How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

The deep and dark web encompasses a vast and hidden digital landscape, featuring a wide range of websites and platforms designed to meet diverse needs and interests, ranging from underground forums to decentralized marketplaces. This hidden ecosystem is fundamentally built on the principle of anonymity, attracting cybercriminals and radicals who exploit these underground platforms to conduct various illicit activities online.
In this article, we will be mapping this ecosystem, highlighting the diverse types of sites and platforms on the deep and dark web, their functions, and how threat actors and cybercriminals utilize them.
Underground forums are a known and popular set of platforms on the deep and dark web, operating as a global hub for cybercriminals. While some forums host discussions about drugs, weapons, extremist topics, and other illicit topics, the majority of these forums focus on hacking-related content and are known as hacking forums.
These forums are frequented by both new and experienced hackers, who use them to share information essential for carrying out cyber attacks and any other fraudulent activities. In addition to knowledge-sharing, these platforms also facilitate the trade in illegal digital items like software exploits, compromised data, and advanced hacking techniques.
Today, there are a large number of hacking forums, which operate not only on encrypted networks such as Tor or I2P, but also on the open web, in order to be accessible to the public as much as possible and attract more audiences. Forums with particularly high traffic can attract a lot of attention, the BreachForums would be a good example of such a forum.
Yet there are many closed forums that look to position themselves as a prestigious closed forum. They look to build their reputation by attracting highly professional and loyal users. They do that by introducing a number of restrictions to filter out unwanted users. For example, some require a fee to create a user, others have a knowledge test that probes the hacking capabilities of new users, or request a consistent professional contribution to the forum. A good example of this type of forum is the XSS forum.
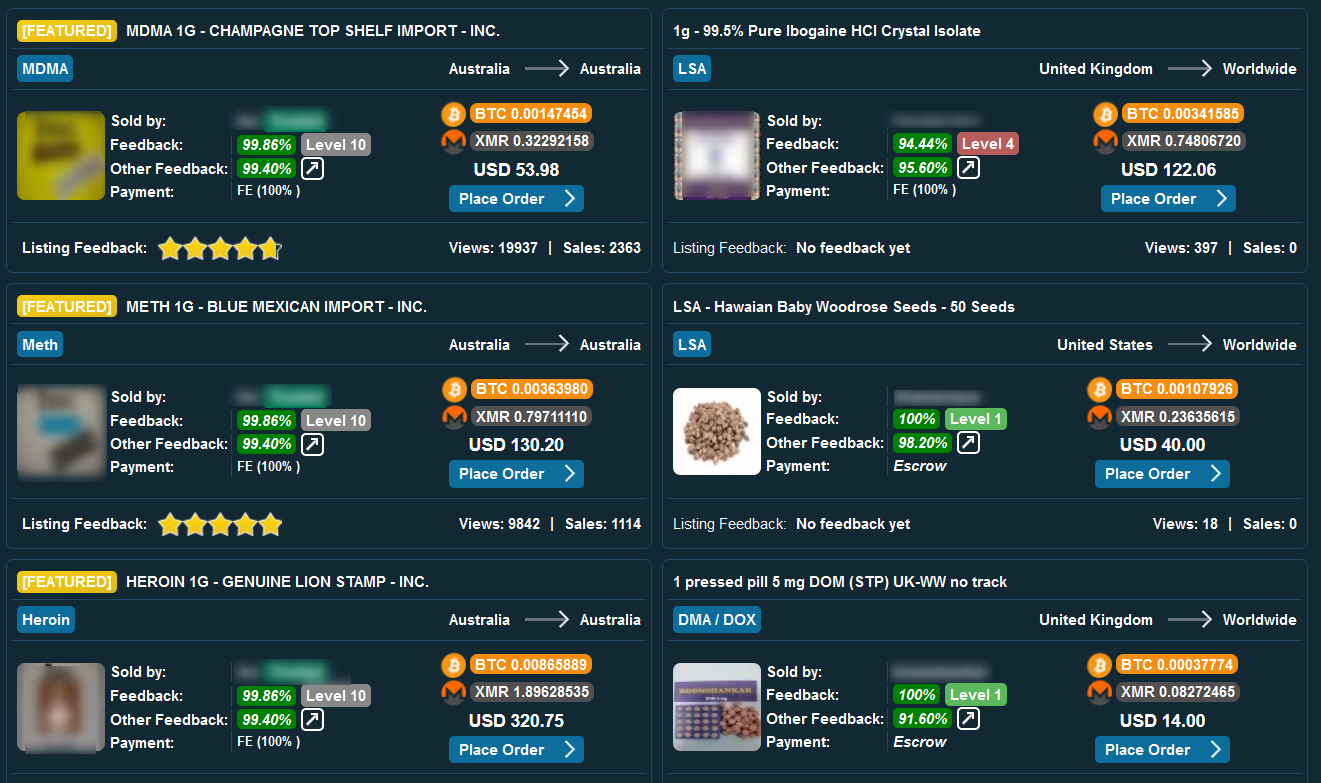
Dark web marketplaces, which usually operate on the Tor network, are used as a platform for illegal trade and money laundering.
