How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Over the past few years we have seen a spike in attacks against governments worldwide as they have become the targets of increasingly sophisticated cybercriminals. These cybercriminals, (some of whom are state sponsored, many of which are not, like Hacktivists) mainly seek to exploit large governmental repositories of sensitive information for financial gain.
In addition, with the rise of cyber warfare like we’ve seen in the Russia-Ukraine cyber war and the ongoing Middle East conflict, politically motivated entities or rival countries are launching attacks against governments to engage in espionage and gain strategic advantage.
Much of the activities and planning before these attacks take place or require resources from the dark web. Due to the anonymity and accessibility of the deep and dark web, these threat actors have found an ideal environment to purchase tools and find forums to openly discuss their activities. Some of what we found in these layers of the web include discussions of threat actors revolving around attack techniques specific to governments, and the trade of sensitive information related to government bodies.
Drill down: how government hospitals can detect emerging cyber threats on the deep and dark web
The behaviors of those who work on the dark web pose significant threats to healthcare institutions, including government hospitals – facilitating illegal activities like the sale of stolen personal health information (PHI), ransomware attacks, and the distribution of malware. Hospitals store vast amounts of sensitive data like patient records, financial information, and research data. This makes them lucrative targets for cybercriminals. Successful cyber attacks on hospitals can disrupt medical services, compromise patient privacy, and lead to severe financial losses or legal consequences.
The situation is urgent. Healthcare is the most frequently-targeted sector in the US, according to the FBI. By way of example, the February 2024 hack of healthcare payments manager Change Healthcare paralyzed swathes of the US healthcare system – from hospitals through pharmacists and physical therapists.
To monitor and detect cyber threats on the dark web, government healthcare bodies can implement several strategies:
By leveraging these methods, hospitals can better protect themselves from the growing cyber risks posed by the dark web.
What are some of the most common types of cyberattacks that governments face today?
Ransomware attacks continue to be a frequent threat to all organizations in general, and to governments in particular. According to a recent White House report, the FBI received 22% more ransomware complaints in 2023 than in 2022, and reported a 74% increase in the cost of ransomware incidents in 2023 relative to the previous year.
By way of example, a large-scale ransomware attack in Germany at the end of 2023 paralyzed services in some 70 German municipalities in multiple districts, while earlier this year US municipalities faced network outages, data breaches and large ransom demands in a spate of ransomware attacks.
This type of attack is particularly popular and widespread among APT groups with a political or social agenda who aim to disrupt and even take down websites maintained by governments. Threats for such attacks can be identified and even managed in real-time (in case of a call to join an orchestrated DDoS attack) on encrypted chat platforms, with Telegram being the most prominent among them.
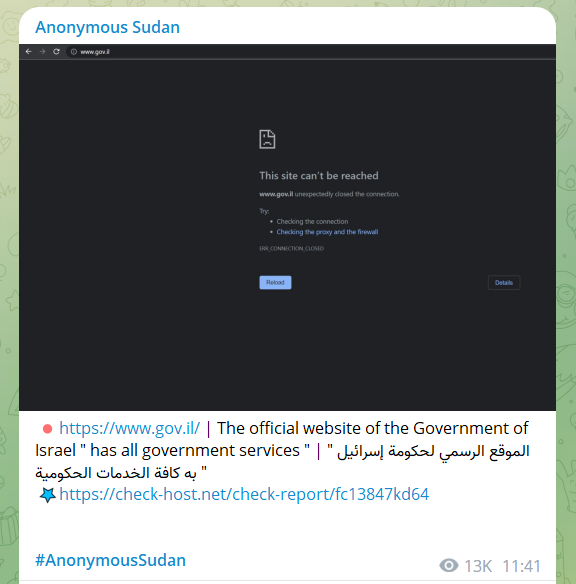
The following image shows a message written by the cybercriminal group Anonymous Sudan on their Telegram channel, where they announce they succeeded in shutting down the official website of the Israeli government by using a DDoS attack:
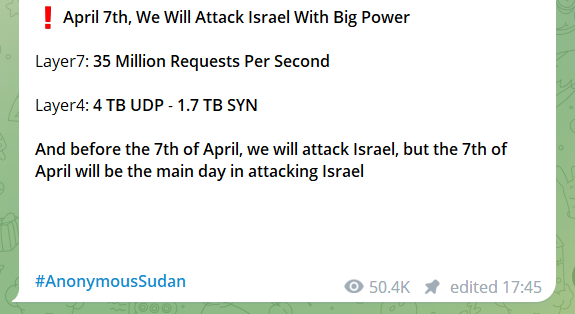
The image below shows another message the group sent, which provides a clear indication that they had planned to launch massive DDoS attacks against Israel, which they later carried out.
