How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.
This topic was recently the focus of an in-depth webinar hosted by Webz.io. For the complete details, you can watch the recording by clicking here. Below is a summary of the findings presented during the webinar.
Cactus Ransomware is quickly becoming a hot topic in the ICS (industrial control systems) space. The recent Cactus ransomware attack on Schneider Electric underscores the critical vulnerabilities currently present in protection for industrial control systems, especially when it comes to protecting the supply chain. Schneider Electric, a French multinational with $28.5 billion in revenue, was the target of multiple data breaches using Cactus ransomware in 2024. The attacks resulted in the exfiltration of a substantial amount of confidential corporate data, and presented large risk to Schneider Electric.
Because Schneider Electric’s products are widely used across various industries in the ICS space, the breaches are particularly concerning. These systems serve as the foundation for numerous critical operations, ranging from enterprise-level automation to industrial control. Any vulnerabilities in Schneider Electric’s products could pose significant operational and safety risks to Schneider Electric and their customers.
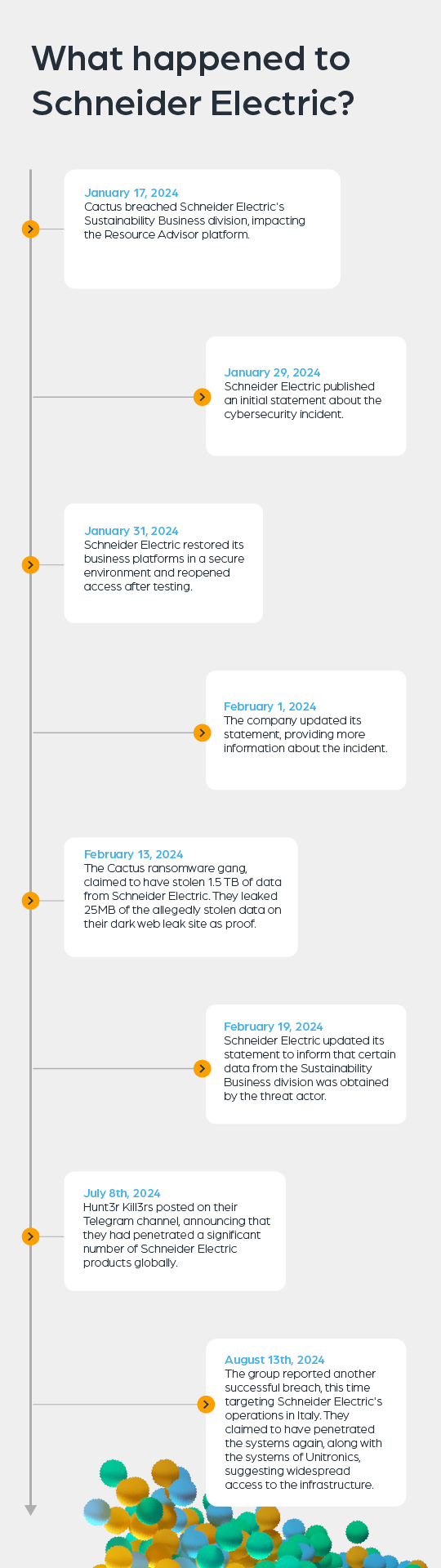
The Cactus ransomware group initiated the first attack against Schneider Electric’s Sustainability Business division. Cactus ransomware stole terabytes of corporate data, impacting key customers, including major brands.
The Cactus group, linked to the Hunt3r Kill3rs Telegram channel, publicly disclosed 1.5TB of stolen data on their ransomware site. This data included accounting records, customer contracts, engineering drawings, snapshots of American citizens’ passports, and other forms of employee PII. Once sensitive corporate and personal information is on the dark web, the company is at risk.
Hunt3r Kill3rs revealed via their Telegram channel that they had infiltrated multiple Schneider Electric products globally. The infiltrated products were specifically the PowerLogic 7650, 8600, and 8650 models—key components of Schneider’s ICS infrastructure.
Cactus ransomware group and Hunt3r Kill3rsclaimed responsibility for another breach. They targeted Schneider Electric’s Italian operations, reporting that Unitronics systems had been compromised. As a result, concerns about the ransomware group’s widespread reach into critical infrastructure were raised even further.
Uncovering attacker sourcing and dark web activity is a critical part of any investigation, for MSSPs (Managed Security Service Providers) and internal cyber teams. This data is often crucial for cooperating with government authorities, cyber insurance companies, and building post-incident reports for presentation to executives. Using Lunar, our dark web monitoring tool, we dove into the Cactus ransomware gang’s activity and were able to find valuable details including the attack’s origins, progress, and even provide critical data points that could help to stop attackers from removing further information if the breach is still active.
