How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Recent reports have shown that there has been a significant increase in the number of CVEs published in 2022 in comparison to 2021. Since the deep and dark web are the main places where threat actors share and discuss CVEs and exploits, we explored every corner of the darknets to find the top CVEs over the past year.
CVE stands for Common Vulnerabilities and Exposures, which is a list of computer security vulnerabilities that have been publicly disclosed. Whenever a security vulnerability is discovered and published, it’s given a CVE ID number by a CNA (a CVE Numbering Authority – major IT vendors or security companies and research organizations) that follows the format of CVE-YYYY-NNNN, like CVE-2018-1234 or CVE-2006-4529, which will then be referred to as the CVE ID, number, name, or identifier. CVE IDs are unique identifiers for publicly known cyber security vulnerabilities.
CVEs are mentioned over different deep and dark web platforms by vendors who sell security vulnerabilities on marketplaces and forums, hackers who share their recent work on security flaws, and other cybercriminals who post, buy, and improve the performance of these CVEs and exploits by communicating with the fellow threat actors on a daily basis.
For this study, we examined CVEs published in 2022 and found in over 50 deep and dark web platforms, including hacking forums such as XSS, Dread, Exploit, Breached Forums, and Cracked, in chat applications such as Telegram, in marketplaces such as Card Club, and in paste sites such as Pastebin.
Let’s first take a quick look at some statistics we gathered by using our data:
We ranked the CVEs according to the number of times they were mentioned in dark web posts as well as the level of engagement of these posts. Here are the top CVEs we found:
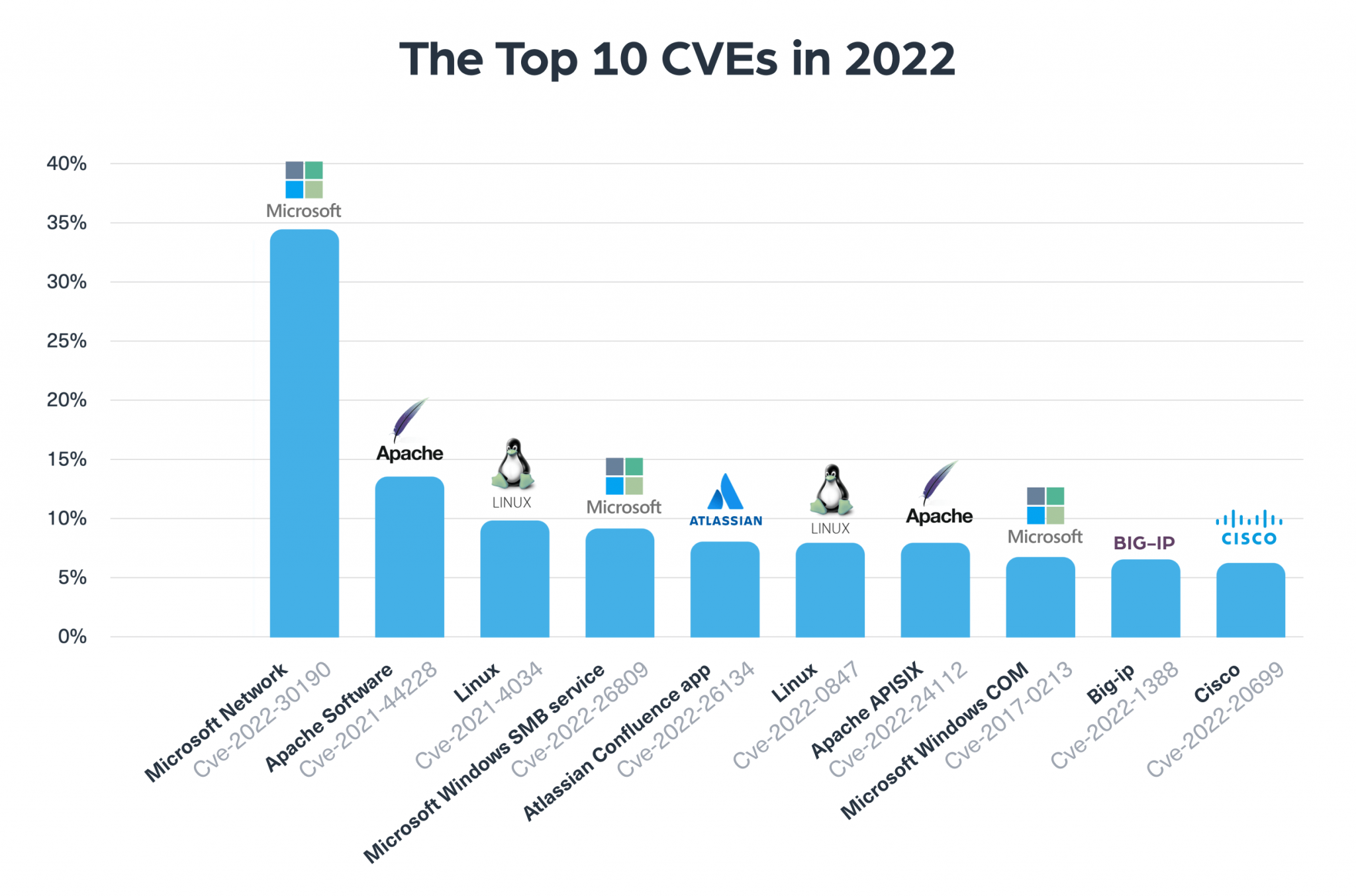
Now let’s take a closer look at the top 3 CVEs that have been mentioned on the dark web over the past year.
