Everything you need to know about RockYou2024

RockYou2024 was published on July 4th, 2024. RockYou2024 contains nearly 10 billion passwords, harvested from a vast number of different data breaches. The results are a fifteen percent increase in data from the original RockYou2021 file.
In 2021, a threat actor published what was then the largest compilation of leaked passwords, with over 8.4 billion plain text passwords, known as RockYou2021. This large repository of stolen credentials was a gold mine for threat actors, making it easier for them to potentially access sensitive information and take over accounts.
What can we find about RockYou2024 on the deep and dark web?
RockYou2024 was published as a text file by a threat actor named ObamaCare, who only recently joined the well-known hacking forum LeakBase. The post went viral and was shared on other popular platforms including BreachForums, Kohlchan, and Telegram (all of which are monitored by Lunar, powered by Webz.io).
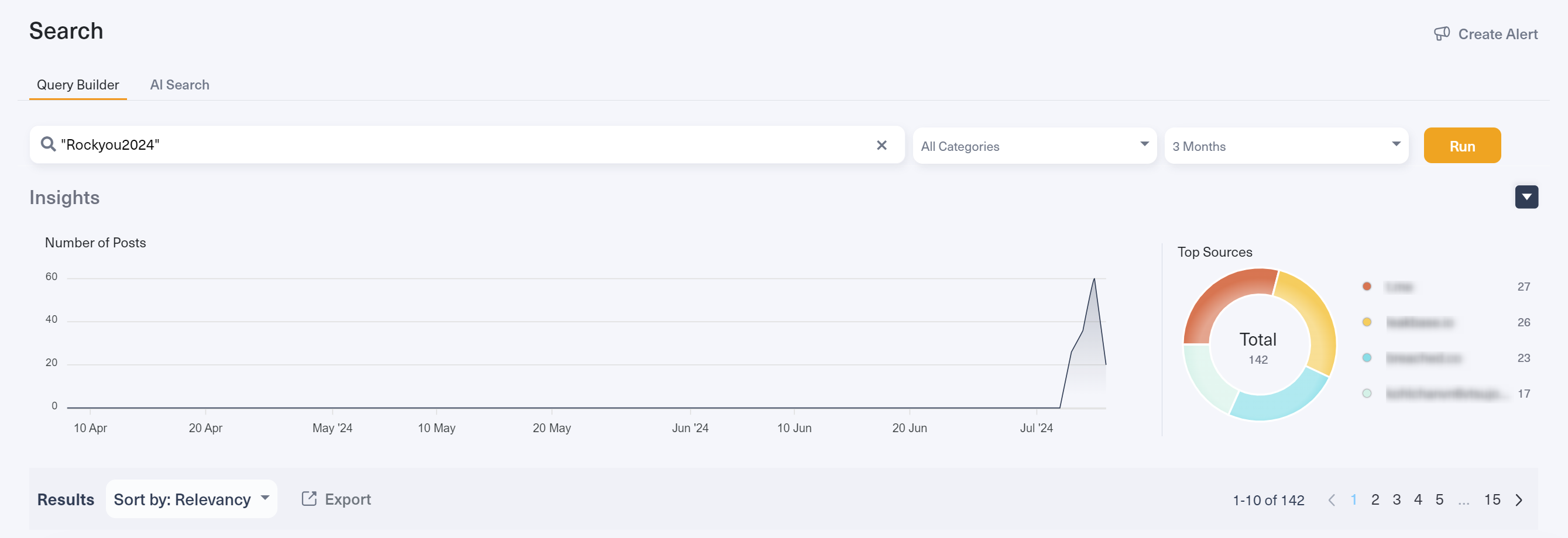
The following graph, taken from Lunar, shows that no one disclosed any information about RockYou2024 until July 2024, and that the discussions about the leak hit a sharp peak and then declined.
