How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Mobile devices have seamlessly integrated into everyday life, providing unparalleled convenience and connectivity. With smartphones and tablets increasingly becoming indispensable tools for numerous tasks, the importance of robust mobile security cannot be overstated. In 2023, Kaspersky noted a substantial rise in attacks targeting mobile devices. The year saw nearly 33.8 million attacks, representing a 50% surge compared to the previous year. Organizations need to prepare and maintain an effective mobile security strategy using dark web monitoring to understand current and evolving mobile device threats.
In the ever-evolving landscape of cybersecurity, dark web monitoring is crucial to understanding and mitigating threats aimed at mobile devices. Cybercriminals constantly look for new ways to exploit mobile vulnerabilities, often finding what they need on dark web hacking forums. These forums host countless conversations about nefarious topics, including social engineering techniques, hacking, and fraud. Threat actors also discuss the proliferation of malware designed specifically to target mobile devices. These malicious activities often lead to the leakage of sensitive data, such as device information, user login details, and financial data. Threat actors can sell this information on dark web marketplaces for profit or use it for other malicious activities like account takeover (ATO) and credit card fraud.
We used Lunar, our dark web monitoring and data breach detection tool to analyze discussions on the dark web, looking specifically at the most widespread threats related to mobile devices. We used tags supported by Lunar, which include hacking, malware, phishing, and data breach. Our findings indicate a noticeable increase in discussions and popularity related to these categories, as illustrated in the graph below.
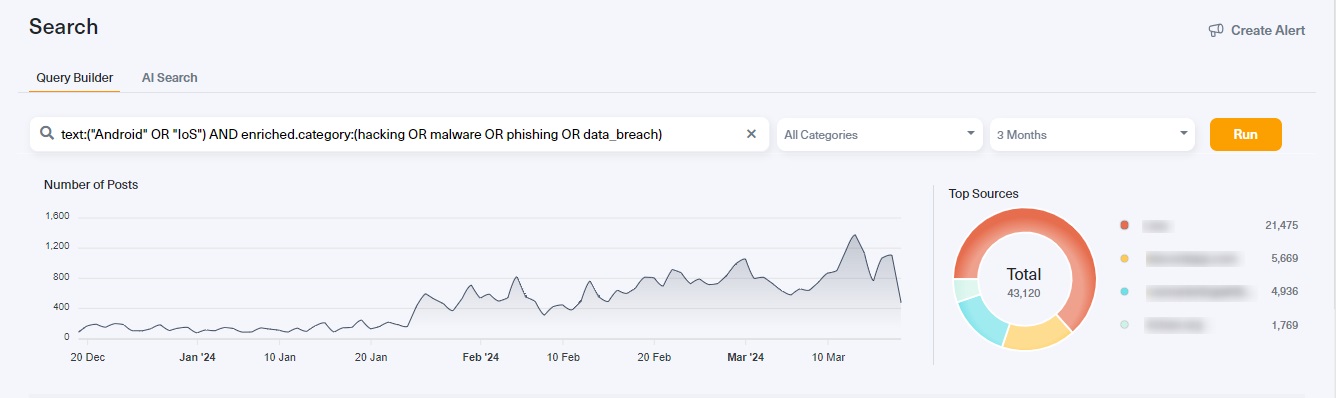
Cyber analysts and security teams can use dark web monitoring to accurately identify various indicators of mobile threats. These indicators include discussions on hacking forums about mobile device exploits and malware. These chats often contain detailed information, such as:
You can better mitigate these risks by monitoring the dark web for mobile device threats and integrating this intelligence into your organization’s cybersecurity feeds. But what are the current top risks to mobile devices according to cybercriminals? With the help of Lunar, we identified three relevant topics discussed frequently on the dark web at this time:
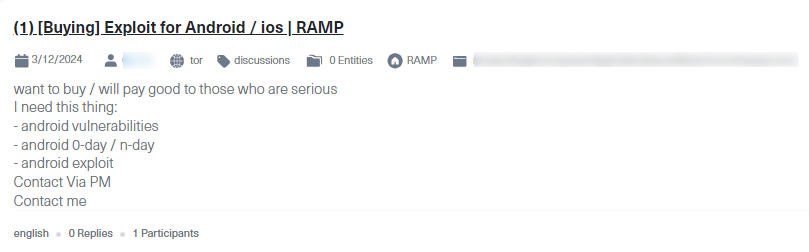
As mentioned above, hackers often discuss and trade mobile device vulnerabilities and exploits that can lead to severe consequences, especially when zero days are part of their attack plan. Below is a screenshot of a thread started on the RAMP hacking forum, where a threat actor wants to buy Android/iOS exploits or zero-day vulnerabilities. A zero-day vulnerability is a vulnerability not known to have been used or seen before, and therefore can be exploited until it has been discovered and patched.
