Ransomware Trends on the Dark Web Following LockBit and ALPHV Takedowns

After collecting numerous hefty ransoms, the purported takedown of two notorious ransomware groups, LockBit and ALPHV (aka BlackCat and Noberus), seem like major victories for law enforcement. However, for cybersecurity experts, these takedowns reveal a harsh reality — that while individual groups may face setbacks, the criminal ecosystem fueling ransomware attacks is far from eradicated.
Today, we’re exploring the current state of ransomware, identifying any changes in ransomware activity, and examining cybercriminals’ overall response to these events. We’ll use Lunar, Webz.io’s dark web monitoring and data breach detection tool, to investigate activity within the deep and dark web networks these cybercriminals frequent and to delve deeper into our findings.
Have ransomware groups decreased their activities on the deep and dark web?
Our analysis of dark web activity reveals that ransomware groups operate largely unabated. LockBit ranks #1 at this time, with other major ransomware players like Play Ransomware and Black Enough not far behind.
| Ransomware Group | No. of Victims |
| LockBit | 160 |
| Play Ransomware | 38 |
| Black Basta | 36 |
| Akira Ransomware | 19 |
| 8BASE | 19 |
Despite its recent takedown, LockBit maintains its position as the most active group with a substantial list of victims. Among the companies targeted by LockBit are Boeing and the UK’s Royal Mail. LockBit brought in an estimated $120 million from more than 2,000 victims worldwide.
Have any new ransomware groups recently emerged?
Over the past month, a few new ransomware groups have emerged, operating their own websites and channels across deep and dark web networks. Among these new groups are DoNex Ransomware and Blackout Ransomware.
Security news sites report that DoNex Ransomware often uses methods involving file encryption and data exfiltration. This ransomware group has primarily targeted European-based companies, among them Chocotopia, Elsap (Elsap.it), MIREL asbl, P-Fleet, and Van der Helm. Their data is available for download from dark web marketplaces.
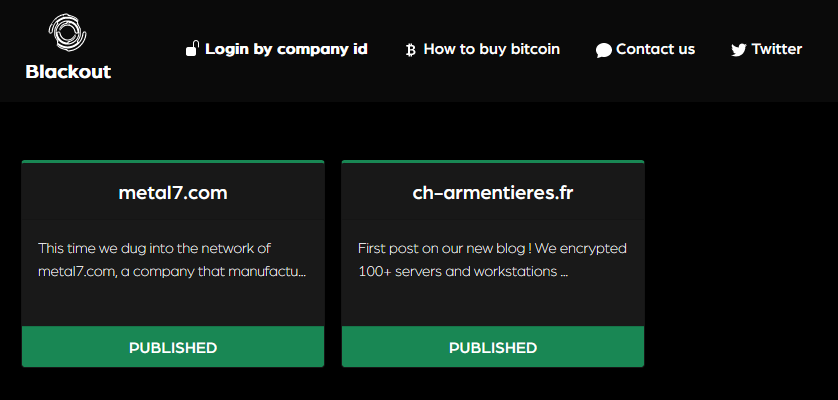
Blackout Ransomware encrypts a victim’s system and data, locking them out of their device or company network. So far, the group has published sensitive data belonging to two companies — one from Quebec and the other from France. These companies haven’t paid the required ransom.
Have the discussions around ransomware on hacking forums been affected by the recent LockBit and ALPHV takedowns?
Our analysis using a new “ransomware” tag in Lunar revealed a roughly 30% increase in ransomware-related posts and messages on dark networks. This significant rise in ransomware talk began right after LockBit’s reported takedown by the FBI.
