What Should GitHub Supply Chain Attack Teach Us?

In the latest supply chain attack, the online software development platform GitHub fell victim to a cyberattack after its source code was compromised.
The source-code repository is sometimes considered the soft underbelly of a company. Developers might leave assets such as IPs, domains, tokens, credentials, and other private assets as part of the package they write. This type of coding style can help attackers to gain access to sensitive private services unnoticed, making it harder for companies to detect the breach for long periods of time.
In this latest attack, the threat actor used stolen OAuth user tokens issued to Heroku and Travis-CI to download data from the private repositories of dozens of organizations, including GitHub’s own npm production infrastructure.
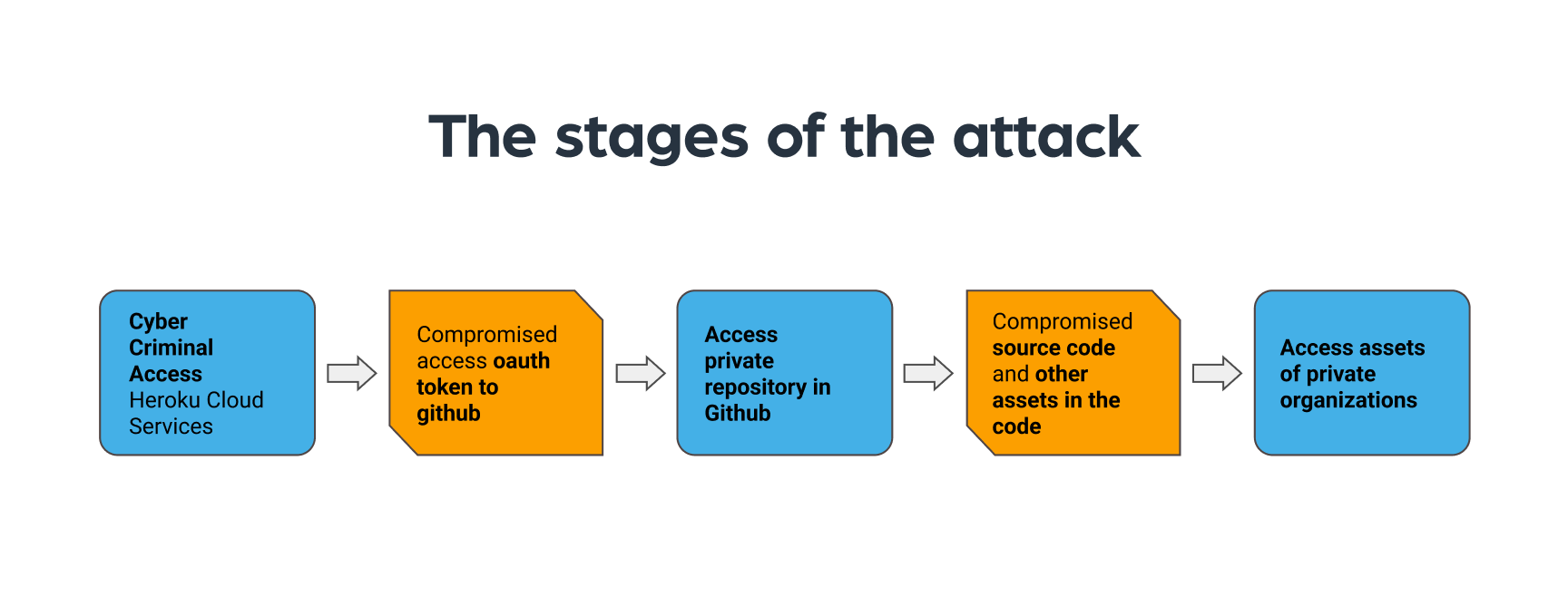
How was the attack launched?
Step #1
The attacker accessed and breached, most likely a few months ago, the cloud services of Heroku and Travis.ci which serve thousands of private companies.
