How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

In today’s digital landscape, the threat of cyber attacks is more pressing than ever. With the average cost to the company who has experienced a data breach is $4.45 million (IBM Cost of a Data Breach report) and the volume of cyber attacks over the past few years has increased by 30% every year (Check Point Q2 2024 cyber attack trends).
By monitoring the dark and deep web, we are able to find the tools and kits used by hackers to conduct these attacks to compromise companies, individuals and brands for their personal gain. We search for these potential threats to safeguard regular, respectable, businesses.
We can find hacking tools on the following types of sites:
Today we’d like to split cyberattacks based on the following:
There are many hacking tools on the web but in this review, we will discuss some of the most common tools out there: malware, ransomware, phishing, DDoS attacks, spoofing, supply chain attacks, DNS tunneling, and code injection .
So let’s start.
Malware (short for “malicious software”) refers to software (such as viruses, trojans, and other destructive programs) used by attackers and threat actors to infect systems and networks. These computer programs are designed to interfere with a computer to carry out virtually any action an cybercriminal desires – exploring, stealing or conducting any behavior on the network of their target.
Theft of sensitive data such as financial details, credentials, sensitive corporate information or PII.
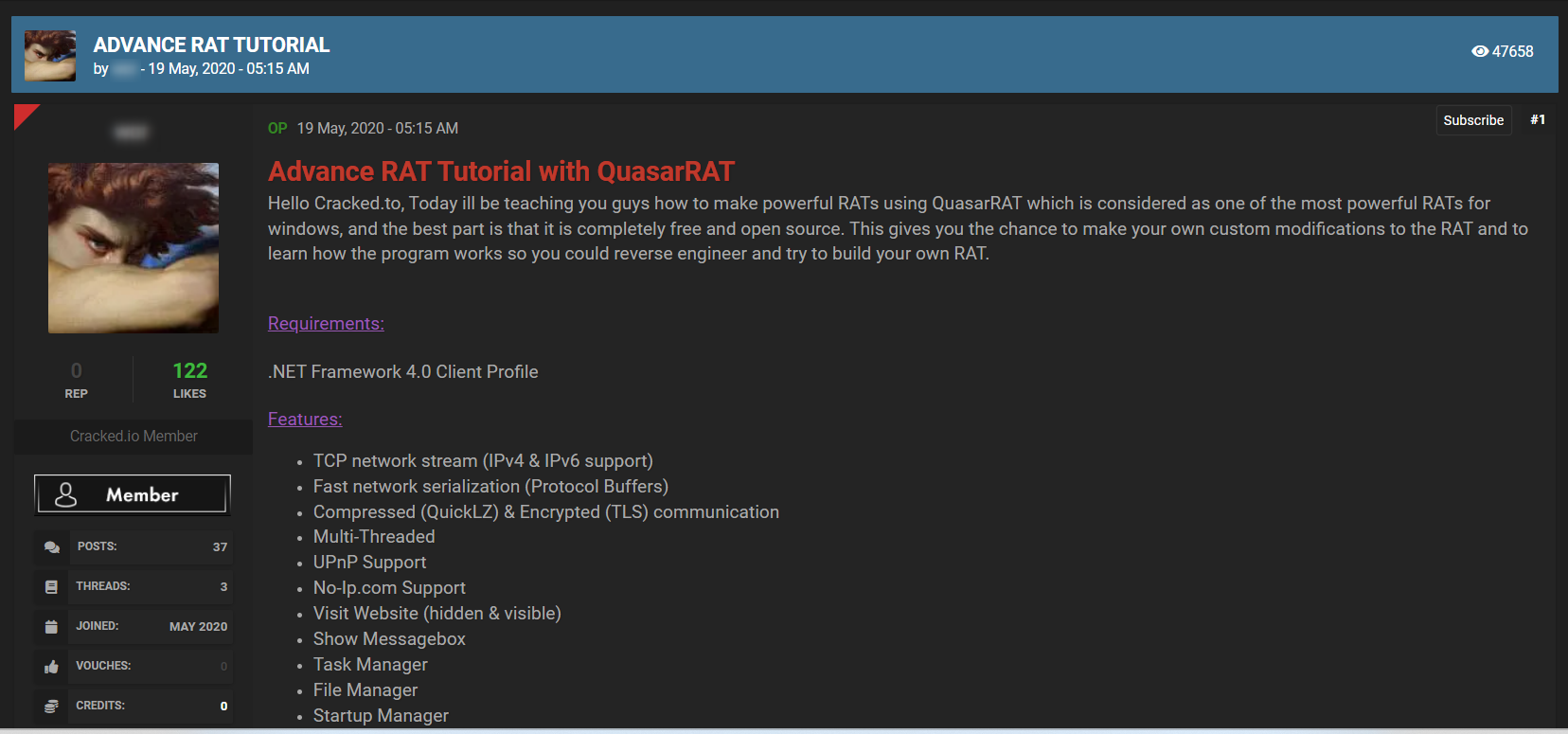
A RAT (remote access trojan) is a type of malware that enables hackers to remotely control a computer that was already infected with the malware. After the RAT is installed on a compromised system, the attacker can send commands to it and receive stolen data in response. The RATs can be attached to emails, hosted on a malicious website, or exploit a vulnerability in an unpatched machine. RATs pose a high risk because they provide the attacker with a high level of access control over a compromised system. This type of malware provides the same level of functionality as legitimate remote system administration tools making it easy to confuse.
