Dark Web Data: A Comprehensive Guide
Learn all about dark web data in our full guide. We cover what dark web data is, how to access it, how to collect data from the dark web, and how to analyze it.

Over the past year, the number of cyber attacks has continued to grow, and today, according to the Cisco Annual Cybersecurity Report, attackers can launch campaigns without human intervention.
With the threat landscape always changing, it is always important to constantly monitor for new attack vectors. Our cyber team dived deep and using our Cyber API, we found the most popular attack vectors mentioned on the dark web in 2021:
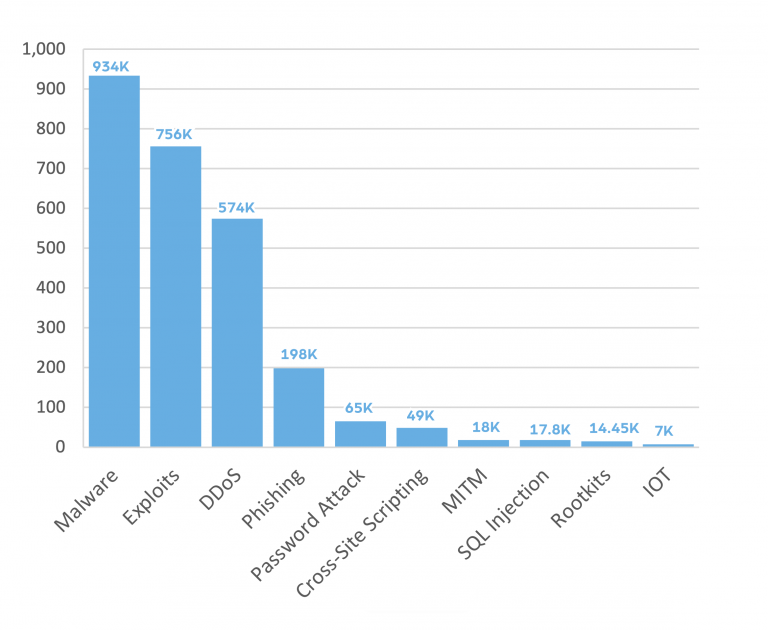
According to our data, the top 3 attack vectors are malwares, exploits and DDoS attacks. We see malware, a malicious code in the form of virus, ransomware, spyware or others, traded in the dark web on a regular basis. In the image below you can see a post we found on Raidforums, in which a threat actor is looking to gain access to a malware:
Malware, exploits and CVEs are basically malicious code that are executed on an organization’s assets such as: servers, PCs, or mobile devices. Any one of them is considered as a high risk to an organization. Cybersecurity, brand protection and threat hunting solutions monitor the dark web to track these indications, assess their level of threat and when needed, take action to protect the organizations they are monitoring.

Learn all about dark web data in our full guide. We cover what dark web data is, how to access it, how to collect data from the dark web, and how to analyze it.

We reveal for the very first time the original post by the hacker behind T-Mobile's breach, which was published three days before the post the media and T-Mobile cited over the past weeks.

Could the latest mega cryptocurrency heist have been prevented? Let's review the role of early indications in averting the next hacking attack.