How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Flagstar Bank, one of the largest financial service providers in the U.S., has only recently discovered that it had suffered its second data breach in two years – in late December. The breach is said to affect 1.5 million customers, leading to a class action lawsuit.
The first breach took place in early 2021, when Cl0p ransomware gang attacked and published the data they had stolen from Flagstar on their blog:
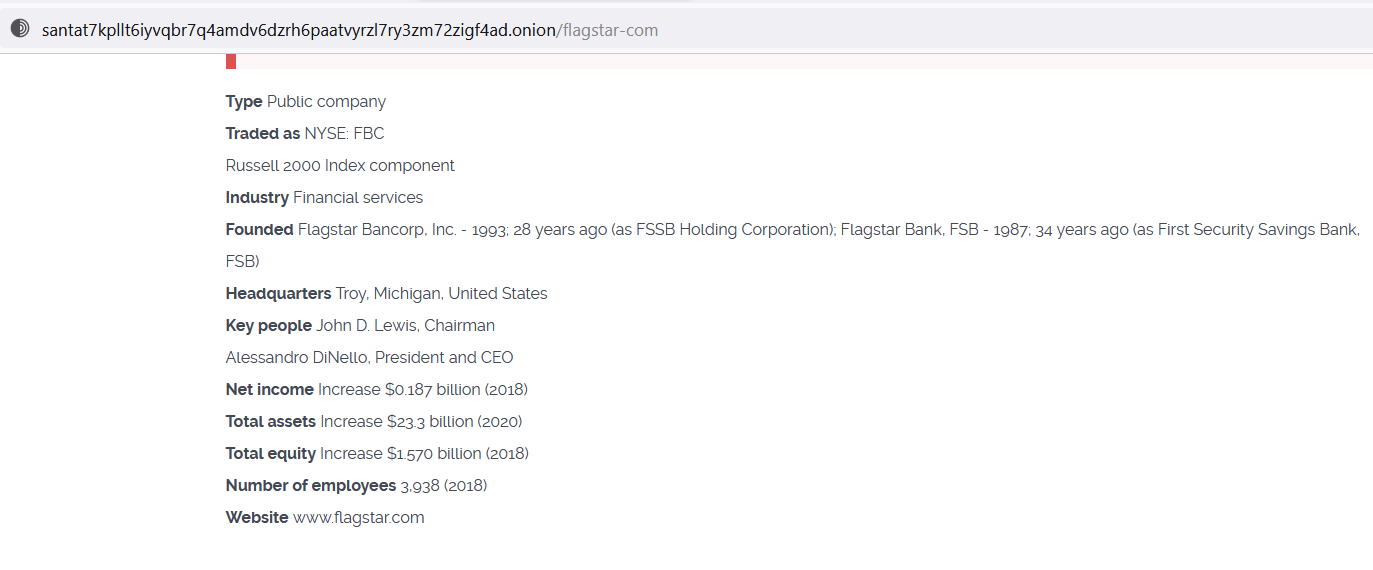
To be able to carry out the type of large scale breaches such as the two Flagstar Bank experienced over the past two years, the threat actors will usually look for ways to access the bank’s systems. One of the easiest ways to do that is by using employee credentials, especially ones with clearance to sensitive information.
By using our Cyber API, we found several indications that credentials belonging to Flagstar Bank employees were leaked and offered for sale on the deep and dark web before the latest attack.
Each one of these compromised credentials could have been used to breach the bank.
Paste sites allow users to share plain text through public posts called “pastes.”
Most of the content people publish on these sites is legal, such as coding texts. But today, these sites are widely used in the cybercriminal community since they allow sharing information easily while remaining anonymous. They regularly use these sites to leak compromised credentials. That’s why monitoring different paste sites across the deep and dark web helps companies track their leaked digital assets.