The hacker can achieve almost any objective on the infected system, including downloading and deploying additional functionalities necessary to achieve their goals.
RATs are usually discussed on dark web hacking forums and on chat applications such as Telegram.
RATs can often be bought at a low price, and sometimes for free, making them extremely accessible for any cybercriminal who is looking to gain access to a remote system.
Ransomware is a malware designed to prevent users or organizations from accessing files on their computers. By encrypting files and demanding a ransom payment for the decryption key, cyberattackers force organizations to pay ransoms in order to unlock their files and data. Various ransomware variants have added additional features, such as data theft, to provide victims with a further motivation to pay the ransom.
Data theft and leakage, money loss, and other vulnerabilities that were created following the leak of the data.
Ransomware tends to be more expensive than different vulnerabilities offered for sale. They can cost hundreds and thousands of dollars. However, their popularity among threat actors and cybercriminals makes them accessible and very easy to find on the dark web.
A threat actor posting on DarkWeb Forums that he hacked eight different domains using ransomware, offering the data he stole for $350K
Phishing is a type of cybersecurity attack in which malicious actors pretend to be someone they are not. Phishing is a type of social engineering, which is a generic term used to describe attempts to manipulate or trick computer users. The hacker’s method in this case is accessing the target from the least expected and suspicious platforms – any platform the targeted victim, usually an employee, uses – including social media platforms such as LinkedIn and Instagram, email service providers, etc.
Influencing a user to install malicious files, click on malicious links, or share sensitive information such as credentials, scripts, PII, credit card information, etc.
Many phishing tools can be found on Hacking forums, and chat applications such as Telegram and dark web marketplaces.
Can be shared for free or sold for less than $10.
Phishing pages and services offered for sale on different dark web marketplaces such as DrunkDragon and GoldApple
A DDoS attack works in the same way as an unexpected traffic jam preventing regular traffic from reaching its destination. When there is too much traffic in the same place the server gets overloaded and slows down, increasing load times to the point where the browser times out. DDoS attacks are malicious attempts to disrupt normal traffic on a server, service, or network by flooding the target with internet traffic. The effectiveness of DDoS attacks is achieved by using a large number of compromised computers. When a victim’s server or network is targeted by a botnet (a network of computers infected with malware used by threat actors), the botnets send requests to a victim’s IP address in order to overload the server or network, and by that causing a denial-of-service to normal traffic, which blocks the flow of information across the network.
This attack blocks the access to the site.
DDoS services and tools are offered for sale on dark web hacking forums, marketplaces and chat applications.
You can find various types of DDoS services available for purchase. Some tools are available for free on hacker forums, while others can be bought on marketplaces for a few dollars. Another option is to hire a professional or purchase access to a botnet—a network of infected computers used to carry out the attack—which can cost anywhere from tens to hundreds of dollars. These options are primarily found on Telegram, and less commonly on social networks like YouTube.
A spoofing attack creates a fake website that is identical to a trusted brand’s website. The goal is to trick existing customers, suppliers, employees, and partners into interacting with the spoofed domain. Threat actors lure victims through phishing emails, smishing, social media impersonation, paid search ads, and even QR codes to the spoofed sites where users are prompted to enter PII, login credentials or payment details. Attackers typically host cloned websites on compromised servers or unreliable cloud services, making it harder for cybersecurity personnel to take down the fake website.
The company is not aware that their website has been spoofed until someone reports it or realizes that the analytics don’t add up. The cost of a spoofing attack rises as the window of exposure grows longer.