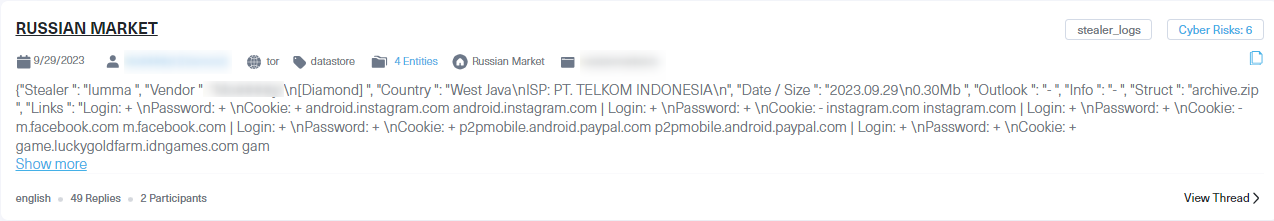
Info-stealer malware pose a significant threat to mobile devices. Once a mobile device becomes infected with an info-stealer, sensitive data like user login credentials, cookies, and device information almost immediately transfer to the threat actor’s remote server. The info-stealer puts the victim at risk of fraudulent activities like ATO and credit card fraud. This data, stored as a file known as a stealer log, is often sold on darknet marketplaces like the Russian Market. Below is an example of a stealer log containing exposed passwords and cookies from various domains, such as PayPal or Apple, accessed on a mobile device.
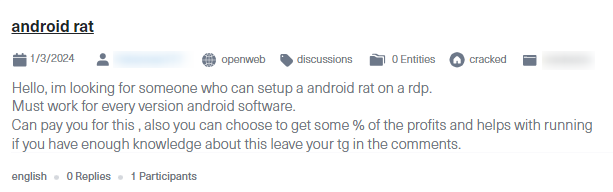
In the screenshot below, you can see a thread on Cracked, a known hacking forum, where a threat actor specifically seeks a Remote Access Trojan (RAT) that can target every Android version. RAT is a type of malware that grants threat actors the ability to interact with the infected device as if they were the owner —e.g., seeing the screen, typing, capturing screenshots. The cybercriminal who created the post offers to pay for the RAT and share a percentage of the profits with the malware developer for their help in running the cybercrime activity. Once a RAT has been installed on a device, it can lead to the installation of additional malware, data theft, or both.
As mentioned earlier, info-stealers pose a significant risk to mobile devices. So, you could start by looking for their existence on mobile devices. We used Lunar to identify logs connected to the Android.com domain for that purpose. We used the following query in the search bar: pii.email_domain:android.com.
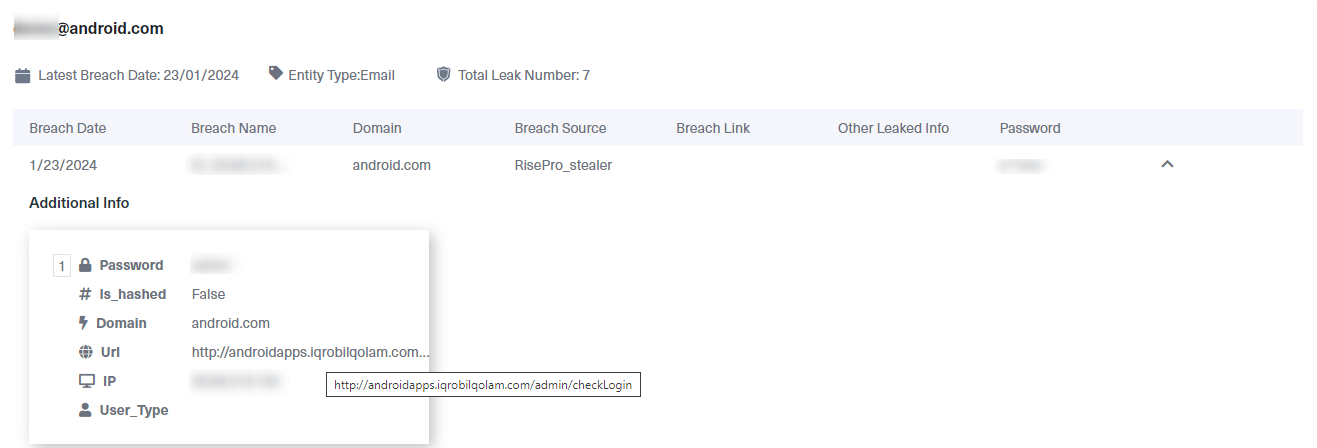
The screenshot below shows one of the info-stealer logs we found with our Lunar search. The log contains information on the info-stealer that infected the device. It also has information extracted from the victim’s device, which includes password, domain, URL, and IP. This mobile device user now faces the risk of fraudulent activities, especially ATO and data theft.
As the threat landscape for mobile devices expands, organizations must take proactive steps to safeguard against cyber threats directed at mobile devices. With a dark web monitoring tool like Lunar, cybersecurity teams can gather the intelligence they need to mitigate the risks we’ve highlighted.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.