How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Two-Factor Authentication (2FA) is considered a key tool for protecting our online accounts. However, while 2FA aims to make our data more secure, it inadvertently opens the door to a new threat: SIM swapping.
SIM swapping, also known as SIM hijacking, is a cyberattack where threat actors gain control of a victim’s phone number by transferring it to a SIM card the attacker holds, thus diverting all incoming traffic onto the new SIM card.
Join us as we use Lunar, Webz.io’s dark web monitoring tool, to investigate illicit activity on deep and dark web networks.
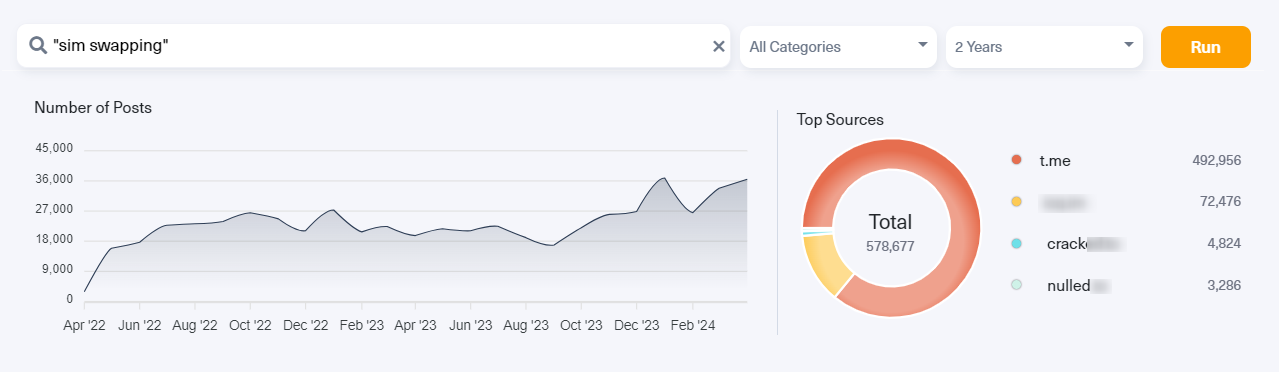
In order to execute this attack, the threat actor must be equipped with the victim’s personal information, such as full name, date of birth, living address, SSN, phone number, and carrier provider.
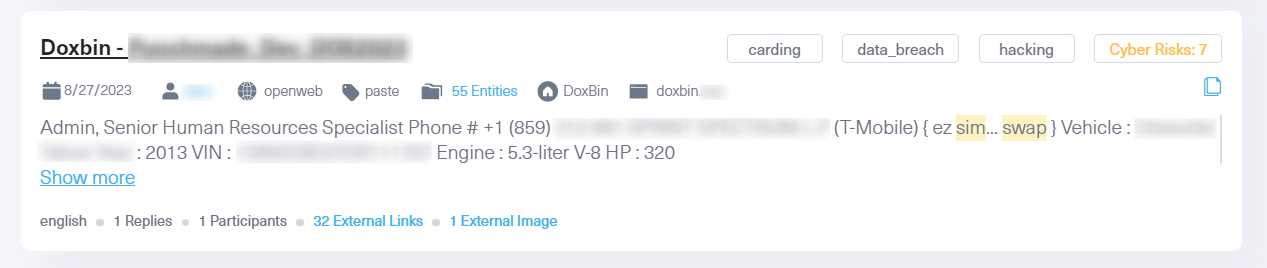
Armed with stolen personal information, hackers exploit vulnerabilities within phone carrier companies. Through sophisticated social engineering tactics, they impersonate victims and deceive customer service representatives into transferring the victim’s number to a SIM card wielded by the attacker.
A successful SIM swap grants attackers complete access to a victim’s digital identity, as many financial, social, and governmental services require connection to the user’s phone number.
A confirmation number by text is sometimes all that is needed to reset a password to a bank account. It only takes one successful attempt at sim swapping and some basic information in order to gain full access to a person’s bank account.
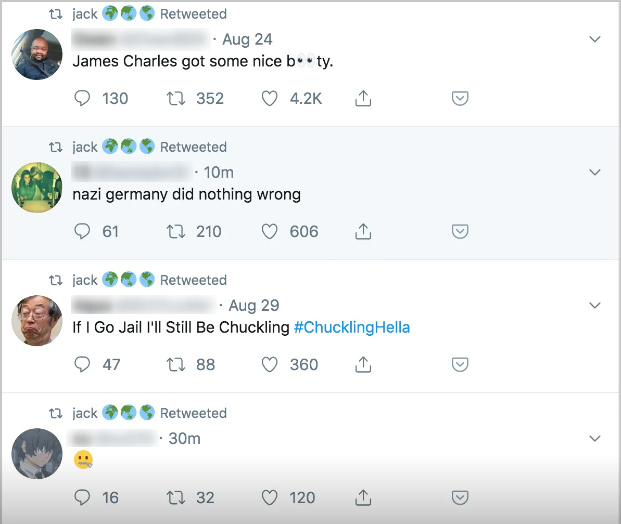
In 2019, former CEO of Twitter Jack Dorsey had his Twitter account compromised due to a SIM-swapping hack. The threat actor who took over his account went on to retweet a series of racist and offensive tweets. While eventually gaining back access to his account, the damage to his reputation had already been done.
