How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.
Dark web users have been recently excited about a new post-exploitation framework (PEF) known as “Exfiltrator-22” (aka “EX-22”), which was created by a group of hackers with deep knowledge of defense evasion and anti-analysis techniques.
The framework is designed to provide threat actors with a comprehensive set of tools and features that streamline the post-exploitation process and help them achieve their objectives more efficiently and effectively.
So far, this group who stand behind Exfiltrator-22 is promoting it on various spaces, including the known Russian dark web forum XSS, a Telegram channel, and a YouTube channel which the threat actors used in an attempt to attract prospective buyers:
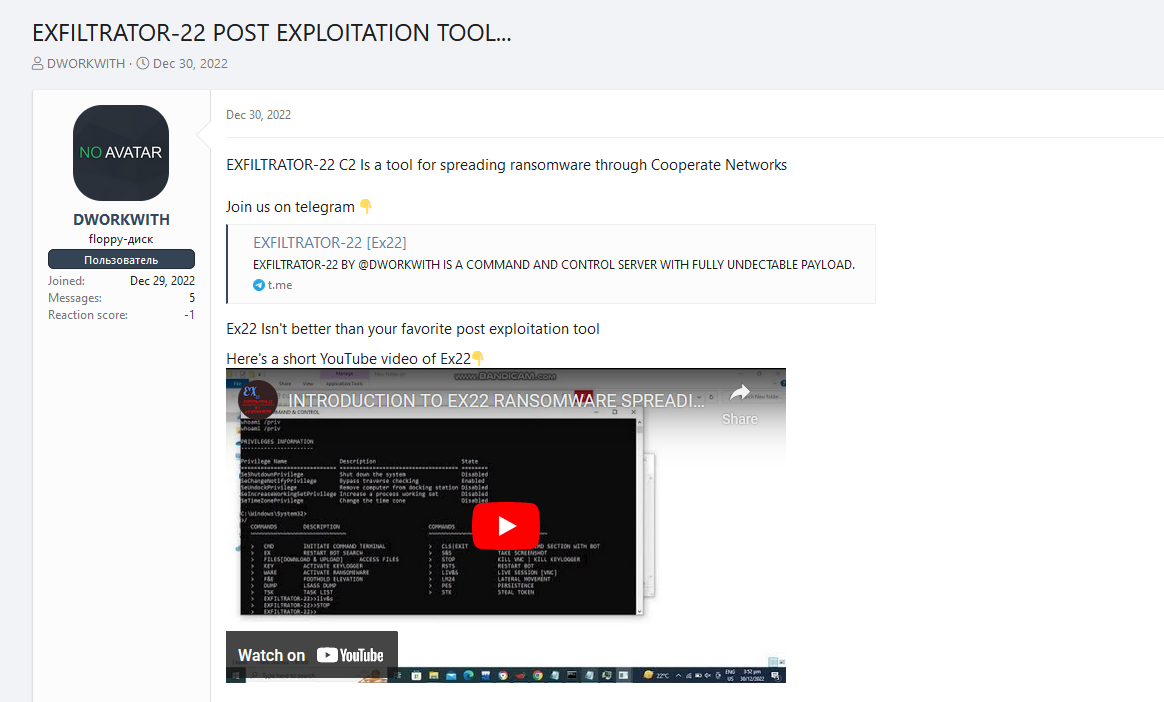
According to its creators, the framework’s primary goal is to enable hackers to remain undetected on target machines once they gain access to the system while expanding their reach throughout networks.
The payment model for Exfiltrator-22 is subscription-based, with buyers required to pay $1000 for a month’s access or $5000 for lifetime access. Once purchased, buyers get login details to access the tool, which is hosted on a bulletproof VPS. This framework uses domain fronting to conceal the cybercriminal’s communication and inject malware into the target host.