Illicit marketplaces on the dark web list various illegal items. The products that are most commonly listed for sale include:
The prices for these products range from a few dollars to hundreds and thousands of dollars, depending on the value of the product and the level of experience the vendor and platform have.
One of the major issues in these underground marketplaces is building trust between buyers and sellers. Staying anonymous is crucial, but it’s also easy to become a victim of scams on these platforms. To address this, many marketplaces use administrators to handle transactions instead of direct exchanges between buyers and sellers. This adds a layer of security, ensures someone can step in if there’s foul play at hand, and keeps users more anonymous since they don’t have to make direct money transfers. One of the most popular and trusted marketplaces on the dark web today is Abacus Market, followed by Nemesis, and Vice City.
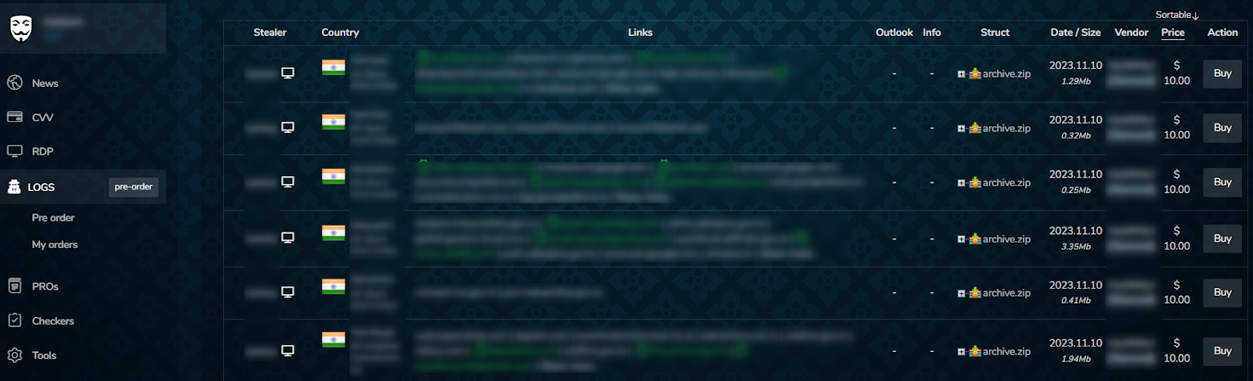
Datastores represent a distinct category within the dark web marketplace landscape.
Unlike what we at Webz.io call “classic marketplaces”, which primarily trade tangible illicit goods, datastores exclusively specialize in the trade of leaked credentials, such as stealer logs credentials, RDP credentials, compromised accounts, credit cards information, stolen prepaid cards, and stolen gift cards.
In contrast to typical dark web marketplaces, datastores typically list data without detailed descriptions or comments and feedback sections. Instead, they organize data in extensive listings sorted by data type and other relevant criteria. Another interesting observation is that most datastores don’t offer spaces for cooperation with many suppliers, and instead, the admin is primarily responsible for managing the listings on the site.
Some of the most popular datastores today include Russian Market and Brian’s Club.
