Revealed: Emerging Ransomware Group, Leaked AWS Accounts, & Secret Log4j Discussions

We are excited to return with the first edition of the Dark Web Pulse for 2022. A quick reminder for those who have missed the last edition, this is our cyber team’s revamped newsletter, bringing you our latest findings from the darkest corners of the darknets.
Now let’s dive in.
Popular ToRReZ Market is Officially Retiring

ToRReZ Market, which launched in September 2020 as a “community-driven market,” recently announced their retirement, shortly after other known marketplaces, the White House Market and Cannazon, revealed they were closing.
According to the official announcement, all transactions and disputes have been resolved by the owners before they shut down.
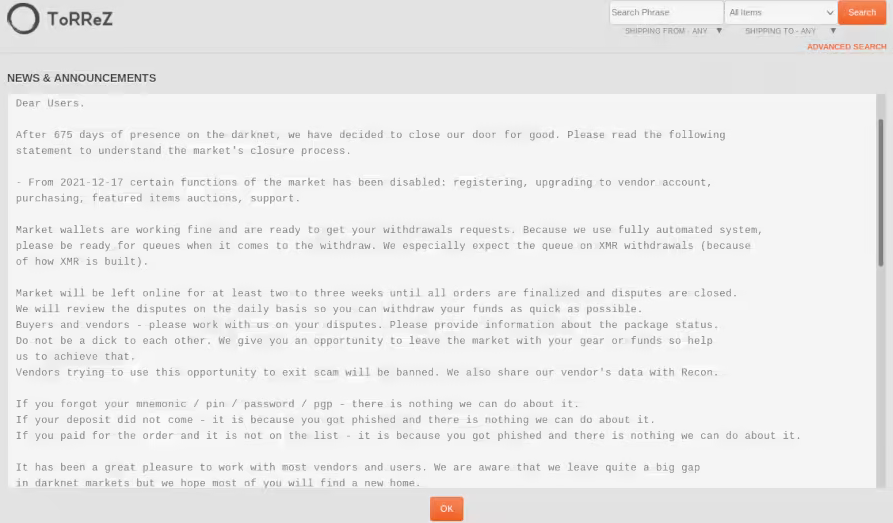
Mr_blonde, the ToRReZ administrator, made their first announcement on ToRRez in mid-December:
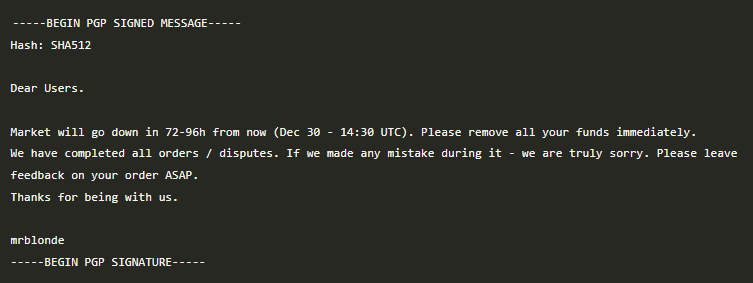
Later, in late December, he posted the following message on Dread:
In his first message, Mr_blonde warned against using established marketplaces, saying that markets grow closer to collapse as they age: “I would personally avoid any “established” market as older they get, bigger chance of collapsing is. Please give a chance to the smaller markets, which are not that loud as others. This is exactly how we became no 1 – being quiet and doing our job, serving customers 24/7 for 675 f***ing days.”
Traditionally, retiring markets have advised users to migrate to certain “friendly” markets or equally well-established markets. In the past, “Mr. White”, the administrator of White House Market, encouraged users to move to Monopoly Market or Versus Market when they announced they were shutting down.
In the last couple of paragraphs of Mr_blonde’s message, he hints at the possibility of making a return in the future: “While ToRReZ will be gone for good, we might (or not) come back at some stage with something different. The whole world goes green. Maybe we will join the trend at some stage ;] When we decide to be back, we will definitely sign the message with one of the known keys so watch out for any copycats. If you have anything to say to me, you can use Dread’s system but I give no warranty that any of your messages will be read, not to mention that they will not get answered.”
Although the site is down, Webz.io keeps history of ToRRez’s crawled posts, making it available in our systems.
