How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Cybercriminals increasingly favor IM platforms like Telegram over traditional dark web forums and markets. Over time, threat actors have recognized the advantages of these apps, using them to communicate, share information, and distribute malicious content.
Much like dark web sites, dark web Telegram channels facilitate a range of criminal activities, largely due to their real-time communication capabilities and privacy features. Cybercriminals leverage instant messaging apps for illegal trade of drugs, malware, and stolen data, money laundering, and discussions about hacking methods.
Additionally, extremist groups have adopted these communication apps to promote their ideologies, disseminate propaganda, and drive others to act on behalf of their cause.
There are several reasons cybercriminals are drawn to instant messaging platforms. Let’s take a look at the top five factors.
It is worth noting that we have seen a drastic increase in the usage of IM apps over traditional dark web sites and marketplaces, especially Telegram black markets.
Due to the advantages and the ease of use of those apps, even to a level where some known forums now operate only on Telegram and ditched the dark web completely.
Of course, there are still those who continue to use both platforms and share their IM account details on dark web forums, either in their profiles or as part of their signatures to “catch” every user they can as potential clients or consumers.
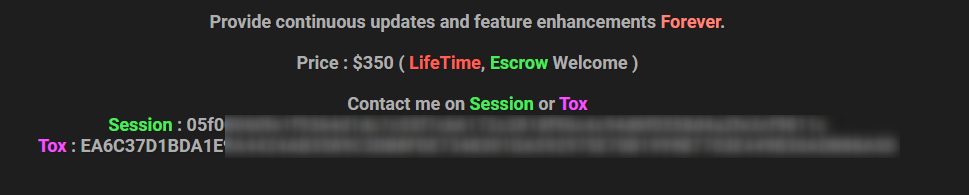
For example, take a look at the following screenshot, taken from a hacking forum. The poster includes contact information for the chat applications Session and Tox.
Since Telegram is one of the most popular chat applications among cybercriminals, we’ll take a closer look at examples we found by using our Cyber API that show how threat actors use both dark web sites and Telegram for their illegal operations.
In the following example, a vendor listed the illegal drugs he is offering for sale on one of the well-known dark web markets, which specializes in drug trafficking. The cybercriminal lists his drug offering, along with his illegal Telegram account and other IM apps which potential buyers may contact him via those, for negotiation purposes.
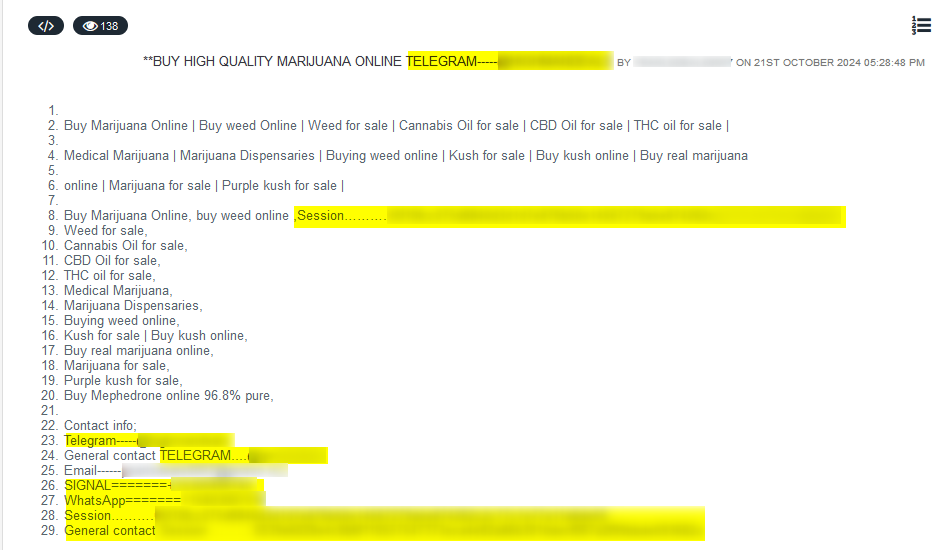
We can use his Telegram username to search for other posts he has written on different Telegram groups and channels. Using the information we gathered from the threat actor’s activity on the dark web and Telegram we can create a threat actor profile for our records.
There are many cybercriminal groups who are responsible for conducting cyberattacks from DDoS and ransomware, to frequently leak the data they steal. As this practice has become more common in recent years, the reliance on IM applications and dark web Telegram channels among these groups has dramatically increased.
These platforms enable cybercriminals to communicate privately with victims and facilitate negotiations. Groups and channels are used to announce future attacks, recruit new members, and distribute or sell compromised databases that have already been obtained.
In the following example, we can see a screenshot we took from a dark web Tor site using Lunar, in which the known ransomware group called K1llsec calls their followers to contact them by IM applications such as Telegram and Tox.