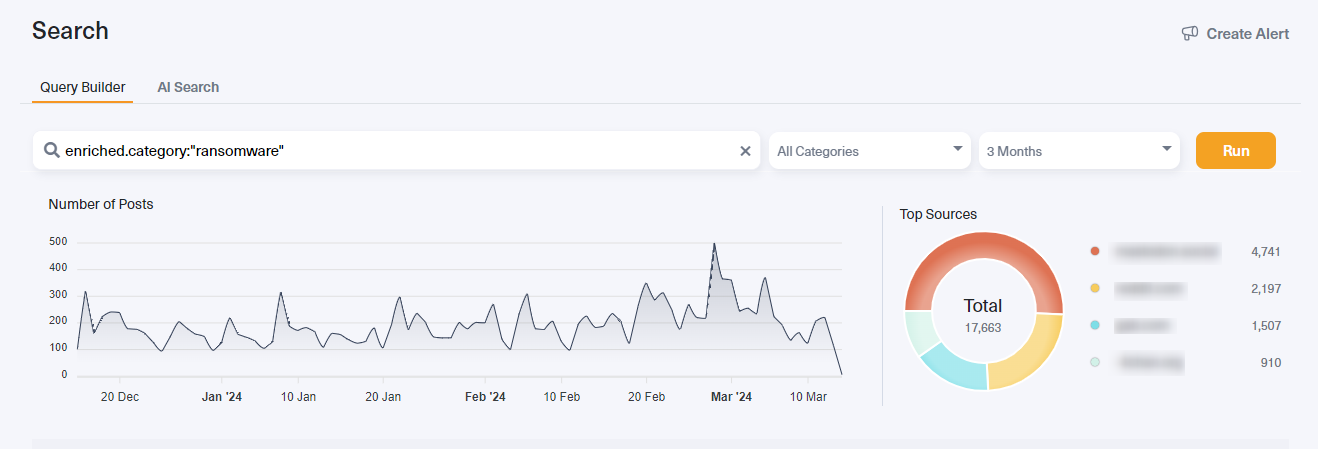
This surge in ransomware posts coincides with heightened interest in the takedown events involving LockBit and ALPHV. Cybercriminals across the deep and dark web are also talking more about ransomware in general. Topics range from new ransomware strains and the file decryptors for them to law enforcement operations aimed at ransomware groups worldwide.
What other recent ransomware trends did Lunar detect?
With the help of Lunar, our cyber analysts detected two other noteworthy trends emerging around the same time as the LockBit and ALPHV takedowns:
- Increasing activity around ransomware group recruiting
- Growing interest in Ransomware-as-a-Service (RaaS)
While there may or may not be any direct links between these two ransomware trends and the recent events in the ransomware space, we think these trends are still well worth exploring. Let’s see what Lunar helped us learn about these two trends.
#1. Increasing activity around ransomware group recruiting
Lunar helped us detect an increase in recruitment posts from long-established and newly created ransomware groups. These posts advertise lucrative opportunities for affiliates — a stark reminder that the pool of potential cyber attackers remains vast. This constant influx of fresh recruits underscores the resilience of the ransomware ecosystem and the need for a multi-pronged approach that disrupts the top players and the entire infrastructure that enables these ransomware attacks.
