How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

In this post we share the important role that dark web monitoring has in risk management solutions like PiiQMedia. Learn more about from the recent webinar we did with them here.
As an organization that works with 85% of Fortune 500 companies, hundreds of universities, the Pentagon, NASA and more, the Solar Winds data breach perfectly illustrates the scope and magnitude of a well-executed supply chain attack. With third-party risk currently one of the biggest threats to organizations, one would expect organizations like SolarWinds to have sophisticated risk management solutions in place.
Unfortunately, these organizations face huge challenges when trying to detect third-party risk. Most of the datasets used to detect third-party risk are too narrow, with very few similar examples or samples over time. This makes detecting patterns and risk very difficult. That’s why it’s critical to not only monitor IT system security and internal data security, but also external web data related to company reputation, sentiment, vulnerabilities, and compromised PII of employees. This is the type of data that indicates risks and threats to the organization and its digital assets.
Risk management solutions that provide organizations with alerts in real-time are only as good as the raw data that powers them.
Risk management solutions that want to extend their monitoring to include third-party risks today must rely on high-quality dark web data feeds with comprehensive coverage. This includes the ability to monitor anonymous networks like TOR, I2P, Zeronet as well as chat applications like Telegram, IRC and Discord in the deep and dark web.
Here is a basic overview of the process that goes into delivering the data to risk management solutions:
The risk management process relies on its ability to gather data from a wide range of sources, starting first and foremost with data discovery, or source mapping. This includes identifying relevant sources from the open web, social media, dark and deep web data through a combination of manual and automatic work.
In comparison with data collection from the open web, dark web data discovery presents unique obstacles. First, the data in the dark web isn’t indexed by search engines by Google, so it’s much more difficult to locate. This is particularly challenging when you consider the sheer magnitude of the data. Chat applications like Telegram, for example, produce half a billion chats a day. In addition, domains of dark web marketplaces often change names, suddenly shutting down and seeming to disappear – only to reopen as a different domain name. Dark web vendors also operate in many different languages, and the time and resources needed to identify the relevant information in these languages can pose an extra challenge.