Date Record Created: June 1, 2022
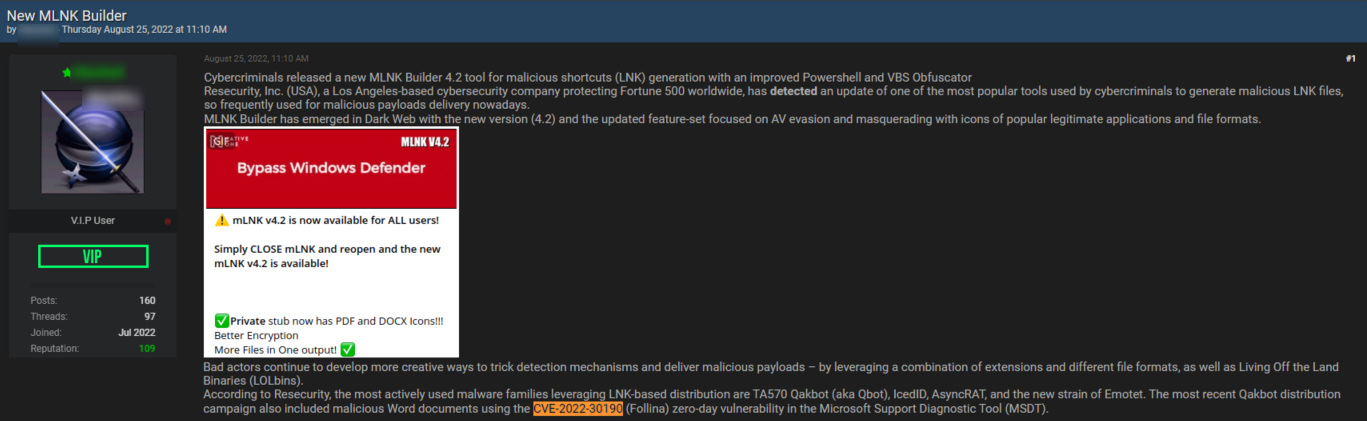
Description of vulnerability: CVE-2022-30190 is a Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability.
In the example below, you can see a threat posted on the popular hacker forum BreachedForums by a cybercriminal. In the post, they discuss CVE-2022-30190, which consists of a security flaw targeting Microsoft servers.
Date Record Created: December 10, 2021
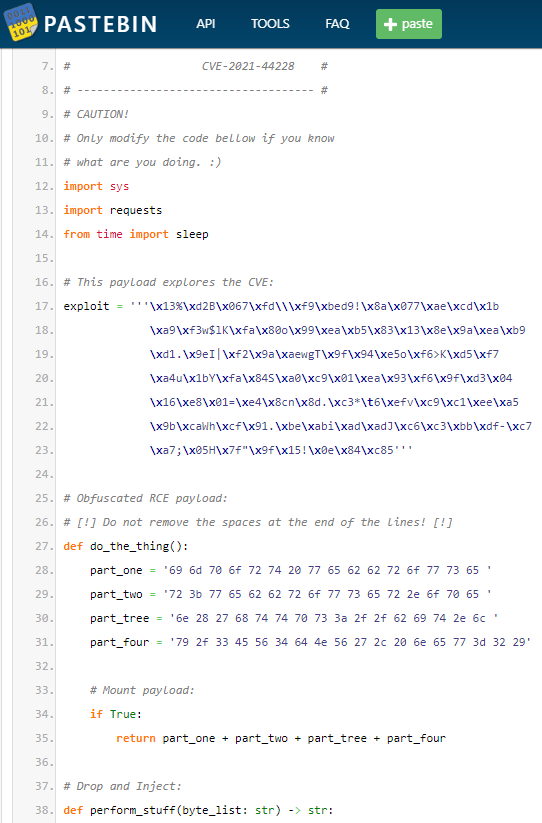
Description of vulnerability: CVE-2021-44228 is a remote code execution (RCE) vulnerability in Apache Log4j 2. An unauthenticated, remote attacker could exploit this flaw by sending a customized request to a server running a vulnerable version of Log4j.
