How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Recently there has been a lot of discussion about the two Apple vulnerabilities, which affect most of its devices, including macOS, iOS, iPadOS.
The two vulnerabilities tracked as CVE-2022-32893 and CVE-2022-32894 allow RCE (Remote Code Execution) access and in some of the devices kernel permissions, which provide full and extensive permissions on the device. Both are related to the Safari WebKit web browser extension, and the OS kernel. Apple said it was aware of reports that both vulnerabilities may already have been actively exploited in the wild – making the need to patch more urgent.
By using our Cyber API, we have been able to exclusively trace another undetected, at the time of publication, Zero Day relating to one of the existing CVE – traded on the dark web.
But before we discuss that, let’s first understand the nature of these vulnerabilities.
Let’s better understand the implication of these exploits:
This vulnerability is an RCE flaw affecting Apple’s Safari Web browser WebKit.
Attack Method: An attacker could maliciously craft a web page, which if visited by a WebKit-powered browser, will lead to the execution of an unauthorized code on the device.
Exposure/Risk level: High, since Webkit is the base engine that is used by any browsers on iOS and macOS, whether Safari, Chrome, or any other. This means that every Apple user is exposed to this vulnerability.
Affected Devices: iPhone 6 and later models, iPad Pro, iPad Air 2 onwards, iPad 5th generation and newer models, iPad mini 4 and newer versions, iPod touch (7th generation), and macOS Monterrey.
This vulnerability is another RCE but this time a kernel-level code execution, which requires initial access to the affected device, for example by using the CVE-2022-32893 to gain access to the remote device.
Attack Method: The attack is caused by an out-of-bounds write an issue and is addressed by improving the bounds checking of the vulnerable components.
Exposure level: Once the threat actor gains access and exploits the vulnerability, they could move from controlling just a single app on the device to taking over the OS and activating any app whether its camera, microphone, accessing all data on the device, and more.
Affected Devices: All devices mentioned above.
Now that we discussed the risk these CVEs pose to Apple users, let’s take a look at what we found on the dark web.
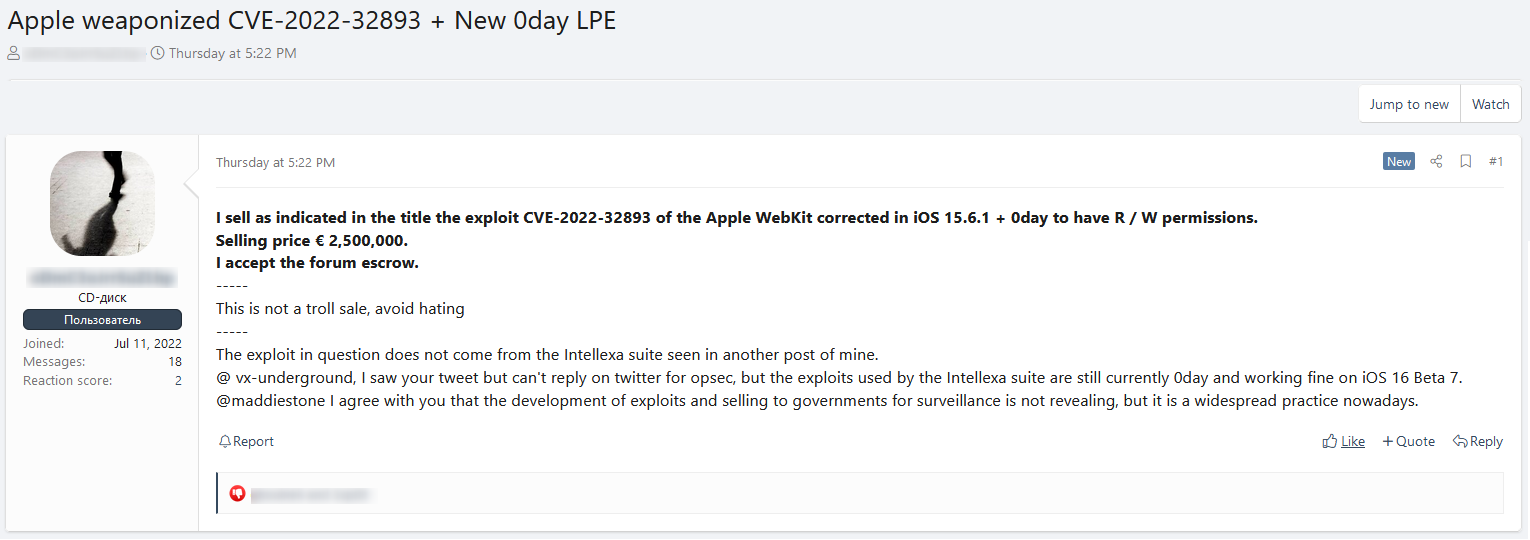
A few days after the initial vulnerability was exposed, we were able to find a post in which a hacker is offering a new zero day around the same CVE-2022-32893 for €2.5 million.