Step #2
The attacker stole OAuth user tokens, enabling access to GitHub.
Step #3
The attacker used the tokens to access GitHub and download the source codes of dozens of private companies.
Step #4
The attacker then used the stolen source codes to compromise other companies.
What will the attackers do next?
Once they steal other private assets, the attacks are likely to take one of the next two steps:
- Sell the compromised assets of these private organizations in dark web marketplaces
- The attackers use the compromised data to breach other organizations and steal more sensitive information and assets.
What are the other implications of the GitHub supply chain attack?
There are various implications to this type of supply chain attack. For example:
- The news spreads and other criminals become aware of the breach which can increase the demand for the breached assets.
- Copycat hackers will try to attack the same cloud service or other cloud services to gain access to GitHub’s OAuth tokens, knowing it’s very likely to lead them to highly valuable private information.
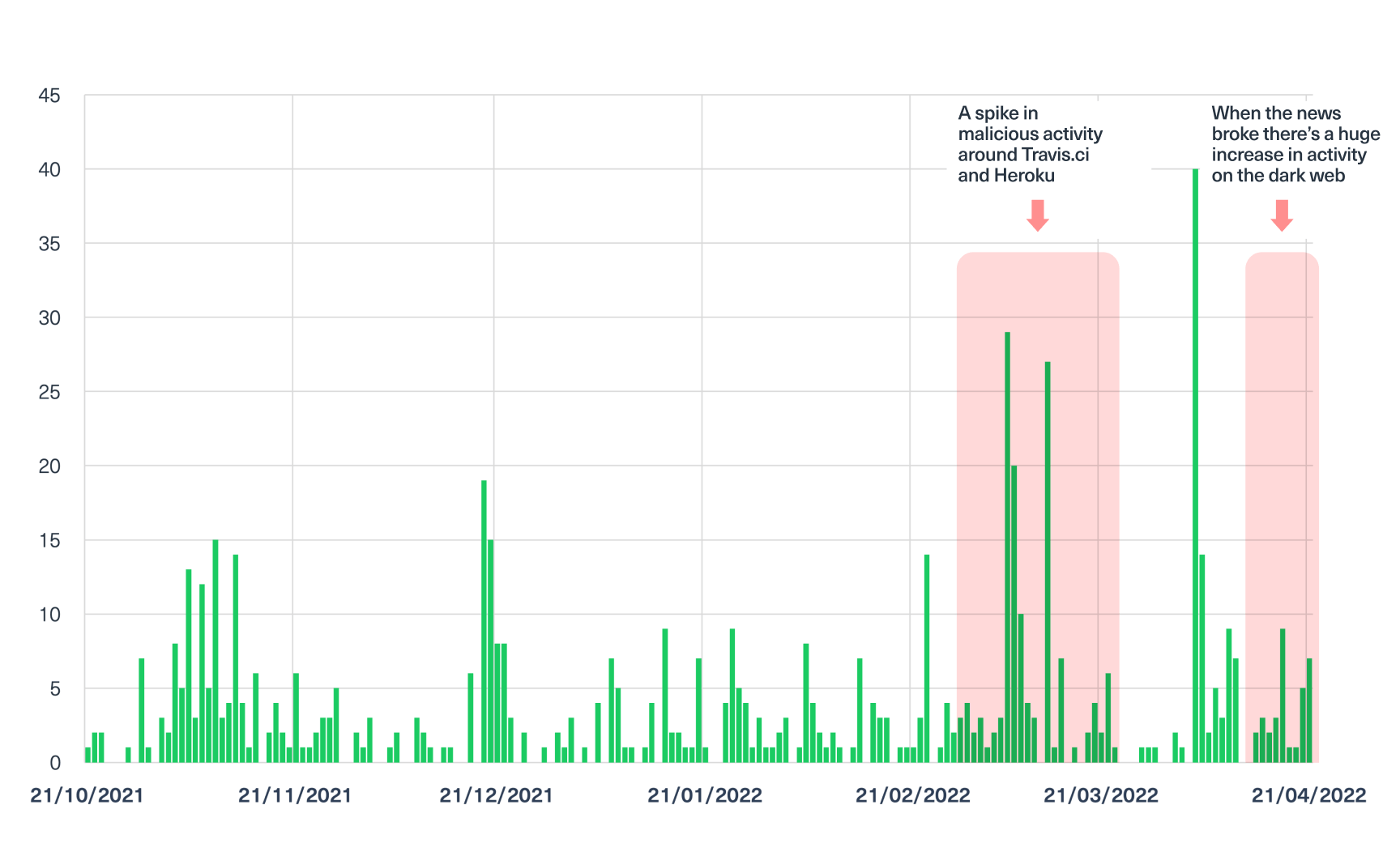
Mentions of Travis.ci and Heroku on the dark web
Using our dark web data, we ran our query to search for mentions of Travis.ci and Heroku on dark web marketplaces, forums, and discussions.
