How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide]](https://webz.io/wp-content/uploads/2025/01/Main-image1-1.jpg)
In a world where high-profile individuals face many threats, protecting executives and VIPs goes beyond traditional security measures. Executive protection teams are no longer limited to physical threats alone but are now facing new, hidden dangers lurking on the dark web.
For this reason, By tracking and analyzing the hidden corners of the internet where illicit activities often thrive, security teams can gain crucial insights into potential threats that might otherwise go unnoticed. From monitoring discussions and chatter about specific individuals to identifying data breaches and leaked sensitive information, dark web monitoring provides an early warning system that allows proactive measures to be taken. This proactive approach empowers executive protection teams to stay one step ahead, mitigate risks, and ensure the safety of VIPs in an increasingly interconnected world.
In this article, we’ll provide a step-by-step guide on how to use our own dark web monitoring tool, Lunar, to protect high-profile individuals and executives.
In this guide, we’ll investigate cyber threats against Christopher Asher Wray, the FBI director.
Before starting the discovery of threats on the dark web, the first step will be to define a query that will guide the initial search. We will use Lunar’s AI Search, which turns a simple request into an advanced query, to ask for a general query that will help us monitor discussions about Christopher Asher Wray, the FBI director.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 2 The simple request typed in Lunar's AI Search](https://webz.io/wp-content/uploads/2023/11/1-39.png)
In the following image you can see the result, a query Lunar’s AI Search created, which we can further tweak to optimize our search.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 3 The query Lunar's AI Search generated as a result (see previous image)](https://webz.io/wp-content/uploads/2023/11/2-35.png)
As can be seen in the image, the query consists of as many variations of Wray’s name as possible, whether his full name or abbreviated name, including different variations of his title (current or previous position), nicknames, or hashtags that are associated with him.
In cases where personal details are available, such as an email address or phone number, they can be added to the query, which can help discover leaked personal information.
The second step is optional, and it allows us to narrow down the results according to different types of threats. This can be done with pre-set categories on Lunar (see the pictures below).
The categories include:
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 4 The categories you can select on Lunar](https://webz.io/wp-content/uploads/2023/11/3-33-2.png)
For the sake of this investigation, we chose not to limit our results to one of these categories (the default is set to “All Categories”).
The third step is setting a timeframe for the results you want to retrieve, which are sorted by the publication date. You can either set your own timeframe, or you can select pre-fixed time frames such as ‘yesterday’, ‘1 week ago’, ‘6 months’, etc.
In our investigation, we’ll set the search to go 6 months back.
After adapting our query and selecting a timeframe for our search, we ran it, which yielded around 3,500 results.
Here, we can already have a quick and preliminary observation – that there has been a recent surge in relevant posts involving the FBI chief, (which can be seen in the chart below), which suggests an unusual trend.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 5 The initial results on the Lunar dashboard](https://webz.io/wp-content/uploads/2023/11/Image-7.png)
However, it’s too time-consuming to sift through this huge number of results, so we should refine our search to get a relevant and manageable scope of results.
One of the best ways for an analyst to narrow down the search is to filter them by a type of digital threat.
Overall, there are 3 prominent digital threats relevant to VIP/Executive Protection that one can monitor on the deep and dark web:
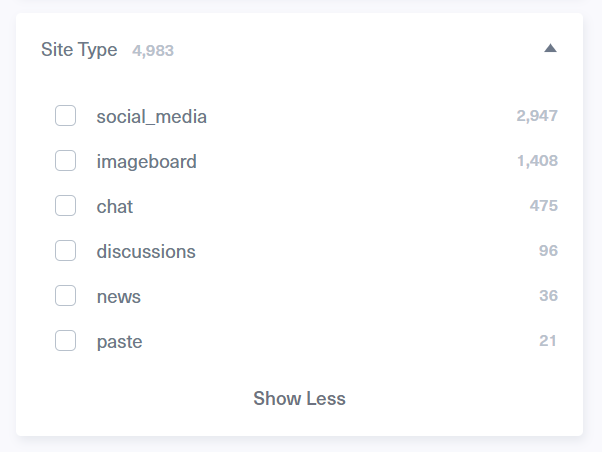
One of the easiest ways to trim down our search when using Lunar is the dynamic filters, which can be used to sort results by various values such as networks, site type, site domains, languages, risk score, and even extracted entities such as CVEs, IPs, and email addresses, and others.