To see content from ToRRez, use the following query:
site.domain:iwkwcpzxxynlz2hmhdiwrtcseh7aqhmd27nhriqwowe6sbdee4feiwqd.onion
Behind the News: Criminal Discussions on Log4j Vulnerabilities

Recently, the global media has been covering the implications of critical Log4j vulnerabilities extensively. The Log4j, an open source software provided by the Apache Software Foundation, records errors and routine system operations and communicates diagnostic messages about them to users and system administrators
This software has been used by many organizations over the years, including: Amazon, Apple, iCloud and others. The vulnerability includes a code injection through user configuration settings that can create a reverse shell out of the target server or control the target in other ways.
We decided to have a closer look at these vulnerabilities in the dark web.
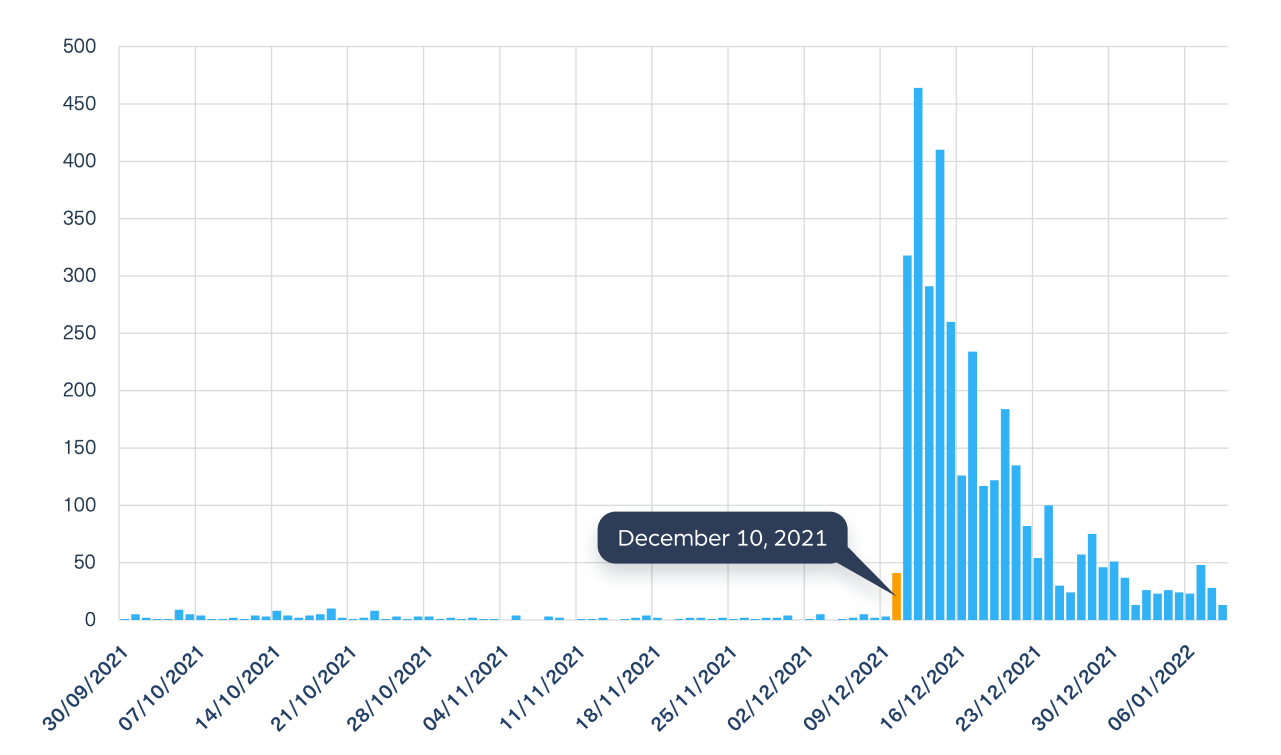
While the vulnerability was first recorded as a CVE on November 26, 2021, the first real Zero-Level alert was applied only on December 10, 2021.
Using our dark web data, we tracked high activity around the same time. We were able to find discussions between threat actors over the Log4j exploits in technical groups on Telegram and on 4Chan on the very same day, on December 10 (see the graph below) .
