See
What Our Customers Say
Scaled Credential Detection
“With Lunar, we scaled dark web monitoring, doubled credential leak detections, and cut investigation time by 30%. It’s fast, flexible, and critical to staying ahead of today’s threat landscape.”
— Aviv Mizrahi
Incident Response Engineer, TrustNet
A Game-Changer for OSINT Investigation
“Lunar has become an invaluable partner in our Dark Web and OSINT research. It eliminates tedious digging in an ever-shifting landscape, freeing us to focus on the real value: in-depth analysis and maximizing the impact of our findings.“
— Senior Director
Global FinTech Company
Faster Detection
Lunar has significantly enhanced our cybersecurity operations by automating and expediting queries, particularly in monitoring platforms like the Russian Market. This efficiency allows us to swiftly identify and address potential threats, ensuring our clients’ security.
— Athos Cauchioli
CEO
36 B+
Compromised Credentials
1.4 B+
Malware Records
48 K+
Ingested Breaches
500 K+
Leaked Credit Cards
Proactive Intelligence That
Keeps You One Step Ahead
Trustworthy & Actionable Insights
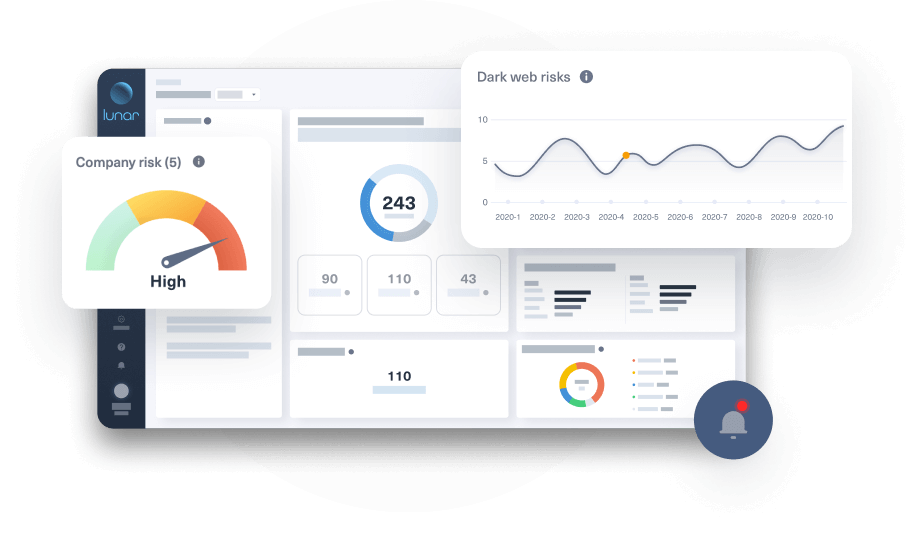
We provide trusted, relevant threat data that is specific to your organization, reducing false alerts and focusing your efforts on incidents that require the fastest response.
Next-Generation Data Collection
Leverage Lunar's advanced technology to identify critical threats from the hard to reach spots on the open, deep, and dark web, reducing false positives and accelerating response times.
Proactive Efficient Response
Combine the vast repository of deep and dark web data with proprietary AI technologies to enhance your threat investigations. Lunar's machine learning models provide actionable insights that enable your team to detect, collaborate and remediate threats before they escalate.
Unleash
The Next Generation of
Dark Web Monitoring
Reduce the Risk of Data Breaches
Proactively prevent new and ongoing breaches with automated detection of relevant stealer logs, stolen credentials, and sensitive data to prevent new breaches and swifty take action to reduce response time.

