Emerging Dark Web Trends in 2025

As cybersecurity evolves, so does the technology used by threat actors, creating new challenges for the industry. According to Forbes, by 2025, damage related to cyber attacks is projected to reach $10.5 trillion annually. Tracking threat activity on the dark web reveals early warning signs of evolving cyber risks, enabling you to stay ahead of attackers and strengthen your defenses in 2025.
What we saw on the dark web in 2024
The past year revealed significant shifts in dark web activity. From the proliferation of decentralized marketplaces to the growing sophistication of social engineering techniques, the dark web has become a dynamic environment requiring constant vigilance. These trends provide valuable insights into what lies ahead.
Overall, we observed four key trends:
- The rise of malicious AI
- The growth of ransomware and RaaS
- Increased supply chain risk
- More indicators of insider threat on the dark web
The Rise of Malicious AI
Artificial intelligence is now being weaponized to conduct more effective attacks. From deepfake voice technology being used to mimic a CEO’s voice requesting urgent wire transfers, to attackers using AI to collect and curate personal information from social media to create a highly personalized spear phishing campaign, AI is reshaping the threat landscape. Threat actors can execute highly targeted and scalable attacks with minimal effort as more tools become accessible and easier to use. As a result of more threat actors using malicious AI in their cyberattacks, 75% of cybersecurity professionals had to modify their strategies last year to address AI-generated incidents.
Threat vectors in 2025
- AI-powered attacks on vulnerabilities
- Attackers use AI algorithms to scan systems and identify potential vulnerabilities more quickly and accurately than traditional methods.
- Analyze vulnerabilities and automatically generate exploit code, making it easier for less skilled attackers to launch sophisticated attacks.
- AI-powered malware can modify its code to evade detection, adapt to security responses, and propagate autonomously. The malware is harder to detect and mitigate.
- Social media and AI-powered social engineering attacks
- When threat actors use generative AI to write phishing emails, the resulting emails are highly personalized. The scam emails written by AI are more successful than similar emails written by humans.
- Data breaches from misuse of LLMs
- An employee uses a publicly available LLM – Gemini or ChatGPT – to increase productivity at work. Through tactics like data poisoning and model extraction attacks, threat actors can obtain sensitive organizational information. The stolen information is then used to break into a company’s network.
- CVE-2024-31621 – this vulnerability was found in Flowise, a popular LLM application builder. Threat actors who exploit this vulnerbaility would have access to proprietary information.
- Quantum computing threats
- Chinese researchers successfully demonstrated an attack on RSA encryption using quantum computing technology.
- RSA (Rivest-Shamir-Adleman) is an algorithm used to encrypt data.
- Chinese researchers successfully demonstrated an attack on RSA encryption using quantum computing technology.
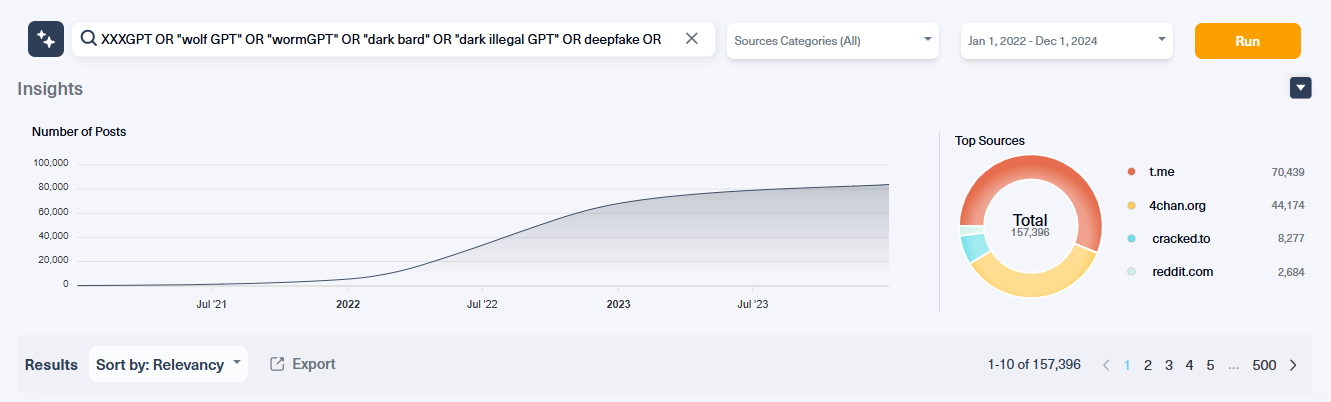
Growth of ransomware in 2024 due to AI and crypto
The ransomware ecosystem is maturing, with advancements in AI and cryptocurrency fueling its growth. Using ransomware-as-a-service (RaaS) models, non-technical users can easily execute sophisticated attacks. RaaS will continue to be popular on the dark web because it is a business model that helps ransomware groups to increase their revenue dramatically. When you put RaaS together with the advancement in AI and crypto anonymization you get one of the most favorite attack weapons by cyber criminals. Cryptocurrency continues to provide a pseudonymous method for ransom payments, so threat actors can remain anonymous and hard to trace to real people who can be arrested.