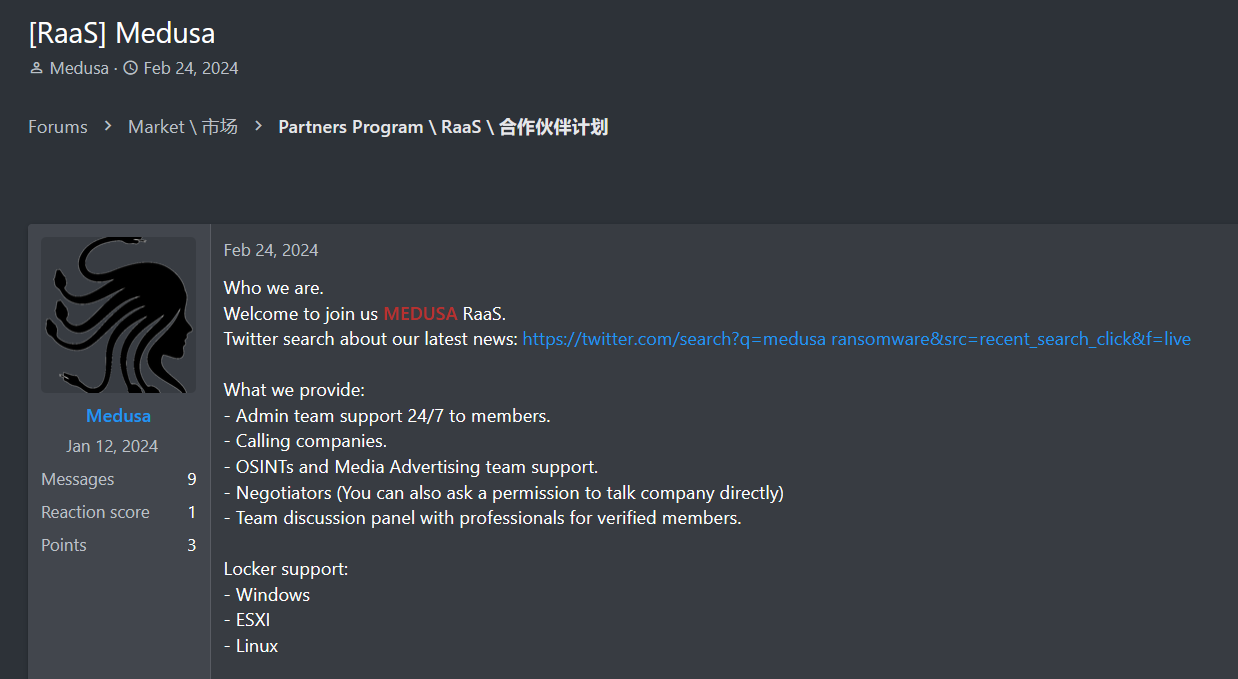
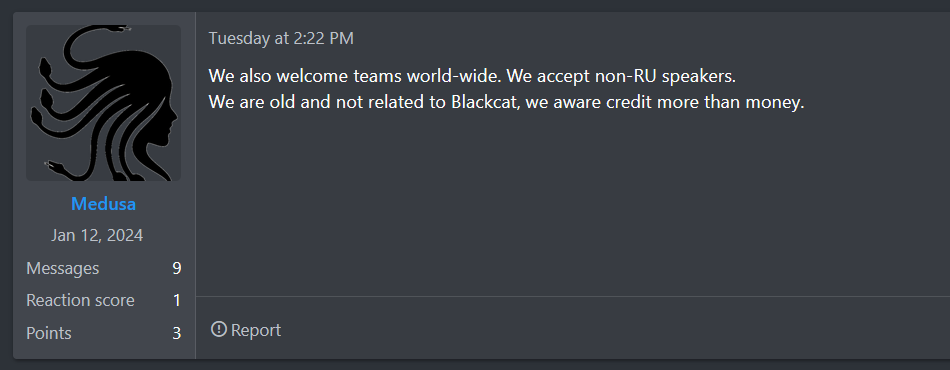
One interesting example of a recruitment post comes from the Medusa ransomware group. The group published it on the well-known ransomware forum RAMP, where members can see that Medusa is seeking recruits to join its ransomware efforts. The post notes that the group is unrelated to Blackcat (ALPHV) and prioritizes credit over money. This glimpse into their operation strategy may indicate a new operational approach within the ever-evolving ransomware landscape.
#2. Growing interest in Ransomware-as-a-Service
Another intriguing trend emerging from dark web forums is the rise in discussions about Ransomware-as-a-Service (RaaS). RaaS platforms provide pre-built tools and infrastructure that allow individuals with little to no technical expertise to participate in ransomware attacks.
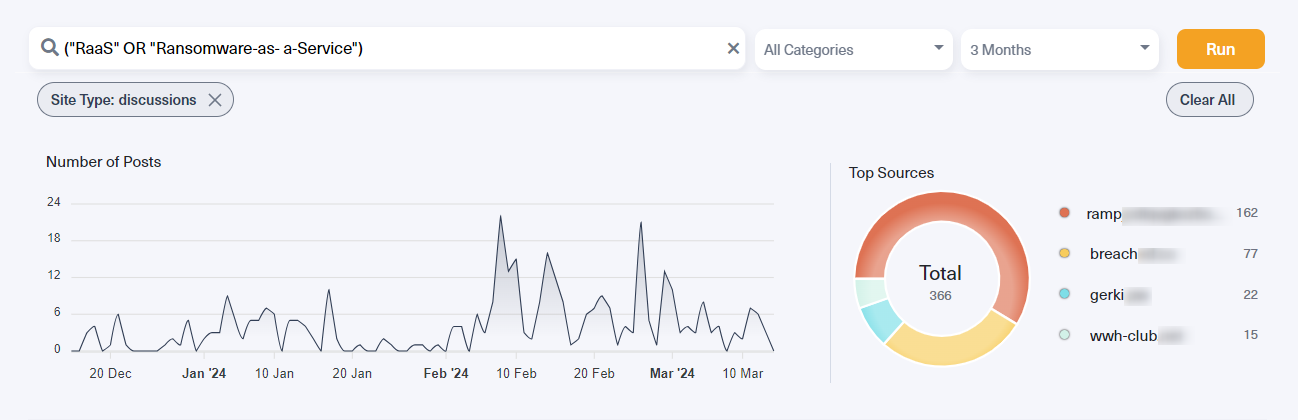
The increased talk about RaaS could signal a shift towards these services, potentially driven by two factors:
- New actors seeking a “safer” and less technical entry point to ransomware activities.