We also took an even closer look and sorted these discussions on the Log4j vulnerability on the dark web according to CVE names:
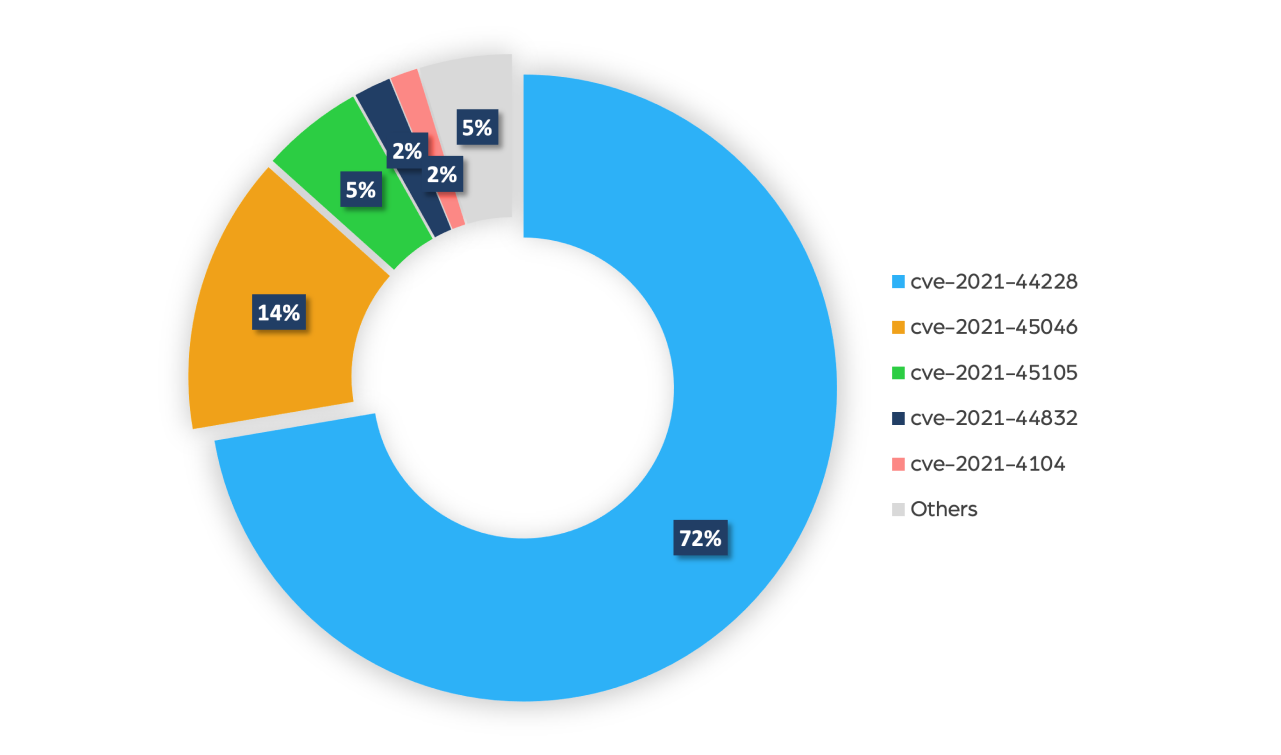
By looking at the pie chart above, we can clearly see that the vast majority of the discussions circle around the latest, high risk CVE-2021-44228, a critical configuration vulnerability. About 14% of them were about CVE-2021-45046, which is an incomplete fix to the CVE-2021-44228.
This high level of activity is a clear indication that servers around the world are at high risk, forcing many to take immediate action and run updates using the latest patches to mitigate this risk.
This type of data helps MSSPs and threat intelligence systems create alerts and notify their customers by identifying immediate risks that are used by criminals on the dark web.
2022: A Surprising New Ransomware Group is Starting Strong

Another ransomware group has recently launched into operations in such a way that signals that 2022 is likely to set a new record of ransomware activity. The new group, Night Sky, started advertising its activities on December 27. Within the short time since, it has already hit two companies from Japan and Bangladesh, encrypting their data using double-extortion attack techniques. Using this method, also known as pay-now-or-get-breached, ransomware groups first exfiltrate information, then encrypt them, and finally, threaten to publish the data unless a ransom is paid.
The Night Sky group maintains a website that runs on the encrypted TOR network, where it announces the companies they attack. A notice on their behalf was published on the site threatening to release all files for free should the companies fail to pay the ransom.

Until now, the data of the two companies has not been released except for a few samples of the stolen data, including sensitive documents that prove the group’s involvement in the leaks.