In the next chart, you can see the number of mentions of Travis.ci and Heroku on the dark web over the past 4 months. We can see a spike in activity around March 7, 2022, a month before GitHub made a public announcement about the attack. This could indicate that threat actors were looking to breach the systems of Travis.ci and Heroku.
A little more than a month later, around the time the news of the attack was made public, we can see another increase in the number of mentions of Travis.ci and Heroku. This could suggest that other threat actors searched for the leaked data from the GitHub attack.
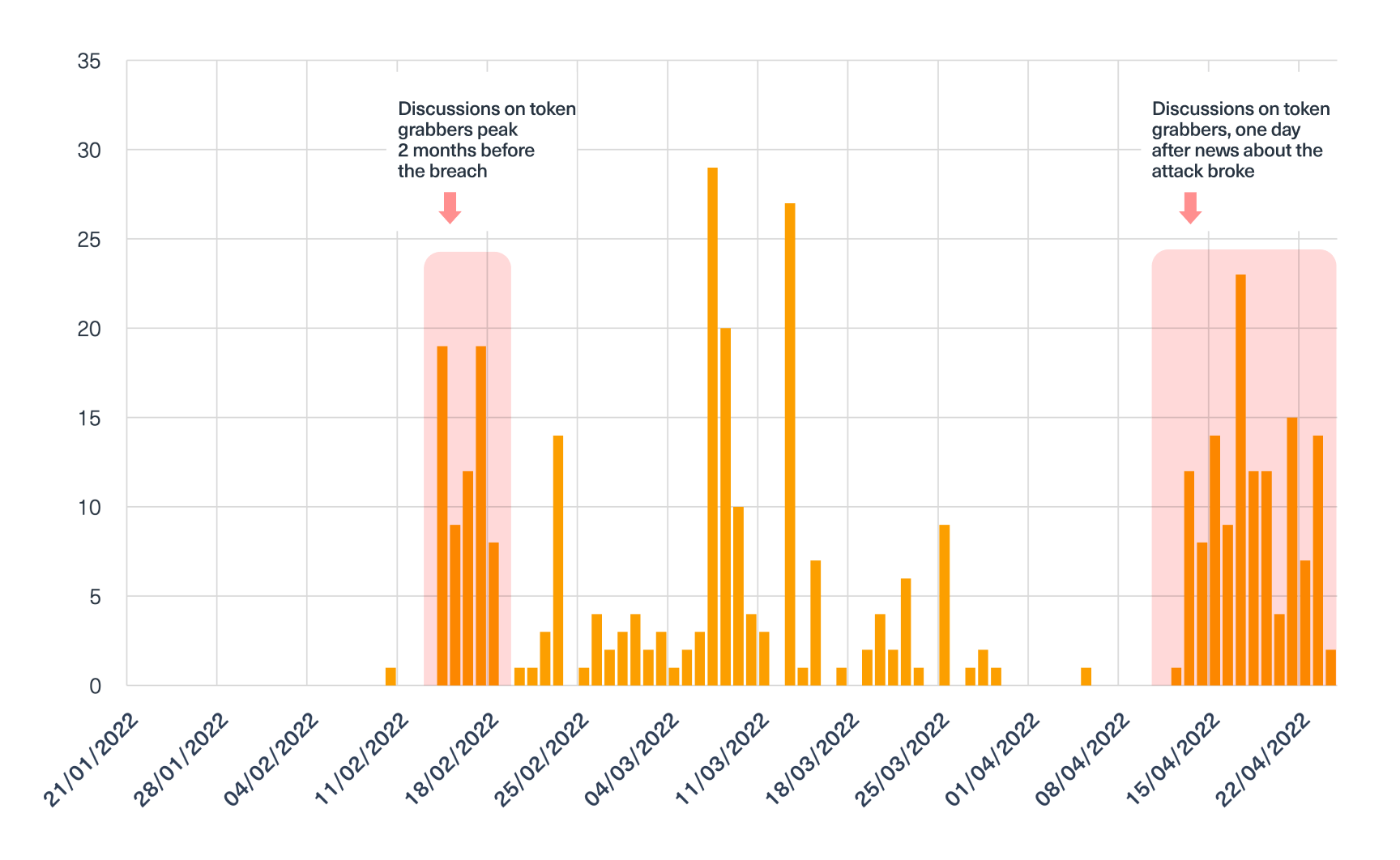
We also searched for keywords that are relevant to this attack. In this case we ran a query to search for mentions of “token grabber” or “token leecher”, on the dark web. The results showed a higher number of discussions on topics like methods to compromise user tokens, including tools and techniques, about two months before and a day after the news about the GitHub attack made it to the headlines.
We also took a closer look at mentions of Heroku leaked accounts, which increased in early 2022. Many of them were traded in Russian Market and 2easy stores.