After the relevant data is discovered, it must be crawled. Data crawling must be continuous, otherwise important data will be missed. This can be especially challenging in the dark web, with admins who regularly kick out suspicious users, block IPs, close sessions, and can identify bot behavior and ban users accordingly. In addition, many dark web sites have understood that complex captchas and changing mirrorlinks are efficient methods to protect themselves against automated crawling.
After the data is crawled, it needs to be extracted. That includes extracting entities such as the author, title, text, and publication date of a post. Other metadata such as the company name, external URLs mentioned in the post, bitcoin address, and other entities are also relevant.
To make data effective, it needs to be structured. Once the data is unified so that data is structured similarly regardless of the source (i.e. whether its from a chat application, dark web marketplace or forum), it can be plugged in to the relevant risk management solutions.
Let’s take an example from the Solar Winds data breach. When glancing quickly at the dashboard, users have the ability to quickly see the different risk factors, news patterns, timelines across geography and the open and dark web patterns across these different modes. But it’s important to understand the complexity involved in delivering those insights, which start with discovering the relevant data connected to each risk.
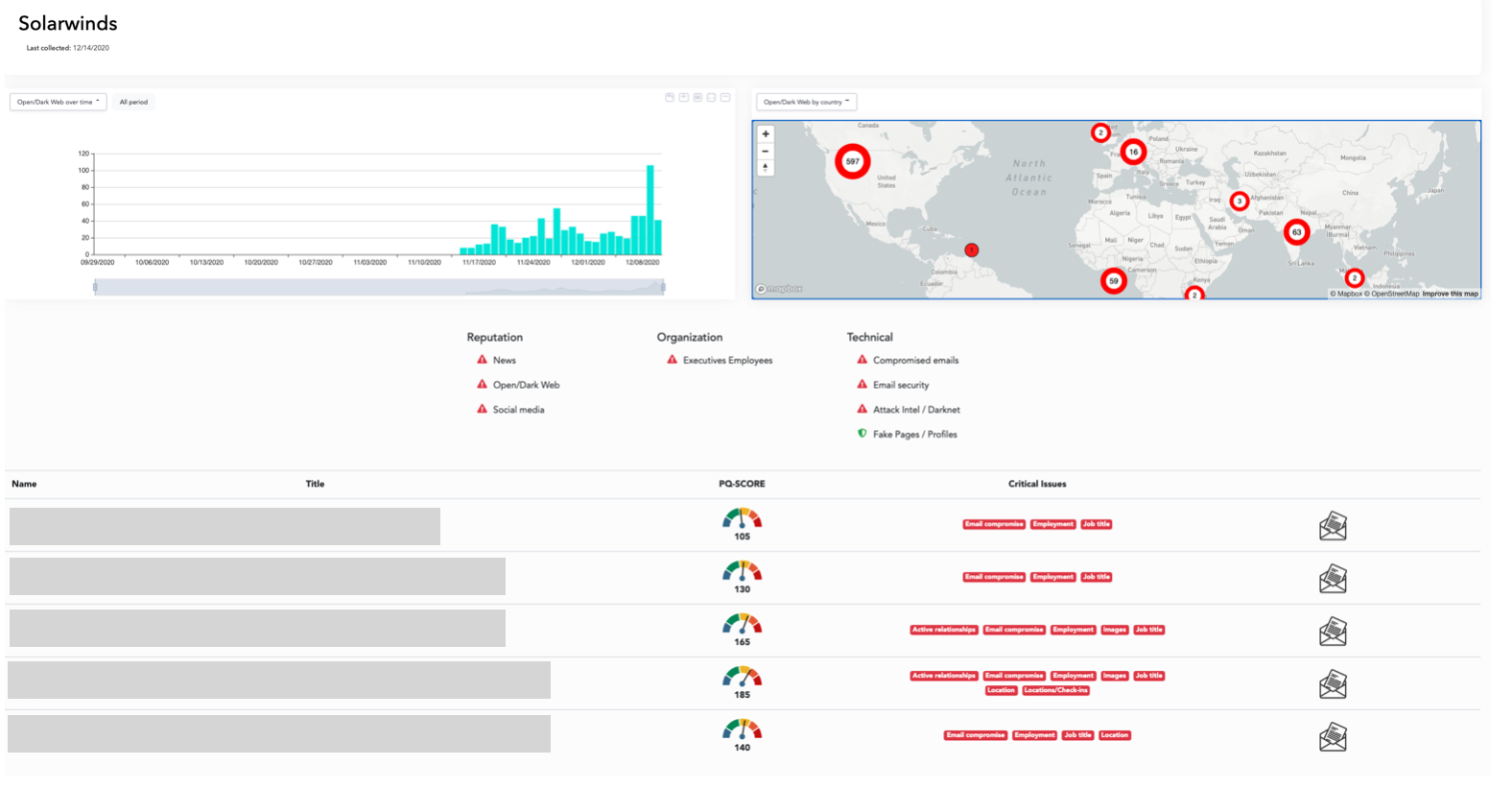
Here is a post from the dark web from Webz.io’s Cyber Endpoint about an MSP-PME (Managed Service Provider – Patch Management Engine) exploit. The exploit is part of the core solution of Solar Winds, the recent breach that impacted more than 30,000 customers. Since many of these customers included huge organizations like the US Army or the Pentagon, the third-party risks of this breach have far-reaching repercussions.
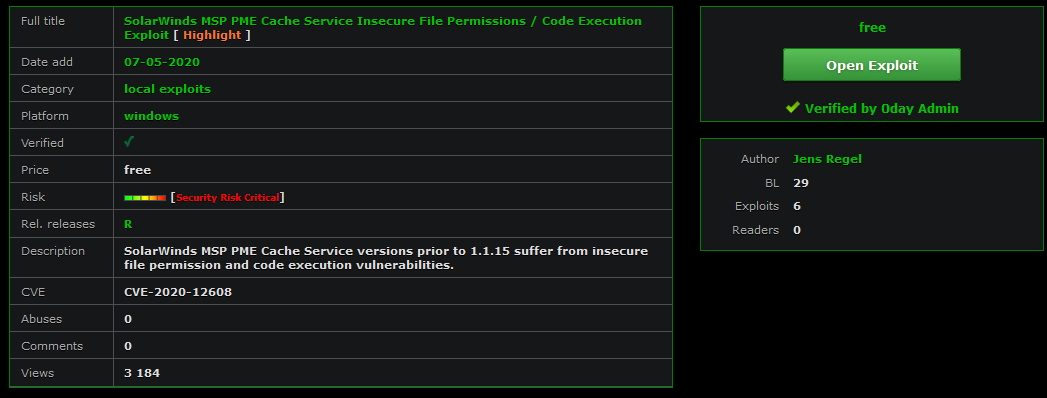
This exploit allows a malicious actor to execute code on the SolarWinds service. That means the exploit can easily spread to all of the organizations using this third-party software. It’s surprisingly similar to reports about the exploit of Orion IT software that SolarWinds sells to organizations.
