How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Dark web hacker forums are critical hotspots for illicit activities, where cybercriminals converge to exchange stolen data, hacking tools, and trade secrets. Over the years, these forums have persisted and adapted to increased scrutiny from law enforcement and cybersecurity professionals.
As we move through 2024, understanding the dynamics and operations of these forums is more crucial than ever for organizations worldwide. Dark web hacker forums contain a treasure trove of intelligence that can help preempt and mitigate cyber threats — from trojan horses and zero-day exploits to phishing attacks and cryptojacking.
This article provides an overview of the top dark web hacker forums in 2024. By exploring the most active and influential forums, we hope to shed light on cybercriminals’ evolving tactics and strategies. Whether you’re a cybersecurity professional, researcher, or someone curious about the dark web, this article offers valuable insights into the forums shaping the cyber threat landscape today.
Monitoring dark web hacker forums is crucial to a successful cybersecurity strategy. These forums are breeding grounds for cybercriminal activities, allowing hackers to share information, trade stolen data, and collaborate on sophisticated attacks. Understanding and keeping an eye on these forums provides several significant benefits:
Organizations must consider ethical and legal considerations when monitoring hacker forums. Monitoring hacker forums involves navigating complex legal and ethical boundaries so you must do so within the framework of the law maintaining high ethical standards to avoid becoming entangled in illegal activities. Engaging with these forums also requires sophisticated operational security measures to protect the identities and activities of cybersecurity professionals from being exposed or compromised.
Selecting the top dark web hacker forums requires a systematic approach to ensure that we identify the most relevant, active, and influential platforms. We used the following criteria to evaluate and select the forums highlighted in this article:
The hacker forums chosen for this top list meet the criteria as outlined above.
Based on our observations from analyzing dark web data using Lunar, we’ve identified the top 7 hacker forums on the dark web in 2024. Lunar is a tool we’ve developed to monitor the deep and dark web.

XSS is one of the most prominent and well-regarded hacker forums on the dark web. Named after the web security vulnerability “Cross-Site Scripting (XSS),” the forum caters primarily to Russian-speaking cybercriminals and hackers. It has gained a reputation for its professional approach and the high quality of its content, attracting a sophisticated and experienced user base.
Launch Date
● Initially launched in 2013, XSS was relaunched in September 2018 after a significant revamp.
Main Language
● Russian
● Exclusive Access: XSS is a closed forum, meaning that access is restricted to members who have been vetted and approved. This exclusivity ensures that the community remains focused and that the quality of discussions is maintained at a high level.
● Paid Memberships: Some sections of the forum are only accessible through paid memberships, which provide additional layers of content and opportunities for its members. These premium sections often contain more sensitive and valuable information.
XSS is known for hosting a wide array of illicit activities and discussions, including:
● Malware and Exploits: The forum is a hub for sharing and selling malware, exploits, and zero-day vulnerabilities. Members discuss various methods to compromise systems and networks, often providing detailed guides and tutorials.
● Credential Databases: XSS features extensive databases of stolen credentials, including login information for various online services. Forum members trade these databases using them for cybercriminal activities.
● Carding: The forum focuses on carding, which involves the theft and fraudulent use of credit card information. Members share tips, tools, and stolen card data to facilitate these activities.
● Access Sales: Cybercriminals on XSS frequently sell access to compromised systems, networks, and accounts. This access can include anything from corporate networks to individual social media accounts, giving buyers various entry points for further exploitation.
● Financial Fraud: Discussions on XSS often revolve around methods of committing financial fraud, including phishing, and social engineering. Most discussions focus on tactics designed to deceive and steal from victims.
XSS employs several measures to protect its users:
● Encrypted Communications: The forum uses encryption to secure communications between members, ensuring that interactions remain private and protected from surveillance.
● Anti-Surveillance Techniques: XSS employs various anti-surveillance techniques to evade detection by law enforcement and cybersecurity professionals. These measures include tools designed to obscure the identities and activities of its members, such as proxy servers and encrypted email services.
XSS has been at the center of several high-profile incidents and trends in the cybercriminal world:
● AvosLocker Recruitment: The AvosLocker ransomware group used XSS to recruit new members for cybercriminal operations. While direct recruitments are rare, such activities highlight the forum’s role as a breeding ground for organized cybercrime.