Phishing and social engineering attacks are a serious threat to governments. In this type of attack, cybercriminals try to trick employees into divulging sensitive information or downloading malicious software. This can result in massive data loss or financial loss. The relative simplicity of these attacks compared to other methods makes them a popular choice for cybercriminals targeting government employees.
Phishing attacks can target government employees through their emails and their mobile devices. Smishing is a type of phishing attack that uses text messages (SMS) to deceive individuals into clicking on malicious links or providing personal information.
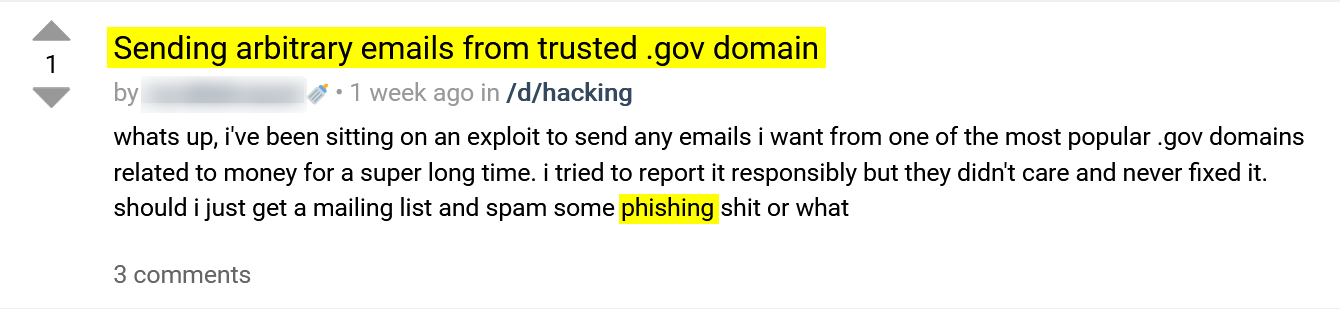
The image below shows a post published on a dark web forum by a threat actor who found an exploit allowing him to send emails from a popular government email domain, which he proposed to use for phishing purposes.
Supply chain attacks against governments involve targeting third-party vendors and suppliers of governmental bodies and agencies to gain access to sensitive government networks or data. These attacks are often harder to detect and can potentially compromise national security or critical infrastructure.
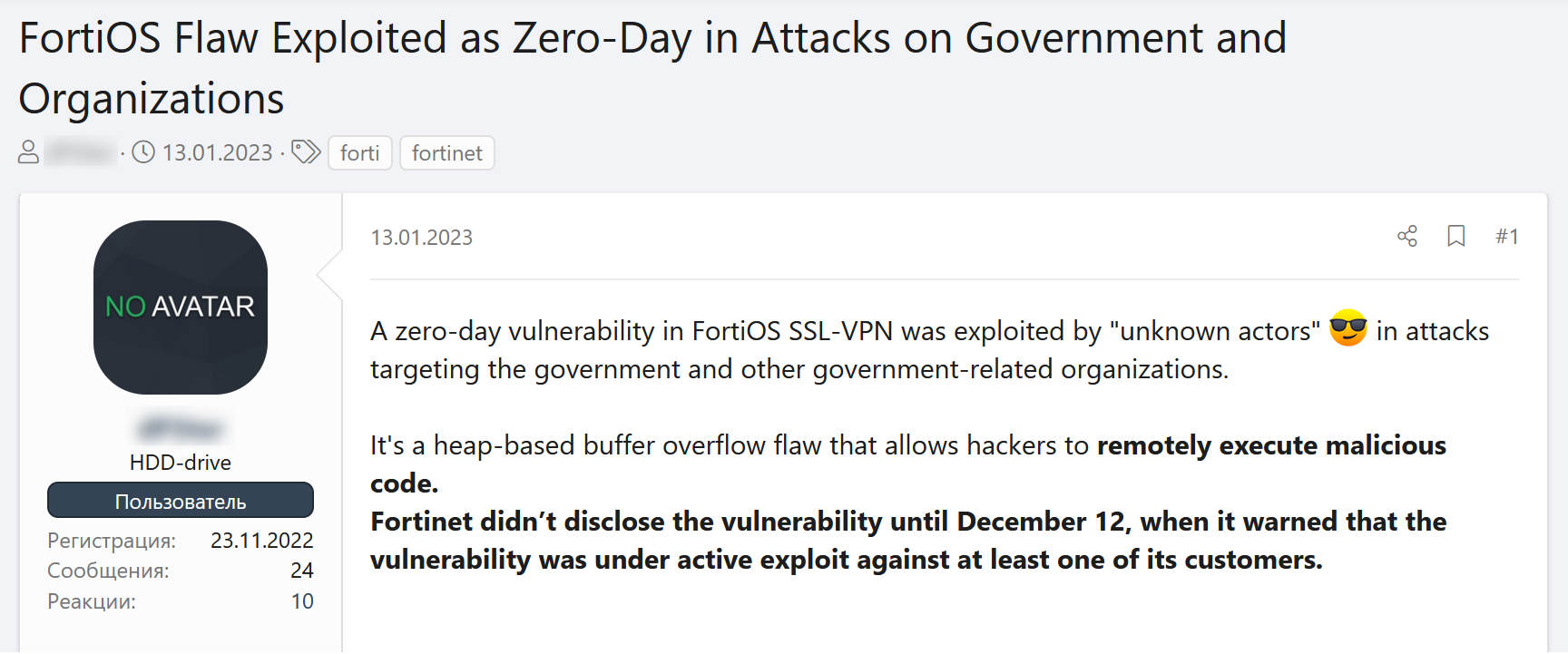
The following thread, which was published on the Russian hacking forum XSS, is discussing a zero-day vulnerability found in FortiOS SSL-VPN, a solution that allows employees to remotely access their organization’s network. In this case, the vulnerability was exploited in order to conduct directed attacks against governments and other government-related organizations.
Insider threats refer to government employees or contractors with lawful access to internal tools, information, or systems within the organization who abuse this access in order to leak or steal sensitive information.
One of the most prominent examples recently refers to an Air National Guardsman who allegedly leaked two sets of classified foreign intelligence documents of the Pentagon by posting them to Discord. Some of the documents were shared on 4chan, Twitter, and Telegram, as can be seen in the following screenshot, taken from the pro-Russian Telegram channel “Donbass Devushka”:

