Account Takeover: Why is Dark Web Monitoring Critical to Protect Business

Account Takeover (ATO) has rapidly become one of the most significant cyber threats plaguing enterprise businesses worldwide. According to Sift, ATO attacks have increased 354% year-over-year in 2023 resulting in nearly $13 billion in associated losses. Beyond the upfront costs of ATO, organizations often face long-term risks such as massive regulatory fines, operational disruption, and degradation of client base and reputation just to highlight a few.
From SMBs to Fortune 500 companies, everyone is at risk.
With organizations of all sizes and in nearly every sector at risk, now is the time to make a cohesive and effective strategy to combat account takeover from the ground up.
Table of Contents
- What is account takeover?
- The dark web: A breeding ground for ATO threats
- How cybercriminals sell credentials on the dark web
- How can dark web monitoring detect the sale of ATO tools?
- Stealer logs and the ongoing risk to your sensitive data
- Mitigating stealer logs risks
- How can MSSPs/MDRs leverage dark web monitoring to counter ATO threats?
- How can enterprise organizations mitigate ATO risks with dark web monitoring?
- How to mitigate ATO
What is account takeover?
The world of account takeover is complicated enough without being lost in the jargon. To streamline your understanding of ATO we’ve defined some of the most significant terms below:
- Account Takeover: Account takeover occurs when an unauthorized individual gains access to a user’s account, typically through methods such as credential stuffing, phishing, or brute force attacks. Once inside, the attacker can perform malicious activities such as stealing sensitive data, committing fraud, or using the account to launch further attacks.
- Compromised Credentials: Compromised credentials occur when login details have been stolen or accessed by unauthorized parties. Typically, compromised credentials may include usernames, passwords, security questions, and other sensitive details used to verify a user’s identity and gain access to accounts and systems.
- Privileged Access: Privileged access refers to the permissions granted to users, applications, or systems that allow them to perform administrative or sensitive tasks beyond those available to regular users. This includes configuring systems, accessing sensitive data, and installing software.
- Sensitive Data: Sensitive data is information that must be protected from unauthorized access to safeguard privacy or security. This includes personally identifiable information (PII), financial data, intellectual property, and any other data that, if exposed, could lead to harm or legal repercussions.
Now that we’ve defined the core elements of account takeover, our focus must shift to the most common vectors for attack. While it’s impossible to list every risk factor or tactic, we’ll present some of the most prominent and widely publicized methods of attack below.
- Spear Phishing: Spear phishing is a targeted phishing attack where cybercriminals tailor their messages to a specific individual or organization, often using information gathered from reconnaissance to make the attack more convincing.
- Malware Campaigns: Malware campaigns are orchestrated efforts by attackers to distribute malicious software (malware) on a large scale. These campaigns often involve: email attachments, malicious websites, or software exploits to infect victims’ systems.
- Zero Day attacks: Zero Day attacks exploit previously unknown vulnerabilities in software or hardware that developers have not yet patched. These attacks can be particularly damaging because they exploit weaknesses before security measures can be implemented.
- Infostealers: a Trojan that is designed to gather information from a system. The most common form of info stealer gathers login information, like usernames and passwords, which it sends to another system either via email or over a network.
- APT: Acronym for advanced persistant threat; Attack campaign where an intruder gains unauthorized access to a network and evades detection for delayed attack or espionage.
- Credential Stuffing: A common technique utilized by cybercriminals to test if historically exposed e-mail addresses and password combinations are valid logins across multiple commercial websites.