- Established ransomware groups diversifying their tactics with RaaS, using it as a backup to traditional methods.
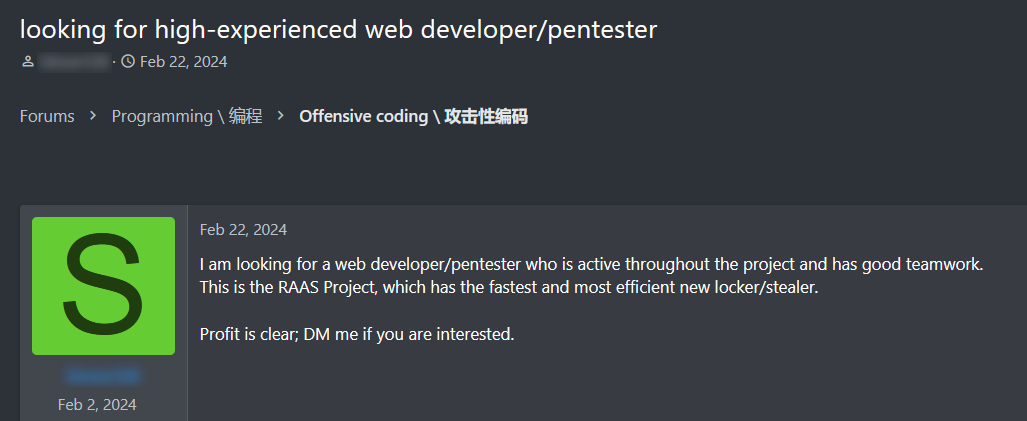
For example, the post in the screenshot below actively pursues a web developer/penetration tester for a RaaS project. The post was published within a hacking forum.
Here is a screenshot of a hacker forum Exploit.IN post. The poster is looking for a ransomware affiliate program:
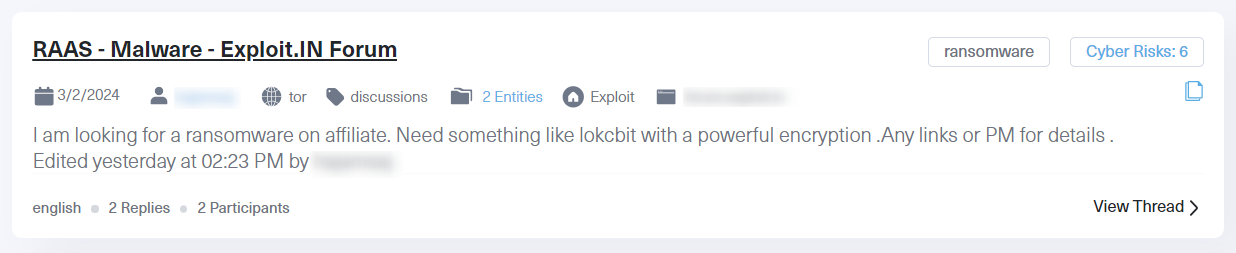
What grabs our attention is the poster’s specific request for “something like Lockbit with powerful encryption.” The continued desire for LockBit-like tools shows a disconnect between ransomware group takedowns and their impact on cybercriminals. Law enforcement may see LockBit’s removal as a win, but the demand for such effective ransomware tools persists within the criminal underground. As law enforcement removes one ransomware tool, another will quickly emerge to take its place.
The ransomware battle continues
The recent takedowns of LockBit and ALPHV are a small part of a larger ransomware battle. Ransomware groups like Medusa continue recruiting members, and more cybercriminals are joining discussions about RaaS tools on dark web forums. These trends paint a dark and disturbing picture — where cybercriminals adapt and persist despite takedowns by law enforcement. However, cyber analysts and security teams can use Lunar to search for emerging ransomware trends and risks — including new ransomware strains and distribution methods, collaborations among ransomware groups, and newly published sensitive data on the dark web. With Lunar, these teams can gain crucial insights that help them strengthen their defenses in the battle against ransomware attacks. Addressing this ongoing threat also requires a multi-faceted approach that disrupts recruitment efforts, dismantles RaaS operations, and fosters international cooperation to hold bad actors accountable.