How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

The dark web has a justifiable reputation as a home for illicit activities and illegal trades, and a hub for sharing tools for cyberattacks. This notorious and nearly anonymous layer of the web is an environment particularly conducive to the planning and execution of malicious activities, including malware and phishing attacks. That’s why closely monitoring what’s happening in the dark web is so important.
In this post, we’ll explain how organizations and businesses can monitor the dark web to detect emerging malware and phishing threats – and head them off before they develop into attacks.
Only a small fraction – some 4% – of the vast ocean of online content is actually searchable through familiar search engines like Google and Bing. This accessible portion of content is called the open web, and it’s where most of us work, play, interact, and ‘live’ our online lives.
The rest of online content, about 96%, comprises what’s called the deep web. These are pages and content that are intentionally hidden, often for legitimate privacy or financial motives. Deeper than all this lies the dark web, which is never touched by mainstream search engines. Accessing the dark web requires special software like Tor, I2P, or Zeronet. It’s a highly secretive space that attracts illegal activities such as trading weapons and drugs, as well as various cybercrime tools and services.
Some of the key types of hacking tools available via the dark web are malware and phishing kits. Malware kits are bundles of malicious software components that allow users to create customized cyberattacks like viruses or ransomware. Phishing kits are the same idea – but include tools to craft deceptive emails or websites with the aim of deceiving users into sharing sensitive information or credentials.
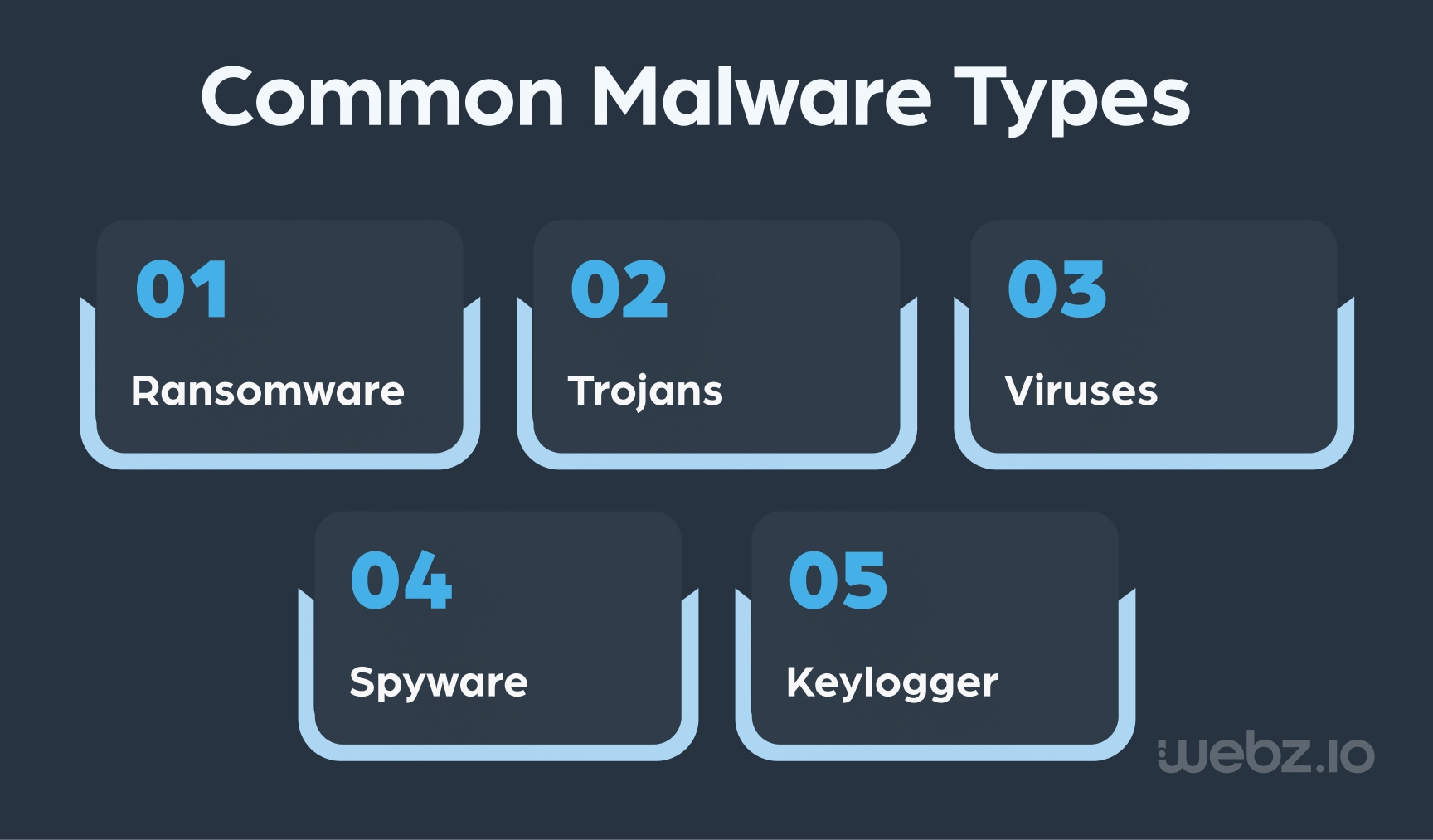
Easily accessible via the dark web, malware is short for ‘malicious software’ and includes a range of harmful programs engineered with malicious intent by cybercriminals. These programs are designed to infiltrate, disrupt, or compromise digital systems – stealing sensitive information, impairing operations, extorting money, or gaining unauthorized access. The malware spectrum includes ransomware, trojans, viruses, worms, spyware, and more – each with its own distinct mode of attack.
For organizations, malware poses a range of threats:
Phishing is one of the most popular social engineering attack vectors. It involves the use of deceptive emails, messages, or websites that aim to trick users into revealing sensitive information – login credentials, personal information, financial data, and more. Owing to both its efficacy and simplicity, phishing is the fastest-growing type of cyberattack. Of the over 800,000 cybercrime complaints reported to the FBI last year, nearly 40% were about phishing attacks – and a staggering 83% of companies reported falling victim to at least one phishing attack a year. These attacks resulted in monetary losses of over $10 billion.