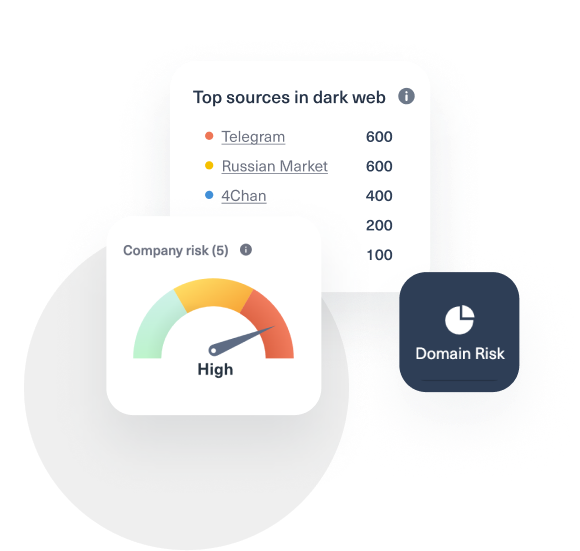
Comprehensive Coverage Means Fewer Blind Spots
Lunar’s 360-degree view of deep and dark web activity related to your organization, employees, and supply chain. ensures you never miss compromised data, threat-related mentions, or potential vulnerabilities.
Mitigate Risk, Strengthen Resilience
Protect brands, digital assets, and employees by tracking attacker TTPs, critical vulnerabilities, and compromised credentials. Gain the insights needed to secure your organization from multiple angles, reducing your overall risk exposure.

Effortless Reporting and Collaboration
Easily share threat intelligence insights with team members or customers using automated, customizable reports. Lunar helps drive collaborative threat response, allowing your team to work seamlessly with executives, partners, and customers to strengthen your security posture.

Proactive Dark Web
Insights for Every Threat

Account Takeover Protection
Automatically identify relevant compromised credentials and login details to mitigate account takeover threats and fraud.
learn more
Identity Theft Protection
Monitor login credentials, and personal information on the deep and dark web to prevent fraud and breaches.
learn more
Data Breach Detection
Rapidly detect past and future breaches by tracking mentions of organizations’ sensitive data or compromised credentials.
learn more
Fraud Detection
Proactively track phishing attempts and discover mentions of organizations’ assets, stolen credit card numbers, wallet IDs, and other confidential data to protect against online fraud.
learn more
Brand Protection
Quickly idenitfy malicious threats against your brand on the deep and dark web such as compromised assets, vulnerabilities, and fraud.
learn more
Supply Chain Risk Monitoring
Uncover your supply chain risk with critical information from the dark web about breaches and compromised assets of both vendors and customers, and cyber risks like CVEs exploit.

VIP Executive Protection
Instantly spot cyber and physical threats against company executives, board members, investors and key personnel.
learn more
Ransomware Attacks Remediation
Discover ransomware threats, profile ransomware groups, and identify target companies to prevent the next major ransomware attack.
Account Takeover Protection

Account Takeover Protection
Automatically identify relevant compromised credentials and login details to mitigate account takeover threats and fraud.
learn moreIdentity Theft Protection

Identity Theft Protection
Monitor login credentials, and personal information on the deep and dark web to prevent fraud and breaches.
learn moreData Breach Detection

Data Breach Detection
Rapidly detect past and future breaches by tracking mentions of organizations’ sensitive data or compromised credentials.
learn moreFraud Detection

Fraud Detection
Proactively track phishing attempts and discover mentions of organizations’ assets, stolen credit card numbers, wallet IDs, and other confidential data to protect against online fraud.
learn moreBrand Protection

Brand Protection
Quickly idenitfy malicious threats against your brand on the deep and dark web such as compromised assets, vulnerabilities, and fraud.
learn moreSupply Chain Risk Monitoring

Supply Chain Risk Monitoring
Uncover your supply chain risk with critical information from the dark web about breaches and compromised assets of both vendors and customers, and cyber risks like CVEs exploit.
VIP Executive Protection

VIP Executive Protection
Instantly spot cyber and physical threats against company executives, board members, investors and key personnel.
learn moreRansomware Attacks Remediation

Ransomware Attacks Remediation
Discover ransomware threats, profile ransomware groups, and identify target companies to prevent the next major ransomware attack.

 When Hackers Plan We Alert.
When Hackers Plan We Alert.