The Internet we all use daily is really just the tip of a massive online iceberg. Only 4% of digital content is indexed and accessible via commercial search engines – the other 96% lies deep below the surface. While much of this 96% is legitimate content, a significant portion is decidedly less so. This is the dark web – well-known as an anonymous haven for drug trafficking, hacking, and other illicit activities. And the illicit activity on the dark web can directly and negatively impact organizations. That’s why closely monitoring the dark web can offer companies valuable insights into potential risks and threats to their reputation, intellectual property, customer data, and other mission-critical interests.
Surface vs deep vs dark web – what’s the difference?
It’s important to understand the difference between the open, deep, and dark webs:
- The open web (a.k.a. surface web, visible web) – Made of up web pages that have been indexed by web crawlers, open web content appears in search results on popular search engines and can be accessed by anyone without restrictions.
- The deep web – Comprising web pages that cannot be indexed owing to a tag in their HTML and are thus not accessible via search engines, most deep web content pages are simply private – like Reddit, for example. Deep web content is accessible via regular web browsers to authorized users.
- The dark web – Made of content that is not indexed by search engines nor accessible via regular browser, dark web content is accessed by special software like Tor, I2P, and Zeronet. Dark web user IP addresses remain hidden, so their activity remains anonymous – which is primary reason that the dark web is “dark”. The anonymity of the activity on the dark web makes it a haven for cybercriminals and illicit content.
What is dark web monitoring?
Dark web monitoring enables organizations and individuals to identify illegal activity or security threats that have the potential to directly impact them. It’s the process of scanning the dark web systematically – illicit online marketplaces, forums and other hidden platforms – to collect data that can help spotlight potential security threats, stolen data, or illegal activities.
For example, dark web monitoring solutions seek out evidence of fraud, identity theft or cyberattack directed at a specific target. This monitoring, run by organizations themselves or their MSSPs, searches for data like stolen login details, CVEs, financial data, zero day attacks, and sensitive organizational information.
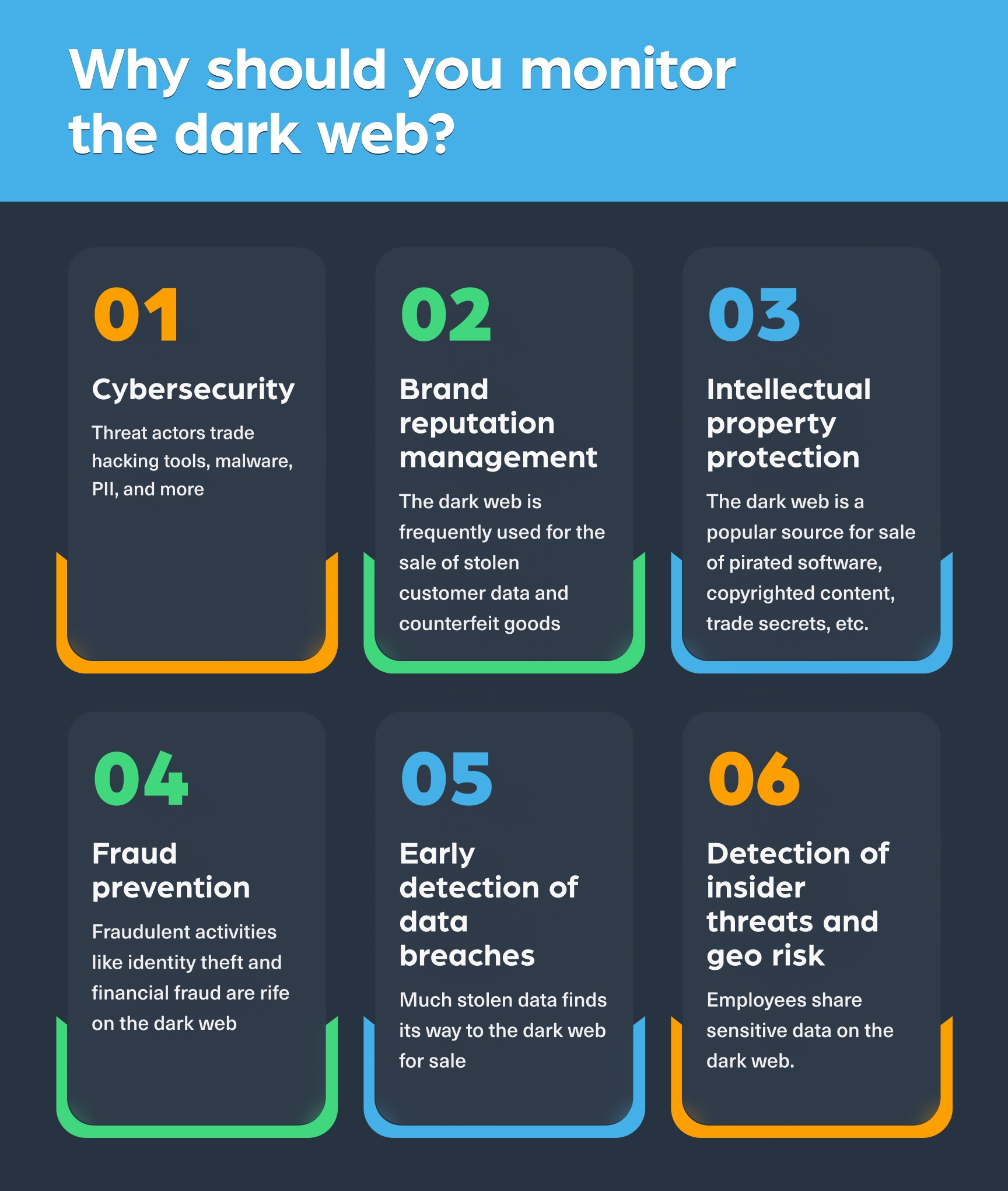
Why should you monitor the dark web?