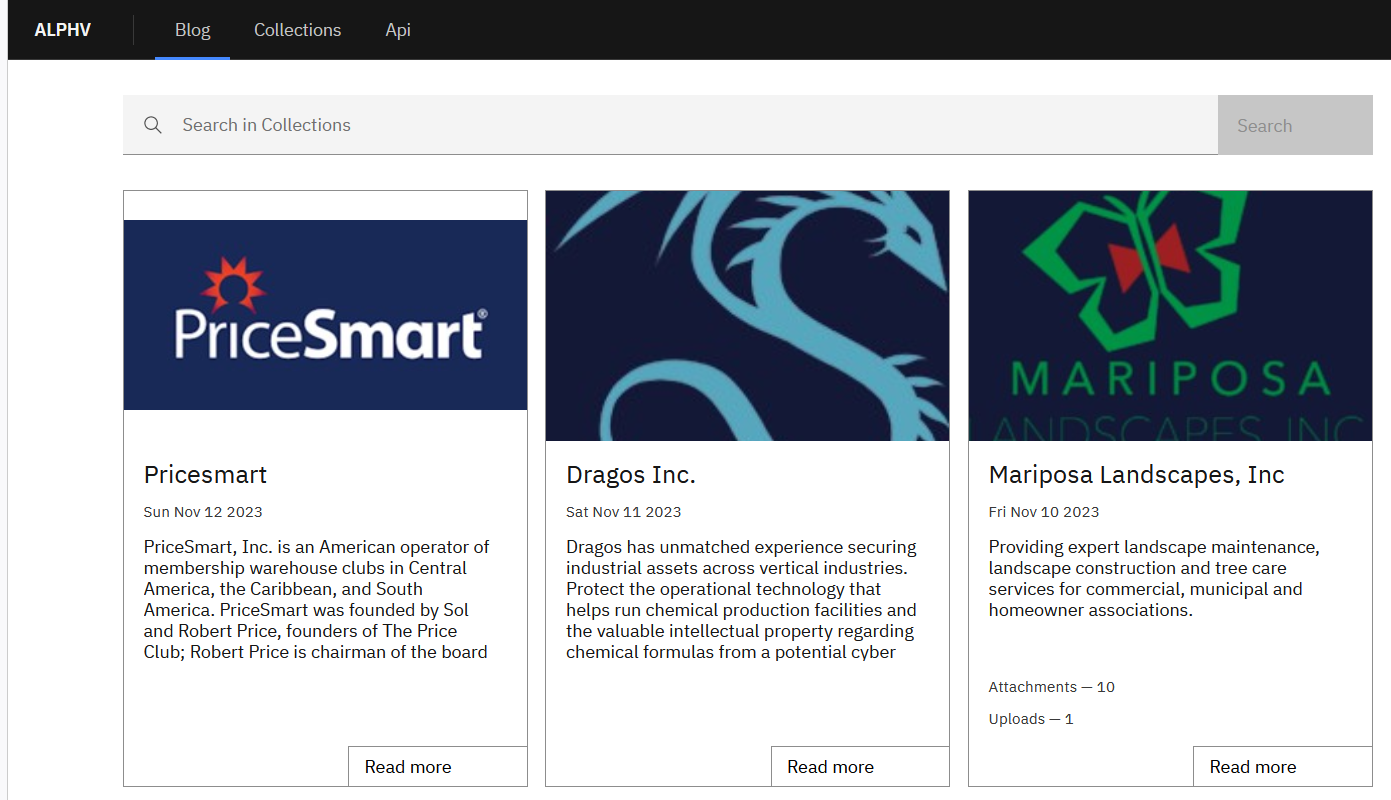
This category includes websites operated by ransomware groups and other advanced persistent threat (APT) groups.
These sites serve multiple purposes, including self-promotion, public messaging, the announcement of victims’ names, the publication and sale of data, establishing communication channels with victims, and even recruitment efforts.
Maintaining such websites allows these cybercriminal groups to bolster their reputation. By publishing sensitive information they’ve acquired, they can effectively pressure their victims into paying ransom. For groups with a certain agenda to promote, these platforms are used to gain more recognition and global attention.
The proliferation of ransomware attacks in recent years has led to a growing number of new websites going live every year. Almost all of these sites operate on the Tor network and frequently change their onion domains to evade detection. Given the disruptive nature of their activities and the potential disclosure of sensitive information, these sites have become a critical source for monitoring threats by cybersecurity and intelligence companies.
Encrypted chat apps, also known as instant messaging (IM) platforms, have gained immense popularity among cybercriminals due to their unique features that help them go undetected. One of the main features promoting that layer of anonymity is the robust end-to-end encryption they offer, ensuring user anonymity and thwarting attempts by standard search engines to index group messages. This lack of indexing makes it challenging for law enforcement agencies to identify and monitor cybercriminal activities.