● Marketplace for Illicit Goods: Over the years, XSS has evolved into a comprehensive marketplace where users can buy and sell various illicit goods and services, including hacking tools, stolen data, and counterfeit documents.
Dread is a dark web forum designed to mimic the structure and functionality of Reddit, featuring a familiar and user-friendly interface for its members. Dread has rapidly become one of the most significant platforms for discussions related to illicit activities, including hacking and cybercrime. Its popularity surged after Reddit banned several darknet market discussion communities, leading many users to migrate to this platform.
Launch Date
● February 2018
Main Language
● English
● Reddit-Like Structure: Dread’s interface is designed to resemble Reddit, complete with sub-communities (subdreads) that focus on specific topics. This structure makes navigation intuitive and allows users to easily find and participate in discussions relevant to their interests.
● Privacy and Security: Dread strongly emphasizes user privacy and security. It operates exclusively over the Tor network, ensuring that users’ identities and activities remain anonymous. Additionally, the forum employs various encryption methods to protect communications.
Dread is a versatile forum that hosts a wide range of discussions and activities, including:
● Hacking Guides and Tutorials: Dread is renowned for its comprehensive guides and tutorials on hacking and cybersecurity. These resources cover a broad spectrum of topics, from basic hacking techniques to advanced exploitation methods.
● Software and Carding: The forum features in-depth discussions on software hacking and carding (credit card fraud). Members share tools, scripts, and strategies for compromising software and conducting fraudulent transactions.
● Drug Trade: Dread is also a significant hub for the trade of illegal drugs. Users can find detailed information about various substances, their effects, and how to obtain them.
● Stolen Data and Databases: Dread is a marketplace for stolen data, including personal information, login credentials, and financial records. Users frequently buy and sell large datasets obtained from data breaches.
● Marketplace Announcements: The forum serves as a bulletin board for announcements related to darknet marketplaces. This includes updates on market status, security alerts, and reviews of different market platforms.
Dread’s commitment to user security and anonymity is evident in its features:
● Tor Network: By operating exclusively on the Tor network, the forum ensures that all user traffic is anonymized and protected from surveillance.
● Encryption: The forum uses strong encryption methods to secure user communications. This includes end-to-end encryption for private messages and encrypted storage for sensitive data.
● Moderation and Verification: Dread employs a team of moderators to maintain the quality of discussions and enforce forum rules. Verified vendors and trusted members are given special status, adding more security and credibility to their transactions.
Dread has been involved in several notable incidents and trends that highlight its significance in the dark web ecosystem:
● Market Shutdown Announcements: Dread has been the primary platform for announcements regarding the shutdown of major darknet marketplaces. For instance, it was used to inform users about the closure of Dream Market, one of the largest darknet markets.
● Guides on Advanced Hacking: The forum hosts some of the most detailed and advanced hacking tutorials on the dark web. These guides cover sophisticated techniques such as reverse engineering, malware development, and penetration testing.
● Community Growth: Since its launch, Dread has seen exponential growth in its user base, becoming a central hub for darknet discussions. Within just a few months of its launch, Dread amassed over 12K users, reflecting its rapid rise in popularity.

Nulled is one of the most prominent and active hacker forums on the dark web. Known for its vast user base and extensive range of illicit content, Nulled is a hub for cybercriminal activities, including the exchange of stolen data, hacking tools, and cracked software. Despite significant disruptions, including a major hack in 2016, Nulled has maintained its status as a key player in the cybercriminal ecosystem.
Launch Date
● 2015
Main Language
● English
● Large Community: With millions of registered users and tens of millions of posts, Nulled boasts a vibrant and active community. This large user base ensures a constant flow of new content and discussions, making it a valuable resource for cybercriminals.
● Diverse Content: Nulled offers a wide variety of content, including cracked software, stolen accounts, hacking tools, and tutorials. The forum is divided into numerous sections, each catering to different aspects of cybercrime and hacking.
Nulled is known for hosting a wide range of cybercriminal activities and discussions, including:
● Cracked Software and Tools: One of the most popular sections on Nulled is dedicated to sharing and selling cracked software and hacking tools. Members can find anything from pirated applications to specialized hacking utilities designed to exploit vulnerabilities.