Here’s another example of dark web data found in Webz.io’s Cyber Endpoint that indicates a possible third-party risk:
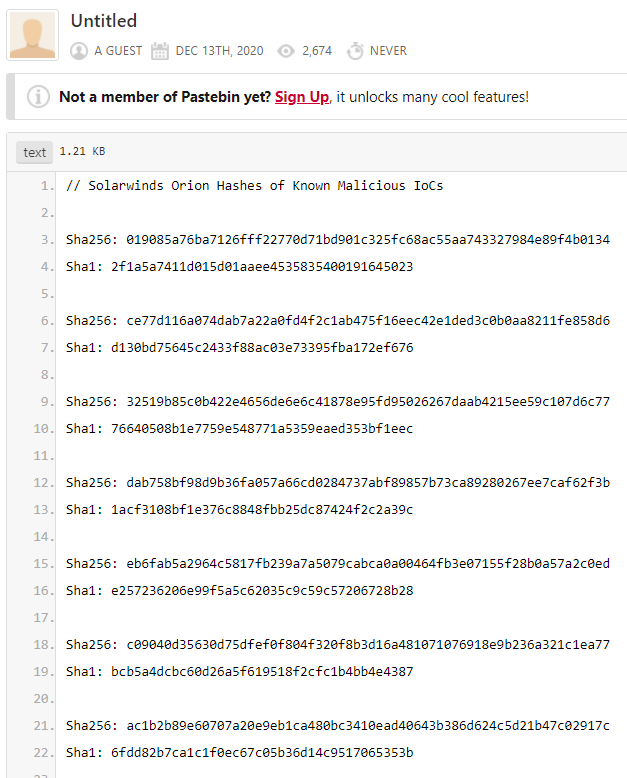
These malicious IOCs are indicators of compromises hashes from the Orion attack. These hashes might lead to actors related to the malware, or just add more technical information about the breach after the attack has been executed. Even though this information is from after the data breach occurred, it is still critical as it can help detect additional indicators of a more specific attack or a method that can block or minimize the impact of the end user.
Let’s take one last example of the impact of third-party risk from ransomware.
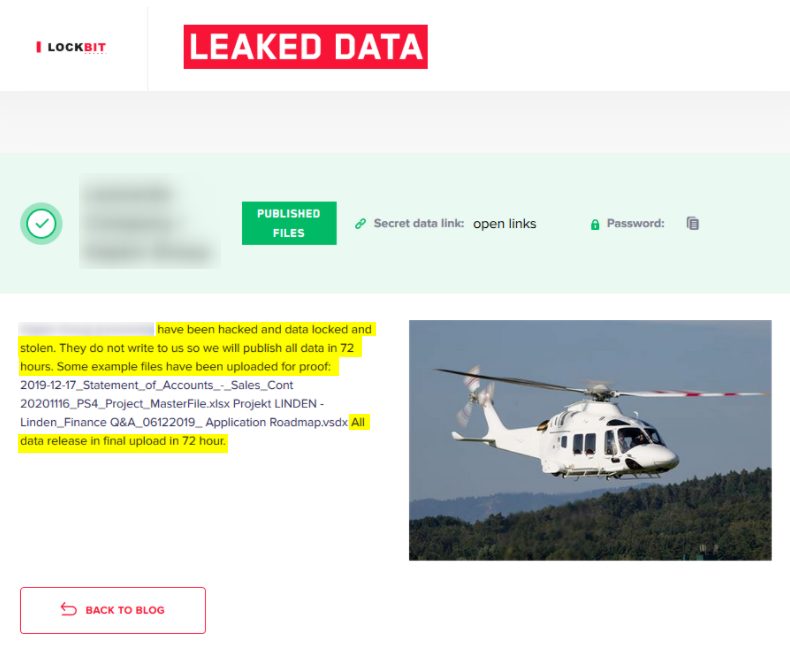
This is a post of a breach about leaked data from the Lockbit ransomware group found in our cyber repository. This breach of a multinational company subsidiary was announced just a few weeks ago. Since ransomware that impacts the subsidiary can also easily impact the holding company, risk monitoring must include the supply chain of the entire company (i.e. its holding organizations, supply chain, and subsidiaries).
Every day thousands of mentions of brands related to data breaches can be found in the dark web. This includes PII and NPI data, threats in the forms of malware, and ransomware in various criminal groups. With tens of thousands of signals in the dark web, it’s critical for organizations to be able to focus on the most relevant data. A tool with robust discovery that identifies the relevant keywords can feed the most relevant data into a platform, collecting signals and converting it into an event. This constant and wide coverage is critical both before and after a major data breach to mitigate them and prevent future attacks. Webz.io is proud to deliver its customers this high-quality coverage to help mitigate attacks in organizations around the world.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.