One of the more interesting findings our team found is that while other ransomware groups use an internal message box, Night Sky communicates with the victims through private emails and through an open web site called “Rocket Chat” that offers encrypted chat rooms (which at some point suspended their account). As far as we know, this is the first ransomware group that used Rocket Chat to communicate with its victims. This is surprising as the Rocket Chat platform is mostly known to be used by radical Islamic groups.
To see content from Night Sky, use the following query:
site.domain:gg5ryfgogainisskdvh4y373ap3b2mxafcibeh2lvq5x7fx76ygcosad.onion
Revealed: Compromised AWS Accounts Ahead of FlexBooker Leak

FlexBooker, the cloud-based booking and scheduling software, recently suffered a data breach. Using our Cyber API, we were able to find the first post relating to the leak on the popular hacking forum “Exploit”, a famous Russian forum on the TOR network. The post was published by “Uawrong”, a new emerging hacking team responsible for several recent leaks such as Racing.com and rediCASE Case Management Software, from the Redbourne Group which supports public health networks across Australia, resulting in a leak of patient data.
Webz.io detected the leak soon after it was published, which is now available through our Data Breach Detection API. The leak includes information belonging to 3.7 million Flexbooker customers. The compromised information includes names, phone numbers, email addresses, passwords, and in some cases, partial credit card information.
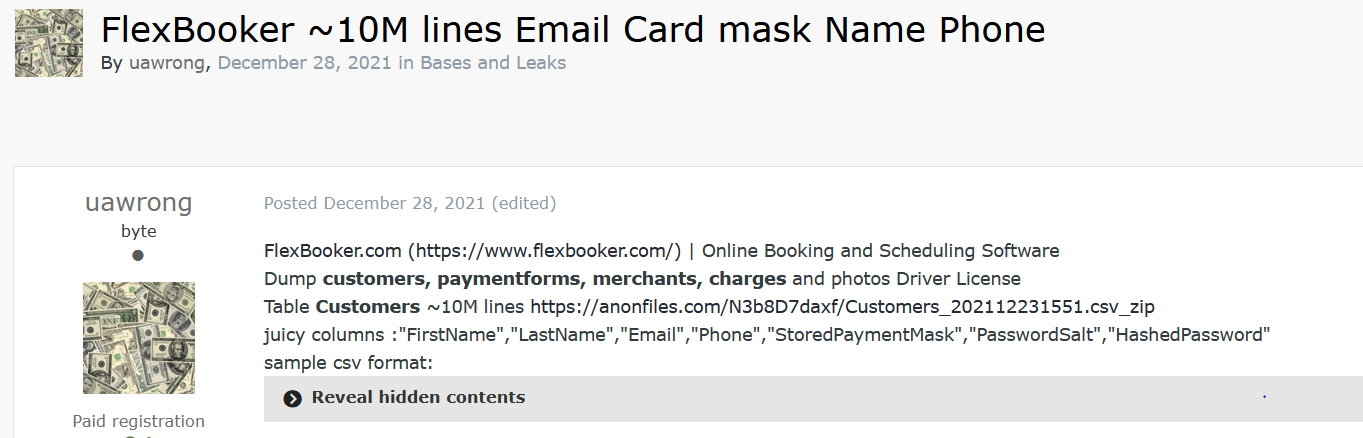
According to an official announcement Flexbooker released, the leak was caused due to a compromised account: “On December 23, 2021, starting at 4:05 PM EST our account on Amazon’s AWS servers was compromised, resulting in our temporary inability to service customer accounts, and preventing customers from accessing their data”.
This is not the first time we see how one compromised account can lead to serious breaches, including the hacking into Colonial Pipeline, the largest fuel pipeline in the U.S., and other risks to companies. Unwanted access in the form of compromised accounts is one of the most accessible options on the dark web. Hacked accounts that are leaked or traded can be found in vast amounts in “data stores”, marketplaces for stolen data (login credentials, cookies, PIIs, etc.), and data breaches that are published on a daily basis in hackers forums, marketplaces and chatting applications such as Telegram.
A quick search of leaked or traded AWS accounts in our API yields over 4,000 results from the past two years. One of them could be the Flexbooker account. Tracking these compromised accounts can help prevent the next AWS leak.
This is it from us on this first edition for 2022. We’ll return in two weeks with new exclusive insights from the dark web. Until then, don’t forget to share your own findings, insights or just let us know what you think about our renewed newsletter by reaching out to us at: [email protected].
Until next time,
Team Webz.io