● Stolen Accounts and Databases: The forum features extensive databases of stolen accounts, including credentials for various online services, email accounts, and financial institutions. These databases are often traded or sold among members.
● Hacking Tutorials and Guides: Nulled provides numerous tutorials and guides on hacking techniques. These resources range from basic hacking methods to advanced exploitation techniques, catering to novice and experienced hackers.
● Marketplace: The forum includes a marketplace section where users can buy and sell illicit goods and services. This marketplace covers a broad spectrum of illegal activities, from selling stolen credit card information to offering hacking services for hire.
● Financial Fraud: Discussions on Nulled often focus on methods of committing financial fraud, including scams designed to steal money from victims, such as phishing and carding.
Nulled places a strong emphasis on user security and anonymity, implementing several measures to protect its members:
● Encrypted Communications: The forum uses encryption to secure communications between users, ensuring that interactions remain private and protected from surveillance.
● Anti-Surveillance Techniques: Nulled employs various anti-surveillance tools and techniques to evade detection by law enforcement and cybersecurity professionals. It employs tools for obscuring the identities and activities of its members, such as proxy servers and encrypted email services.
● Account Verification: Nulled requires new users to go through a verification process to gain full access to the forum. This helps maintain the quality of the community and reduces the risk of infiltration by law enforcement or security researchers.
Nulled has been involved in several notable incidents and current trends regarding this marketplace, including:
● 2016 Hack and Data Leak: In 2016, the Nulled platform was hacked, resulting in a significant data leak that exposed the personal information of its users, including email addresses, passwords, and purchase records. This incident drew considerable media attention and demonstrated the risks involved in participating in such forums.
● Resilience and Recovery: Despite the 2016 breach, Nulled managed to recover and continue its operations. The forum’s resilience has solidified its reputation as a reliable platform for cybercriminal activities.
● Ongoing Activity: Nulled remains one of the most active hacker forums, with daily updates and continuous user engagement. Its ability to attract new members and maintain a steady flow of content ensures its ongoing relevance in the dark web landscape.

Cracked.io is a prominent hacker forum known for its extensive user base and diverse illicit content. As one of the most active forums on the dark web, Cracked.io attracts cybercriminals, hackers, and individuals interested in exploiting various digital vulnerabilities. The forum is a go-to destination for sharing and trading hacking tools, cracked software, and stolen data.
Launch Date
● April 2013
Main Language
● English
● Large User Base: Cracked.io boasts over 3 million users and more than 17 million posts, reflecting a highly active and engaged community. This extensive user base ensures a continuous flow of new content and discussions.
● Comprehensive Categories: The forum is organized into various categories, each focusing on different aspects of hacking and cybercrime. These categories include sections for cracking, hacking tutorials, coding, leaks, and marketplaces.
Cracked.io is a versatile platform that hosts a wide array of illicit activities and discussions, including:
● Cracking and Hacking Tools: The forum is renowned for its extensive collection of cracking tools and hacking utilities. Members share software designed to bypass digital protections, exploit vulnerabilities, and gain unauthorized access to systems and accounts.
● Leaked Data and Accounts: Cracked.io is a major marketplace for leaked data and stolen accounts. Users frequently post and trade login credentials, personal information, and financial data obtained from data breaches and other illegal activities.
● Hacking Tutorials and Guides: The forum offers numerous tutorials and guides on hacking techniques. These resources range from basic beginner instructions to advanced methodologies for experienced hackers. Topics covered include malware development, network penetration, and social engineering.
● Illicit Marketplaces: Cracked.io features dedicated sections for buying and selling illicit goods and services. This includes counterfeit money, stolen identities, and hacking services.
● Coding and Development: The forum focuses strongly on coding and software development, with members sharing scripts, code snippets, and programming advice. This section supports the creation and distribution of custom hacking tools and exploits.