This is what we consider to be a unique publication of a zero day, because it is rare that a hacker publicly sells zero day, especially related to a large enterprise such as Apple.
This specific hacker has a history of selling zero days for Apple and Android.
This does not come as a surprise as we have been able to see a higher level of activity on the dark web around the time the publication about the vulnerabilities. We ran a search of the two vulnerabilities by using our Dark Web API and this is what we found:
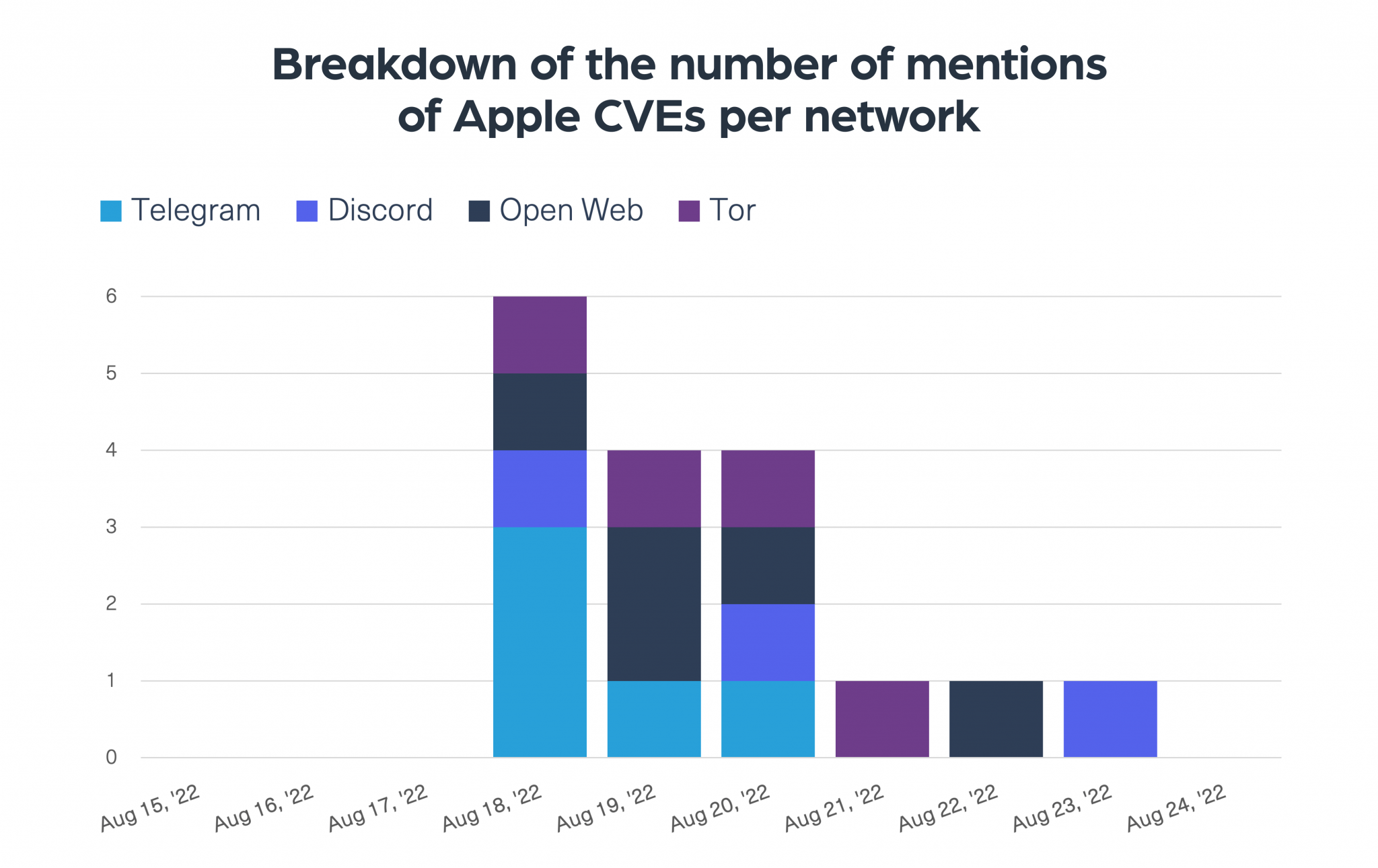
Most of the activity was around technical forums, some Telegram hacking channels, and image boards, even one mention of them on an alternative social platform.
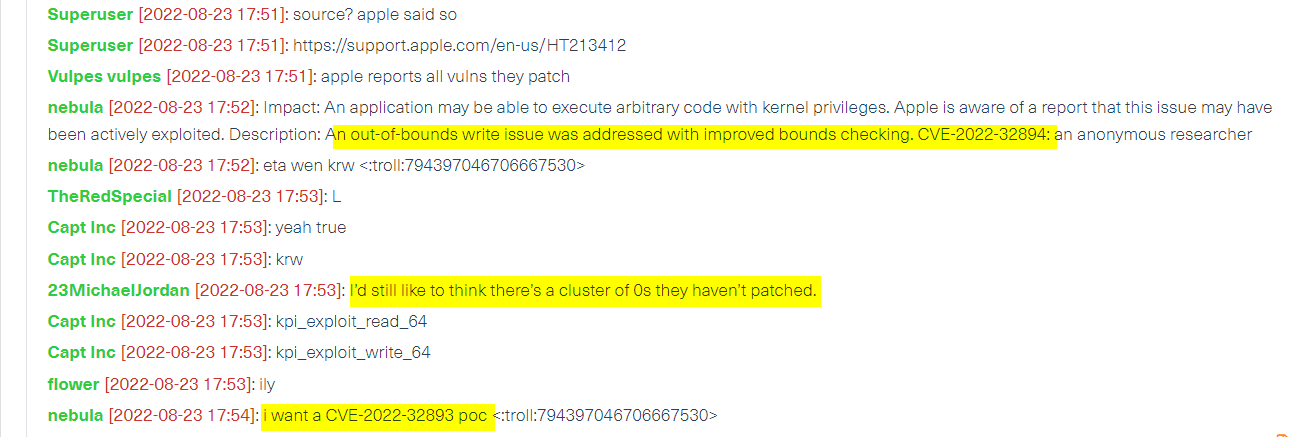
In the image below you can see a discussion between hackers about CVE-2022-32893/4. Threat actors are trying to exploit the CVE as fast as possible. They are also looking for additional zero days around the already existing WebKit patch.
