How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

In today’s rapidly evolving cyber landscape, cyber security teams must move beyond traditional defense mechanisms and adopt a proactive approach to threat intelligence. Cyber adversaries operate with diverse objectives and target various sectors, each employing distinct tactics. Understanding these actors—how they operate, what motivates them, and where they communicate—is essential for developing a resilient security posture because it helps cybersecurity teams stay ahead of threats, adapt their defenses, and shut down attacks before they gain traction.
Before discussing how to deal with cyber threat groups, we must first define who they are. Threat actors come in different forms, each with distinct motivations, tactics, and levels of sophistication.
In this section, we conduct adversary group classification. The five primary types of cyber threat actors are:
APT groups are highly sophisticated and well-funded. Each group operates under the direction of a specific government. Their objectives typically involve long-term cyber espionage campaigns, intellectual property theft, and occasionally, disruptive or destructive cyberattacks.
Cybercriminals operate either as part of organized crime groups or as independent actors. Their primary focus is on monetizing stolen data, deploying ransomware, and selling illicit goods on the dark web. As attack techniques and expertise in this field have advanced, many cybercriminals have adopted the Ransomware-as-a-Service (RaaS) model. This approach allows them to sell access to malware and attack frameworks, enabling even less-skilled threat actors to execute sophisticated cyberattacks.
Hacktivists conduct cyberattacks to promote social or political causes, often in retaliation against perceived injustices. Their attacks are typically disruptive rather than financially motivated, with the goal of exposing sensitive information, defacing websites, or disrupting services.
Insider threats come from individuals within an organization—employees, contractors, or business partners—who misuse their legitimate access. Unlike external attacks, insider threats bypass traditional security defenses and can be harder to detect.
Script kiddies are inexperienced individuals who use pre-built hacking tools and automated scripts without fully understanding how they work. While they lack the sophistication of nation-state actors or organized cybercriminals, they can still cause significant disruption—especially when leveraging DDoS attacks, website defacements, or basic malware distribution.
Recognizing the different hacker group names and types is just the first step. To effectively defend against them, cybersecurity teams must go beyond identification, leveraging real-time threat intelligence to proactively track, detect, and mitigate threats before they escalate into full-blown attacks.
Threat hunting is a proactive security strategy that involves actively searching for signs of malicious activity within an organization’s environment before an attack can fully materialize.
Instead of relying solely on automated detection tools, threat hunters and CTI teams use intelligence-driven techniques to identify emerging threats based on attacker behaviors. Rather than relying on IOCs, which identify past activity, hunting focuses on identifying Indicators of Attack (IOAs) and aligning them with the MITRE ATT&CK framework, a comprehensive matrix that maps out the tactics, techniques, and procedures (TTPs) used by known threat actors. When security teams map identified IOAs to the MITRE ATT&CK framework they can anticipate attacks before they unfold, disrupt threat actors in action, and strengthen their defenses against future threats.
The two primary methodologies used by security teams for threat hunting are:
While IOCs are traditionally associated with incident response, they still play a role in proactive threat hunting. Security teams can use IOCs to track known malicious infrastructure, identify repeated attack patterns, and correlate past activity with emerging threats. Threat hunters can uncover leaked credentials, compromised IPs, or malware hashes before they are widely used in attacks by monitoring the dark web.
By using Lunar, our dark web monitoring platform, you can track and collect mentions of malicious IPs, domains or URLs found in dark web forums, marketplaces, and Telegram channels. Lunar also detects file dumps containing IOC collections, as in the example shown in screenshot, where we detected an IOC dump in the LockBit Telegram channel.
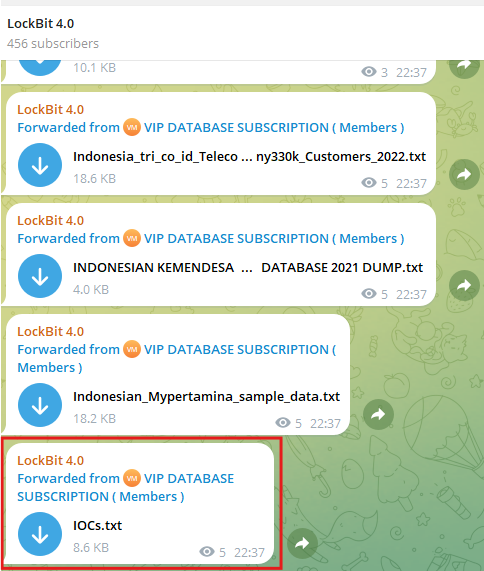
Effective threat hunters follow a structured process that aligns with attacker behaviors rather than static indicators. They leverage MITRE ATT&CK techniques to proactively detect and mitigate threats before they escalate.