There are phishing kits and website cloners available for purchase on hacker forums, Telegram, and marketplaces. The prices are based on the type of the kit/cloner and can vary from tens to hundred of dollars.
Posts from a WeTheNorth market, offering RATS for purchase.
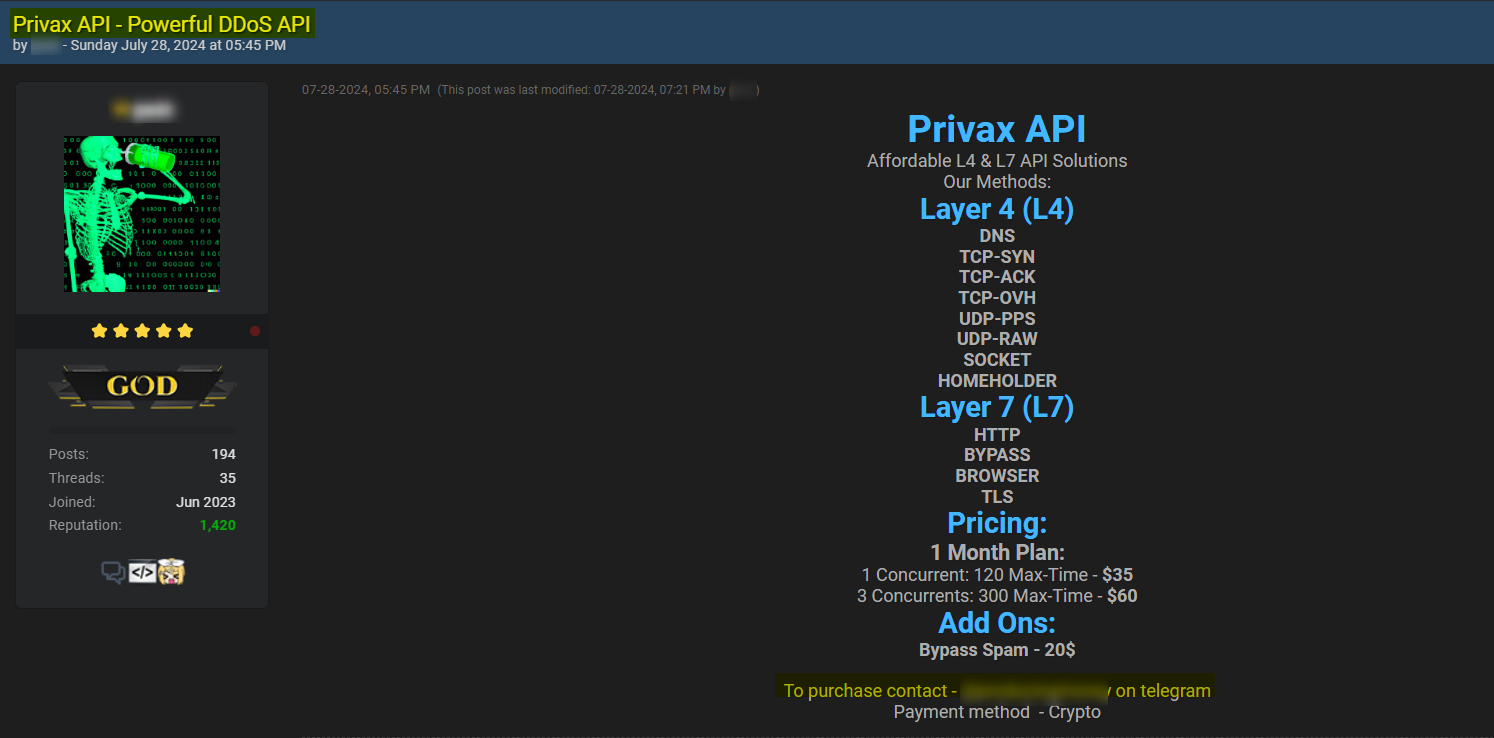
A supply chain attack is a cyberattack that exploits vulnerabilities in third-party vendors to infiltrate larger networks. Software supply chain attacks are when malicious code is embedded into widely used software components. This is particularly concerning because modern software development heavily relies on third-party APIs, open-source libraries, and vendor-supplied code. A single compromised component can lead to widespread breaches, affecting countless businesses. Additionally, the reuse of software across different projects means that vulnerabilities can persist, posing long-term risks to organizations.
