How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

With 83% of organizations reporting they experienced a phishing attack this past year, the danger these attacks pose to businesses is real.
Phishing is a fraudulent attempt to deceive an end-user into providing confidential information, such as login credentials. This attempt is carried out by using social engineering, a manipulation technique that exploits human error. There are a lot of phishing techniques, some of them targeting a specific person or organization, and some of them are designed to target many different people.
Because the deep and dark web are prime spaces for cybercriminals to communicate and share such tools, we decided to dive deep into the darknets to list what we can find about some top phishing techniques:
A phishing website is a malicious website that aims to impersonate an official website. The phishing website will mimic the domain name and interface of the official site. This can deceive users into entering the fake site either when using search engines, or when using a link that was sent to them. At this point, the user will type their credentials to log into their accounts on the site, and by that expose their credentials to a malicious actor.
On the dark web, we can see many automatic phishing tools, which can quickly imitate sites, offered for sale and a lot of to-do guides and tutorials. While these techniques are valuable for researching the way scammers operate, they are too general to help companies monitor threats against organizations.
In addition to using domain monitoring solutions to detect any malicious impersonator website, using dark web data can help track the trade of phishing and scam pages before they target organizations.
Take for example the post below which is taken from the popular hacker forum Cracked. In the post, a threat actor is offering a schwab.com phishlet for Evilginx. This is a man-in-the-middle attack framework that is used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. This framework can use so-called phishlets to mirror a website and trick the users to enter credentials.
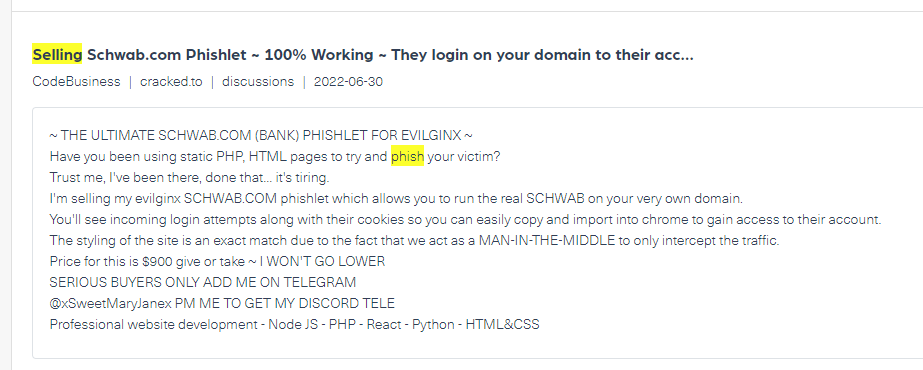
Monitoring the dark web for this kind of post could help companies like Charles Schwab Corporation, a U.S.-based financial services company, defend against phishing threats.
Email phishing is carried out by sending a forged email supposedly on behalf of a legitimate organization that is justifiably asking for credentials. One of the techniques used in email phishing is email spoofing. In spoofing attacks, the attacker forges the email sender so that client software displays the fraudulent sender address. This technique is widespread and although one of the best ways to protect against it is to be aware and cautious when receiving emails, many can still easily fall for phishing emails.
The most proactive way to address this issue is by finding email addresses that are at risk on the deep and dark web. Trading leaked databases of email addresses is one of the most popular topics on hacking forums and dark web marketplaces. These databases are used for various malicious activities once obtained by a cybercriminal, one of them is email phishing that they send to a wide audience. The detection of email addresses that were leaked can indicate they are at risk.