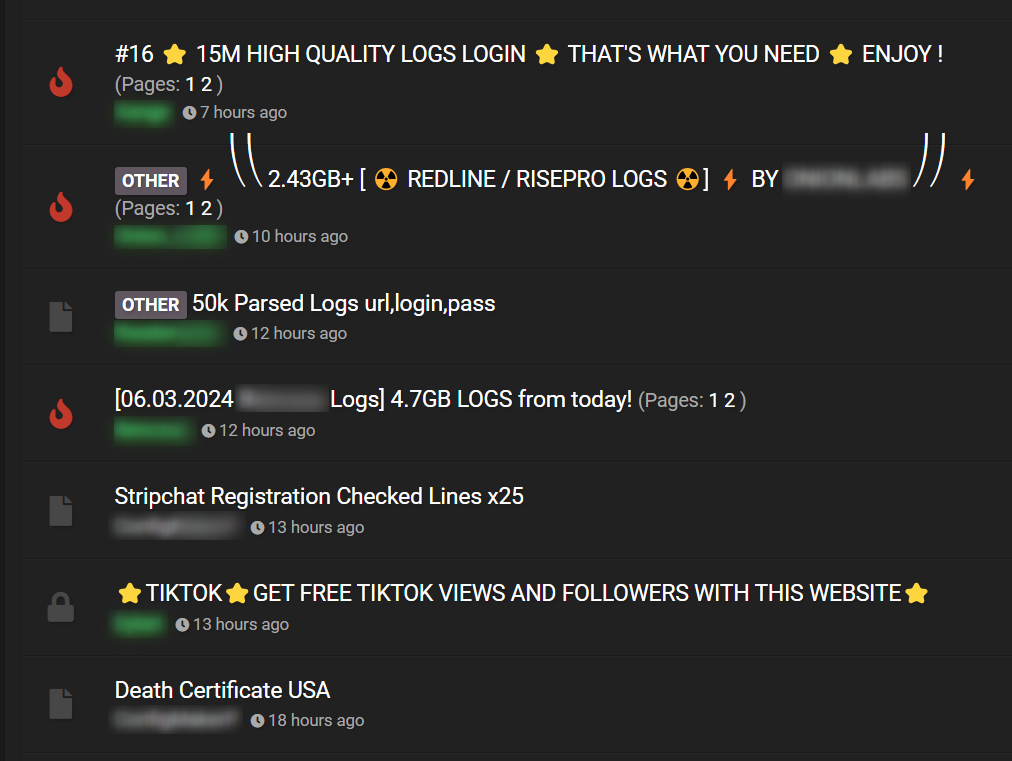
Cracked.io employs various measures to protect its users, including:
● Encrypted Communications: The forum uses encryption to secure communications between members, ensuring that interactions remain private and protected from surveillance.
● Anonymity Tools: Cracked.io encourages the use of anonymity tools such as VPNs, Tor, and encrypted email services to safeguard user identities. These measures help to reduce the risk of exposure and legal repercussions for its members.
● Strict Moderation: The forum employs a team of moderators to enforce rules and maintain the quality of discussions. This includes verifying the legitimacy of posted content and monitoring for potential threats or infiltrations by law enforcement.
Cracked.io has been involved in several notable incidents and trends:
● Continuous Growth: Since its launch, Cracked.io has seen consistent growth in its user base and activity levels. The forum’s ability to attract new members and maintain high engagement ensures its ongoing relevance in the dark web landscape.
● High-Profile Leaks: Cracked.io has been a source of several high-profile data leaks, including large databases of login credentials and personal information from various online platforms. These leaks are often sold or traded among members, contributing to the forum’s notoriety.
● Community Support: The forum is known for its supportive community, where experienced hackers and coders mentor newcomers. This culture of knowledge sharing helps to sustain and grow the cybercriminal ecosystem.

CraxPro is a prominent dark web hacker forum known for its focus on account cracking, data leaks, and trading of stolen digital goods. Since its launch, CraxPro has garnered a large and active user base, making it a significant platform for cybercriminal activities. The forum is designed to cater to novice and experienced hackers, providing various resources, tools, and discussions related to various aspects of cybercrime.
Launch Date
● 2017
Main Language
● English
● Diverse Content: CraxPro offers a wide variety of content, including cracked accounts, leaked databases, hacking tools, and tutorials. The forum is organized into different sections, each dedicated to specific illicit activities.
● Active Community: With thousands of active members and regular updates, CraxPro maintains a vibrant and dynamic community. Users frequently engage in discussions, share new exploits, and collaborate on cybercriminal projects.
● Marketplace: CraxPro includes a bustling marketplace where users can buy and sell a range of illegal goods and services. This includes stolen accounts, cracked software, personal data, and hacking services.