Such an attack can have a severe impact on national security, as it can compromise highly sensitive information and damage public trust in the ability of the government to protect such information.
Mobile devices have become indispensable tools for government employees, but they also introduce new vulnerabilities that can be exploited by cybercriminals. One of the primary threats is mobile malware, which can be installed on devices through malicious apps, phishing attacks, or compromised app stores. Once installed, malware can steal sensitive data, track user activity, or even launch attacks on government networks.
Another significant vulnerability is the use of unsecured Wi-Fi networks by government employees. Public Wi-Fi networks are often poorly protected, making it easy for attackers to intercept data transmitted over them. This is particularly dangerous for government employees who access sensitive information or government systems while connected to public Wi-Fi.
To mitigate the risk of mobile malware and insecure Wi-Fi connections, governments should implement strong mobile device management policies, educate employees about mobile security best practices, and provide strict cybersecurity policies.Such policies should include the following measures:
The top dark web sources for early cyber threat indicators against governments
Using Lunar, our dark web monitoring platform, Webz examined posts on deep and dark web forums that indicated a potential threat to cyber security on public sector targets. We evaluated the volume of indicators and classified them according to their respective sources. As the chart below reflects, we found that deep and dark web forums account for the majority of indicators with 65% of the total number of indicators, with over a million potential cyber threats to governments. This number includes underground forums and imageboards.
