How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Business email compromise is an email cybercrime scam that targets companies’ business email addresses in order to defraud the company. It is a common social engineering scam, which is conducted by spoofing or hacking the email account of a senior employee or executive. This information is then used by cybercriminals to send an email that appears to come from a known source and make a legitimate request in which they instruct the unknowing victim to approve payments, release client or employee data or simply transfer money to the scammer’s bank account. The goal of a BEC is either to defraud a company of funds or to obtain personally identifiable information (PII) to be used in future attacks.
According to the FBI’s Internet Crime Complaint Center, Americans lost a record $16.6 billion to scammers and cybercriminals in 2024. That total includes BEC, ransomware, and cryptocurrency scams, and marks a 33% jump from the previous year. While ransomware and crypto theft continue to dominate headlines, Business Email Compromise remains one of the most costly and underreported threats, responsible for $2.77 billion in losses last year.
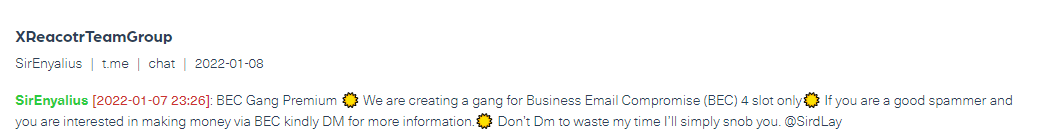
The first step cybercriminals and hackers take in conducting a BEC scam is to obtain the Personally Identifiable Information (PII) of an executive.
Take for example an executive’s email account. To run a BEC scam, the attacker typically starts by getting into the executive’s email — which is how they join meetings, access platforms, and get things done. The compromised email address leaves the executive, as well as the company, at risk and open to attacks and fraud. Below is an example of Account Compromise, found on hacking forums, marketplaces, and Telegram groups/channels where a Telegram actor offers to sell PII for committing BEC scams.
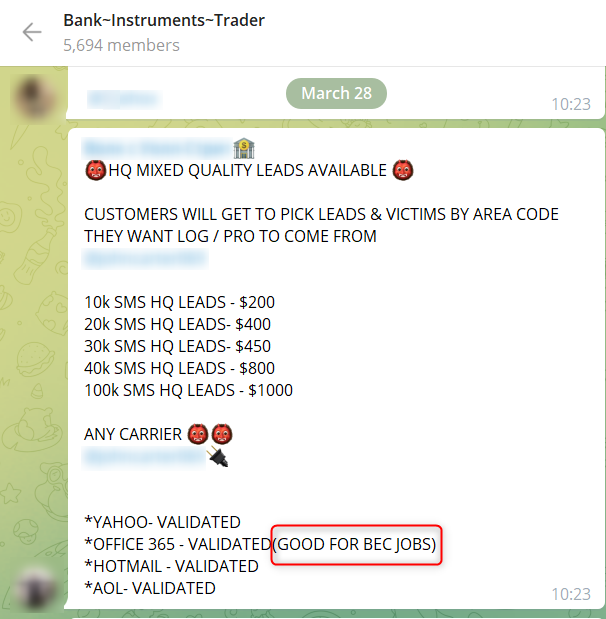
There are two main ways to obtain executives’ PIIs – social engineering and cyberattacks.
Social engineering targeting PII
Social engineering includes a wide range of malicious activities conducted through human interactions, in which cybercriminals use psychological manipulation to trick users into making security mistakes or divulging sensitive information.