These platforms also provide a wide array of communication options, allowing cybercriminals to engage in various illicit activities. They can conduct discreet one-on-one conversations or manage group chats, channels, and servers with many participants, enabling them to easily collaborate on illegal projects.
Given these advantages, it’s no surprise that cybercriminals use instant messaging apps extensively for a range of illicit purposes.
These illicit activities include:
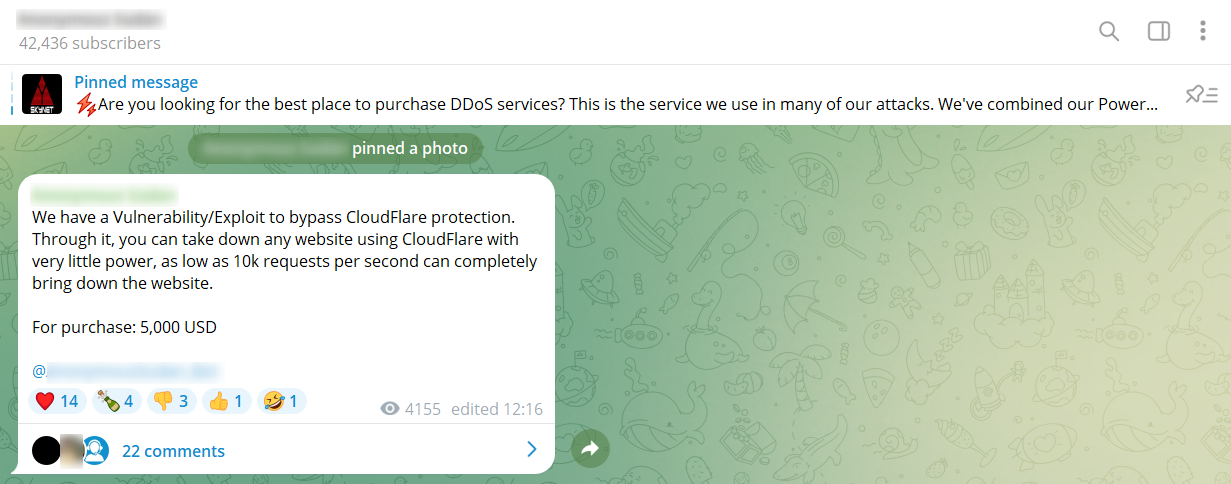
Paste sites are websites designed for storing and sharing text-based information, ranging from code snippets and scripts to configuration files and plain text.
The simple and straightforward interface of paste sites enables users to paste their content, and instantly generate a unique URL for easy sharing. While these platforms are commonly used by developers and technical professionals, they have also become favored tools among cybercriminals. For instance, Pastebin, which is a legitimate website, is being widely used by many cybercriminals.
Their appeal to threat actors and hackers is attributed to several factors. Firstly, paste sites provide a convenient and anonymous means to share critical information, such as stolen code, configurations, or password files. Secondly, unlike many other online services, paste sites typically do not require users to register or authenticate, ensuring a level of anonymity. Thirdly, content on these platforms is rarely actively monitored or removed by administrators, making them ideal for clandestine information sharing.
These paste sites primarily reside on the open web, but some can also be found on encrypted networks. Cybercriminals are likely to use these websites in order to share malicious software codes, sensitive security information, leaked PII, hacking guides and tutorials, and promote private criminal services such as hitman services.