For example, one of the filters that are more relevant to our investigation is the ‘Tags’ field, which includes 14 different tags, such as extremism, hacking, data breach, phishing, crypto, and others. The tags are used to help us retrieve instances where the subject we’re inquiring about is mentioned in the context of the selected tag. Since the discussions are taken from deep and dark web networks, most of the posts will probably have an illegal nature. It’s important to note that not every result we get when filtering according to those tags will necessarily indicate a direct threat. However, by clicking on those tags, we can easily narrow down our search according to relevant threats.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 6 The Distribution of Posts by Illicit Topics](https://webz.io/wp-content/uploads/2023/11/Image-2.png)
Let’s take a close look at the results we retrieved associated with the 3 digital threats mentioned before:
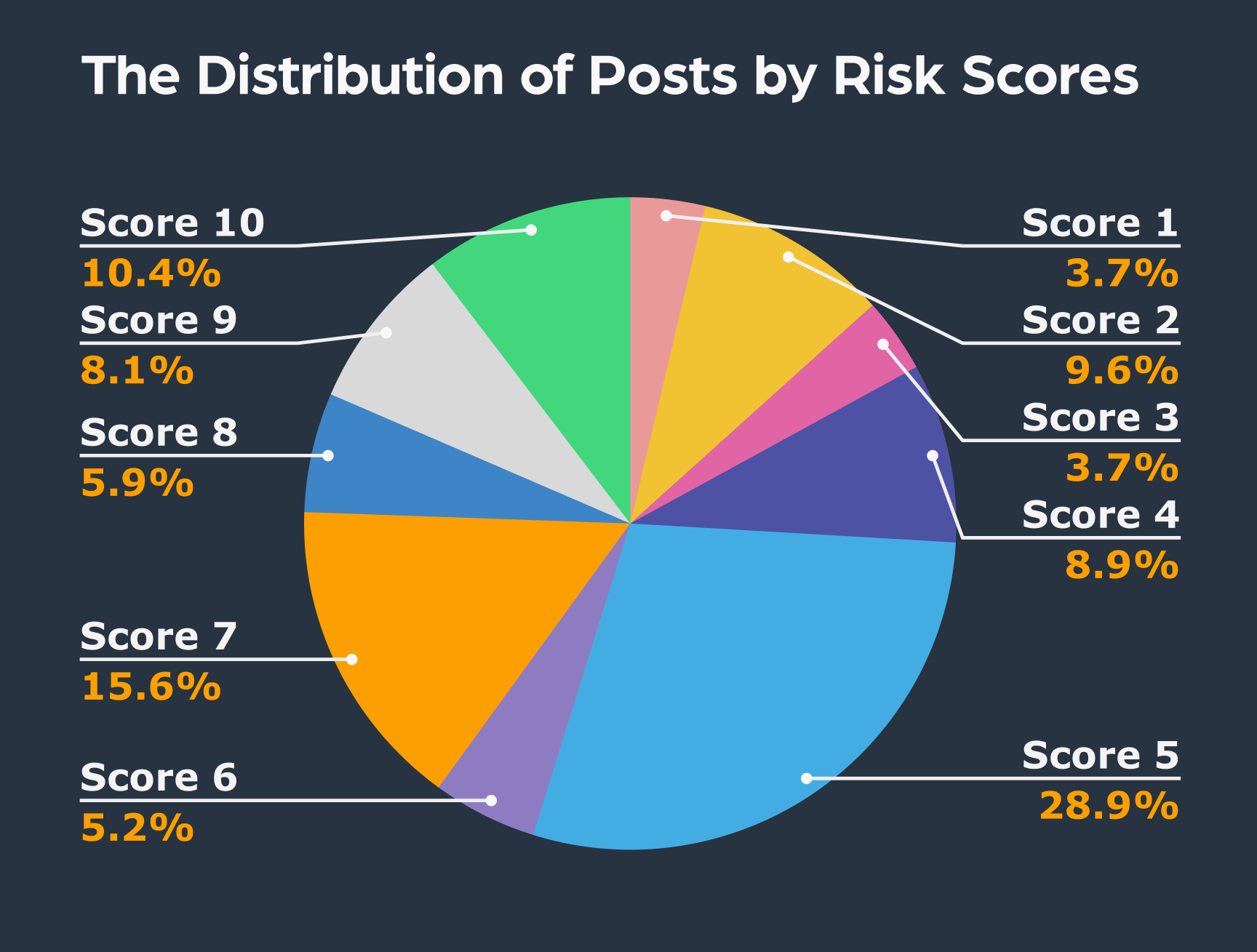
As you can see from the pie chart above, around 5,000 posts of all the results we received are classified as ‘Extremism’, meaning they have an indication of radical content involving Wray. We can further narrow down our results by using another dynamic filter Lunar supports which filters posts by site type. This is where we clearly can see that the majority of these “extremist” posts were published on alternative social media platforms and imageboards.