In the following image, you can see an example of one of these mentions, which we crawled from a Telegram hacking group in February. In this post, threat actors are discussing Heroku breached accounts:
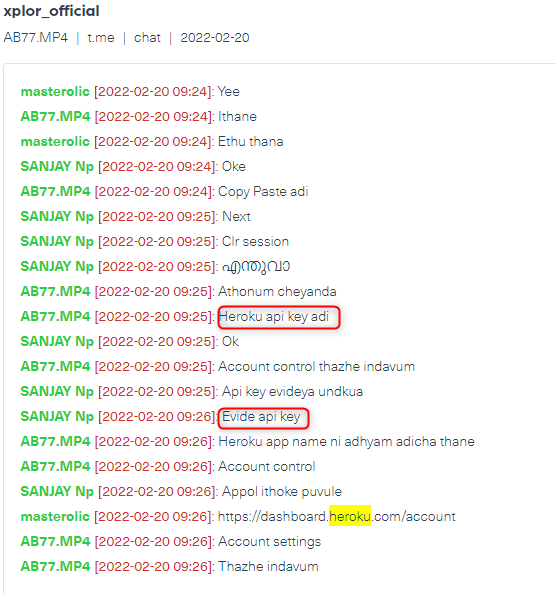
The discussion on this group, called xplor_official, is in Malaysian. Two threat actors are discussing Heroku tokens, one of them asks if the other has a token, the second user responds by saying he has a token. This discussion is an indication of a potential risk for Heroku’s domain. We identified similar mentions of Heroku across other Telegram channels.
In order to break the chain and protect against third-party attacks, companies need to continuously collect intelligence from the deep and dark web. It is in these online spaces that threat actors and cybercriminals discuss their plans and trade compromised entities and PIIs which can bring the entire chain down.
Using Webz.io’s live and historical data from the deep and dark web, enterprises and organizations around the world are monitoring compromised assets, entities, brands, IPs, and CVEs to stay ahead of the next cyberattack.