Brand Protection: The Threats Microsoft is Facing in Hacking Forums

Hacking forums on the deep and dark web are places where cybercriminals thrive. They discuss, share and even trade leaked databases, software vulnerabilities, hacking tutorials, and more. In most cases, hackers will not reveal their exact intentions and targets, but it is not uncommon to see discussions with specific details, such as mentions of company names, domains, and services that they target. In some cases, discussions on online hacker forums even correlate with cyberattacks.
As hacker forums play a big role in distributing information about vulnerabilities, tools, and threats, they are considered to pose a high risk. Monitoring them plays an important role in today’s threat intelligence, as tracking mentions of company assets on these platforms can help protect these companies’ assets.
In this post, we will review some examples of these early indicators of threats found on two of the main hacking forums: Breached and Exploit.
Let’s take a look at recent cyber threats we found against Microsoft Windows on dark web hacking forums:
Example #1: Exploit to Microsoft Windows vulnerability
The threat actor posted an exploit to CVE-2022-34718 (Windows TCP/IP Remote Code Execution Vulnerability) on Exploit hacking forum. The CVE was released on September 13, 2022, meaning it is still pretty recent and it is likely that it can be used as some Windows users may have not updated their software yet which would patch this vulnerability.
System updates in large organizations are a big operation that consumes a lot of time and resources. This means they don’t happen immediately after each software update is released. Even then, installation bugs can occur. Hackers are relying on these human errors when publishing these exploits, assuming these vulnerabilities are still available in some organizations (which has proven to be true in the past).
In the image below, you can see an example post where a threat actor shares a repository containing the exploit to Windows’ Remote Code Execution (RCE) vulnerability. RCE allows attackers to remotely execute commands on a machine, connecting to it over the network. In this case, in IPv6.
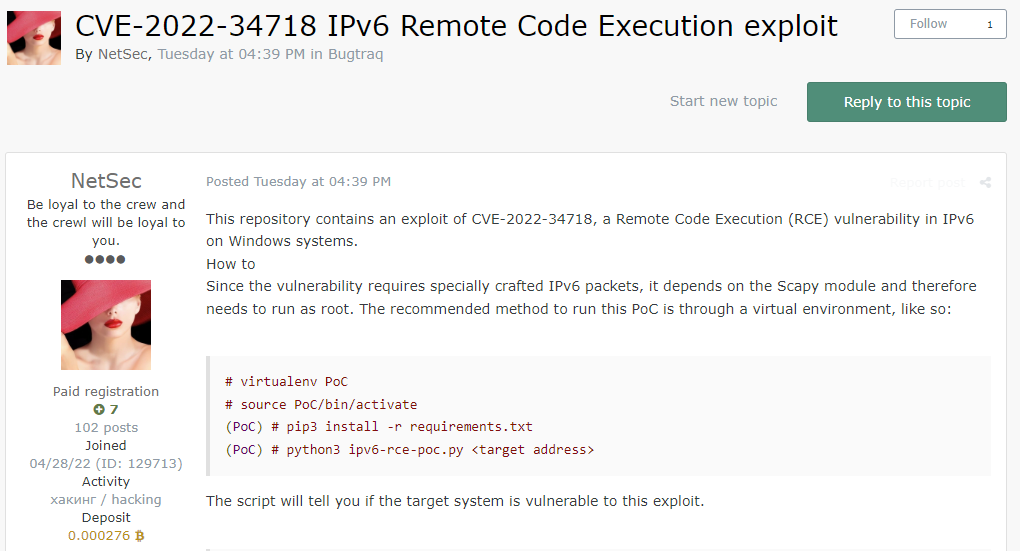
The hacker also shares a script to find out if the target system is vulnerable to this exploit as the vulnerability requires specially crafted IPv6 packets.
Example #2: Rootkit for Windows
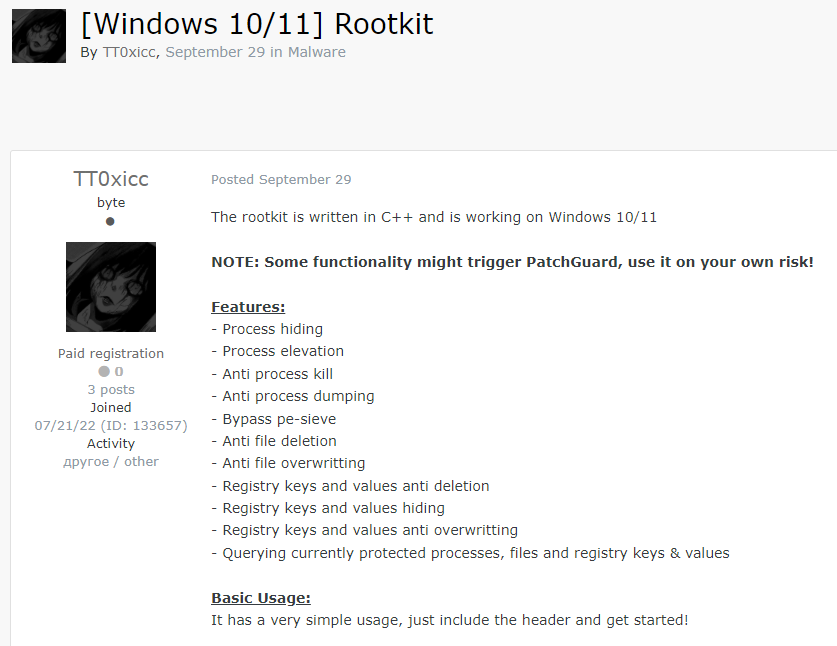
Rootkit is a collection of malicious computer software that is designed to enable remote admin access to the operating system while avoiding detection. This access can enable hackers to conceal malware, gain undetectable remote access to the operating system, and bypass security programs.