In this investigation, we’ll first focus on posts retrieved from what is classified as ‘discussions’ site type, which includes deep and dark web websites, which have a lower number of results compared to the ones mentioned before.
One of the first threads we found was published on a far-right online forum (see image below). In this thread, a radical user called Christopher Wray a “Nazi” and “pedophile-protector”, while speaking against U.S. government agencies, including the FBI:
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 8 A threat against Christopher Wray on a far-right online forum, the image is taken from Lunar](https://webz.io/wp-content/uploads/2023/11/Image-3.png)
Another risk we’d like to examine is the leak of personal information belonging to Wray. To do that, we filtered the search results by using the ‘data breach’ tag, which helps us retrieve results that indicate that there has been a potential leak of personal, confidential, or sensitive data.
To further trim down our search results, which retrieved around 200 results so far, we used Lunar’s cyber risk score filter, a feature that rates each post on a scale of 1 to 10, with 10 indicating the highest level of cyber threat.
In this investigation, we set our search to posts with a cyber risk score of 7 or higher, allowing us to concentrate on the subset of only a few dozen posts with the highest risk of data breach.
The following post (see image below), listed with a risk score of 8 and tagged as ’data breach’, was published on Doxbin, a paste site used by people posting personal data of any person of interest.
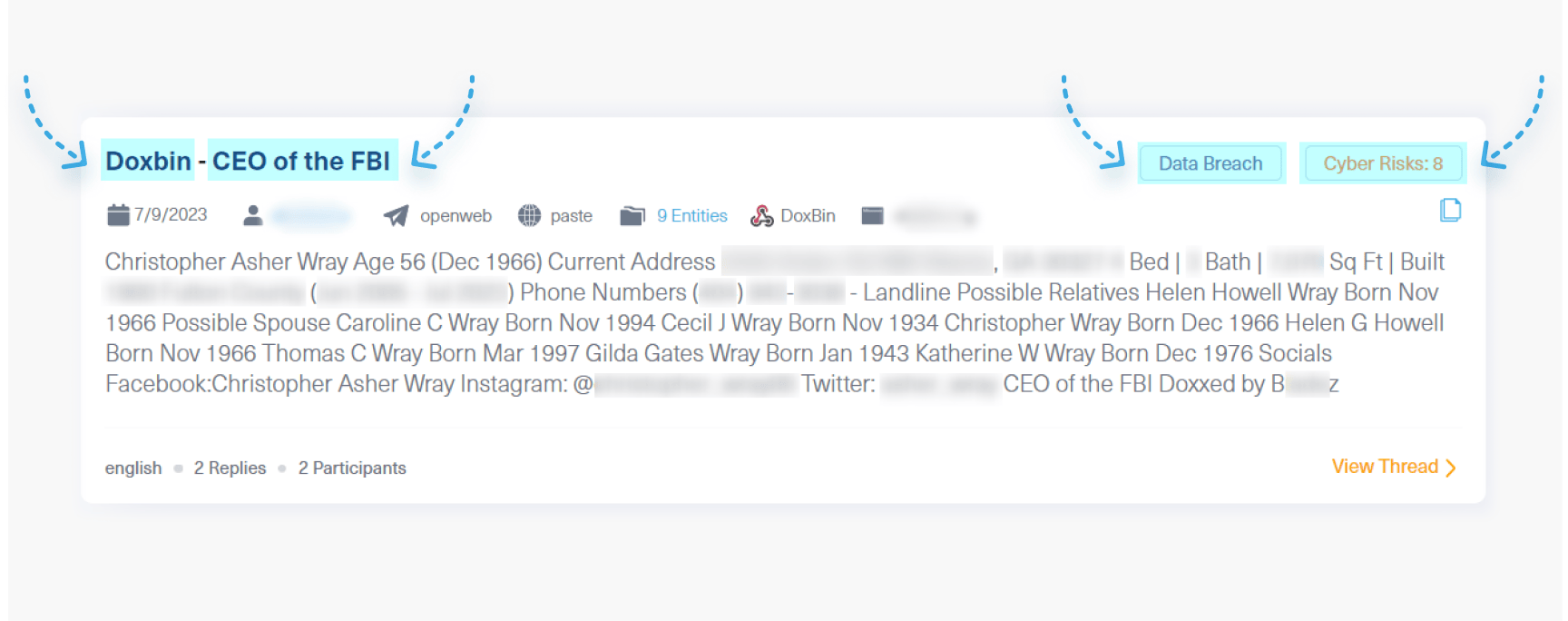
This post shows that Christopher Wray was a victim of doxxing, and his personal information such as physical address, house description, and phone number has been exposed.