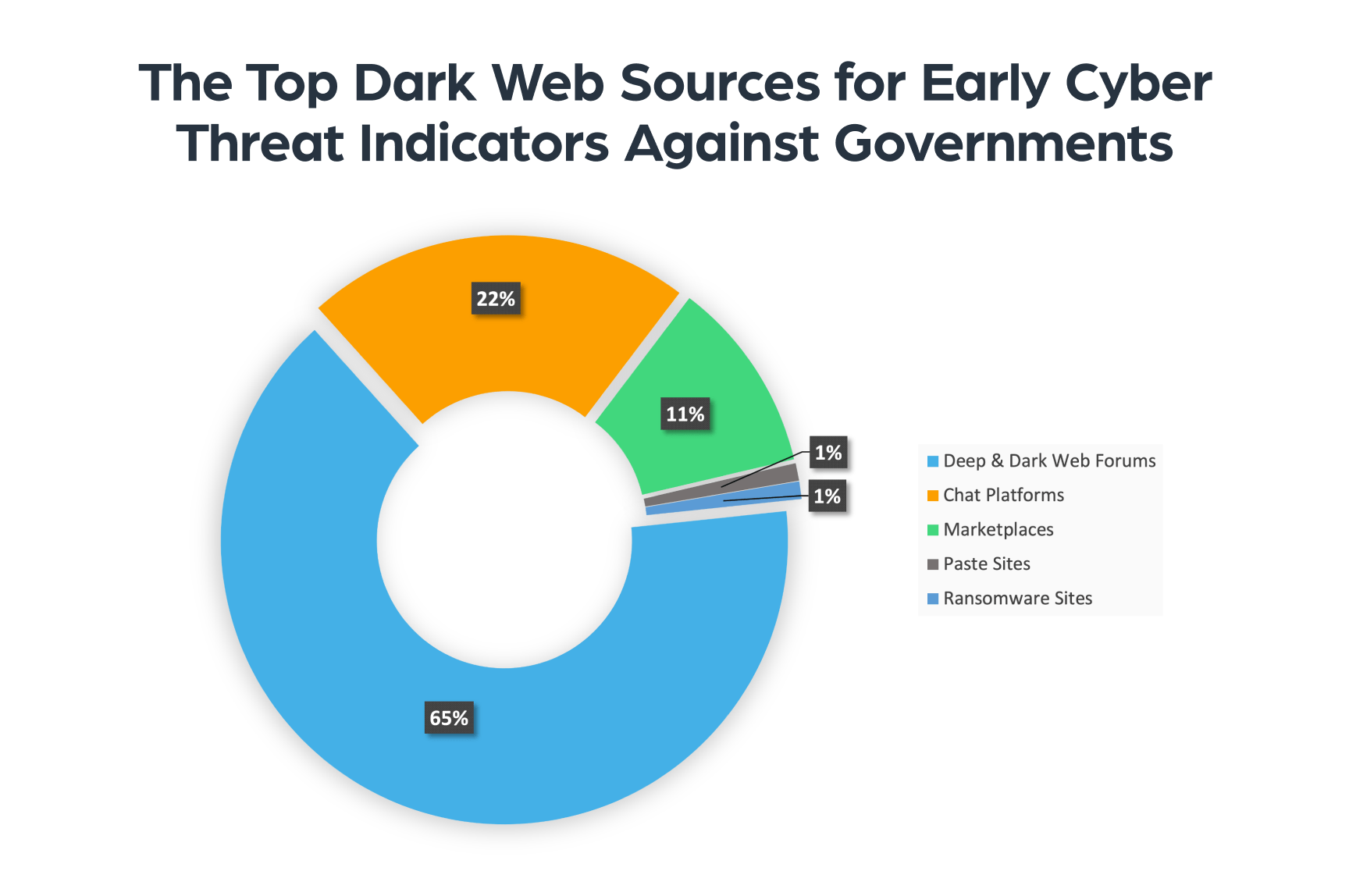
In the second place we see chat platforms. Chat platforms are considered a breeding ground for radical groups or cybercriminals planning attacks against governments. In the third place, we have marketplaces that are used to trade sensitive information that can be used to exploit governments. Lastly, we have paste sites and ransomware sites which mainly expose the victims of the attacks that were launched against governmental bodies.
How can deep and dark web monitoring help governments stay safe?
Governments today face various cybersecurity threats on a daily basis. A single attack against a governmental system can lead to serious damage, including data loss, mega leaks, monetary loss, and dramatic effects on the operation of governmental systems and activities. Tracking governmental entities, such as domains and IPs, in the hidden corners of the web can serve as key indicators for emerging government cyberattacks. By monitoring the deep and dark web, governments can identify potential threats and take proactive measures to prevent and mitigate cyberattacks.
Ready to take proactive steps to secure your government’s digital assets? Learn more about Lunar’s dark web monitoring services.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.