How Proactive Brand Monitoring Can Flag Suspicious Mentions — Before Disaster Strikes
Key Facts:
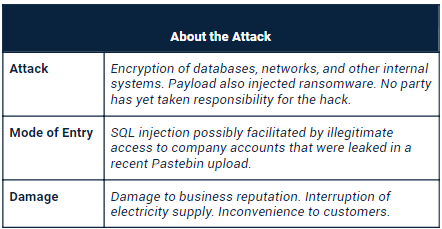
- City Power, the utility provider responsible for providing Johannesburg, South Africa with electricity, recently suffered a devastating ransomware attack.
- The attack prevented customers from being able to view or pay electricity bills online.
- This resulted in some customers — particularly those that pre-pay for electricity, as well as those that relied on using the app to upload purchased electricity to their smart meters — being left without power.
- The virus’ payload was unleashed on the company’s internal systems on Thursday morning (25/07/19) and more than a quarter of a million customers were affected by the breach.
- According to a spokesperson for City Power, no customer details were compromised.
- Although the first services to be affected by the virus have already been restored and secured, the company has said that it could “take weeks” to undertake a complete scan of the affected networks and systems in order to patch any remaining vulnerabilities and ensure that no backdoors remain open.
Summary:
In recent days, City Power, the electricity provider to the city of Johannesburg in South Africa, suffered a ransomware attack which resulted in its databases and networks being encrypted. A quarter of a million customers were affected. Many, particularly those that pre-pay for their power supply, were left without electricity.
Unlike the municipalities of Riviera Beach and Lake City in Florida, US, which last month decided to pay the attackers ransoms in order to recover data about their residents, the Johannesburg city government, which wholly owns City Power, is planning on resolving the breach entirely through its own efforts.
Commentary:
Could a Hacker’s Paradise have been City Power’s Undoing?
In general, cyber hacks such as that which struck City Power are preceded by a period of network mapping and intelligence gathering during which would-be hackers probe their target’s technical infrastructure for vulnerabilities to exploit.
Forewarnings — including the sharing of details about servers and proprietary systems — can surface on both the clear and dark webs many months before an actual attack. Real-time monitoring of both these domains can provide cyber-defence teams with invaluable information that could help thwart an attack.
Subscribers to Webz.io’s Data Breach Detection (DBD) API, for example, receive real-time information about exploited user credentials to help expedite damage containment and system repairs.
In other instances, the Cyber API can help detect information shared on the websites, hidden communities, and messaging applications that are beyond the reach of conventional internet indexing tools, such as search engine bots that probe and catalogue the open web. These websites on the dark web frequently host illicit and hacking-related information. Personally identifiable information or system vulnerabilities documented and shared over one of these fora is a red flag for technical teams. Once seen, these must work to identify the malicious plotters and take steps to prevent them from accessing their systems. But receiving these in a timely manner is easier said than done.