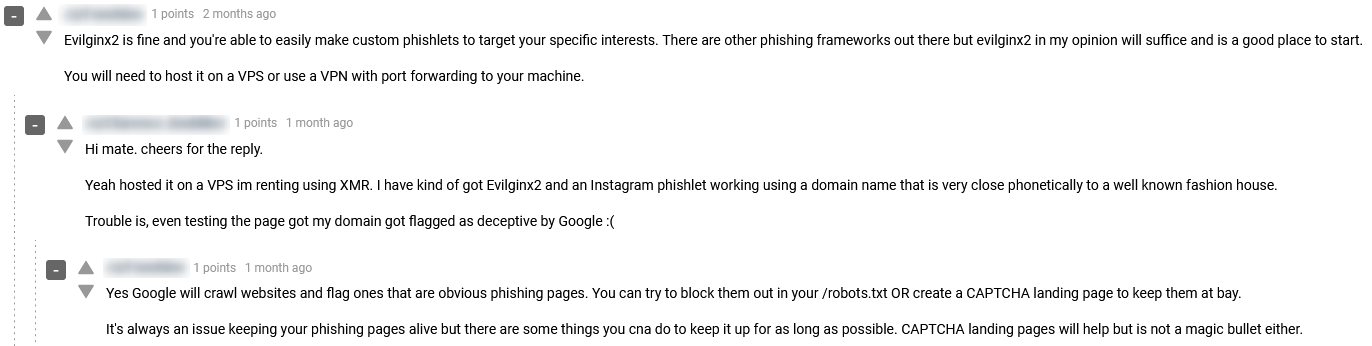
Evilginx2 is considered a Man-In-The-Middle attack, taking its name from the practice of hackers to put themselves between a website and the user making it seem as if the exchange of information is normal. Using Evilginx2, cybercriminals can phish login credentials along with session cookies to bypass two-factor authentication, and by that gain access and control business accounts or an executives’ email, as part of their BEC scam.
The screenshot below shows a thread of a discussion between threat actors over the Evilginx2 social engineering method on the dark web hacking forum Dread.
Cyberattacks targeting PII
The fraudster gets access to personal or sensitive information about individuals, usually the CEO, C-levels and executives. To obtain this information, the fraudsters usually target HR employees who often have access to this type of data or hacking forums where such data is offered for sale. This data may be used at a later stage to launch BEC attacks such as CEO Fraud, a spear-phishing email attack in which the attacker impersonates the CEO.
This is a common way to obtain compromised accounts belonging to executives, which can be used to conduct BEC scams in the future.
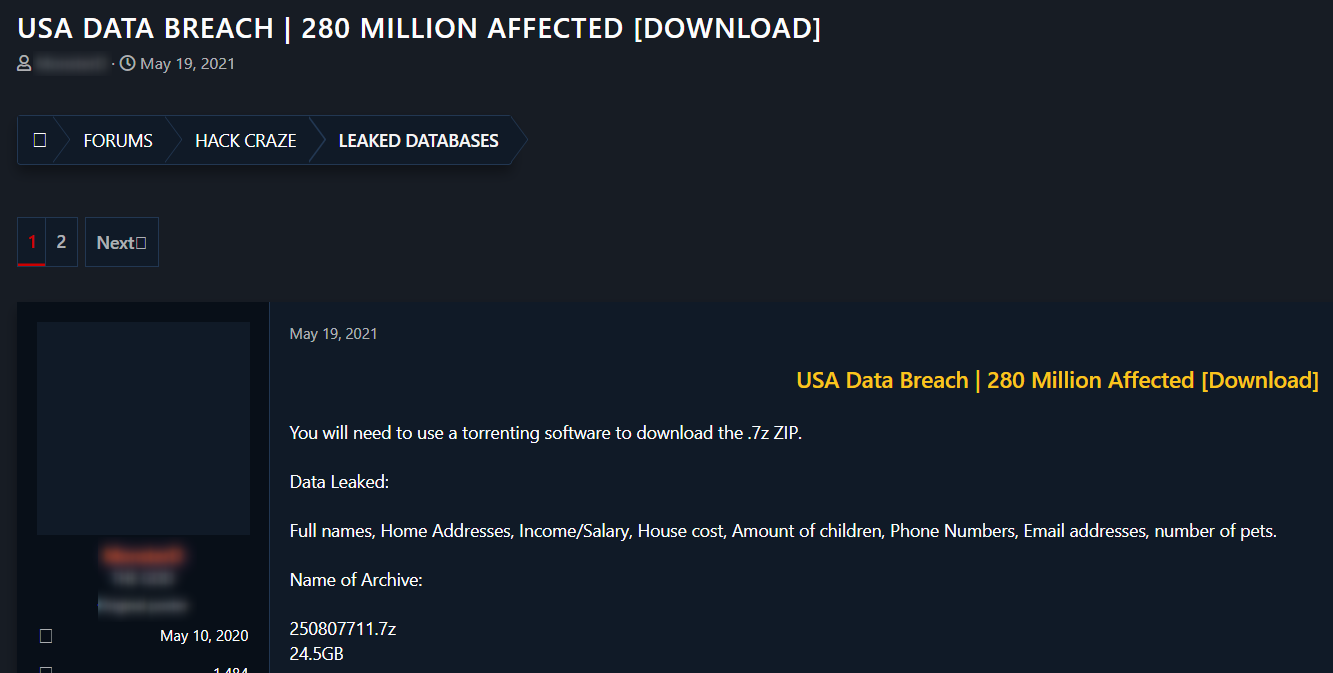
This is an example of a post where a hacker published a 280M data breach which includes email addresses, phone numbers, home addresses and other PIIs.