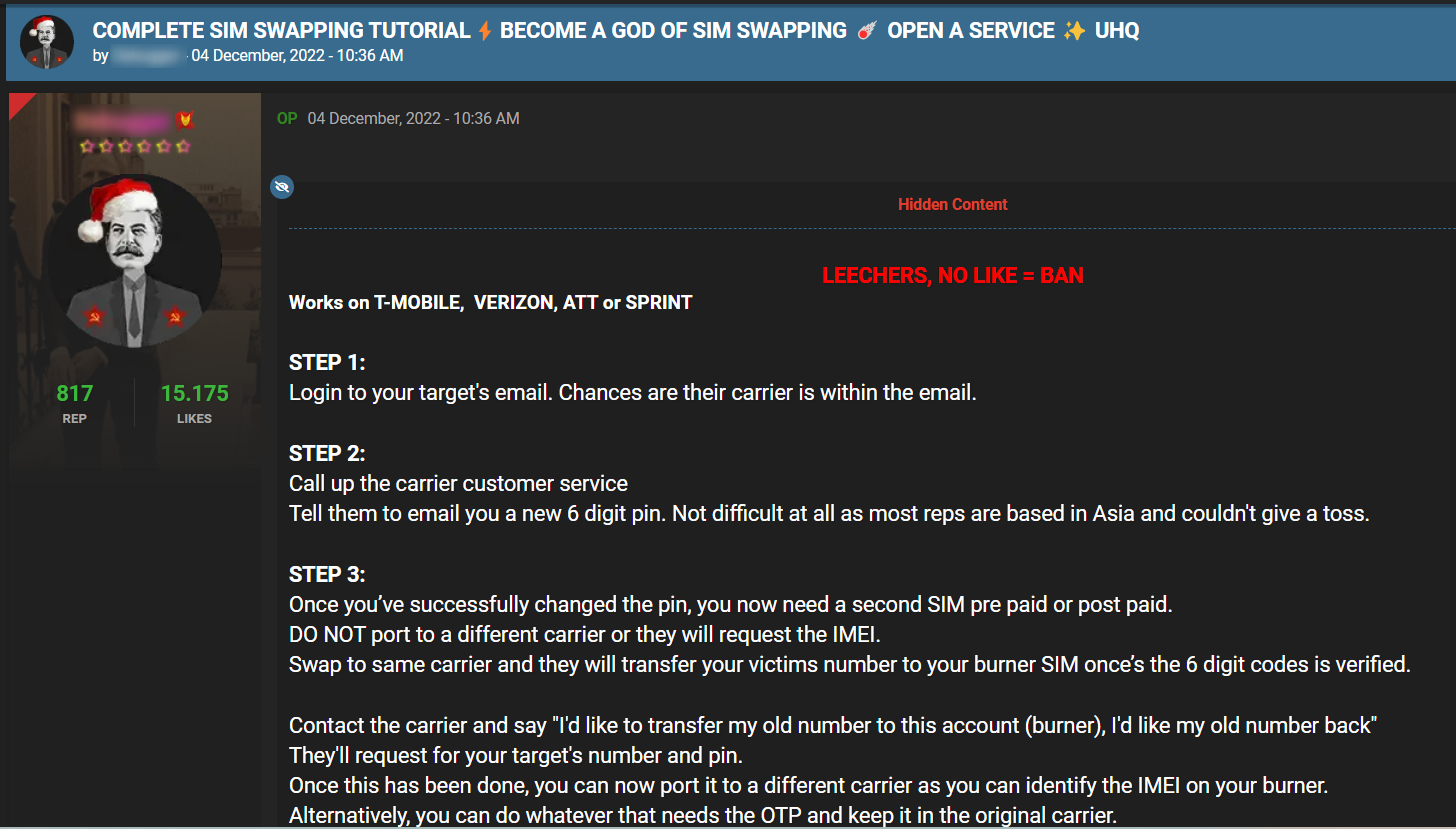
Threat actors involved with SIM swapping activities often to hacking forums, marketplaces, and fraud sites for various purposes. Here are some of the discussions taking place revolving around SIM-swapping attacks:
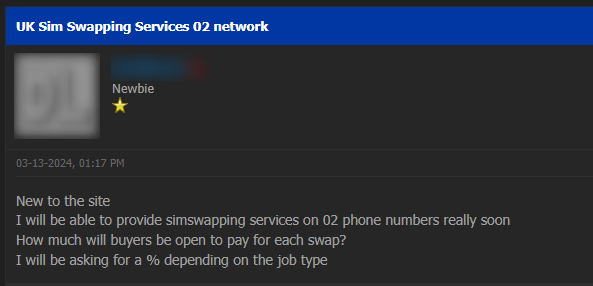
Vigilantly monitoring the dark web for signs of compromised personal information and emerging techniques is crucial in combating SIM-swapping attacks. Early detection can help prevent damage and protect individuals and companies from major financial losses. Lunar, our dark web monitoring tool, helps individuals and businesses combat cybercrime effectively. Offering real-time alerts, data breach monitoring, and extensive dark web surveillance, Lunar helps organizations remain proactive and secure in an increasingly challenging digital landscape.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.