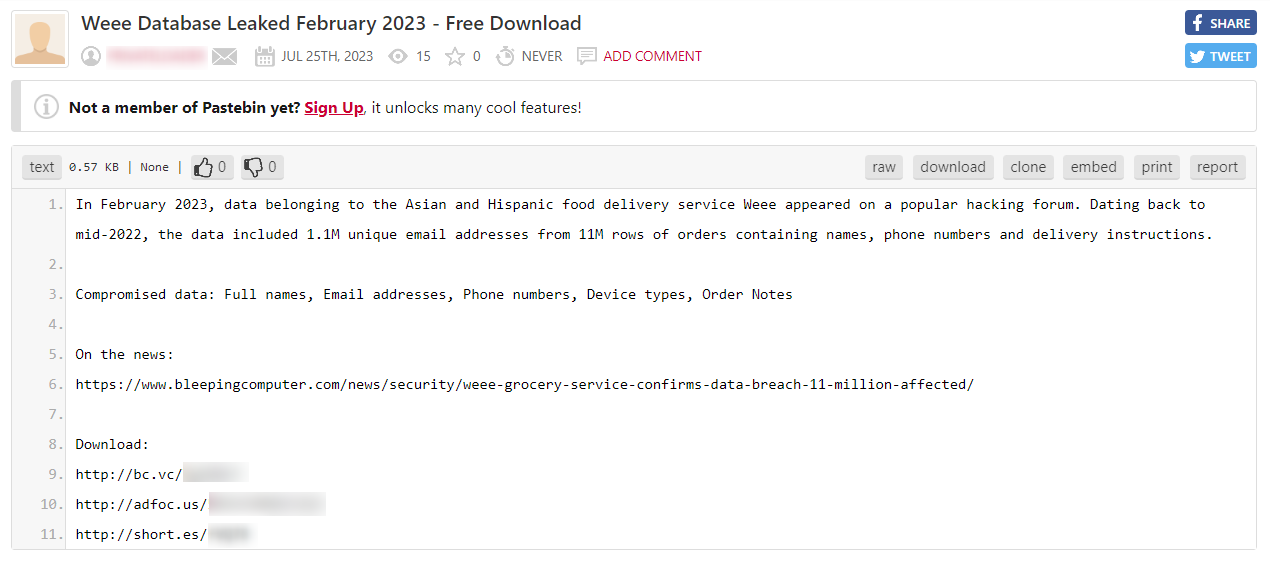
Imageboards are online forums that include threads that users start by posting images, to which other forum members can freely reply, with no restrictions. Imageboards have gained significant popularity in recent years and are widely used by people from all over the world.
The majority of content on imageboards is legal and includes various discussions on topics such as anime, movies, fashion, and video games. However, because imageboards are known for keeping the identity of their users anonymous and have no restriction over the type of content that can be shared, they enable users to share content and create discussions on offensive, extreme, and inciting topics. This has made imageboards become a fertile ground for extremist groups, movements, and individuals to spread hate speech, disinformation, and fake news against brands and executives which can sometimes pose a high risk to them.
Today, imageboards are operated on the open web, Tor, and i2p. The most popular imageboard is 4chan, followed by KohlChan, 8kun, and EndChan.
Alternative social media platforms, sometimes known as “Alt-tech” (alternative technology), closely resemble mainstream social media platforms both in user interface and functions. However, they set themselves apart by imposing fewer to no restrictions on the types of content their users can share. These platforms have emerged as havens for individuals and groups that have been banned or restricted on mainstream platforms due to the content they propagate.
Due to their unrestricted nature, alternative social media platforms are widely used by radical individuals or organizations, who disseminate radical ideologies, incite by spreading fake news, and provoke violence that can have real-world criminal consequences.
The large volume of banned users, criminal elements, and radical opinions on alternative social media platforms presents a pressing challenge for law enforcement and security agencies seeking to combat the spread of extremism and violence in the digital realm and beyond.
Underground news sites may not get a lot of attention and are surprising to some people, but they are a notable site category on the deep and dark web. Despite their relatively modest presence on these clandestine platforms, they are an important source to monitor when combating online illegal activities.
These hidden news websites are maintained by radical groups and organizations and are intended to attract as many potential activists as possible. Notably, groups like ISIS and other radical Islamist organizations, as well as neo-Nazi groups, operate such news sites. Their primary purpose is to inform readers about their ongoing activities, engage and maintain their activists, and advance their agendas by disseminating propaganda.
The deep and dark web ecosystem is huge but yet hidden. We have only mapped the primary types of sites and platforms commonly used by cybercriminals you can find on these layers of the web. Yet alongside these sites, there are other resources, such as illegal service-based sites, file hosting platforms, personal criminal blogs, and even dark web search engines.
Understanding this complex network of platforms is the first and crucial step in combating the dangers in the digital realm, the online world that lurks beyond the scope of conventional search engines and public online interactions. Whether you’re a cybersecurity professional, an OSINT researcher, or an intelligence analyst, gaining insight into the intricacies of the deep and dark web is essential for monitoring digital threats. The next step is accessing and investigating it, whether through a cyber API or with a dark web monitoring tool. To learn how to do that, get in touch with us.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.