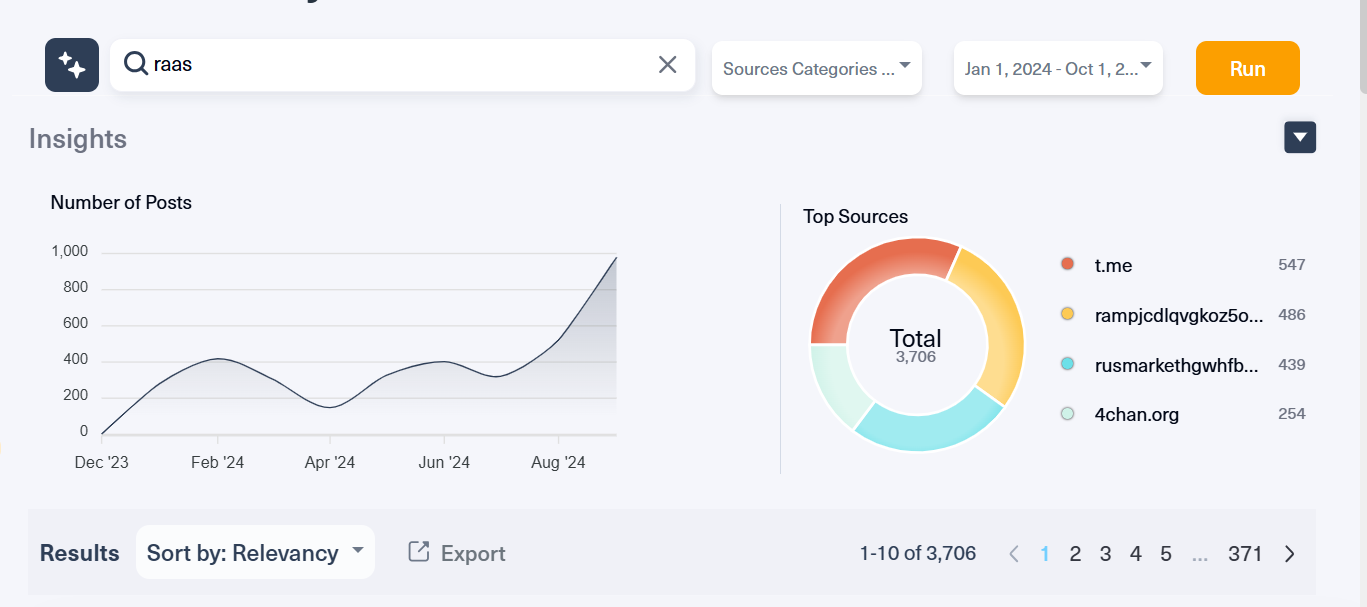
Targeted industries with examples of ransomware attacks:
- Manufacturing
- Retail
- Healthcare
The manufacturing, retail and healthcare industries hold a wealth of sensitive data. Healthcare organizations, for example, are rich in personal health information, which is highly valued on the dark web. Retail and manufacturing companies are often less prepared for sophisticated attacks, making them appealing targets for cybercriminals.
2025 Predictions
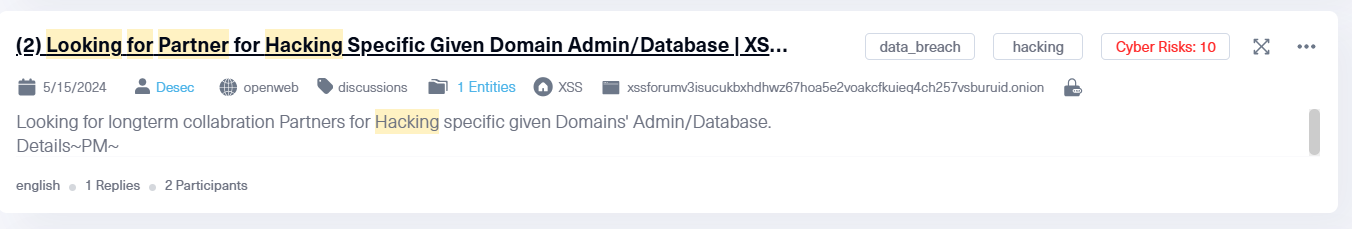
Looking ahead to 2025, we predict that the Internet of Things (IoT) will become the next major target. The more interconnected devices, the more potential entry points for attackers. The possibility for widespread disruption increases.