To search for impersonation and fraud threats, we used Lunar’s ‘Phishing’ tag, which is often a good indication of these threats.
Once we used this tag, we could quickly spot emails used in our search results (seen in the next image). This is made easy thanks to Lunar’s capability to automatically recognize and pull out specific information from texts, like domains, email addresses, phone numbers, IP addresses, cryptocurrency addresses, and more.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 11 Emails associated with phishing attempts linked to Christopher Asher Wray, the FBI director](https://webz.io/wp-content/uploads/2023/11/9-4.png)
All of these emails appeared to be associated with potential phishing attempts. Once we clicked on one of them, we could see a post that confirmed this suspicion:
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 12 A post showing a potential phishing threat associated with Christopher A. Wray](https://webz.io/wp-content/uploads/2023/11/10-6.png)
This post was published on StopScamFraud, a website used by people to report on internet scams. In this report, an email, which appears to be a phishing scam, is published for all. In this case, a scammer is impersonating the FBI director, Christopher Asher Wray, and claims that the ‘targeted victim’ has $46 million dollars in funds. The scammer is trying to trick the victim into contacting him by using email addresses that sound official like “[email protected]” and “[email protected]”, which refer to fraudulent internet domain names.
Once the analyst has fine-tuned their search criteria in order to make the discovery process more efficient and precise, the next step will be to use the relevant posts that indicate that there’s a real need to deepen the investigation.
The first step of the investigation is to confirm whether the threat exists or not. This is when you analyze your data and look to corroborate evidence from other sources within the deep and dark web community, especially if there is enough traction around it from users.
Next, you’ll evaluate the extent of the threat and how common it is in the deep and dark web landscape. This is done by determining how frequently it is discussed and how many users are engaged in discussions related to this threat. You’ll then look for additional insights from other dark web users who might possess valuable information to help you better assess the threat
At this point, you’ll want to investigate further by searching for other posts attributed to the same threat actor. Here we’ll identify any additional identifiable information or patterns associated with this actor. In some cases, aggregating multiple posts from the same threat actor can assist in creating a more comprehensive profile.
Another important part of the investigation is to explore the origin of the threat indicators. Investigate the source where these indicators were discovered. This may help in identifying other sections or posts on the site that could be relevant to your investigation, and provide valuable context and other leads.
Let’s take a look at the last search we ran that indicated impersonation and phishing threats associated with Christopher Asher Wray. The high number of emails, exceeding those displayed in the screenshot above, points to a widespread phenomenon where threat actors impersonate the FBI in general, and Wray specifically.
To further investigate the source of this threat, which is currently unknown and anonymous, we used Lunar to search for phishing attempts associated with the entire FBI agency in dark web marketplaces and underground forums in an attempt to identify any threat actors involved in such activities.
The results included the following post where a threat actor was selling FBI-related email addresses and domains to run phishing scams. This person even provided their Discord username for those interested in learning more about his “services”.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 13 A threat actor selling emails related to FBI](https://webz.io/wp-content/uploads/2023/11/Image-6-1.png)
This post offers valuable insights for analysts and researchers and sheds light on the potential threat actor behind the activities we’ve uncovered in the course of our investigation.
When we searched again for the Discord username that was mentioned in the post and the username used to make the initial dark web forum post, we were able to retrieve additional results. These findings provide us with more details about the threat actor in question.
The last phase isn’t exactly last as it indicates that this should be an ongoing practice of monitoring threats. VIP/executive protection means you have to stay on top of any threats that may target the executive you’re protecting. With dark web monitoring tools, like Lunar, you can set alerts based on predefined queries, which ensures you remain on top of any relevant developments or threats related to your organization, executives, or personnel.
This alert system helps simplify the process of monitoring threats on the deep and dark web. You can also define a time range, and specify the frequency of your notification, and their priority – making sure you only get the information you need, and when you need it.
In this investigation, we can use the same query we used at the beginning of our process since we’d like to get any new relevant posts that indicate some type of threat when mentioning Wray in the deep and dark web.
![Executive Protection: How to protect VIPs with Dark Web Monitoring? [Guide] 14 Setting an alert on Lunar for ongoing monitoring threats on the dark web](https://webz.io/wp-content/uploads/2023/11/12-2.png)
The deep and dark web are the main spaces used by threat actors and extremists to act against your executives and VIPs. For this reason, dark web monitoring tools have become critical in safeguarding against emerging threats, whether they are phishing, leaks, or hate speech. In this guide, we’ve walked you through a few steps you can easily take when using our dark web monitoring tool, Lunar, to investigate these threats to your executives and business.
Ready to simplify your dark web investigations? Talk to us about Lunar now.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.