CraxPro is known for hosting a wide range of cybercriminal activities and discussions, including:
● Account Cracking: One of the main focuses of CraxPro is account cracking. Members share tools, techniques, and lists of cracked accounts for various online services, including streaming platforms, social media, and financial services.
● Data Leaks and Databases: The forum is a major marketplace for leaked data. Users post and trade large datasets containing personal information, login credentials, and other sensitive data obtained from data breaches.
● Hacking Tools and Software: CraxPro provides access to various hacking tools and software, including keyloggers, remote access trojans (RATs), and password crackers.
● Tutorials and Guides: The forum offers numerous tutorials and guides on various hacking techniques. These resources cover topics such as phishing, social engineering, malware development, and network exploitation, catering to beginners and advanced hackers. Tools and software available on the forum are often accompanied by tutorials and guides on their usage.
● Illicit Marketplaces: The marketplace section of CraxPro allows users to trade a wide range of illicit goods and services. This includes the sale of stolen credit card information, counterfeit documents, and hacking services.
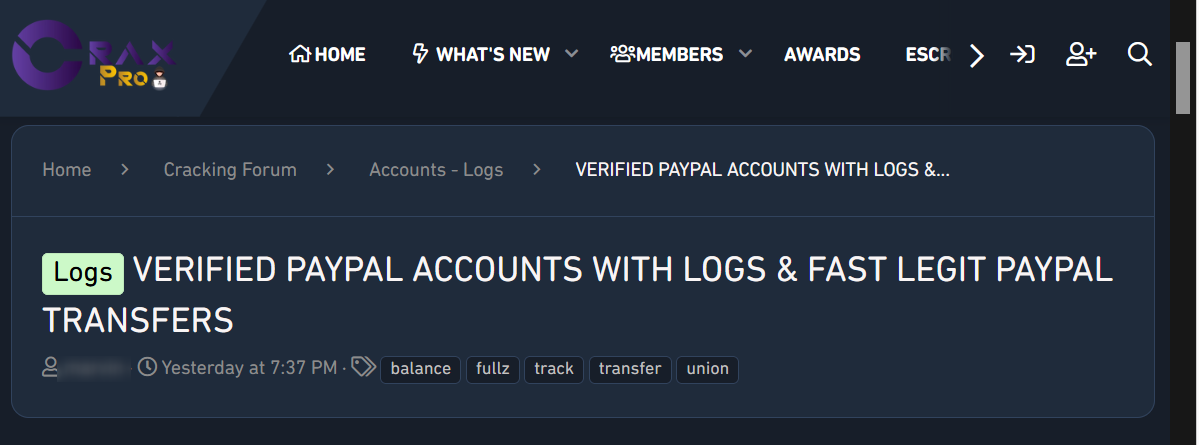
CraxPro has implemented various measures to protect its users, including:
● Encrypted Communications: The forum uses encryption to secure communications between members, ensuring that interactions remain private and protected from surveillance.
● Anonymity Tools: Members are encouraged to use anonymity tools such as VPNs, TOR, and encrypted email services to safeguard their identities and activities.
● Verification and Vetting: CraxPro has a verification process for new members to ensure the quality and security of its community. This process helps reduce the risk of infiltration by law enforcement or security researchers.
CraxPro has been involved in several notable incidents and trends, such as:
● High-Profile Data Breaches: CraxPro has been a source of several high-profile data breaches, where large volumes of stolen data have been shared or sold on the forum. These breaches have affected various organizations and individuals globally.
● Rapid Community Growth: CraxPro has seen rapid growth in its user base and activity levels since its launch. The forum’s ability to attract new members and maintain high engagement ensures its ongoing relevance in the dark web landscape.
● Emerging Threats: CraxPro is often at the forefront of discussing and developing new hacking techniques and tools. By monitoring CraxPro, cybersecurity professionals can gain early insights into emerging threats and prepare accordingly.

Russian Anonymous Marketplace (RAMP) is a prominent dark web forum that quickly became significant within the cybercriminal community. Established as a successor to several earlier dark web marketplaces, RAMP focuses on providing a secure platform for trading a wide range of illegal goods and services, including drugs, digital goods, and hacking tools. The forum’s emphasis on anonymity and security has made it a popular destination for cybercriminals.