The RockYou2024 File
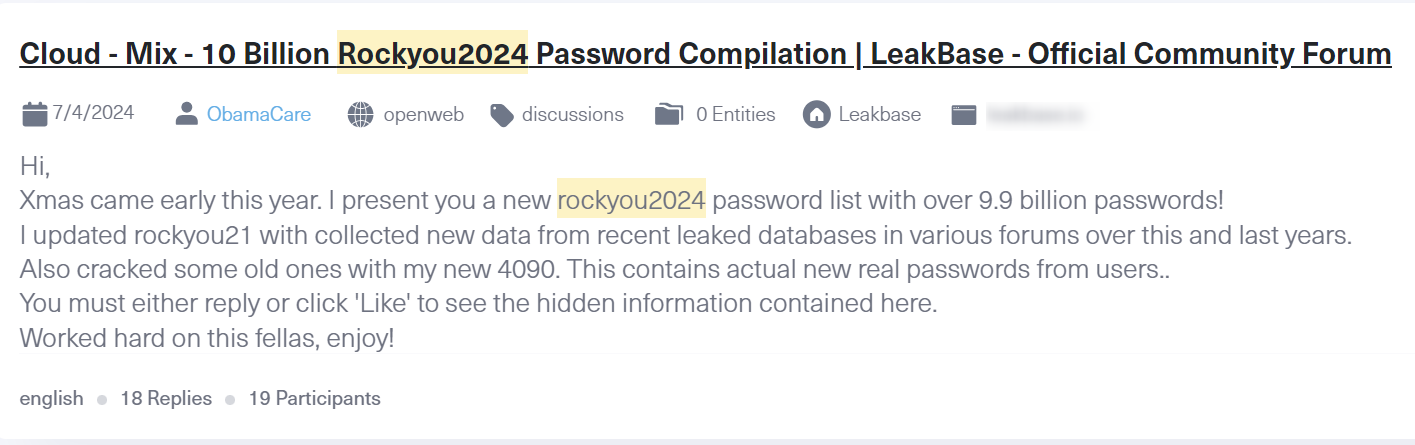
A new user named ObamaCare posted the file to LeakBase on July 4. The largest cache of leaked information to date, this file contains 9.9 billion passwords from users around the world. The passwords were taken from RockYou2021 plus an additional 1.5 billion new passwords from the past three years.
Even though the original thread was mysteriously removed from LeakBase we can still find it using our dark web monitoring tool, Lunar, which indexes and archives content from the deep and dark web.
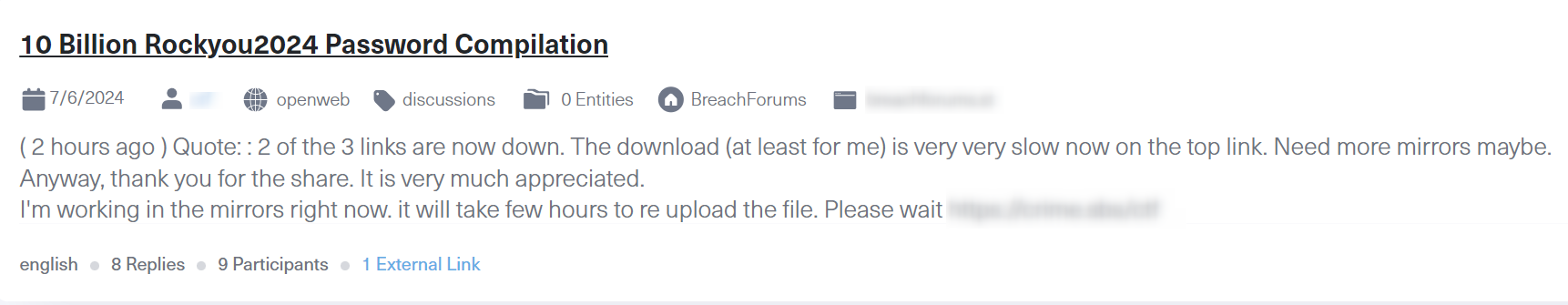
We could find theRockYou2024 file shared on various forums across the dark web and users thanked ObamaCare for the information.
Discussions about the RockYou2024 data leak
Some users claimed this leak could be “a huge upper hand” for threat actors, such as the user in the next image, taken from an alternative social media platform.
What kind of threats does RockYou2024 pose?
Threat actors can use passwords in this massive compilation of 9.9 billion passwords to conduct various types of attacks, but the primary threat is brute-force attacks. Brute force attacks require password databases to gain unauthorized access to various online accounts of both individuals and corporations. They could run a script that automatically checks these passwords against existing login credentials to break into the account.
The big picture
Zooming out, we see that leaking passwords is the first step in MITRE’s ATT&CK Vector for Enterprise. Reconnaissance, or information gathering, involves collecting personal data about the person or group they target. Once a threat actor has the necessary information (email addresses, end platforms, and phone numbers) they can perform Account Takeover (ATO) and identity theft.
How to keep track of future credential leaks?
As data breaches and leaks continue to rise, both in scope and in frequency, it has become essential to track whether the credentials of your employees or clients have been compromised.
Stay informed on the dark web chatter
As the landscape of online security evolves, so does the cyber security professional’s job. For this reason, it’s critical to keep track of your organization’s important information with comprehensive dark web monitoring tools, such as Lunar, by Webz.io. Filter through the noise by easily accessing the data you need from dark web marketplaces or alternative social media to proactively monitor threats to your organization.