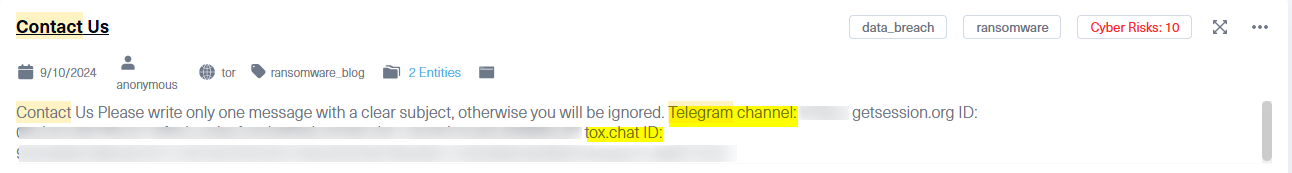
As we wrote in previous Dark Web Pulse posts, many other cyber-criminal groups, such as RansomHouse, Arvin Club, Lapsus , BlackShoadow, GhostSec, Moses Staff, and more, use Telegram.
Like we wrote in previous Dark Web Pulse posts, there are many other cyber criminal groups who use Telegram, such as RansomHouse, Arvin Club, Lapsus , BlackShoadow, GhostSec, Moses Staff and more.
Administrators of hacking forums also manage groups and channels on chat apps. On this channel, the admins publish updates related to the forum and other new and interesting topics that are being discussed, published or items that are sold on the forum. This allows them to extend their influence, engage with a wider audience, and facilitate real-time communication within the cybercriminal community.
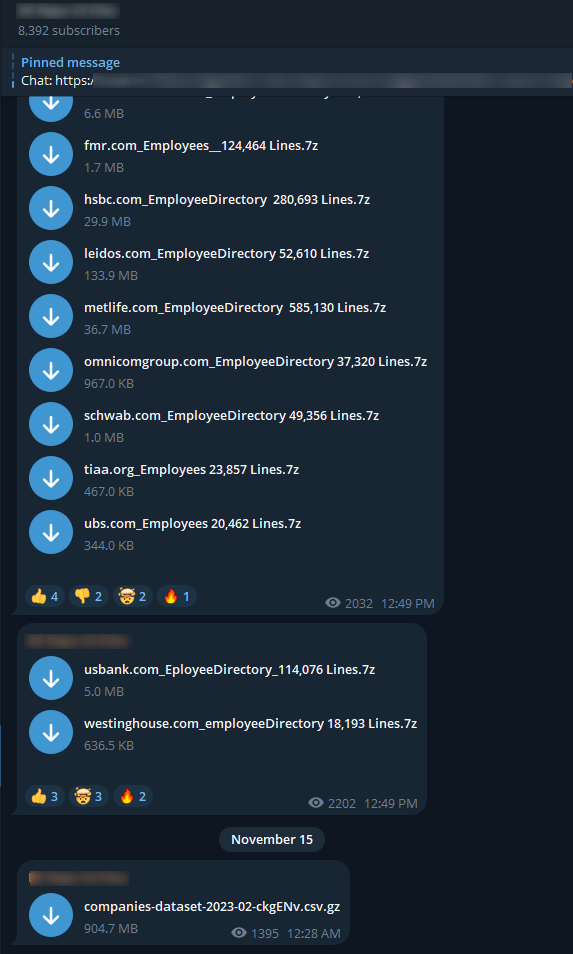
For example, a known Telegram channel in the hacking community operated by the name BF Repo V3 Files that constantly stores and shares backup files from data breaches, if talking about leaked passwords, combos (including email addresses), KYC, ID screenshots, or even full documents belonging to a country or a company.
The screenshot below was taken from that channel, containing sensitive data from various sources, from private companies’ employees and banks. This data may be very useful for attackers who wish to target those companies by using phishing techniques, identity theft, or even physical harm.
Over time, chat apps have introduced numerous new features, making these platforms more user-friendly and accessible. As these apps become a major tool for cybercriminals, monitoring them alongside dark web sites has become crucial as part of seeing threats before they harm your organization.
Monitoring Telegram using a dark web monitoring platform is a strategic approach to keep track of potential threats, sensitive data leaks, or malicious activities targeting an organization.
Dedicated and comprehensive solutions such as Lunar, uses specialized algorithms and scraping approaches to scan and monitor public and semi-public channels or groups on Telegram.
Using Lunar, it’s possible and even crucial to monitor Telegram chats and set alerts. Here are some of the recommended alerts to set:
When you come across an alert, it’s important to assess the credibility and potential impact and react immediately, depending on the alert. There are various use cases, let’s review some of them:
We collaborate with top-tier MSSPs (Managed Security Service Providers), MDRs (Managed Detection and Response), DRP (Dark Risk Protection), WEBINT, crypto protection, CTI (Cyber Threat Intelligence), and IT (Identity Theft Monitoring) teams to deliver the most relevant data from deep and dark web sites, as well as chat applications, in near-real time.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.