How to Automate Supply Chain Risk Reports: A Guide for Developers
Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Today’s data breaches are more damaging to organizations than ever before, now reaching almost $4 million on average — a rise of 12% in the past 5 years due to a combination of increased regulations, financial penalties and more sophisticated data breaches. Not only are these data breaches more expensive than in the past, they are also becoming increasingly frequent. In the last three years alone, over 11.7 billion records have been lost or stolen from organizations.
Although most of the damage inflicted on the company occurs during the year immediately following the breach, significant effects can often be felt for an additional two years. And the damage to organizations today extends well beyond the financial, negatively impacting the brand’s reputation and consumer trust.
Data breaches can be broken into three main stages:
This post will give examples of how an advanced web monitoring service can aid an organization in every step of a data breach.
The good news is that the earlier an organization is able to detect a data breach, the better they will be able to mitigate these costs. But how can they best do this?
The key is to detect a data breach as early as the planning stages, the weeks to months before the breach is made public on the labyrinth of networks, forums and illicit marketplaces that make up the dark web. Early detection is particularly crucial when the company name is explicitly mentioned. That’s because hackers know that mentioning the entity involved in the breached data is likely to bring it to the attention of the public in a relatively short space of time, resulting in the removal of the files, and serious mitigation of damage to the organization.
Let’s take a look at an example of the Malindo airline breach that received worldwide media attention. We were able to capture the breach in our Cyber API from a Torum site that took place up to two weeks before this breach was reported in the media worldwide.

When downloading the link, we can see the CSV file with the leaked data from the airlines well before officials reports of the leak from either the media or the company itself. The ability to search for posts with these types of links allows national security and intelligence and law enforcement agencies to detect possible breaches or leaks before they happen or before they become public knowledge.

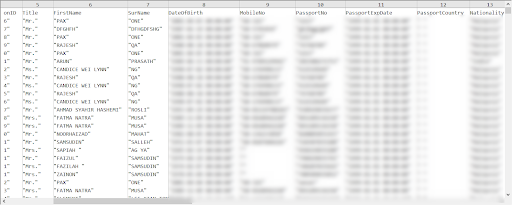
Here is another example of a post, authored by a user named ‘novemberrain’, that was seen 8 days before the media learned about the hack (Note: the link to the stolen data no longer works).
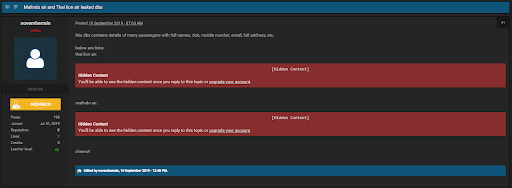
Notice that both of these examples above specifically mention the name of the organization breached. Organizations that want to mitigate data breaches must choose a comprehensive data breach detection service that continuously scans and identifies the most recently compromised data so that the organizations can act quickly to prevent the waste of time and resources – not to mention extensive damage to the brand.
Early detection enables an organization to quickly take additional security measures to prevent more leaked data in the future. Malindo was able to quickly hire a team of data forensics and cyber experts to deal with fallout from the breach, initiating an automatic reset of all customer passwords as a precautionary measure. Once these systems were secured, the matter was passed to law enforcement for further investigation and prosecution.
Once a data breach is detected, the cybercriminal will do his best to find multiple methods of splitting and distributing the breached data, making it harder to trace. That’s why a comprehensive and wide monitoring service is necessary to find all the relevant mentions and mitigate the damage successfully. Webz.io’s granular filtering capabilities were able to find additional mentions of the IP address, Amazon server or other digital identifiers related to Malindo in the dark web. After being identified, these leaks were then removed immediately.
Continuing the Malindo attacks example, the data stolen was neither the result of a cybersecurity defect in Malindo’s internal systems nor of Amazon Web Services (AWS), its cloud infrastructure provider, so these systems didn’t need to be attended to immediately. The stolen data was, however, uploaded to an AWS bucket before being removed for violation of those services’ terms of service — but not soon enough to have been reuploaded in different AWS regions, where it remained an ongoing threat within easy reach of hackers and cybercriminals.
But even with that threat remaining, the right darkweb monitoring tools can significantly mitigate the damage of these links. With advanced cyber data feeds that offer superior coverage of the dark networks, including millions of sites, files, marketplaces and messaging platforms, the dots can be easily connected to run more thorough searches and detect additional instances of that same breach.
For example, we saw many mentions of a hacker named “Spectre” and “his website.” Many hackers thanked and gave credit to this hacker for the Malindo and Thai Air breach. Upon further investigation, Webz.io found the original AWS link URL beginning with “sunstarcms.s3.amazonaws” that contained the database of passenger data for both Malindo Air and Thai Lion Air posted on the hacker’s Intel site. Malindo hosted much of its cloud infrastructure on AWS and the URL probably reflects a bucket that hosted a Content Management System (CMS) called Sunstar or an ERP or booking management application operated by the airline.
This type of advanced keyword monitoring ability allows law enforcement, national security and intelligence agencies to find references to unique digital designators and locate those spreading leaked data, or plotting to do so. Any brand mentions coupled with unique digital designators on the dark web should arouse a high index of suspicion for most companies that those sharing the leaks are plotting attacks on their infrastructure.
These unique digital designators can include:
When it comes to data breach detection, the best form of mitigating damage is early detection. Once a breach is made public, containing the damage can be more challenging, as the organization must prove to its consumers that it has taken the necessary measures to prevent future damage.
But even 6 months after a breach comes to public attention, continuous monitoring of the dark web for uncontained breaches is vital, since each additional data breach creates a bigger challenge for a brand to regain consumer trust. Sometimes a data breach that an organization thought was contained is discovered again many months later. Or additional breaches come to light, especially in well-known organizations with an extensive infrastructure and various endpoints.
Take the example of Facebook, which announced a third-party data breach from Cambridge Analytica affecting 50 million users in April 2018. Less than six months later, they announced an additional data breach affecting 40 million users. Today the company still faces the immense hurdle of regaining consumer trust.
The longer an organization takes to detect a breach, the more extensive the damage, both in financial terms and in consumer trust in the brand.
Although the average time an organization takes to detect a breach is 206 days, organizations that are able to detect and contain a breach in less than 200 days spent $1.2 million less on the total cost of a breach. Once word of a data breach reaches the public, containment of the breach and rebuilding trust in the brand takes more effort.
Webz.io’s Data Breach Detection service not only monitors for the first signs of a data breach across websites, marketplaces, and forums, but during and after it is announced to the public — saving time, resources and damage to the brand at each and every stage of the data breach.
To find out more about Webz.io’s Database Breach Detection service, speak to a Webz.io representative

Do you use Python? If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.

Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.

A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.