In the following example the threat actor posts Rootkit for Windows on Exploit hacking forum. The Rookit offered includes features like “Process hiding”, which hides all windows that belong to the process, and “registry key” which enables hackers to manipulate Windows Registry keys (a database that contains information and settings for hardware, software, users, etc.).
Example #3: A guide for stealing Windows admin passwords
Tutorials and guides are commonly shared on hacking forums.
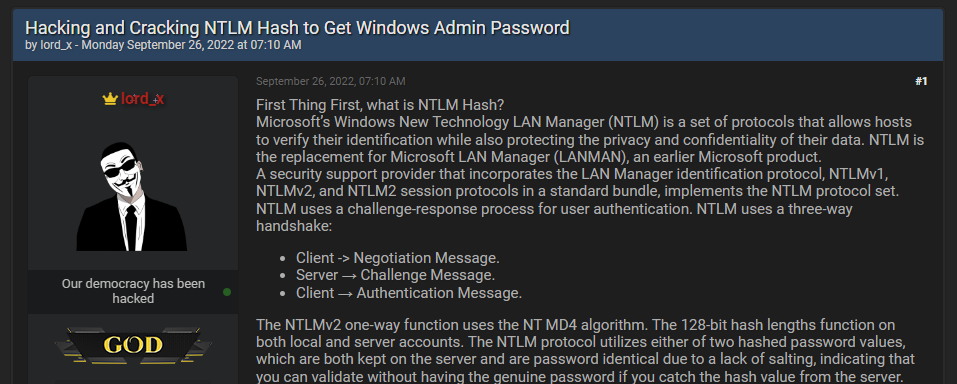
You can see an example of one of these posts in the next picture (see below), where a threat actor is offering a guide on Breached to help other threat actors capture the hash of the admin passwords by using a vulnerability in NTLN (Microsoft’s Windows New Technology LAN Manager, which is a set of protocols that allows hosts to verify their identification while also protecting the privacy and confidentiality of their data).
The exploit actually uses a vulnerability in NTLM protocol by opening a malicious PDF on the victim’s system. Once the victim clicks on the PDF file, the NTLN hash is revealed to the attacker.
To get the actual password out of the hash, a threat actor will need to use another tool such as “John the Ripper” which can extract the real password.
Example #4: A zero-day for sale
The term “Zero-Day” is used when security teams are unaware of their software vulnerability, and they’ve had “0” days to work on a security patch or an update to fix the issue.
A hacker published on Breached forum a Windows zero-day vulnerability (he mentions that it works for all major Windows versions, including the latest updated one), which allows an attacker with local privileges to gain more permissions or obtain access to additional, more sensitive systems. For example, administrative privileges. With these privileges, hackers can steal databases, make significant changes to the system, and cause greater damage. The threat actor is offering it for the fee – of $150K, which indicates that this vulnerability is a serious threat.
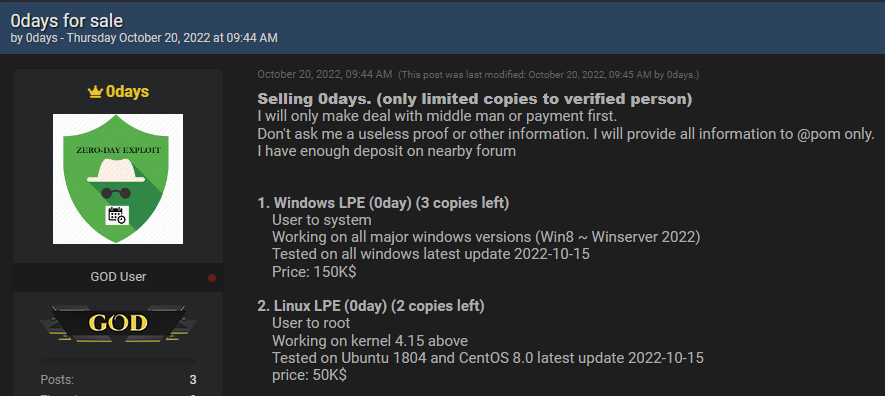
This post presents a medium risk, since there is no direct, proven threat, and the threat actor is still unknown and hasn’t published it in other popular hacking forums.
Brand protection: how monitoring the dark web can help?
Not every mention of a company in a malicious context on the deep and dark web will turn into a high-risk threat that requires immediate action. That’s why it is important to find the relevant data and analyze it to detect real threats that exist in the sea of dark web noise.
Webz.io crawls dark web hacking forums on a daily basis, which provides early indications of possible cyberthreats. We provide cyber risk score grades to posts that are based on the content of the post and where they were published, which gives an early indication of the severity of the threat. This way companies can filter the high-risk posts and address the most dangerous threats in time to prevent or mitigate future attacks.