If City Power were subscribing to a data feed that monitored for brand mentions on these networks in real time, could it have received clues that may have helped prevent the breach? Our cyber analysts looked through company data to try and find the answer.
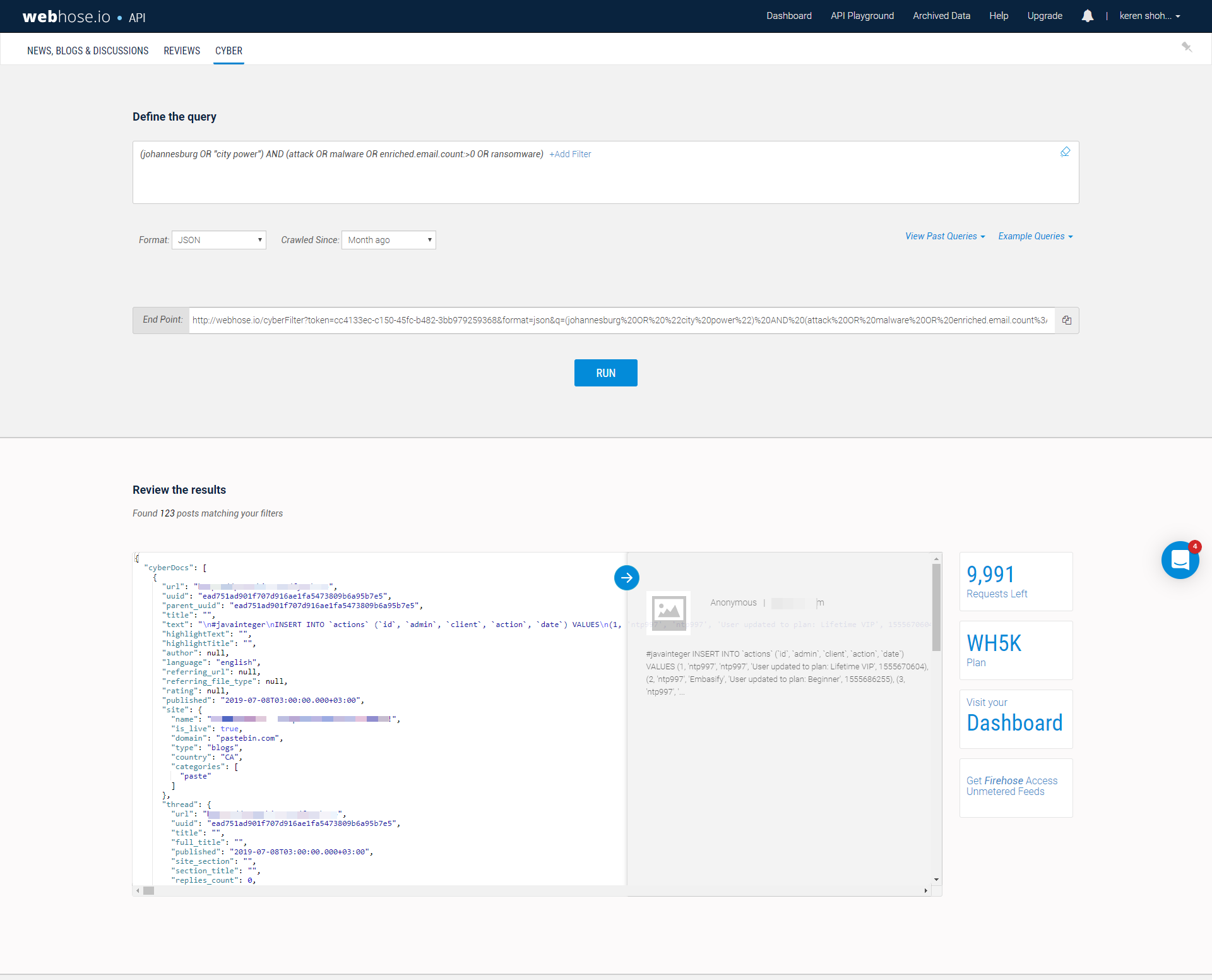
By accessing Webz.io’s historic data, we were about to search for keyword matches for “City Power” on all of our data streams. When we did, we discovered several noteworthy matches from a variety of sources.
A couple of these are below, taken from a website called PasteBin.com that allows users to leave anonymous text pastes for other users to inspect .
“Pastes” are frequently uploaded to PasteBin by hackers with malicious or sensitive information about an organization. In doing so, hackers take advantage of the fact that text can be uploaded without registering with the service or providing any personally identifiable information (PII), making ascertaining their identity virtually impossible — particularly if they access the website via its dark web mirror or over a VPN (in which case even their IP address is not exposed).
Well-known malicious pastes have included the Lulzsec hacktivism collective’s posting for public scrutiny of more than 70,000 records, including names, telephone numbers, and email addresses, of contestants that took part in the popular X Factor television show. As may well have been the case with the City Power breach, that paste was made possible due to the insecure SQL databases that Fox — the show’s owner — then operated.
While leaks such as the X Factor one may seem impressive, they are often quickly moderated — or deleted by the owners themselves after they have been seen by a collaborator. Time, however, is of the essence, and businesses that want to protect their reputation need to act quickly or immediately to contain the damage and stop the spread of leaked information. Collaborating over dark web channels such as Telegram or IRC, hackers could arrange to exchange a malicious SQL injection query in mere seconds. Only real-time monitoring of brand mentions that straddles the clear, deep, and dark webs — and outputs its results in machine-readable format — stands a chance of thwarting such activity.
Webz.io can provide these data feeds and also offers two years of trailing data on its Cyber API which monitors the dark web. This enables algorithms and software to detect and flag what human brand monitoring teams might miss. Coverage of the open and dark webs means that brands are less likely to miss a crucial signal that could indicate an imminent attack is already in the works.
Querying The Webz.io API for Suspicious Brand Mentions
Let’s return to the PasteBin mentions that our systems captured and imagine that we were tasked with helping defend City Power’s infrastructure from potential attackers.