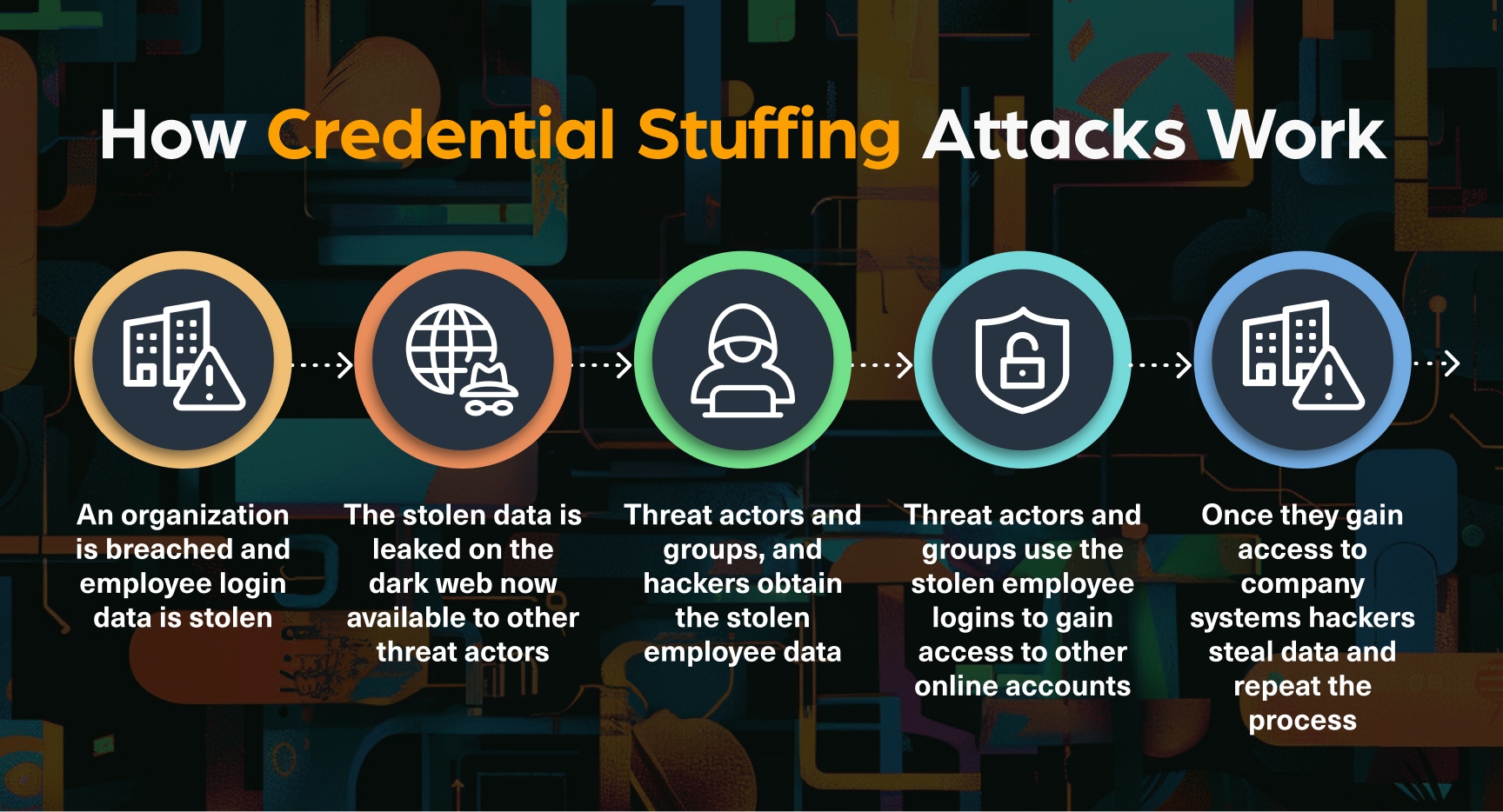
After defining the terms and methods of attack, we shift our collective focus to where account takeover threats originate and to effective strategies to mitigate the risks.
The dark web: A breeding ground for ATO threats
It is easy to get caught up in the hype of the dark web, with its ominous media coverage and perceived barriers to access. But is it really so malicious? What happens on the dark web and how is it different from the open web the majority of professionals have been operating on for decades?
The short answer might not be so far removed from the perceived boogieman lurking in the figurative shadows.
