The 5 Most Active Hacktivist Groups of 2024
In 2024, hacktivist groups continue to influence global events. They are motivated by political, social, and ideological agendas. These groups deploy various tactics, including Distributed Denial of Service (DDoS) attacks, website defacements, and data breaches, to push their causes forward.
As we closely monitor this phenomenon, it’s clear that hacktivism is on the rise, fueled by increasing political polarization. Conflicts like those in Ukraine and Israel have further amplified this trend.
This article reviews the five most active hacktivist groups of 2024, including an analysis of their key operations, motivations, and the broader impact of their actions on global affairs, based on insights gathered from their Telegram channels.
We used Lunar, Webz.io’s Dark Web Monitoring tool, to query these groups and gather the insights presented in this article.
1. NoName057(16)
Active since: March 2022
Known for
Allegedly a Russia-based group, they focus on DDoS attacks, website defacements, and data exfiltration. They are known for targeting government websites and media outlets, particularly in countries supporting Ukraine in the ongoing Russia-Ukraine conflict. They frequently claim responsibility for attacks via social media and Telegram.
Notable operation in 2024
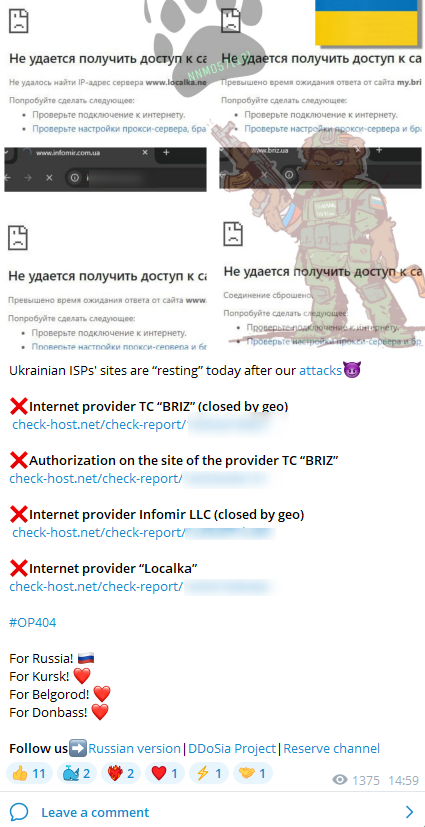
As part of their #OP404 campaign that started in August 2024, NoName057(16) is targeting government and media websites in Ukraine and in countries supporting Ukraine, particularly NATO members. The operation aims to disrupt access to these sites through DDoS attacks, symbolizing the “404 page not found” error, reflecting the campaign’s goal of taking websites offline.
2. SiegedSec
Active since: April 2022
Known for
Commonly self-described as the “Gay Furry Hackers”, and led by an individual under the alias “vio”. The group focuses on data breaches, defacement attacks, and leaking sensitive information. Known for exfiltrating government and corporate data, often leveraging SQL injection vulnerabilities and DDoS attacks.
Notable operation in 2024
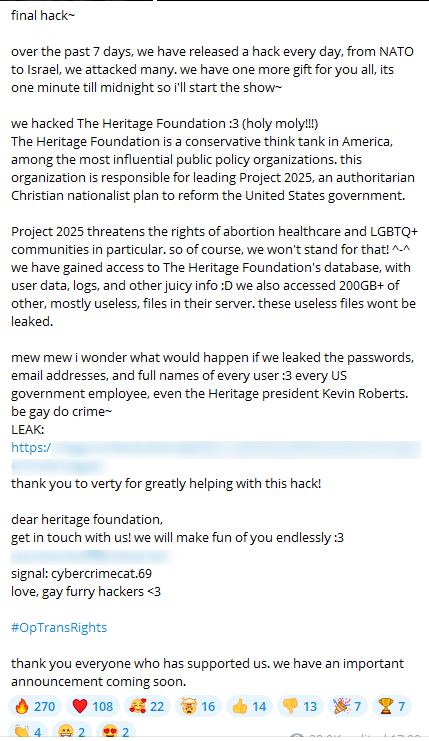
Even though the group disbanded in July of 2024, we chose to write about them due to their history of highly active, large-scale operations. In their allegedly final campaign, dubbed #OpTransRights, the group breached the database of The Heritage Foundation, leaking sensitive data, including full names, email addresses, and passwords. The group released the data on their Telegram channel and included a chat transcript with Kevin Roberts, the president of The Heritage Foundation.
