Decoding Cyber Warfare with Deep and Dark Web Intelligence

What is cyber warfare?
Cyber warfare is a highly debated and complex topic with no universally agreed-upon definition. While many scholars, militaries, and governments typically define cyber warfare in terms of state and state-sponsored actors, others expand the definition to include non-state actors like terrorist groups, political or ideological extremist groups (AKA hacktivists), and transnational criminal organizations. In this discussion, we adopt a broader perspective, viewing cyber warfare as a cyber-attack or series of attacks targeting a country. These attacks can disrupt both governmental and civilian infrastructures, potentially causing significant damage and even loss of life.
Who is behind cyber warfare?
The domain of cyber warfare involves a variety of actors with different motivations and capabilities.
- State and state-sponsored actors: Governments engage in cyber warfare to achieve national objectives, such as propaganda, sabotage, or election interference. State-sponsored groups, endowed with significant resources and advanced capabilities, are highly effective and often hard to detect.
- Non-state actors: This diverse group encompasses terrorist organizations, political or ideological extremist groups (commonly referred to as ‘hacktivists’), and transnational criminal organizations. These actors utilize cyber warfare to spread fear, influence public opinion, or achieve financial gain.
What are the different types of cyber warfare?
We will examine the timeline of cyber attacks starting with the Hamas attack on October 7th, 2023 to illustrate various types of cyber warfare. We have identified hundreds of cyber-attacks executed by dozens of different threat actors since the attack. Using Lunar, our dark web monitoring tool, we investigated these attacks to see how deep and dark web data can influence threat prediction. This case study not only highlights the diversity of cyber warfare tactics but also provides valuable insights into the types of data we can expect to find in such conflicts.
Timeline of attacks
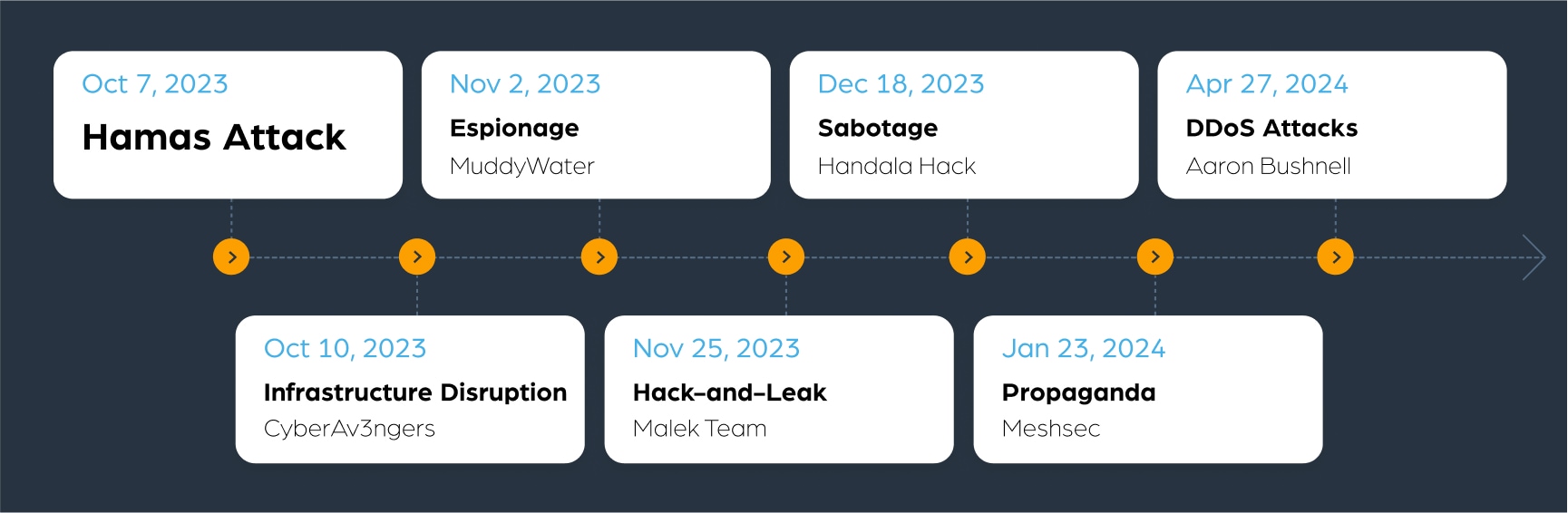
Infrastructure disruption (October 10th, 2023)

- Targets critical infrastructure systems such as power grids, water supplies, and communication networks. The primary objectives are to disrupt essential services, cause widespread chaos, and paralyze societal functions.