Below is the step by step investigation you should take using your dark web monitoring platform to track down key details of the Cactus Ransomware attack. We highly recommend you follow these steps as the data we found contains critical details regarding the ransomware attack, IOCs (indicators of compromise) that signalled future attacks were coming, and how you set up alerts to leverage that data to ensure you stop the attacks in progress for the next time.
Begin your investigation by running a broad discovery query to find any mentions of Schneider Electric across the deep and dark web. This should include variations of the company’s name and domain, such as:
Set your timeframe for at least one year to capture all relevant mentions before, during, and after the Cactus ransomware attack.
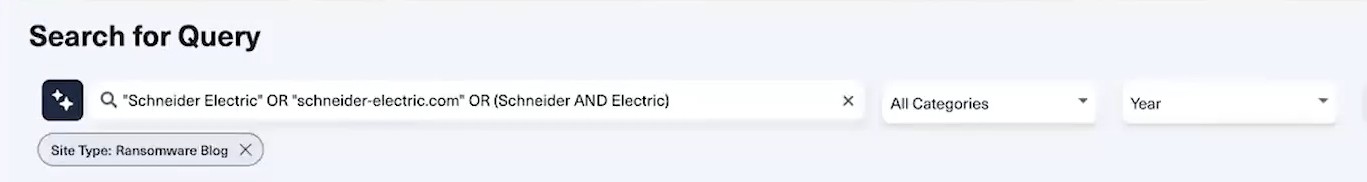
Next, filter the results by “site type” and focus on Ransomware Blogs, which leads you directly to discussions and posts related to the Cactus ransomware group. This allows you to analyze posts across various forums, telegram groups, and other discussions connected to the attacks on Schneider Electric.
To understand how the threat actor initially gained access, remove the “site type” filter and examine the peak in activity before the attack. Narrow down your results further by filtering for Threat Intelligence. The number of results should go from over 2,000 to around 500, making it easier for you to focus on intelligence you can make use of immediately.
Then take a look at your Top Sources Pie Chart so you can see which source is going to be your most active. Russian Market, a known dark web datastore specializing in stolen credentials and stealer logs, emerges as the leading source. This leads you to your next query, a search in the stealer logs repository:
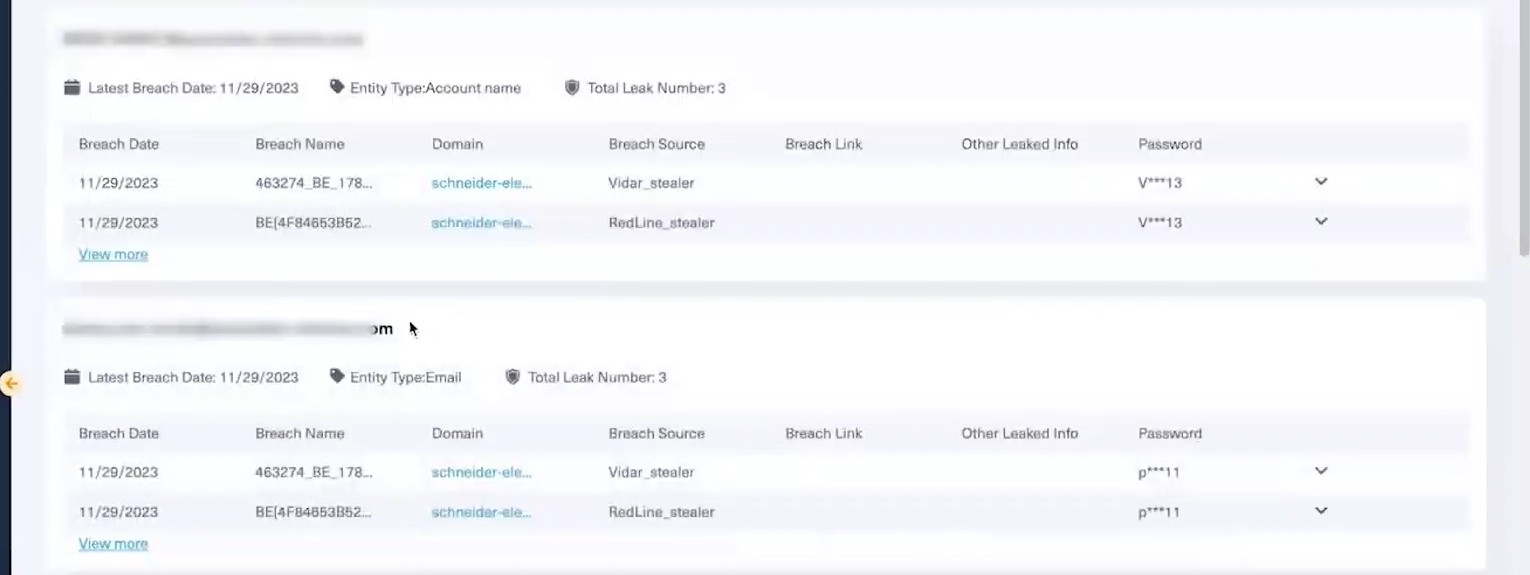
This search yielded a critical result. The credentials of an employee of Schneider Electric had been leaked three separate times about a month before the attack. Investigating this specific entry revealed key details like the user’s credentials, malware path, and hardware ID. Critical information for mitigation as well as uncovering a potential entry mechanism which must be included in your report.