What’s more, phishing is evolving. Using Generative AI and other tools available on the dark web, attackers are continuously adapting their tactics to exploit new vectors, beyond traditional email-based phishing. Cybercriminals are increasingly targeting individuals and organizations through messaging platforms and other popular communication channels – WhatsApp, Signal, SMS, and more. They’ve begun exploiting vectors like social media platforms, collaboration tools like Slack and Microsoft Teams, and even voice assistants.
Start Monitoring Malware & Phishing Threats
Dark web monitoring is a vital investigative tool for tracking and mitigating malware and phishing threats that originate in the hidden layers of the internet. Dark web monitoring enables organizations to stay ahead of emerging threats, fortify their defenses, and swiftly respond to potential breaches or vulnerabilities before they escalate into larger security incidents.
By monitoring clandestine dark web forums, marketplaces, and encrypted networks, cybersecurity experts can detect early signs of emerging malware threats and phishing activities. Monitoring the dark web delivers perspective on what threat actors are discussing – for example, the creation, sale, or deployment of malware and phishing kits. These types of early insights allow organizations to understand evolving malware or phishing threat tactics and potential targets. And this helps them create more targeted and proactive defense strategies.
Dark web monitoring also helps track stolen or compromised data obtained via phishing or ransomware attacks, like login credentials or financial information. Once an organization knows such data is for sale, stakeholders can act swiftly to mitigate the impact – informing affected parties, changing credentials, or implementing stronger security measures.
Finally, dark web monitoring helps identify vulnerabilities in organizational infrastructure or systems. By understanding the specific vulnerabilities, exposures, methods and tools being discussed on the dark web, cybersecurity teams gain a deeper understanding of the specific threats facing their organizations and can fortify their systems accordingly.
Navigating dark web monitoring poses many technical, legal and budgetary challenges, including:
To implement dark web monitoring for malware and phishing mitigation, start with these steps:
The dark web is a notorious enabler for illicit activities and cybercrime – particularly malware and phishing. Dark web monitoring offers proactive defense against these evolving dangers. Choosing the right dark web monitoring tool or data via dark web monitoring API can help your organization track evolving threats, fortify defenses, and swiftly respond to a constantly evolving malware and phishing threat landscape.
Talk to Webz.io to discuss how we can help you – whether you need a dark web monitoring tool or dark web data to automate your own dark web monitoring solution.

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.