In the following table, you can find relevant types of common illicit content sorted according to the layer of the web and site type we usually find them on and the sort of content:
| Type of Illicit Content | Open Web | Deep Web | Dark Web |
| Stolen Credentials | Phishing sites, paste sites | Private forums, unindexed websites, chatting apps | Data stores, marketplaces, credential dump sites |
| Phishing Kits | Scam websites, forums | Private forums, chatting apps | Marketplaces, forums |
| Botnets | Paste sites, forums | Private forums, chatting apps | Marketplaces, botnet rental sites |
| Fraudulent Transactions | Scam websites, forums | Private forums, chatting apps | Marketplaces |
| Credit Card Fraud | Scam websites, paste sites, data stores | Private forums, chatting apps | Data stores, marketplaces, carding forums |
| Account Data | Paste sites, forums | Private databases, unindexed forums, chatting apps | Data stores, marketplaces, data dump sites |
| Fake Documents | Scam websites, forums | Private forums, chatting apps | Marketplaces |
| Identity Theft Services | Scam websites, forums | Private forums, chatting apps | Marketplaces |
| Social Engineering Kits | Scam websites, forums, paste sites | Private forums, chatting apps | Marketplaces, forums |
Consequently, the dark web is frequented by both new and experienced hackers, who use its various forums to share information essential for carrying out cyber attacks and innumerable fraudulent activities.
How cybercriminals sell credentials on the dark web
Cybercriminals use various hacking forums, marketplaces and datastores on the dark web to sell credentials. The credentials range from financial Information such as bank account details and credit card numbers to corporate credentials like login details for company email accounts and other internal systems.
Some of the ways threat actors use to sell credentials on the dark web include:
- Direct sales – cybercriminals list the credentials they have for sale on different sites, often including sample data to prove authenticity. Buyers can purchase specific items directly.
- Auctions – various dark web marketplaces allow sellers to auction off datasets of credentials to the highest bidder.
- Subscriptions – sellers sometimes offer subscription-based services where buyers pay a recurring fee to access a stream of freshly stolen credentials.
How can dark web monitoring detect the sale of ATO tools?
According to Egress, 58% of organizations experienced account takeover (ATO) incidents in the last 12 months, with 79% starting from phishing emails that harvested employee credentials. Many of these credentials were obtained through the dark web.
With the increase in dark web marketplaces and the global demand for Malware-as-a-Service, ATO has become a common attack method to breach cyber defenses and steal vital data.
To counter these attacks, organizations are implementing defensive measures such as firewalls, strong system segmentation, and employee cybersecurity training. While these steps can help mitigate and even prevent some attacks, they are not sufficient for long-term risk prevention.
Stealer logs and the ongoing risk to your sensitive data
That’s where monitoring the dark web comes in. By tracking the release of stealer logs generated by infostealers, threat intelligence professionals gain critical insights into what data has been compromised.
Stealer logs, compiled by malware like Redline and Raccoon, contain sensitive information stolen from compromised devices. This data includes browser history, cookies, visited websites, installed software, and user information. These logs present a significant risk because they can be exploited or sold by Initial Access Brokers (IABs) to orchestrate various attacks, including ransomware, social engineering, and Remote Access Trojans (RATs).
Most damning about stealer logs is that they are fluid and are constantly being updated with revised and up-to-date compromised data. Where in the past a data breach might only represent a moment in time, stealer logs create a doomsday scenario in which nothing on your device is safe; not your password, your pictures, your every document or email will be secure. until that malware is removed.
Mitigating stealer logs risks
To mitigate the risks associated with stealer logs and leaked databases organizations need first to identify the breach and monitor for leaked Personally Identifiable Information (PII) of employees and customers, especially those with privileged accounts.
As any seasoned professional can attest finding stealer logs in the deep and dark web is a complex task. We at Webz.io continuously scan the deep and dark web to expand our scope of stealer logs.
The simplest way to search for them is by using a dark web monitoring tool, such as Lunar.
To illustrate it, we used Lunar’s enriched.domain.value:Airbnb.com filter to retrieve results that mentioned the Airbnb.com domain. We further narrowed our search to stealer logs associated with the Airbnb.com domain using the tag “Stealer_logs”.