Once the fraudsters gain access to a compromised email account, they can conduct the BEC scam by either of the following ways:
It is important to note that these scams contain no malicious links or attachments that direct the employees or executives to a harmful virus page. They solely rely on human interaction as they impersonate the victim. That’s why BEC scams often pass under the radar of traditional anti-malware and other cybersecurity software such as antiviruses.
Fraudsters pose as the CEO or executive of a company either by email or by using the company’s internal chat platform. They then request funds to be transferred to their account.
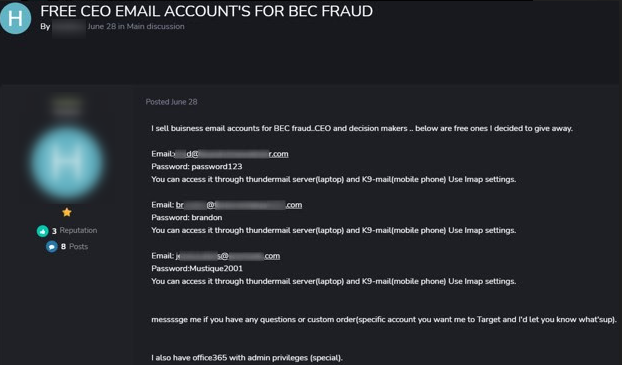
The following post shows a threat actor selling CEO accounts for BEC fraud on carding forum carder.tv:
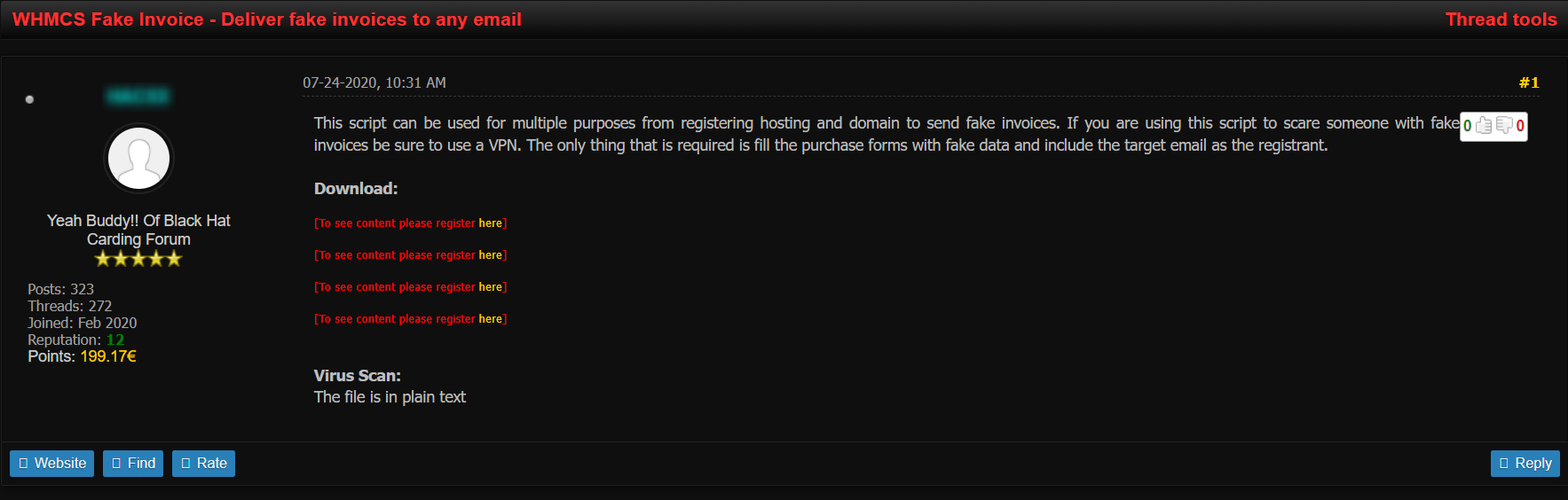
The False Invoice Scheme often targets companies with foreign suppliers. The scammers pretend to be their overseas supplier and request funds to be transferred to their accounts.
The screenshot below shows a threat actor posting a Fake Invoice script for multiple uses on dark web hacking forum Blackhat Carding.
Another way to carry out BEC scams is the Legal Representative Impersonation or Attorney Impersonation. In this BEC scam the scammers present themselves as a lawyer or a legal representative. The scam is typically aimed at junior employees, assuming that they are not knowledgeable enough to question the validity of the request.
Lunar, Webz.io’s dark web monitoring platform, helps security teams spot signs of BEC risk early. It surfaces exposed corporate PII across dark web forums, marketplaces, and Telegram channels. We’ve used it to identify cases where threat actors discuss phishing techniques, swap credentials, or trade access to business email accounts. These kinds of exchanges often signal that a company is being targeted. With that context, teams can step in and take action before the damage is done.
How significant can financial losses from BEC scams become?
Financial losses add up fast. In 2021, U.S. companies reported $2.4 billion in losses tied to BEC attacks. That figure doesn’t even include the extra time, legal work, or recovery efforts these scams often trigger. For a small company, one well-executed scam can wipe out months of progress.