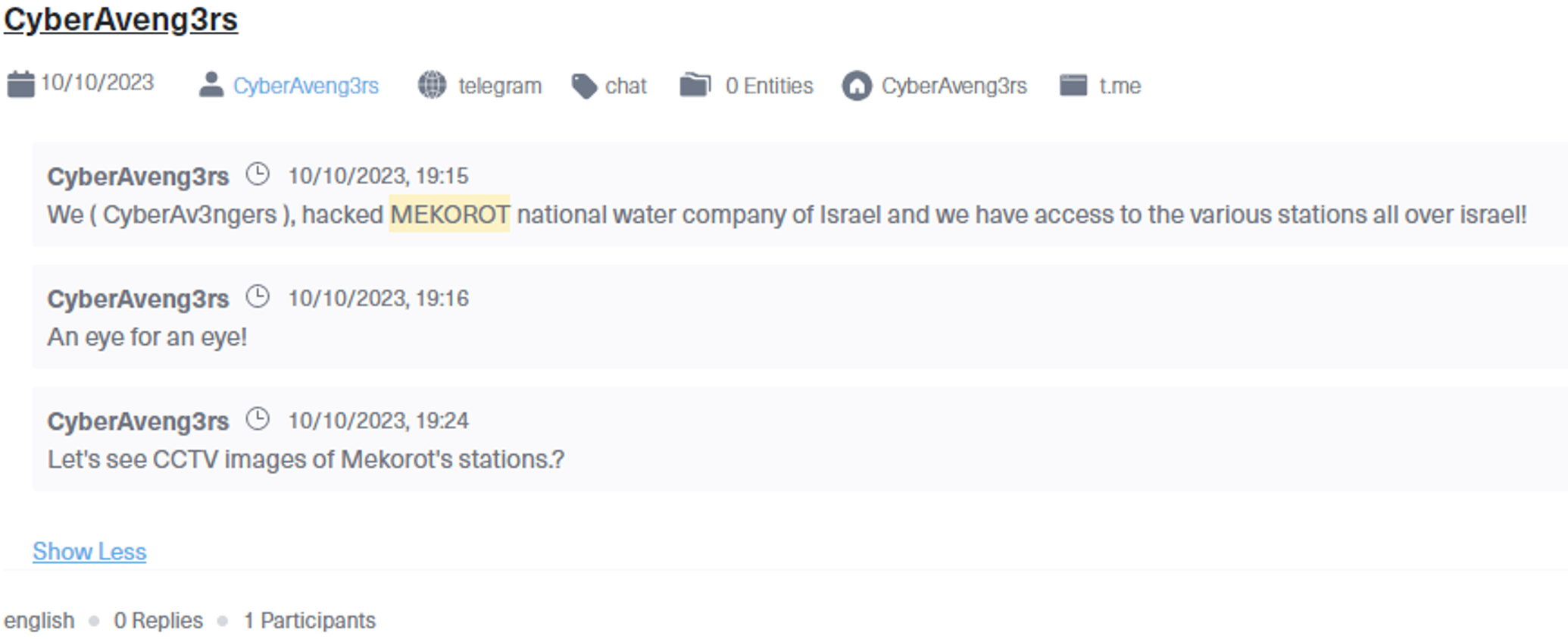
- Example: On October 10th, 2023, three days after the Hamas attack, a hacktivist group named CyberAv3ngers, associated with Iran, claimed responsibility for hacking into the stations of MEKOROT, the Israeli national water company. This attack exemplifies how infrastructure disruption can be used to destabilize and inflict damage on a nation’s critical systems.
Espionage (Nov 2, 2023)

- Espionage in cyber warfare involves penetrating digital networks to access sensitive, classified information such as government data, military plans, or intellectual property.
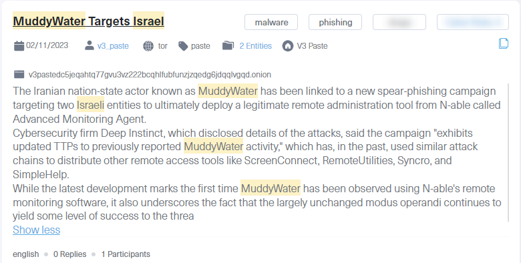
- Example: Around November 2nd, 2023, the Iranian APT group MuddyWater executed a spear phishing campaign targeting Israeli entities. The attack began with emails that appeared to be official communications, tricking victims into downloading attachments. These attachments contained a multi-stage infection vector that led to the installation of a legitimate remote administration tool, allowing MuddyWater to access the victims’ sensitive data.