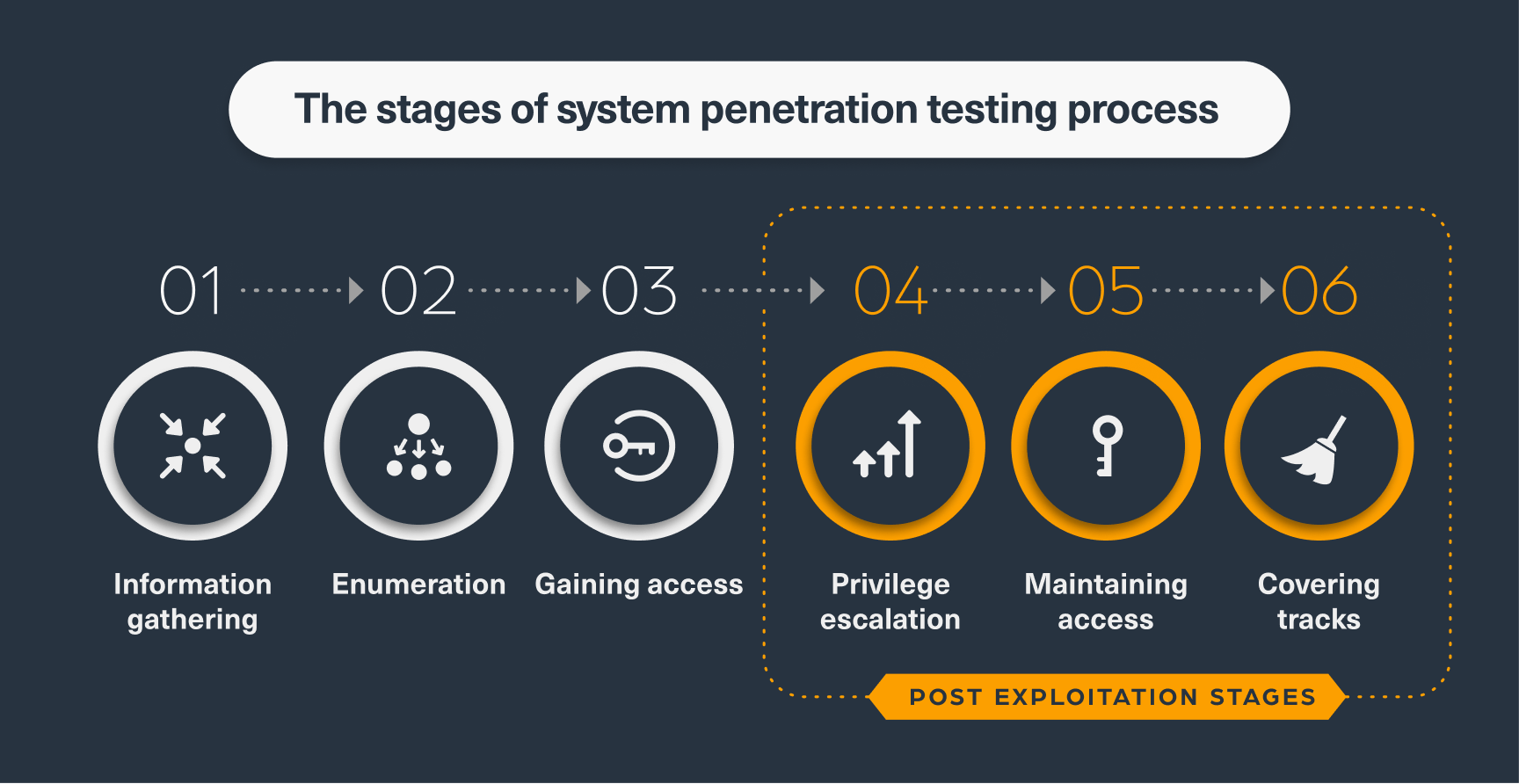
The term “Post-Exploitation” refers to any actions taken by a threat actor after successfully penetrating and gaining access to a system, such as maintaining access within the system or escalating privileges.