Cyber analysts, automated intelligence platforms, businesses, government agencies, MSSPs, and other organizations need to proactively monitor the dark web as part of their ongoing risk mitigation strategy.
Dark web monitoring enables early detection of illicit activities with potentially far-reaching business consequences – data breaches, fraud, reputational damage, financial losses, damage to productivity, noncompliance, and more. More specifically, monitoring the dark web is crucial for:
- Cybersecurity – Hacking tools, malware, PII, and more – the dark web is a magnet for cybercriminals seeking to trade in the tools of their trade. By closely monitoring the dark web, organizations are able to identify specific threats or vulnerabilities attackers are planning to exploit – and can shore up their cyber defenses accordingly.
- Brand reputation management – Since the dark web is frequently used for the sale of stolen customer data and counterfeit goods, effective monitoring empowers brands to identify trademark infringement early on and take measures to protect their reputation and brand equity.
- Intellectual property protection – Pirated software, copyrighted content, trade secrets and more – the dark web is well-known as a source for sale and distribution of proprietary information. By monitoring the dark web, companies can quickly identify intellectual property theft and counterfeiting, then take swift action to mitigate damages from it.
- Fraud prevention – Fraudulent activities like identity theft and financial fraud are rife on the dark web. By scanning the dark web for early evidence of trade in customer personal and financial data, organizations can more proactively protect their clients, limit damages from fraud, and ensure constant compliance with strict fraud prevention regulations.
- Early detection of data breaches – Much stolen data finds its way to the dark web for sale. Often, the appearance of such data for sale is the first evidence of a serious yet undetected data breach. Effective dark web monitoring helps mitigate the impact of such breaches when they occur.
- Detection of insider threats and geopolitical risk – For both businesses and government agencies, the danger of employees sharing sensitive data via the dark web is acute. The consequences of such leaks can range from negative impact on business continuity to tangible geopolitical risk. Monitoring the dark web can catch such leaks before they spiral into crises.
Top five threats and vulnerabilities detected by dark web monitoring
Dark web monitoring can help detect and mitigate the effect of numerous cyberthreats and potentially damaging illicit activities, including:
- Stolen credentials – Usernames, passwords, and other login credentials are frequently compromised and sold or traded on the dark web. Monitoring can help the organization take immediate action to safeguard accounts from unauthorized access.
- Identity theft – Personal information like name, address, phone number, or email is often traded via the dark web for identity theft purposes. Ongoing monitoring enables early detection of such abuses, helping organizations and individuals mitigate potential damage.
- Data breaches – When an organization’s sensitive data – customer records, intellectual property, confidential documents, and more – is exposed on the dark web, response time is key to minimizing loss. Dark web monitoring helps organizations identify breaches faster, respond more effectively and remediate more thoroughly.
- Illegal activities – Discussions related to illegal goods and services like drugs, weapons, counterfeit products, hacking tools, and more are the precursors to actual transactions. Dark web monitoring enables law enforcement and security professionals to identify illicit activity early on and take action accordingly.
- Financial fraud – If financial information like credit card numbers, bank account details, or Social Security numbers are for sale on the dark web, effective monitoring helps organizations take the necessary measures to protect their financial well-being.
Conclusion
Effective dark web monitoring is an excellent way for organizations to lower risks and protect themselves against threats to their intellectual property, reputation, sensitive data, and more. The right dark web monitoring solution empowers security teams to preempt attacks – identifying potential threats before they impact the organization – and also helps surface undetected data leaks while protecting brand reputation and financial integrity.
Talk to Webz.io about our dark web monitoring platform and dark web data feeds for your own dark web monitoring solution.