Launch Date
● 2021
Main Language
● Russian
● Marketplace Structure: RAMP is a comprehensive marketplace with dedicated sections for different illegal goods and services. These sections include drugs, counterfeit items, stolen data, and hacking tools.
● Security and Anonymity: The forum strongly emphasizes user security and anonymity. It uses advanced encryption methods and operates exclusively over the Tor network, protecting user identities and activities.
● Community and Support: RAMP fosters a community of buyers and sellers, providing support and resources for transactions. Users can review vendors, share experiences, and discuss security measures.
RAMP is known for hosting a variety of cybercriminal activities and discussions, including:
● Drug Trade: The forum has a significant focus on the trade of illegal drugs. Vendors worldwide list various substances, and buyers can purchase them with cryptocurrencies. Detailed vendor profiles and user reviews help ensure the reliability of transactions.
● Digital Goods and Services: RAMP features extensive listings for digital goods, including stolen data, software exploits, and hacking tools. Users can buy and sell databases of personal information, malware, and access to compromised systems.
● Counterfeit Items: The marketplace includes sections for counterfeit goods, such as fake passports, IDs, and other documents. These items are often used to facilitate fraud and identity theft.
● Hacking Tools and Tutorials: RAMP provides a platform for selling hacking tools and software. Members also share tutorials and guides on using these tools effectively, catering to novice and experienced hackers.
● Financial Fraud: Discussions on RAMP often focus on methods for committing financial fraud, including carding, phishing, and other scams designed to steal money from victims.
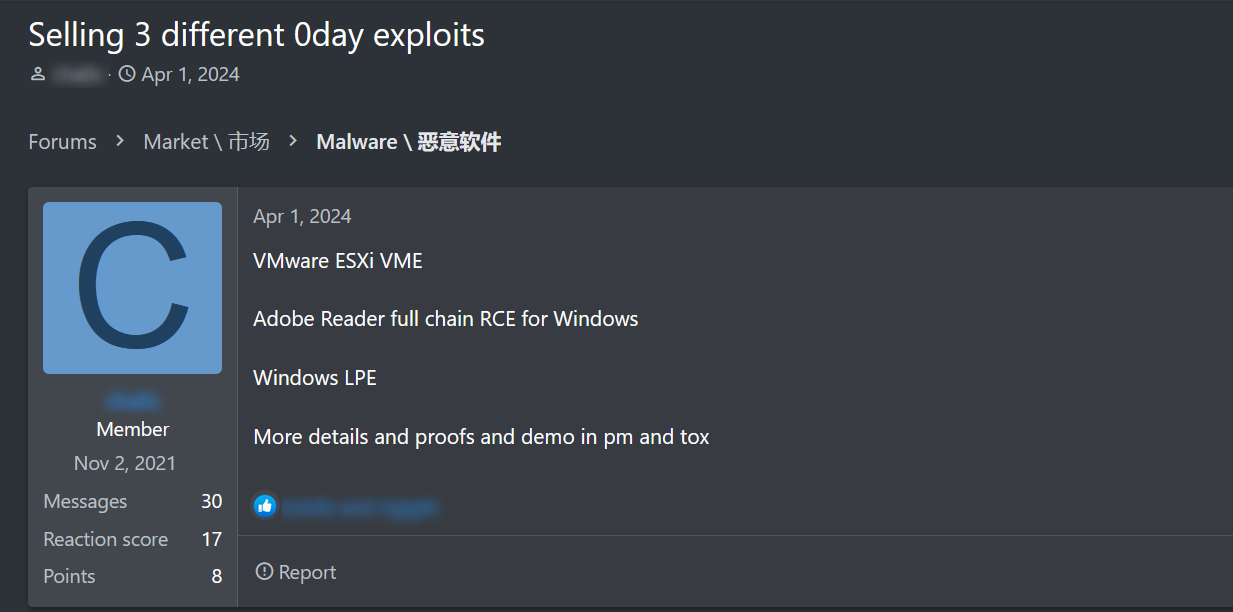
RAMP has implemented several measures to protect its users:
● Tor Network: RAMP operates exclusively over the Tor network, ensuring all user traffic is anonymized and protected from surveillance.
● End-to-End Encryption: The forum uses end-to-end encryption to secure communications between members, ensuring that their interactions remain confidential.