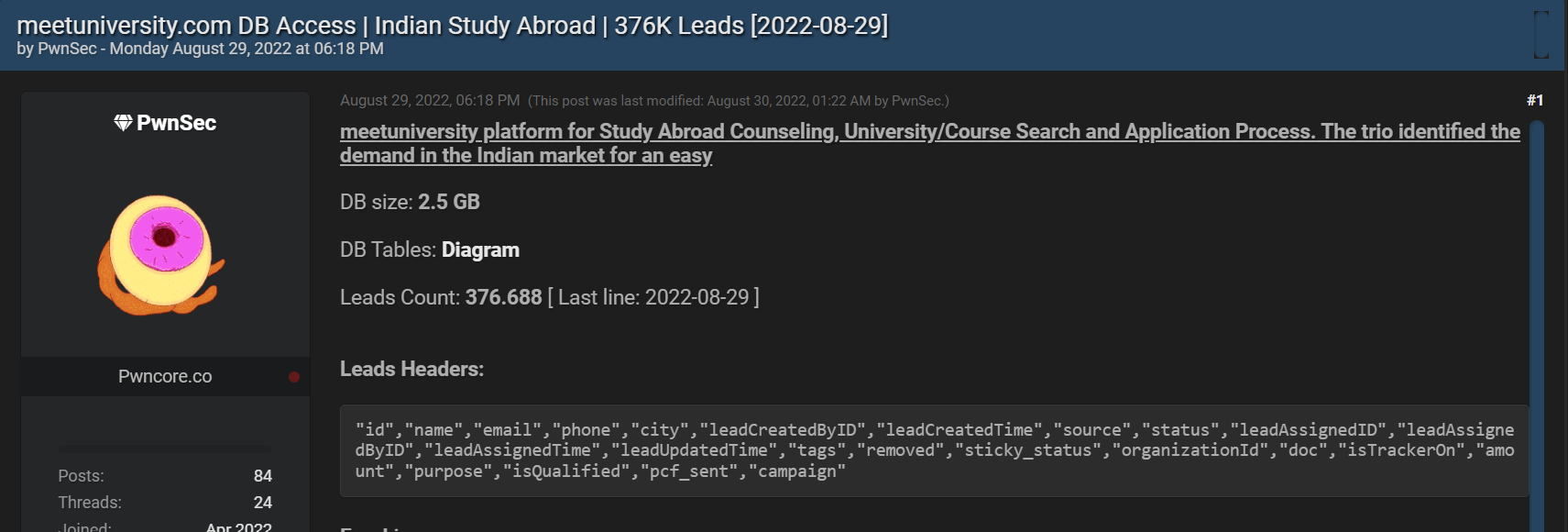
The following example is taken from hacker forums Breached.co, where a leaked database of meetuniversity.com, an Indian international study platform, was published. This leak includes email addresses and additional personal information about the users, such as city and phone number. The leak does not include passwords, which cybercriminals still would like to obtain. However, they can take this database and send phishing emails to the database, which is related to the Meetuniversity platform.
Another example of targeted phishing emails can be seen below, where a threat actor posted a link to a Pastebin page that includes the email address of the University of Cypress staff on the deep web hacking forum Cracked.to. The actor mentions these leaked emails can be used for phishing (spear phishing – read more on that later on).
Smishing stands for SMS phishing. It is a form of phishing in which scammers use fake text messages to trick users into sharing personally identifiable information (PII). Similarly to email phishing, avoiding falling for these scams can be very challenging.
Threat actors are usually using a large database of phone numbers, which they can easily obtain on the deep and dark web, to carry out these sorts of attacks.
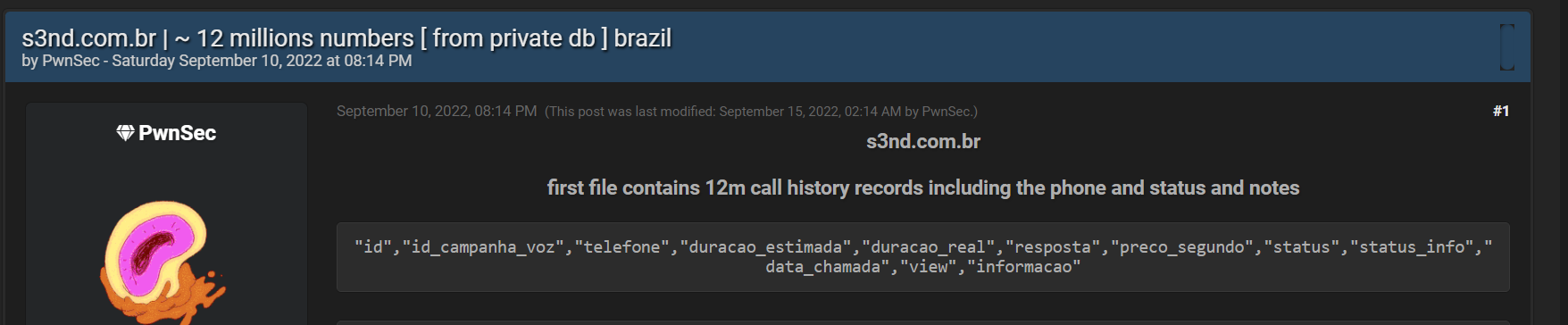
The following example includes a database of 12 million phone numbers of Brazilians that were leaked on hacker forum Breached.co. This database is readily available for use by a threat actor who would like to launch a smishing attack against these leaked phone numbers.