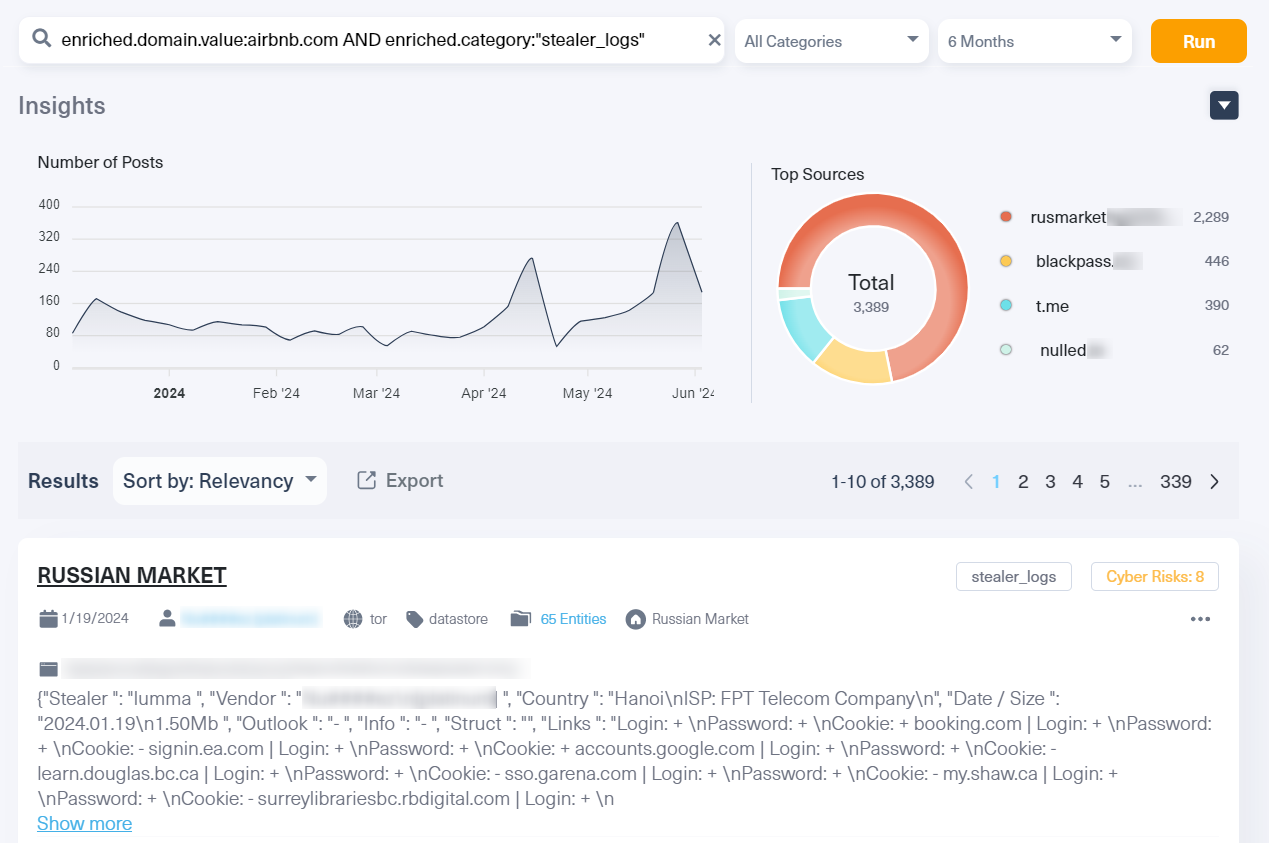
By actively tracking stealer logs on the dark web, with dark web monitoring tools like Lunar, Managed Security Service Providers (MSSPs), and Cyber Threat Intelligence (CTI) teams can stay ahead of emerging threats, safeguard client data, and mitigate future cyberattacks.
How can MSSPs/MDRs leverage dark web monitoring to counter ATO threats?
In this era of evolving cyber risks and even more massive financial consequences we don’t need any more theoretical, or more pie-in-the-sky ideas. With customers fleeing at the first signs of data compromise and devastating corporate fines in toe few organizations can afford the aftermath of a well-targeted ATO attack.
When it comes to mitigating risks from the dark web MSSPs, MDRs and other invested players must create iron-clad approaches integrating a defense-in-depth ideology to stop the torrents of cyber attacks plaguing enterprises worldwide.