Extortion tactics, like “living off the land” attacks, will also become more common, as cybercriminals exploit existing systems to carry out their attacks.
Strategies to combat the growing threat of ransomware in 2025:
- Dark web monitoring, which allows businesses to track ransomware-related activity and identify early warning signs of an impending attack.
- Keeping software updated ensures that known vulnerabilities are patched before ransomware operators can exploit them.
- Implementing strong, unique passwords reduces the risk of unauthorized access to critical systems and data.
Supply chain risk
Supply chain vulnerabilities are exploited by dark web actors, and these attacks are on track to become a major financial burden. By 2031, supply chain attacks are projected to cost organizations a staggering $138 billion. The primary challenge in managing supply chain risks is the lack of visibility and transparency across interconnected systems. Many organizations have limited insight into the security posture of their suppliers. This makes it difficult to detect and mitigate potential threats before they impact the business. These disruptions can lead to production delays, financial losses, and a compromised ability to meet customer demands.
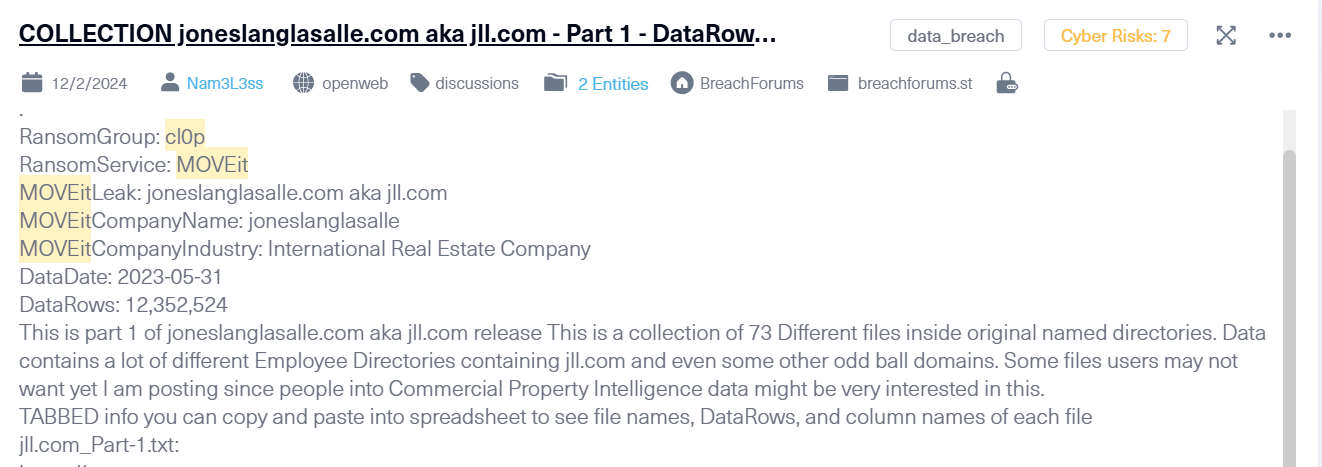
In 2024, several key trends related to supply chain attacks have emerged on the dark web:
- Third-party risks
- The AT&T data breach exposed call and text records for nearly all of its US subscribers. Hackers accessed this data through a third-party cloud platform, exploiting a vulnerability in the supply chain.
- Data breaches
- Sensitive customer or proprietary information continues to be a valuable target for cybercriminals. Data breaches can expose confidential data, leading to severe reputational damage and financial losses.
- Supply chain disruptions caused by
- Cyberattacks
- Geopolitical events
- Organized boycotts
- Misinformation campaigns
- Theft of intellectual property and counterfeit products
- There is a growing threat of intellectual property theft, including the theft of design documents, manufacturing methods, and research.
- Attackers undermine brand integrity and undermine product integrity through counterfeit products and brand impersonation.
2025 Predictions
Looking ahead to 2025-2026, the supply chain landscape will remain a complex mix of persistent challenges and emerging opportunities. As organizations become more connected through third-party vendors and service providers, cyberattacks will become more common. To mitigate these risks, organizations must invest in cyber threat intelligence focused on the full supply chain, including shadow IT. Dark web monitoring tools, like Lunar, powered by Webz.io, can help identify potential threats and complications. These tools provide early visibility into malicious activities within the supply chain ecosystem. This proactive approach will be essential for protecting against disruptions and safeguarding critical business operations.