As part of that effort, we would need to run some API queries that could feed our analysis tools with any potentially suspicious mentions of our brand. If we see these, we can immediately alert out cybersecurity team that it might be time to harden our defences ahead of an anticipated attack. If a specific IP address is mentioned, for example, we can tweak our firewall settings to disable incoming connections from certain ports.
What queries might supply the requisite data?
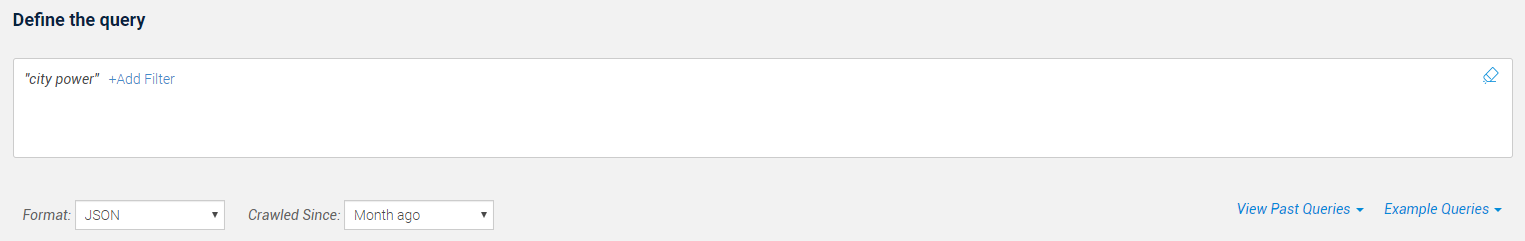
If we start with a simple text string query for “city power”, for example, we can obtain all matches for “City Power” on both the clear and dark web irrespective of where they came from. Naturally, this will include false positives such as news mentions as well as other innocuous activity that isn’t of interest to us, but on the positive side, it will cast a wide net.
When widening the search, however, things get more interesting.
It appears to be an advanced query to facilitate an SQL injection. Evidently (potentially as a result of the previous leak), the would-be hackers have done some preliminary network mapping and identified some public IP addresses belonging to the utility company that they plan on targeting in the injection.
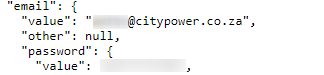
Beyond retrieving simple text strings, Webz.io’s Natural Language Processing (NLP) technology is also able to identify discrete entities such as email addresses and users can run wildcard queries that return any times an email address was posted alongside a mention of “City Power”.
Of course, any chase for signs of collaboration among malicious actors should also include the dark web. And if we were monitoring for suspicious mentions on behalf of City Power, we would certainly want to also poll for results from the Webz.io Data Breach Detection (DBD) API.
Data Breach Attacks on Electricity Providers Are A Growing Threat
It’s safe to assume that the attack on City Power will not be the last time that ransomware attackers target an electricity provider where they can leverage the enormous bargaining power of an interrupted electricity supply to pressure the provider — or the local government — into paying the ransom.
A recent report by top US intelligence officials concluded that hacking the electrical grid is one of the most significant threats facing national security. Triton, an infamous Russian hacking collective, has already begun probing key junctures of the US power network potentially as part of a future plan to unleash its signature Xenotime malware on the network. This is precisely the kind of advanced network mapping and surveillance that, on a different level, companies want to prevent.
And the results of such mapping are self-evident. Earlier this year, the US power grid suffered its first confirmed successful cyberattack on its power infrastructure resulting in a temporary and partial loss of visibility into certain parts of the Supervisory Control and Data Acquisition (SCADA) systems at plants in Utah, Wyoming, and California. Other attacks are almost certainly being actively prepared.
Stay on Top of Threats by Proactive Brand Monitoring
As an external organization, we can’t know what cyberdefences those responsible for securing City Power’s technical infrastructure had in place at the time of the attack.
However, we do know that if they had been using the Webz.io Dark Web Monitoring API to monitor for brand mentions on the open and dark web that their team would have noticed a number of red flags including a PasteBin.com dump (since deleted) that provided an SQL injection query that may have formed an integral part of the attackers’ payload.
Critical infrastructure segments, particularly the power generation and supply sector, are almost certain to remain highly lucrative targets for both financially-motivated ransomware hackers and state actors seeking to gain leverage over foreign governments.
In light of this threat, organizations should arm themselves with as much information as possible that could forewarn about malicious activity — including suspicious brand mentions on the open and dark webs.
Speak to one of Webz.io’s experts today to learn about how your organization can spot suspicious mentions and protect your online infrastructure.