● Anonymity Tools: Members are encouraged to use additional anonymity tools, such as VPNs and encrypted email services, to further protect their identities and activities.
● Vendor Verification: RAMP employs a vendor verification process to ensure that only reliable and trustworthy sellers can list their goods and services. This helps maintain the quality and security of transactions on the forum.
RAMP has been involved in several notable incidents and trends, including:
● Law Enforcement Crackdowns: Despite its security measures, RAMP has been the target of several law enforcement operations aimed at disrupting its activities. These crackdowns highlight the ongoing cat-and-mouse game between dark web marketplaces and authorities.
● Growth and Adaptation: Since its launch, RAMP has adapted to various challenges, including increased law enforcement attention and competition from other marketplaces. Its ability to evolve and maintain a strong user base underscores its resilience and significance.
● Cryptocurrency Use: RAMP’s reliance on cryptocurrencies for transactions reflects a broader trend in dark web marketplaces. Using digital currencies enhances anonymity and complicates efforts to track and shut down illegal activities.

Exploit.in is one of the oldest and most well-established hacker forums on the dark web. Known for its focus on sharing exploits and vulnerabilities, Exploit.in serves as a major platform for cybercriminals seeking to buy, sell, and discuss advanced hacking tools and techniques. Over the years, it has built a reputation for hosting high-quality content and maintaining a robust and active community of experienced hackers.
Launch Date
● 2005
Main Language
● Russian, English
● Longevity and Reputation: As one of the longest-running hacker forums, Exploit.in has a well-known reputation. Its long history and continuous operation attract a wide range of skilled cybercriminals and researchers.
● Diverse Content: Exploit.in covers a broad spectrum of topics related to cybersecurity and hacking. The forum is organized into sections dedicated to specific types of exploits, malware, social engineering, and more.
● Marketplace for Illicit Goods: The forum includes a marketplace where users can trade illicit goods and services, including malware, stolen data, and hacking tools.
Exploit.in is known for hosting a variety of cybercriminal activities and discussions, including:
● Exploits and Vulnerabilities: The forum is a major hub for sharing and trading exploits and vulnerabilities. Members discuss methods for compromising systems and networks, such as zero-day vulnerabilities.
● Malware Development: Exploit.in features detailed discussions and tutorials on malware development. This includes creating and modifying malware to evade detection and maximize impact.
● Hacking Tools and Software: The forum provides access to a wide range of hacking tools and software. These tools are often accompanied by tutorials and guides on their usage, catering to novice and experienced hackers.