Leveraging Dark Web Monitoring
- Credential Monitoring: Continuously monitor the dark web for leaked credentials and stealer logs. By identifying compromised accounts early and active breaches, MSSPs and MDRs can prompt organizations to remove malware, reset passwords, and implement additional security measures to mitigate and prevent attackers from exploiting the stolen data.
- Threat Intelligence: Gather and analyze threat intelligence from the dark web to understand the latest tactics, techniques, and procedures (TTPs) used by cybercriminals. This intelligence helps in proactively adjusting security measures and defenses to counter emerging threats.
- Alerting and Reporting: Establish real-time alerting mechanisms for any relevant findings on the dark web. Immediate notifications allow organizations to take swift action to mitigate risks and protect sensitive information.
- Phishing Detection: Identify phishing kits and campaigns on the dark web that target the organization. By understanding these threats, MSSPs and MDRs can develop specific defenses and user awareness programs to counteract phishing attempts.
Integrating with Existing Security Measures
- Identity and Access Management (IAM): Use insights from dark web monitoring to enhance IAM solutions by detecting and responding to compromised accounts, ensuring that unauthorized access is swiftly addressed.
- SIEM & UEBA Integration: Feed dark web intelligence into SIEM and UEBA systems to enrich the data set, improving the detection of suspicious activities and anomalous behaviors that may indicate account compromise.
- Endpoint Detection and Response (EDR): Use dark web insights to update EDR solutions with the latest threat indicators, enhancing their ability to detect and respond to malware and other malicious activities.
Additional Measures:
- Least Privilege Access: Based on dark web findings, review and adjust user access levels to minimize the risk posed by compromised credentials.
- Regular Security Audits: Incorporate dark web intelligence into regular security audits to identify new vulnerabilities and threats that have emerged, ensuring a proactive security posture.
- Data Loss Prevention (DLP): Use dark web monitoring to identify exfiltration tactics used by attackers and configure DLP solutions to detect and prevent these specific methods.
By leveraging dark web monitoring in these ways, MSSPs and MDRs can more effectively identify and counteract ATO threats, providing robust protection for their clients.
How can enterprise organizations mitigate ATO risks with dark web monitoring?
Enterprises organizations often employ sophisticated threat intelligence and security tools to safeguard their digital assets and mitigate risks. These tools may include Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and advanced endpoint protection platforms.
However, as cybercriminals increasingly leverage the dark web to trade stolen credentials and other sensitive information, integrating dark web monitoring and analyzing stealer logs have become critical components in countering Account Takeover (ATO) threats. By enhancing their existing security measures with dark web intelligence, enterprises can stay ahead of potential ATO attacks and protect their critical data.
Some of the steps enterprises can take include:
- Integrating dark web intelligence – by incorporating dark web monitoring tools into existing threat intelligence frameworks.
- Setting up real-time alerts to detect compromised credentials related to the organization.
- Enhancing authentication protocols – introducing stronger authentication measures, including multi-factor authentication (MFA).
- Cross-checking internal data, including security logs, with dark web threats.
- Proactive threat hunting – use dark web intelligence to conduct proactive threat hunting.
- Leveling up your incident response by integrating dark web findings into incident response plans.
How to mitigate ATO
Never in history have the risks and whole-scale destruction emanating from the dark web been so great. From ad hoc players to major multinational hacking groups everyone is utilizing the dark web’s vast illicit resources to compromise your company’s data. To counter the ever-rising swells of malicious data leaks and account takeovers a cohesive defense in depth focused policy must be implemented.
By continuously monitoring the dark web and tracking infected devices with info stealers (using such tools as Lunar) securing endpoints, and enhancing employee cyber education organizations large and small can drastically reduce their attack surface and mitigate the risks of ATO.
Dark web monitoring offers a proactive defense against these evolving dangers. Choosing the right dark web monitoring tool or data via dark web monitoring API can help your organization track evolving threats, fortify defenses, and swiftly respond to a constantly evolving malware and phishing threat landscape.
Talk to Webz.io to discuss how we can help you – whether you need a dark web monitoring tool or dark web data to automate your own dark web monitoring solution.