Hack-and-leak (Nov 25, 2023)

- Hack-and-leak operations involve breaching digital systems to steal sensitive information and then publishing it for public consumption.
- Example: On November 25th, 2023, the Iranian-associated Malek Team conducted a hack-and-leak operation, claiming to have accessed over three hundred thousand medical records from patients at ZIV Medical Center in northern Israel. They published samples of these records on their website.
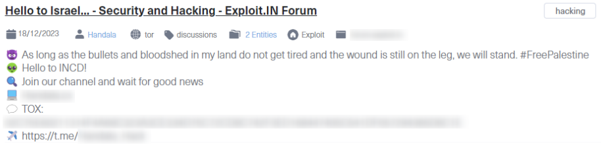
Sabotage (Dec 18, 2023)

- Sabotage in cyber warfare involves intentionally damaging or destroying digital systems and data to disrupt operations and cause harm.
- Example: In December 2023, the hacktivist group Handala executed a sabotage campaign targeting governmental and financial institutions in Israel. They sent phishing emails pretending to be from a security firm, tricking recipients into downloading malware named COOLWIPE and CHILLWIPE, disguised as a security update. This wiper malware damaged files by overwriting and deleting them, severely disrupting the targeted institutions.
Propaganda (Jan 23, 2024)

- Propaganda campaigns in cyber warfare involve spreading disinformation or biased information to influence public opinion in a certain way.
- Example: On January 23rd, 2024, the Turkish hacktivist group Meshsec conducted a propaganda campaign by hacking into the screens of an Israeli cinema chain. They displayed gory images from the Hamas massacre along with hateful and threatening messages to manipulate public sentiment and spread fear.
DDoS (Distributed Denial of Service) attack (Apr 27, 2024)

- DDoS (Distributed Denial of Service) attacks overwhelm servers and networks with a flood of traffic in order to block access and take services offline.
- Example: On April 27th, the hacktivism group Aaron Bushnell conducted a DDoS attack that blocked access to the website of Tel Aviv University.
How can dark web monitoring tools help safeguard against cyber warfare?
Step 1: Uncover
In the first step, Uncover, we use dark web monitoring tools to discover emerging threat actors in real time.
Set alerts to notify us when an invite link for a new Telegram group appears. Upon notification, we review and access the new threat actor’s group, such as the Hunter Killers. If the new source matches our use case, we add it to our coverage for continuous monitoring. This cycle repeats as we set alerts for new channels and use their data to find additional emerging threat actors.
Step 2: Identify
The second step, Identify, involved using dark web monitoring tools to profile threat actors associated with suspicious activities. For example, using Lunar, we sought to profile the hacktivist group Handala Hack, known for sabotage, hack-and-leak, and propaganda activities. While their affiliations are unclear, actor profiling helps our analysts find more ways to identify potential threat actors.
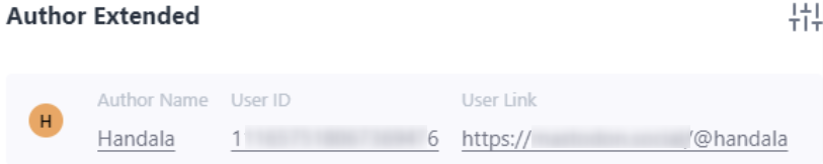
- Using Lunar, we discovered different authors in illicit forums using Handala as part of their username. Investigating these users further allowed us to identify more group members. For example, we found a user associated with Handala, his user ID, guiding us to investigate more posts by this user.
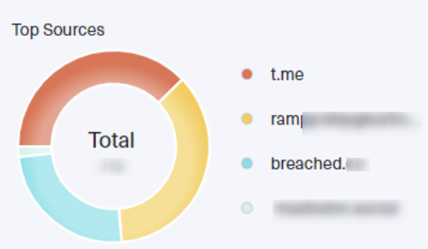
- By investigating multiple usernames linked to Handala, we generated a pie chart that shows the sites on which the group is most active, where they might publish or sell data breaches, etc.
Additionally, we identified domains mentioned in their posts providing insights into potential targets.
Step 3: Take Action
The final step, Take Action, demonstrates how brand and organization monitoring on the dark web can be vital for detecting Indicators of Compromise (IOCs) and mitigating events. For example, we conducted a brand monitoring investigation for several Israeli companies and organizations, setting alerts for any mentions on the deep and dark web. In the following screenshot, we see that an alert was set for the domain of a specific Israeli company, which notified us whenever an employee’s credentials were leaked.