● Social Engineering: Exploit.in includes sections dedicated to social engineering techniques like phishing and vishing. Members frequently share strategies for manipulating individuals and organizations to gain unauthorized access to information and systems.
● Stolen Data and Credentials: The marketplace on Exploit.in frequently features listings for stolen data and login credentials. Users can buy and sell sensitive data obtained through cybercriminal activities, including personally identifiable information (PII) and financial records.
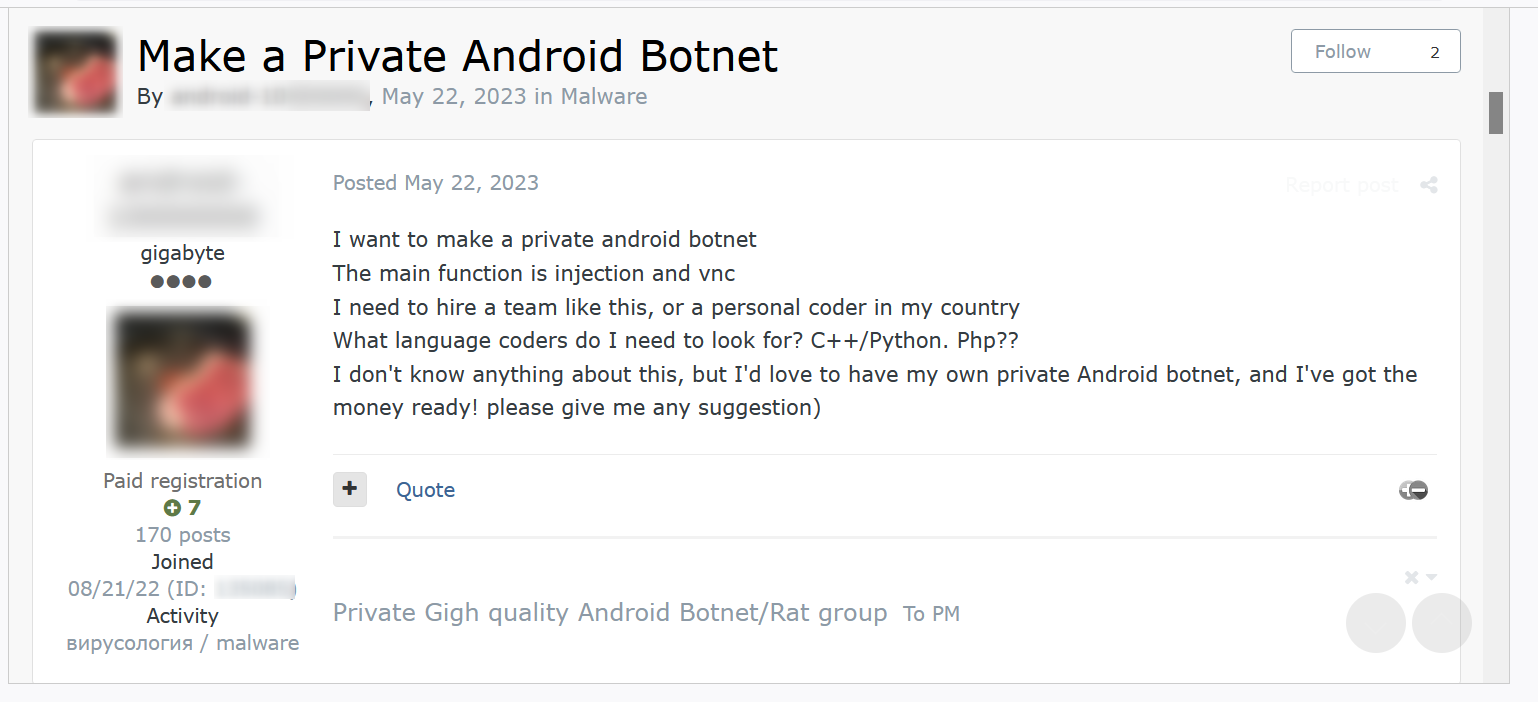
Exploit.in employs various measures to protect its users:
● Encrypted Communications: The forum uses encryption to secure communications between members, ensuring that interactions remain private and protected from surveillance.
● Anonymity Tools: Members are encouraged to use anonymity tools such as VPNs, Tor, and encrypted email services to safeguard their identities and activities.
● Verification and Vetting: Exploit.in has a verification process for new members to ensure the quality and security of its community. This process helps reduce the risk of infiltration by law enforcement or security researchers.
● Moderation and Enforcement: The forum employs a team of moderators to enforce rules and maintain the quality of discussions. This includes verifying the legitimacy of posted content and monitoring for potential threats or infiltrations.
Exploit.in has been involved in several notable incidents and trends, including:
● High-Profile Exploits: The forum has been a source of several high-profile exploits used in major cyberattacks. These exploits often target widely used software and systems, making them valuable commodities on the dark web.
● Continuous Community Growth: Despite increased law enforcement attention and competition from other forums, Exploit.in continues to grow, attracting new members who contribute to its extensive database of hacking knowledge and resources.
● Advanced Threat Intelligence: Exploit.in is often at the forefront of discussing and developing new hacking techniques and tools. By monitoring Exploit.in, cybersecurity professionals can gain early insights into emerging threats and prepare accordingly.
We expect the cybercrime landscape to continue evolving rapidly throughout 2024 and beyond. Trends we expect to see include:
These cybercrime trends require organizations to stay vigilant, proactively adapting their strategies and tools to counter emerging threats. Because dark web hacker forums strongly emphasize security and anonymity, security professionals and cyber analysts find it challenging to effectively track cybercriminal activities and threats on these platforms.
To overcome these challenges, Webz.io offers a stable and continuous flow of information from dark web forums and a tool to analyze that data. You can access deep and dark web data through our dark web API and perform detailed data analysis with Lunar. These tools help you easily investigate the illicit activities hidden in forums across the dark web.
Interested in learning more about how to monitor dark web forums?

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.