The chart below illustrates the different phases involved in a typical penetration testing process:
In the past, hackers used to create customized payloads to target different device platforms, such as Windows or Linux servers, and specific applications. However, the current trend is towards standardization, with threat actors largely relying on established methods that have already proven effective. As a result, over the past year, we have witnessed a normalization process of post-exploitation into standard platforms. Hackers no longer want to customize the exploit for each case but prefer to use standard tools that can quickly and easily leverage the exploit. Because the majority of targets are servers and mobile devices.
The increasing popularity of Metasploit for example, a freely available penetration testing framework used to test exploits in server environments, provides evidence of this trend.
We analyzed the number of times Metasploit was mentioned on the dark web and found a recent surge in mentions over the past two months (which can be seen in the next chart):
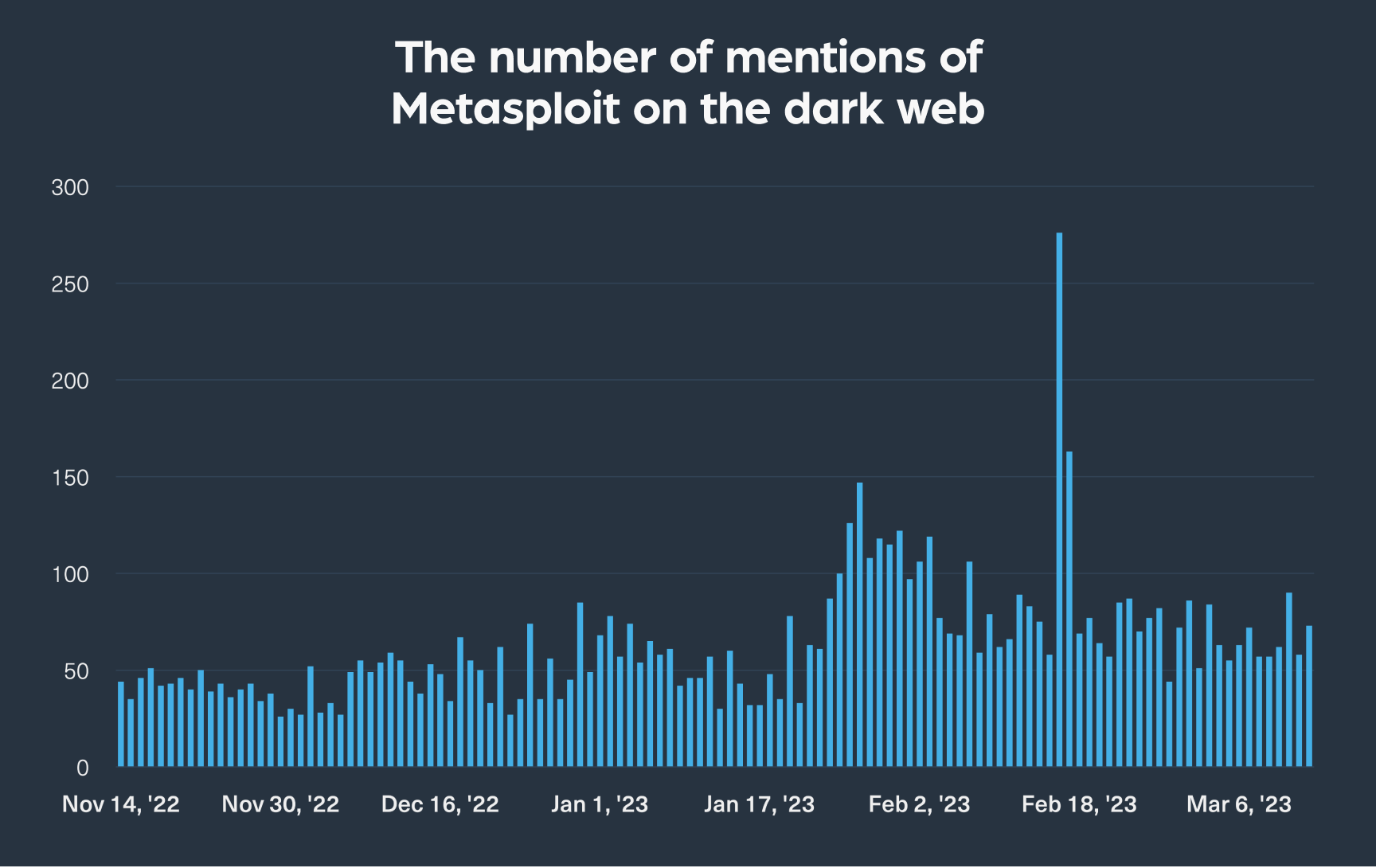
This trend indicates that threat actors are adopting standardized tools like Metasploit to streamline their post-exploitation activities, which enables them to launch cyberattacks more effectively and efficiently.