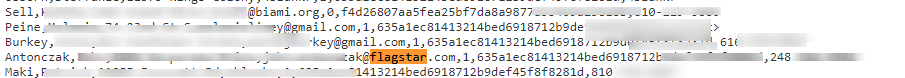
Take for example Flagstar. We searched for mentions of related information and found a leak (see below that was published on controlc.com in May 2021. We found 8K leaked entity information, including names, addresses, emails and more. One of them was of a Flagstar email domain.
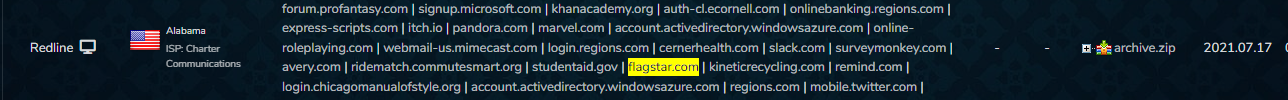
There are dozens of marketplaces operated by cybercriminals that are dedicated to selling credentials: cookies, login details and more.
In the image below, taken from Russian Market, one of the top marketplaces for the trade of stolen digital fingerprints, we found a Flagstar login for sale:
We have detected dozens of similar posts, all were posted before the attack, any of them could’ve been used by the attacker to gain access into the bank’s systems.
We used our Data Breach Detection (DBD) API, which helps tracing leaked entities from data breaches, in order to search for Flagstar email domains that may have been compromised. The result we received included 1,024 compromised email entities belonging to the organization.
Since these leaked databases are freely accessible to hackers on the dark web, they could have easily been used to breach Flagstar’s system.
Here’s one example out of the total 1,024 compromised emails we found:
We also used our Cyber API to see if we could find other mentions of Flagstar in cybercriminal communities on the deep and dark web.
We could see thousands of mentions of the bank in the cyber API from over the past two years. Most of them are related to trading or leaking the bank credit cards and bank accounts. Here’s one post for example, where a Flagstar credit card is leaked on a carding forum:
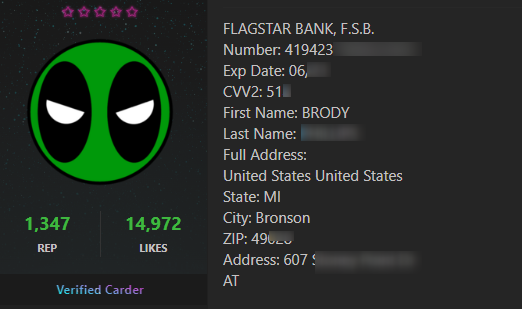
The next example is from a leaked credit card that is offered for sale on a dark web marketplace:
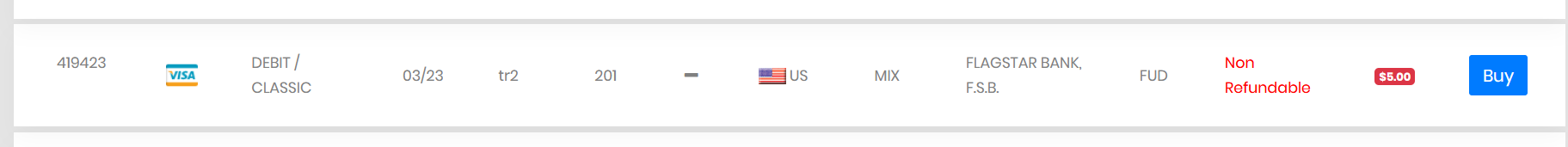
We regularly see these types of bank information traded on the dark web. But what’s interesting about these two examples is that they are not part of a large-scale leak. That may imply that they were probably obtained from phishing or stealer malwares. They are not a part of a massive data breach, like the breaches mentioned above. And finally, most of these posts offer stolen credentials that belong to the bank’s clients, and are mainly used for fraud.
By using Webz.io’s Cyber API and Data Breach Detection API, we were able to identify compromised data that could have been used to gain access to the system of Flagstar. Monitoring these types of mentions and information is key to preventing and mitigating future risks.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.