Insider risk: the human factor in cybersecurity
When discussing cybersecurity, external threats often dominate the conversation. However, insider threats—those originating within an organization—remain a significant and growing concern. In 2024 alone, 83% of organizations reported at least one insider attack, according to Cybersecurity Insiders’ 2024 Insider Threat Report. The Verizon Data Breach Investigations Report highlights a dramatic increase in the percentage of breaches involving internal actors, jumping from 20% to 35% this year.
What is insider threat?
An insider threat involves any authorized individual, such as an employee, contractor, or business partner, who misuses their legitimate access to harm an organization. There are three categories of insider threats::
- Malicious Insider
- A person who deliberately steals data, sabotages systems, or disrupts operations.
- Negligent Insider
- An individual who unintentionally exposes vulnerabilities due to carelessness or lack of awareness.
- Compromised Insider
- A user whose credentials are stolen and exploited by an external attacker.
Insider Threat Indicators on the Dark Web
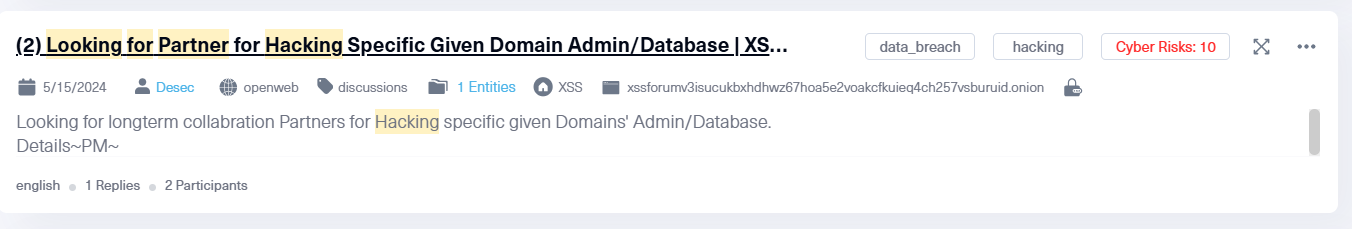
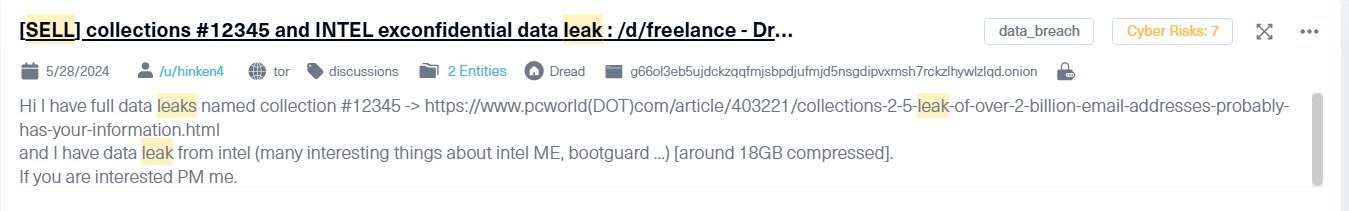
The dark web often serves as a platform where insider threats begin to take shape. Using tools like Lunar by Webz.io, organizations can uncover critical indicators, such as:
- Posts on hacking forums or marketplaces where threat actors seek or sell insider access to corporate networks.
- Confidential company information listed on dark web marketplaces, which may stem from malicious insiders or accidental exposure by negligent employees.
- Posts on hacking forums where hackers solicit guidance on penetrating specific organizations, which may involve insiders.
- Posts hinting at plans to leak or steal company information, indicating potential insider or external threats.
2025 Predictions
As insider threats evolve in 2025, the dark web will continue to play a crucial role in their facilitation. Companies must adopt a proactive stance by expanding their dark web monitoring activities to detect early warning signs of insider risk.
Solutions
In addition to leveraging dark web intelligence, organizations should prioritize:
- Employee awareness training: Educating staff on cybersecurity risks and fostering a culture of accountability.
- Zero-trust policy:
- Data loss prevention solutions: Monitoring and safeguarding sensitive information to prevent leaks or unauthorized transfers.
Insider threats may not always make headlines, but their impact can be devastating, often surpassing that of external attacks. Monitoring the dark web for indicators and implementing comprehensive prevention strategies can reduce these risks and safeguard organizations’ operations.
In the future, when attackers plan we notify
Want to stay ahead of dark web risks? Discover the 7 features your dark web monitoring solution needs to have in order to be effective.