In the following image, you can see the top entities (organizations or platforms) and technologies (such as protocols, services, or others) mentioned on the dark web within conversations involving post-exploitation frameworks (PEFs):
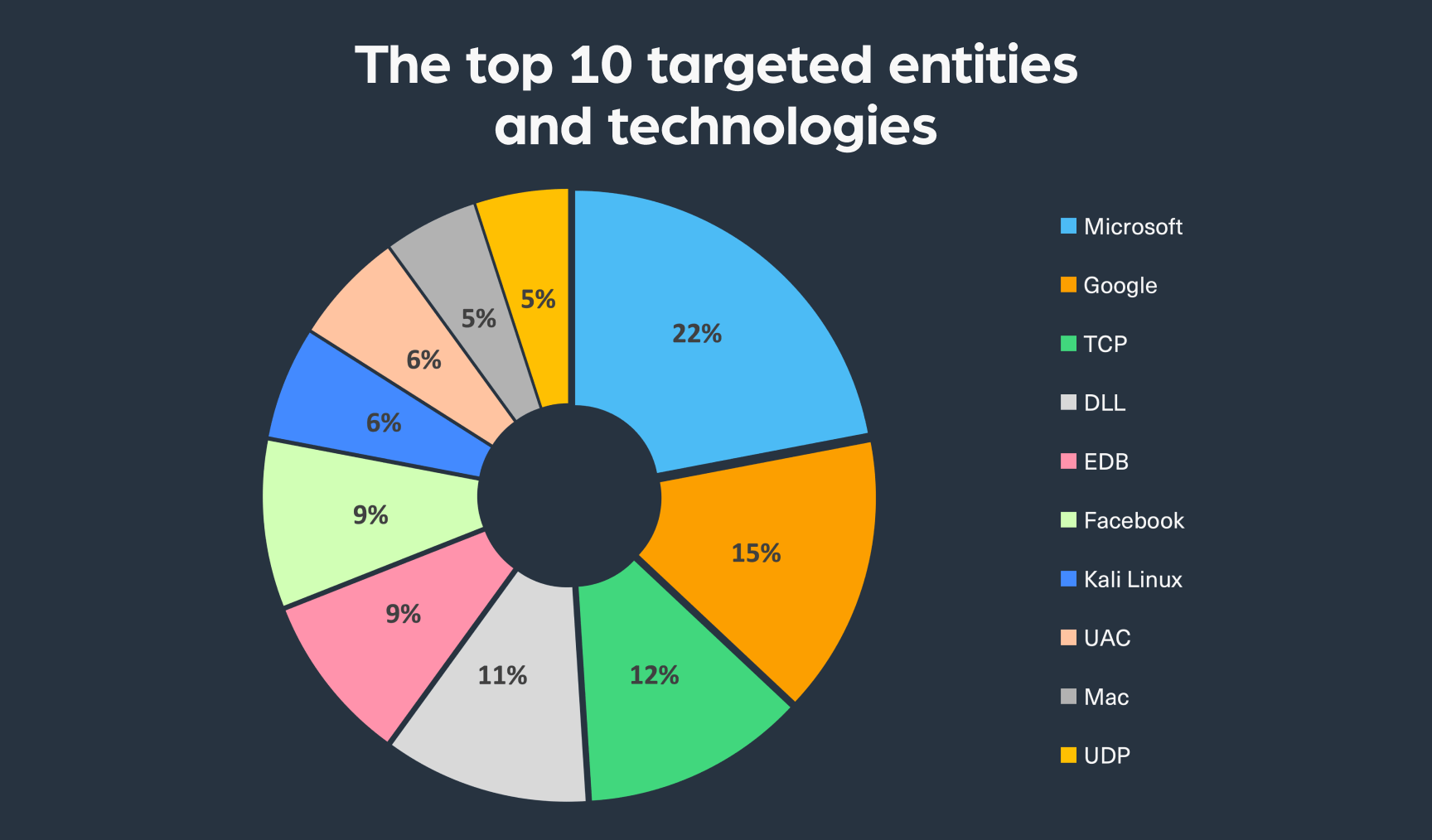
As can be seen, the list includes giant tech enterprises such as Google, Microsoft, Facebook, Apple, and other cloud infrastructure, which proves that nobody is safe from PEF attacks. Protocols are also mentioned on the list, which means that the data of applications using them could be at risk.
Metasploit, which is mainly used by pen testers to test different host machines by white hat hackers, is also sometimes misused by hackers with malicious intent.
For example, cybercriminals can use Metasploit’s tools together with open-source intelligence to identify and exploit zero-day vulnerabilities and eventually inject malware, such as ransomware, into the targeted host.
