram groups and alternative social media platforms to conduct their activities, the way they handle the matter of funding changes as well. Despite efforts to freeze and sanction terror-related cryptocurrency accounts, groups find ways around such restrictions, mainly in the forms of crypto mixing and tumbling, laying transactions and using stolen identities.
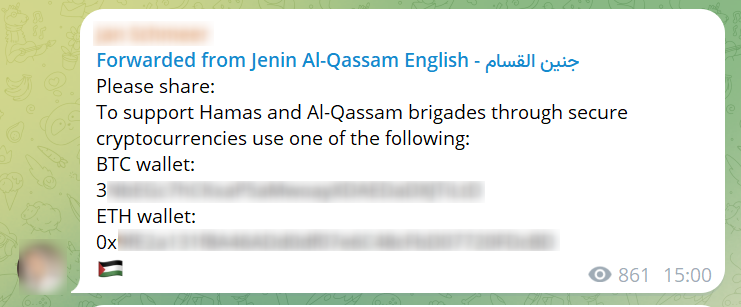
While the deep and dark web offer fertile ground for crypto-based criminal activity, identifying associated addresses within this vast landscape can feel akin to searching for a needle in a haystack. With advanced dark web tools like Lunar, threat intelligence analysts can effectively monitor crypto crime. These tools streamline the process, allowing analysts to discover, investigate, and monitor suspicious cryptocurrency addresses on the dark web with just a few clicks, ultimately generating actionable data crucial for crime prevention.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.