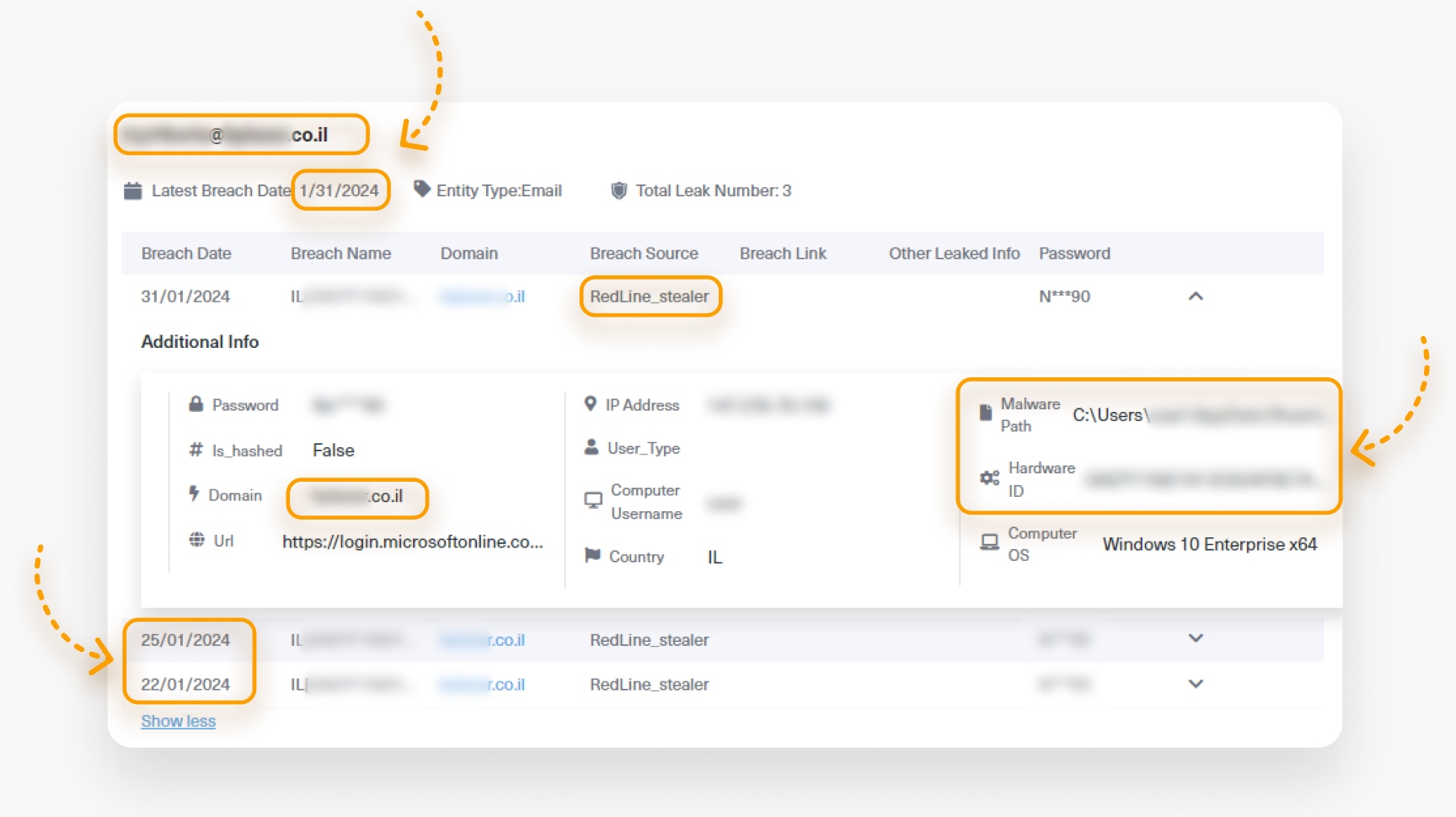
By the end of January 2024, an employee’s computer at this company was infected with the Redline info stealer malware, leading to leaked credentials, including sensitive user passwords. The data continued to leak every two days because the infection went undetected. The following screenshot shows the leak indication found using Lunar, along with the malware path and hardware ID, which are crucial for mitigation.