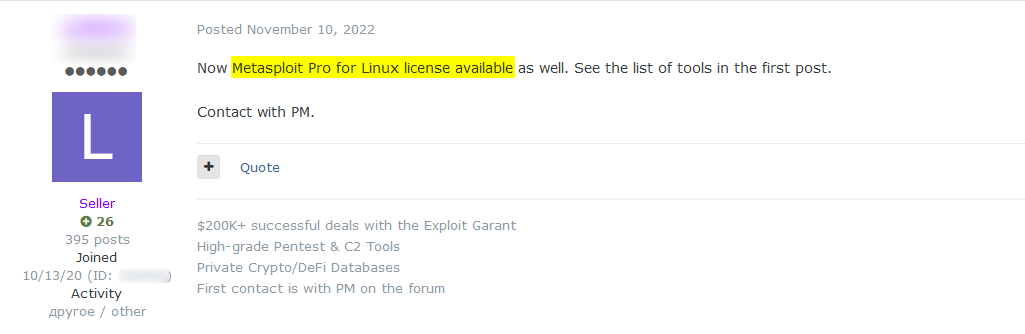
The following picture shows a recent example from Exploit hacking forum, where a threat actor is selling a license to Metasploit that can be used for hacking purposes:
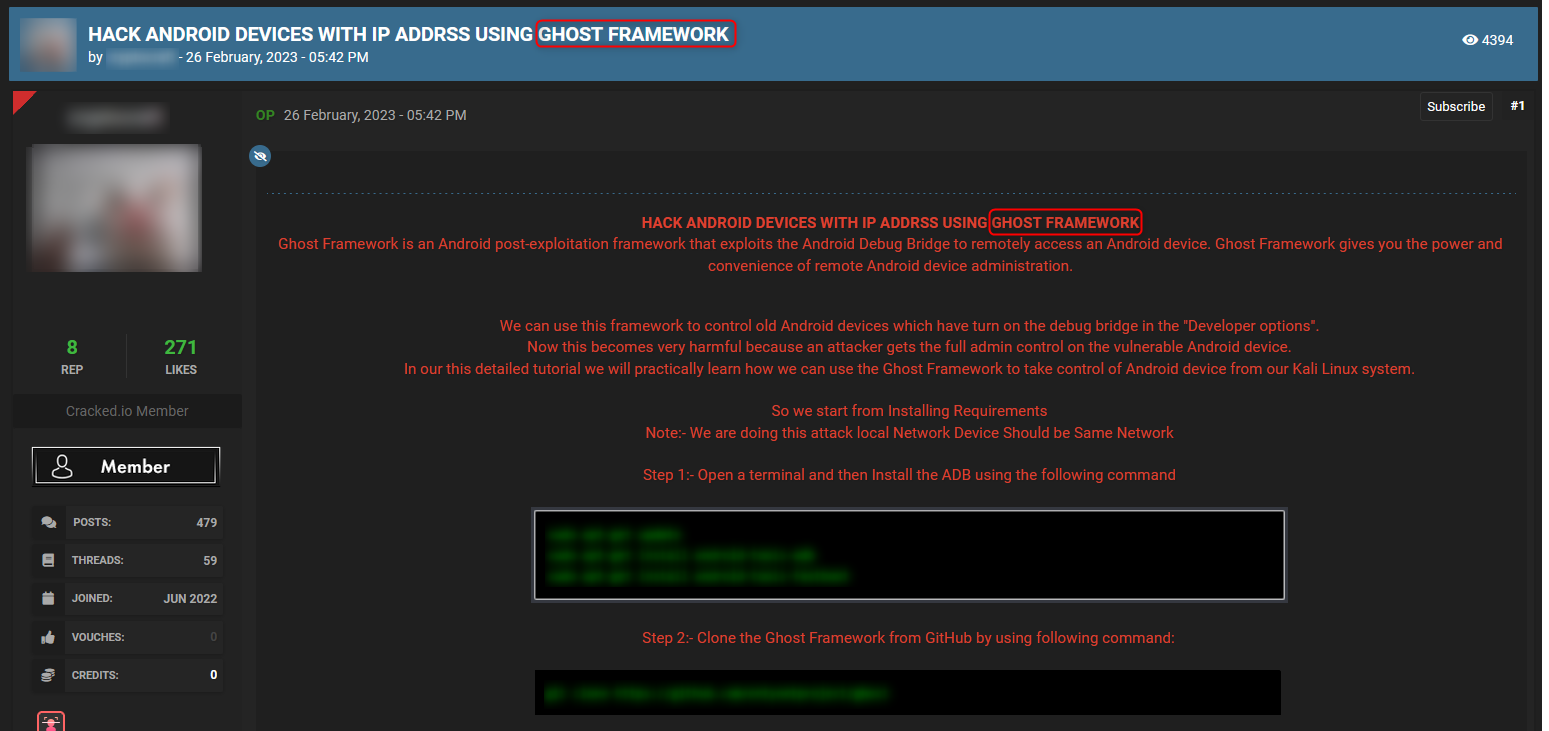
Ghost framework is an open-source post-exploitation framework that exploits the Android Debug Bridge to remotely access android devices.
The example below is taken from dark web hacking forum Cracked, where you can see a typical thread that includes a tutorial on how to use the framework for hacking android devices.
Early detection of such mentions can help organizations to prepare and defend against such threats, by better understanding the framework’s capabilities and the threat actors that are trading it.
PEFs are used to ensure stable communication with the targeted platforms and systems. They are used for various purposes, including:
With post-exploitation frameworks trending on the dark web in recent months, it is important to keep tracking their mentions and use them to gain meaningful early indications. These frameworks help hackers save resources when attacking, which means they are not going anywhere.
Often, the targets and the techniques threat actors are using are mentioned on relevant posts on the dark web. Threat actors continuously trade PEFs, tutorials, and the compromised assets they steal once they breach the targeted device. These can be detected with dark web monitoring to protect against planned attacks and mitigated the impact of already exfiltrated assets shared on the dark web.
Threat intelligence companies are using Webz.io’s Cyber API to help detect such malicious events in near real-time and mitigate the threat PEFs pose to organizations around the globe.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.