In the following example a threat actor posts a script on Pastebin which can be used to exploit CVE-2021-44228. This exploit allows hackers to use this vulnerability in unupdated platforms that have not patched this flaw.
Date Record Created: January 28, 2022
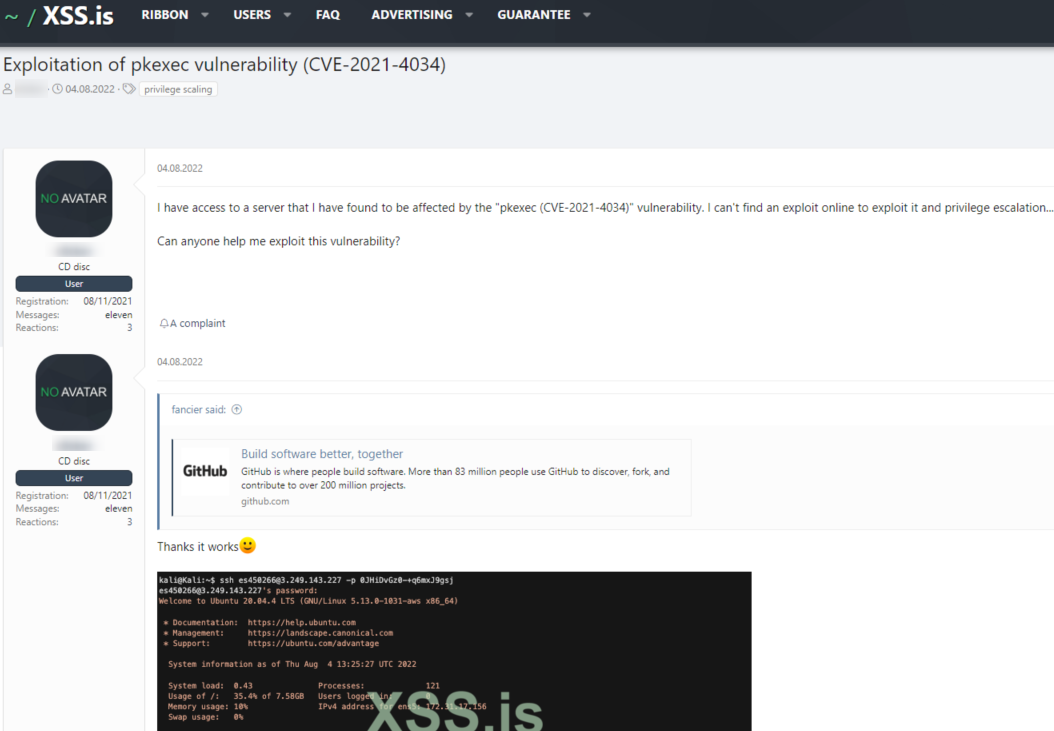
Description of vulnerability: CVE-2021-4034 is a local privilege escalation vulnerability that was found on Polkit’s PKexec utility. PKexec is a setuid tool that allows unprivileged users to execute commands as privileged users according to predefined policies. Due to a bug in the default version of PKexec, environment variables were attempted as commands rather than calling parameters. An attacker can take advantage of or exploit this by crafting environment variables that cause pkexec to execute arbitrary code. When successfully executed, the attack can cause a local privilege escalation by giving unprivileged users, such as the hacker, administrative rights on the target machine.
In the next example, you can see a threat actor asking about an exploit to the Apache Log4j vulnerability, referred to as CVE-2021-4034, and receiving a link to such an exploit from another threat actor on the popular hacking forum XSS.
Cybersecurity teams around the world are constantly looking for new ways to develop a good vulnerability management policy, since patching all vulnerabilities is nearly an impossible mission. To help these teams keep up with the changing vulnerability landscape it is important to use external data from the deep and dark web to monitor CVEs in real time.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.