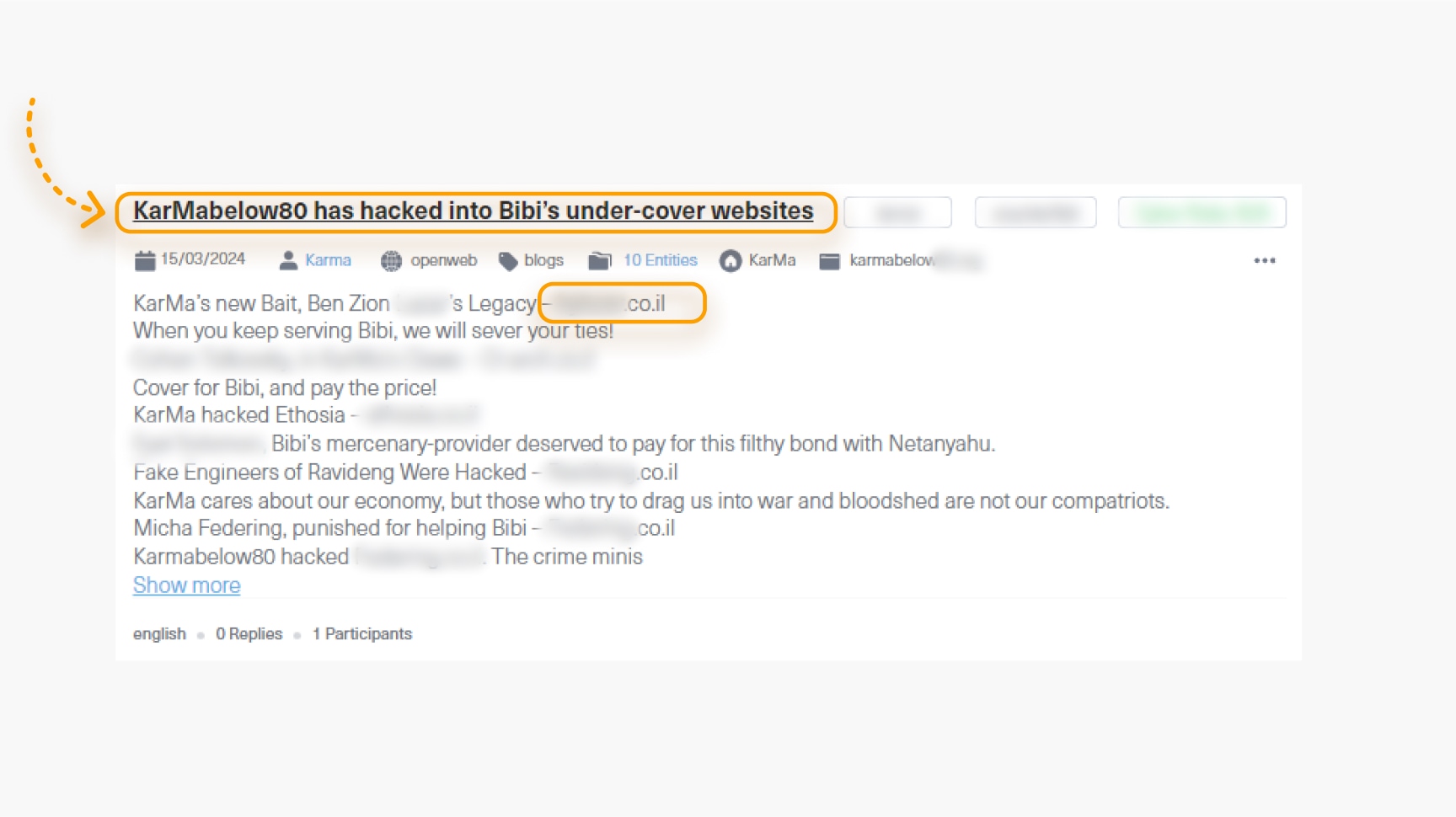
A month later, the Iranian hacktivist group KARMA announced they had hacked the specific company we monitored. The following screenshot from Lunar shows a post crawled from KARMA’s official site where they publish their victims. This example highlights how threat actors exploit leaked accounts to infiltrate companies. Early detection of this IOC could have helped mitigate the incident and prevent the breach.
What does 2024 have in store for us?
In an increasingly unstable global landscape, where tensions between nations are rising and major events such as the US 2024 elections, the Russia-Ukraine war, and escalating conflicts in the Middle East dominate headlines, the importance of gathering and analyzing cyber threat intelligence is paramount. Dark web monitoring tools like Lunar play a crucial role in safeguarding against these threats using three major steps – uncover, identify, and take action. As we move further into 2024, leveraging such intelligence will be essential for maintaining security and resilience against the evolving cyber threat landscape.