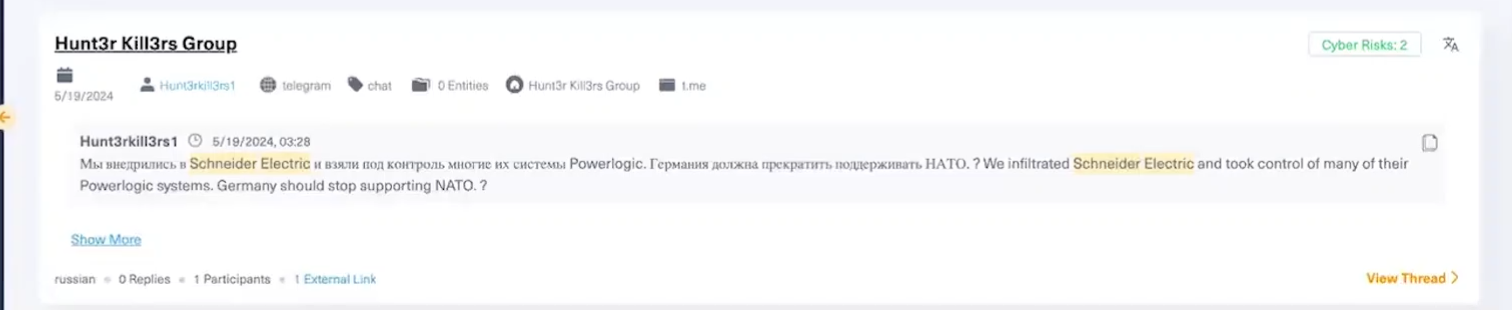
To narrow down the most relevant conversations, search for Schneider Electric within the thread and sort the results by descending date. The second result reveals details about an attack targeting Schneider’s headquarters. Additional posts provided insights into how deep the attackers penetrated into Schneider Electric’s systems. These posts mentioned specific components that were compromised, further mapping the extent of the attack.
Finally, to stay ahead of future threats, create an alert that would notify you whenever Schneider Electric was mentioned again in the Hunt3r Kill3rs Telegram channel. This alert system is crucial for early detection, allowing you to respond more effectively to potential threats before they escalate.
The dark web investigation of Schneider Electric’s ransomware attack underscores the importance of proactive monitoring and swift response. Here’s how you can apply the lessons from this investigation to protect your organization:
The first step in any effective security strategy is to uncover potential threats before they cause significant damage. As demonstrated, a discovery query can help you find leaked credentials, malicious discussions, or indicators of a potential attack. Set up alerts to notify you when similar threats reappear, allowing you to respond in real-time rather than launching an investigation from scratch.
Action Step: Set alerts for mentions of your company on the dark web. This will give you immediate notifications if your credentials or vulnerabilities are exposed.
The second step is to identify the key threat actors or vulnerabilities by diving deeper into the data. By tracking down the individuals or groups behind malicious activity, such as ransomware gangs, you can gain insights into their tactics, techniques, and procedures (TTPs). Investigate their activity across platforms to determine whether they are serious or pose a genuine threat.
Action Step: When you uncover a potential threat, analyze the actor’s profile. Ask yourself key questions: Is the actor real or fake? Are they connected to other threat groups? What vulnerabilities are they discussing? This will help you understand the severity and scope of the threat.
After gathering this intelligence, the final step is to neutralize the threat. Compile your findings into a comprehensive report that outlines the malware path, the threat actor’s identity, and their group’s activity. This report equips your response team with the information they need to swiftly remove malware, patch any compromised systems, and prevent future breaches.
Action Step: Generate actionable reports with all the critical information. Share these reports with your security team to ensure they can address the threat effectively and prevent further data leakage.
This investigation into Schneider Electric’s ransomware attack highlights how critical dark web monitoring is for uncovering early indicators of compromise. By tracking credential leaks, monitoring threat actor chatter, and setting up custom alerts, cybersecurity researchers working for MSSPs can proactively protect their clients from emerging threats.
Learn more about our dark web monitoring tool, Lunar, and how it can enhance your threat detection capabilities.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.