Here are some common threats to your company’s software supply chain:
The risk of software supply chain attacks can be profound: a single compromised dependency in a widely used application can result in the compromise of every business that uses it. Possible outcomes of using vulnerable software include leaking credentials or confidential data, corruption of data, installation of malware, and application outages.
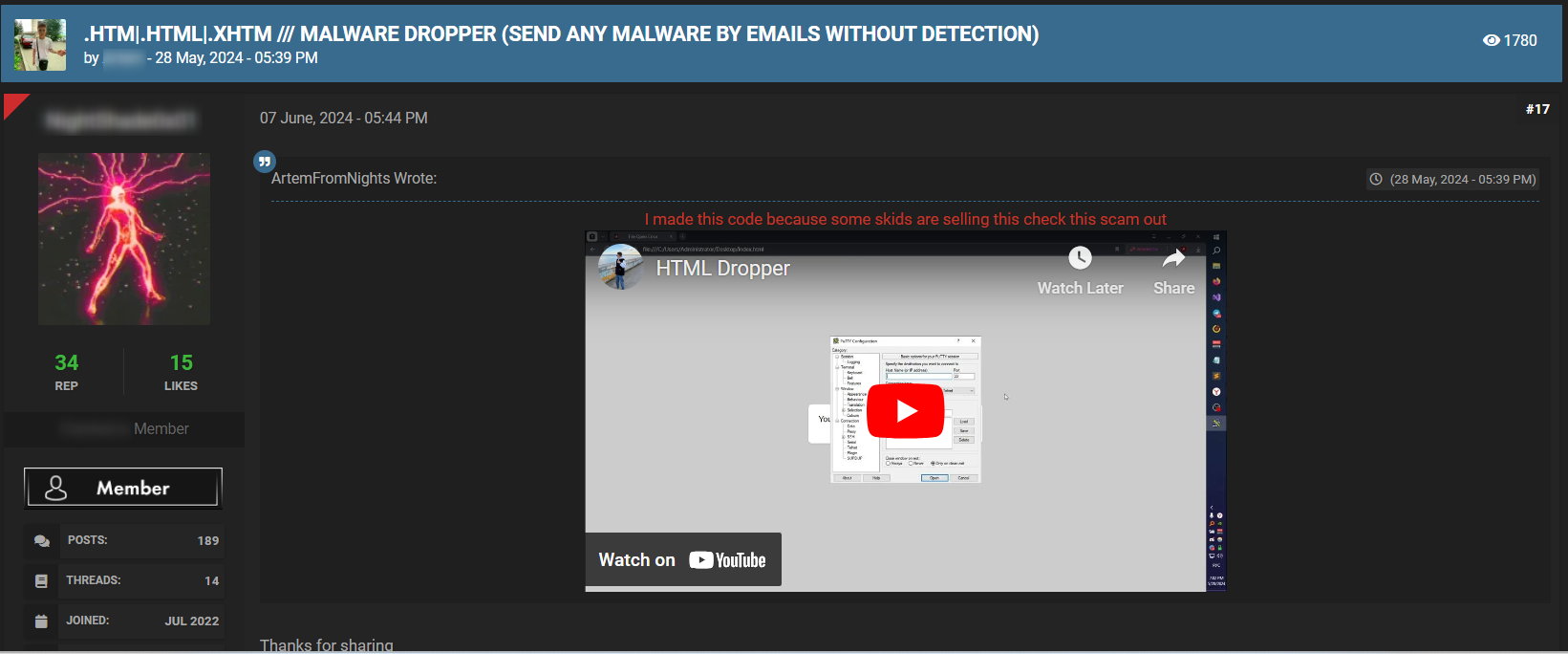
Various tools and methods are employed in these attacks, including code injection tools, credential stealers, malware droppers, and more. These tools can be sourced from hacker forums, Telegram channels, paste sites, marketplaces, and other platforms. They are available both for free and for purchase, with prices ranging from tens to thousands of dollars, depending on the tool and method used.
Finding dark or deep web hacking tools and vulnerabilities can be easy for those who know where to look. Many of these tools and services are free and cheap which means hackers can gain access to login details and PII with very little cost. This means that cyberattacks are no longer limited to so-called “professional hackers”. With the plethora of cyberattack guides, tutorials, and scripts available on the dark web, anyone who has the will and time to enter the dark web can acquire the tools needed to launch a cyber attack. This is why the deep and dark web have become the frontier that every company needs to guard to protect its brand, reputation, data and employees.
Discover how to use Lunar, by Webz.io, to monitor the dark web for hacking threats today.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.