Spear phishing is personalized phishing attacks, targeting a specific person, group, or organization. The attack will often include specific information known to be of interest to the target. These attacks are extremely hard to predict in advance because they are not conducted on a large scale, which makes them very professional or very personal. Experienced cybercriminals are not very likely to leave a lot of details online regarding their future action.
For example, the post below, which was taken from breached.co, shows that a threat actor obtained an email address from a data breach of an admin in a credit company. But this cybercriminal is professional and does not leave any incriminating details behind:
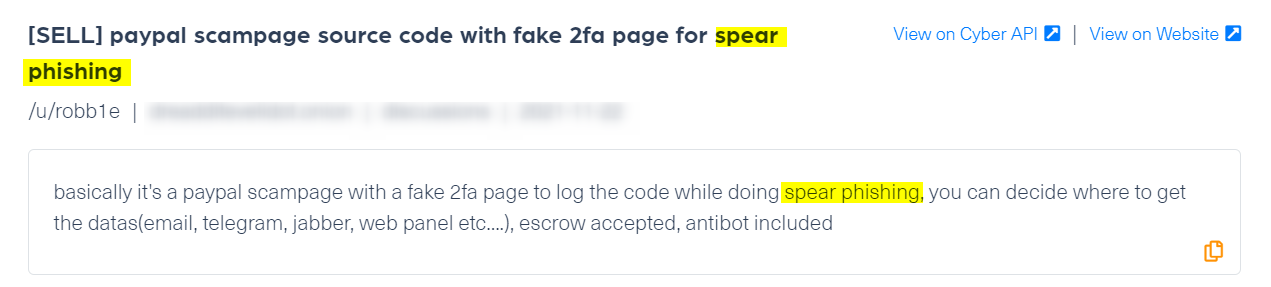
Finding a spear phishing attack against an organization requires a steady stream of quality web data that can be used for monitoring mentions on deep and dark web data sites.
The example below is taken from the dark web hacking forum Dread. The threat actor is selling a Paypal scam page with a fake 2-factor authentication page:
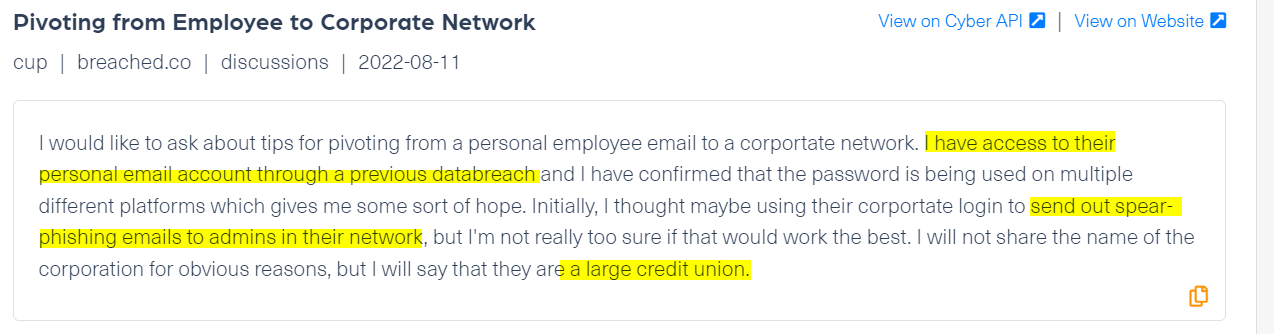
While there are many solutions that offer some protection against phishing attacks, it is nearly impossible to keep track of them all without tracking external web data, where threat actors and trading and discussing phishing tools. This is how you can track breached emails and accounts, which can be easily targeted by phishing attacks. Webz.io is adding millions of records every day from deep and dark web sources, including an early indication of tools targeting specific organizations that can help organizations protect against future phishing attacks.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.