3. Cyber Army Of Russia Reborn
Active since: January 2023
Known for
This Pro-Russian group is believed to be linked to the notorious Russian Advanced Persistent Threat (APT) group Sandworm, which operates under Russia’s Military Intelligence Agency. Their politically motivated attacks primarily aim to further Russian interests, particularly in conflicts involving Ukraine and against NATO-aligned nations. The group often utilizes Telegram to organize their operations and disseminate stolen data.
Notable operation in 2024
#OpSpain is a cyber campaign launched by pro-Russian hacktivist groups, including Cyber Army of Russia Reborn, targeting Spanish government websites and media. The operation involves DDoS attacks and defacements, aiming to disrupt services and spread pro-Russian propaganda. The campaign is a retaliation against Spain’s support for Ukraine and its alignment with NATO, reflecting the group’s broader anti-Western agenda.
4. 𝐈ndian Cyber Force
Active since: December 2022
Known for
This highly active Indian hacktivist group collaborates with other pro-India teams like TeamUCC, Team-Network-Nine, and BlackDragonSec. A pro-Israel group, they are known for claiming cyber attacks on critical infrastructure in multiple nations, including Bangladesh, China, Pakistan, and Indonesia. It is difficult to verify the strong claims made by this secretive group, but we have seen an increase in their activities in recent months. In addition to their Telegram channel, they also maintain a Twitter page.
Notable operation in 2024
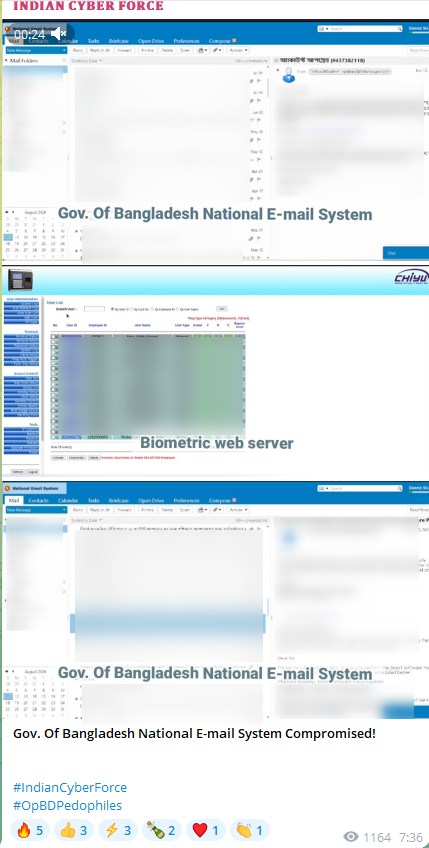
The group has recently launched cyberattacks on Bangladesh, releasing videos claiming to have hacked the network monitoring dashboard of Grameenphone Telecom and other ISP providers, as well as the Bangladesh Government’s national email system.
5. UserSec
Active since: February 2022
Known for
UserSec is a pro-Russian group known for carrying out Distributed Denial-of-Service (DDoS) attacks and publishing data leaks, primarily targeting entities that support Ukraine. They frequently collaborate with other pro-Russian hacktivist groups, such as NoName057(16) and KillNet, to amplify the impact of their campaigns.
Notable operation in 2024
After the arrest of Telegram CEO Pavel Durov, several pro-Russian groups, including UserSec, launched attacks on French entities under the campaign hashtag #FreeDurov. In a recent joint operation, UserSec and The Cyber Army of Russia Reborn successfully took down the websites of the National Court of France and the Paris Tribunal.
Hackist activity in 2024 is categorized by the persistent actions of groups like NoName057(16), Cyber Army of Russia Reborn, and UserSec, and others. They use the dark web and platforms like Telegram to coordinate and execute attacks on government institutions and private organizations. Their influence and motivations turn global conflicts into global cyber conflicts. Unfortunately, these groups are not going anywhere. Cybersecurity professionals need to be aware of the groups and their tactics.
Finding evidence of hacktivist attacks on the dark web and Telegram offers critical insights into the tactics, targets, and motivations of these groups. This visibility enables proactive threat detection, allowing security teams to anticipate and defend against potential attacks before they escalate. By monitoring these platforms, professionals can track discussions, leaks, and coordinated efforts, helping them strengthen their organization’s defenses, respond more effectively to breaches, and better understand the evolving threat landscape.