How do cybercriminals obtain the PII of executives for BEC scams?
Cybercriminals either trick someone into sharing PII or buy it from a dark web marketplace, data store, or illicit Telegram chat, while phishing emails are still a go-to. Some attackers go after HR teams because they have access to sensitive data. Others use leaked info from old breaches. Once threat actors can identify names, roles, and email habits, launching a convincing business email compromise scam is easy.
Why are BEC scams often difficult to detect with traditional cybersecurity software?
The way BEC scams are engineered makes sure that there’s nothing technical to catch. No malware, no shady links – just a message that sounds like it came from someone inside the company. Most tools don’t flag that. Business email compromise works by mimicking everyday communication, not breaking rules.
How do cybercriminals collaborate and utilize the dark web for BEC activities?
Cybercriminals treat the dark web like a workshop. There are forums where people behind BEC attacks trade templates, sell access to inboxes, and swap ideas. There are even walkthroughs for people just getting started. Cybercriminals use the dark web to both buy tools and learn how to use them.
What can organizations do to reduce the risk of BEC scams?
To reduce the risk of BEC scams, organizations should combine employee training, verification protocols, and technical defenses. Educate staff to recognize suspicious emails and require secondary confirmation for financial or urgent requests. Strengthen email security by implementing SPF, DKIM, and DMARC to block unauthorized or deceptive email activity. Additionally, monitor for exposed credentials and sensitive data on the dark web. Tools like Lunar provide early warnings that help identify risks before attackers can exploit them. This multi-layered approach—awareness, process controls, and proactive monitoring—significantly strengthens an organization’s ability to detect and prevent BEC attacks.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.