Below is a step-by-step process for hunting using IOAs:
Threat hunting begins with a hypothesis. If an adversary gains access to a corporate network using Valid Credentials (T1078) over Remote Desktop Protocol (RDP) (T1021.001), the threat actors may attempt to move laterally across the network, access sensitive systems, or exfiltrate valuable data.
Using hunting queries, threat hunters look for repeated RDP login attempts, particularly from unusual locations or unauthorized accounts.
Once remote access is confirmed, the next step is to detect unusual activities performed after login, mapping them to MITRE ATT&CK techniques to understand the attack progression. Threat hunters analyze user behavior to identify:
If attackers successfully access internal systems, they may attempt to sell access to compromised machines on dark web marketplaces. Using Lunar, our dark web monitoring platform, threat intelligence teams can monitor underground forums for mentions of company domains in RDP access listings or the company employees’ credentials being sold.
Additionally, Lunar allows you to set up real-time alerts for relevant mentions, enabling proactive threat detection and mitigation.
If unauthorized RDP access is confirmed and linked to dark web activity, immediate actions should be taken:
Building on the previous example, by connecting unauthorized RDP access to dark web exposure, CTI teams and threat hunters can use Lunar to trace the full lifecycle of a breach, from the valid accounts credentials that enables the threat actor to abuse the RDP, to the RDP access that might be offered for sale in the dark web post the incident, to other services available to detect such as initial access brokerage, and exploit development.
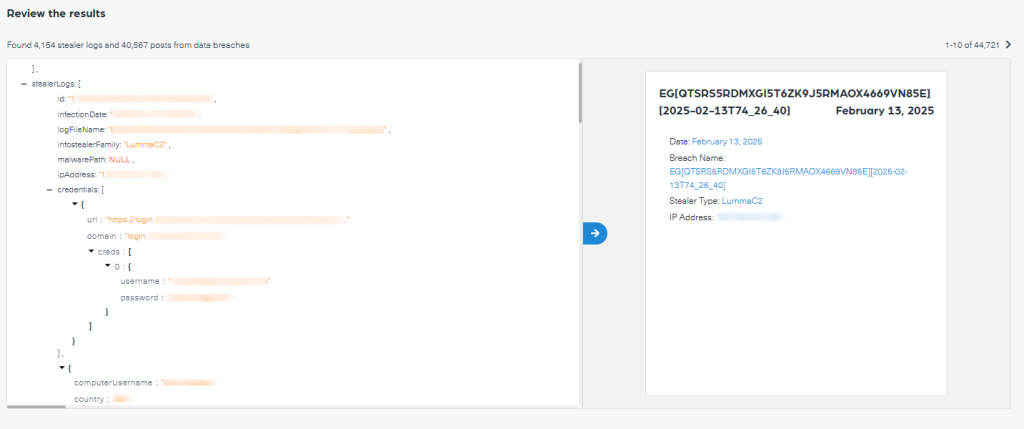
Using Lunar helps you gain insights on notable threat actors and their actions, identify early indications, track exploitation trends to anticipate targeted attacks and to build better detection and mitigation strategies.
Identifying threat actors is just the first step; proactive hunting and intelligence-driven defense are essential. By leveraging MITRE ATT&CK techniques, tracking IOAs, and monitoring dark web activity, CTI teams can detect threats early, disrupt attack lifecycles, and anticipate emerging risks. Integrating threat actor profiling, structured hunting, and dark web intelligence strengthens security postures, ensuring organizations stay one step ahead of evolving cyber threats.
Learn how to use Lunar, our advanced dark web monitoring tool, for real-time threat intelligence.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.