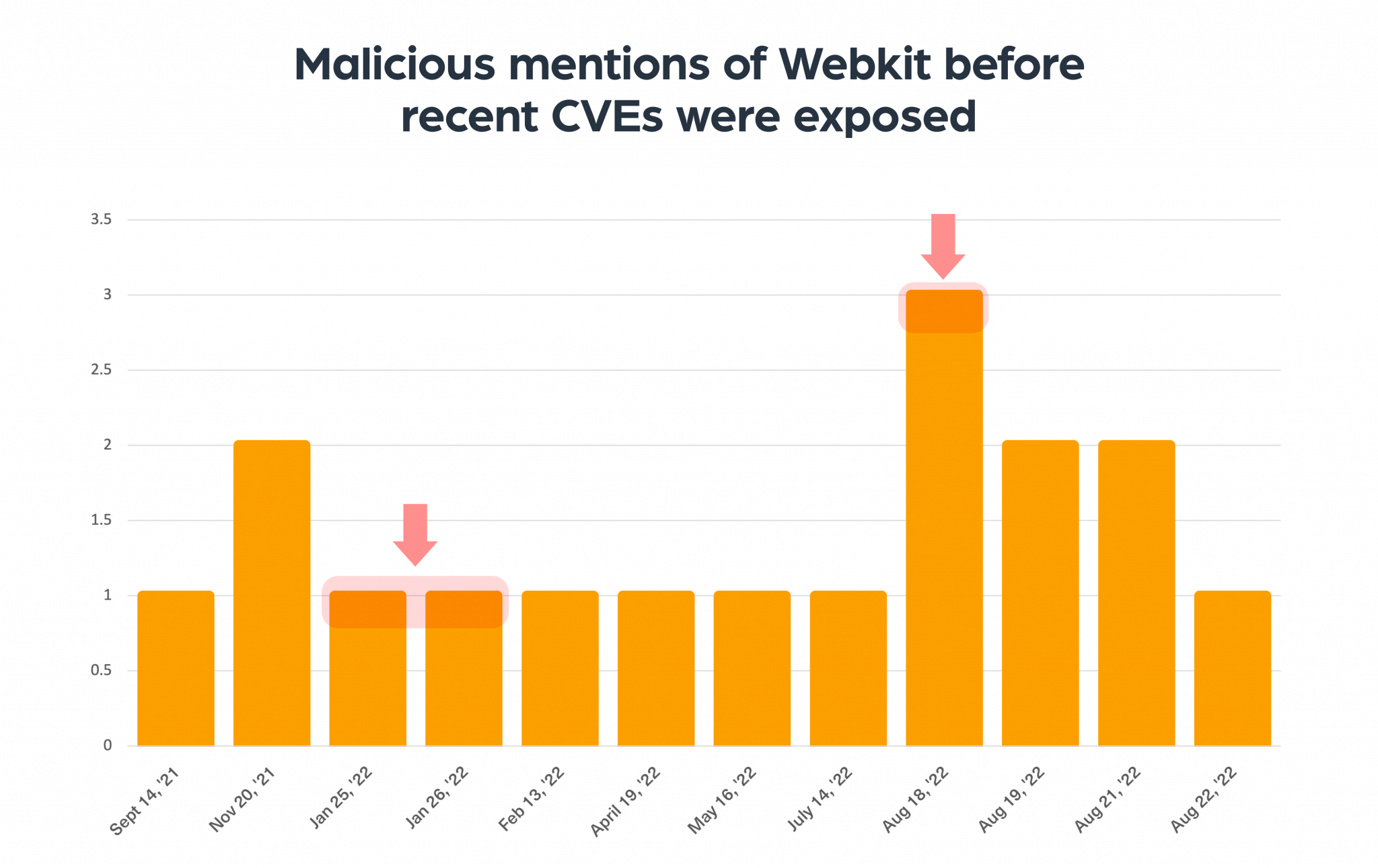
We used our cyber data feeds to search for indications around the WebKit and the out-of-bounds issue that was exploited including Kernel. We were able to find a pattern, in which in some cases, the discussion takes place even before the official publication of the CVE.
In many of the spikes you can see in the chart below, we were able to find early discussions between hackers about Webkit just before the CVEs were found, which means that they target a specific platform/system. This can serve as a valuable alert for organizations to proactively take measures and mitigate the potential threat.
Webz.io’s Dark Web API provides the critical data needed to discover discussions around vulnerabilities, and the expertise to locate malicious activities ahead of time by finding new exploits for specific platforms traded or discussed on the deep and dark web.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.