How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Malicious insiders are people with lawful access to internal tools, information or systems within an organization who intentionally abuse this access (using legitimate credentials) for financial or personal gain. Malicious insiders are often current or former employees, contractors or business associates.
The main motivations behind the activity of malicious insiders are:
1. Unsurprisingly, most malicious insiders are motivated by financial gain.
2. Some malicious insiders conduct corporate espionage for a competitor or for nation-state espionage.
3. Other malicious insiders look to harm their employer for personal reasons or revenge.
Because the majority of malicious insiders using the deep and dark web are motivated by financial profit, we decided to find out what we can learn about them.
Insiders who look to make profit are either using their legitimate access to offer fraud services or sell the raw sensitive information they are able to access to a third party. That sensitive information might be intellectual property belonging to a company, confidential customer information like PII and other classified data.
Malicious insiders use the deep and dark web to discuss and share information they obtain.
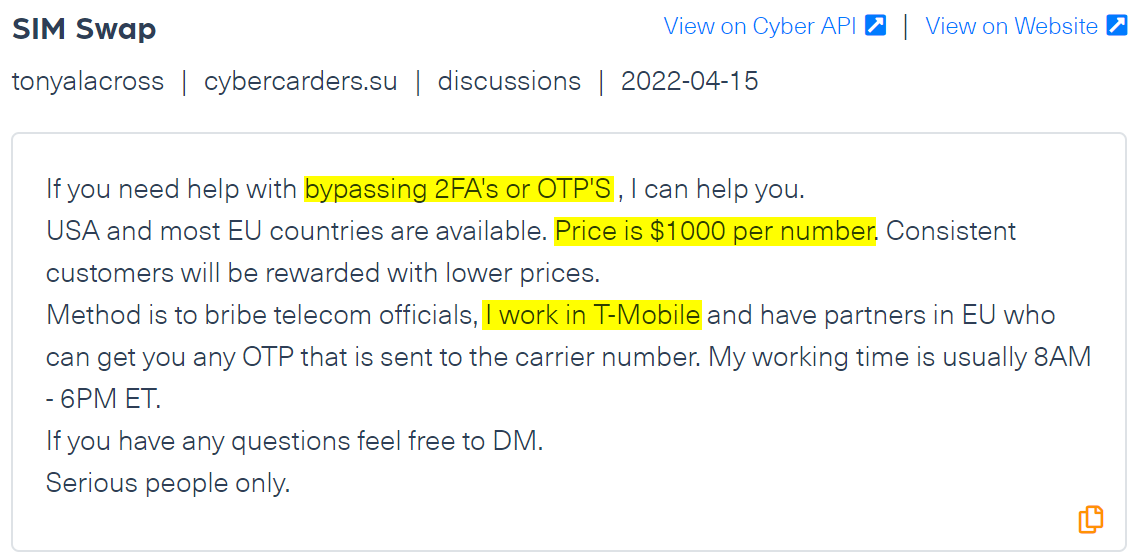
Take for example the following post from a carding forum. A T-Mobile employee offers threat actors access to the company’s system in order to bypass multi-factor authentication systems, in this case 2FA and OTP, and by that gain access to the devices or accounts of victims. The malicious insider charges $1000 for his services and explains his method of work – literally stating that this would be a bribe.
One of the most targeted industries by malicious insiders on the dark web is the financial industry.
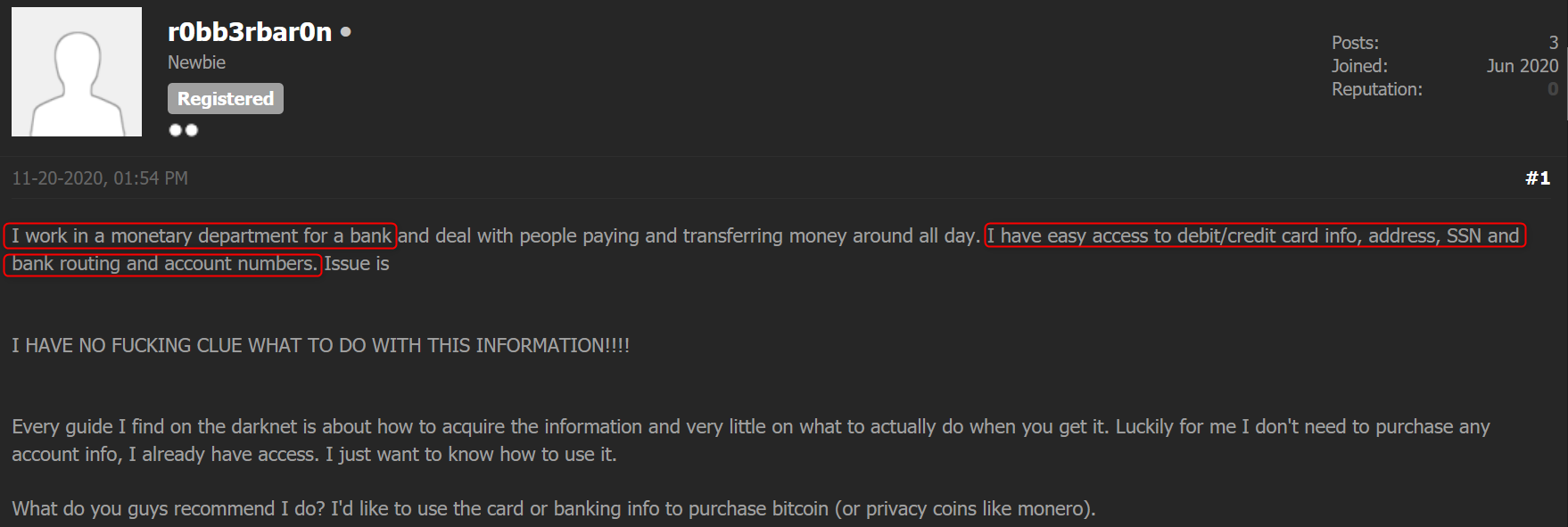
Below you can find a post published on the CryptBB carding forum, where a business associate of an unnamed bank says that he has access to PII such as debit and credit card information and SSN. He is asking for an advice from other forum members as he doesn’t know what to do with the information he has:
Companies of all sizes invest a lot of time and effort into monitoring external threats that can harm them, but many ignore the threat malicious insiders pose to their financial health and reputation.
Using Webz.io’s Cyber API, organizations around the world monitor these types of threats, which are often hard to detect, whether it is because of their elusive nature or the need for deep contextual data to spot the threat. As many of these threats are invisible to traditional security systems, it is important to be able to monitor the organization’s assets on the deep and dark web, a prime space for malicious insiders to trade and discuss their intentions and the sensitive information they obtain.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.